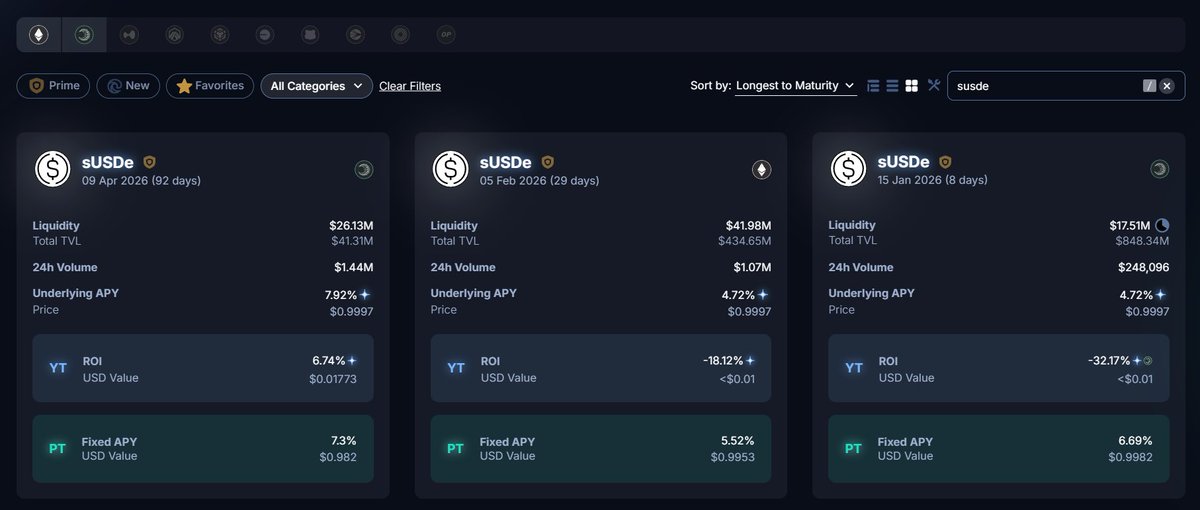
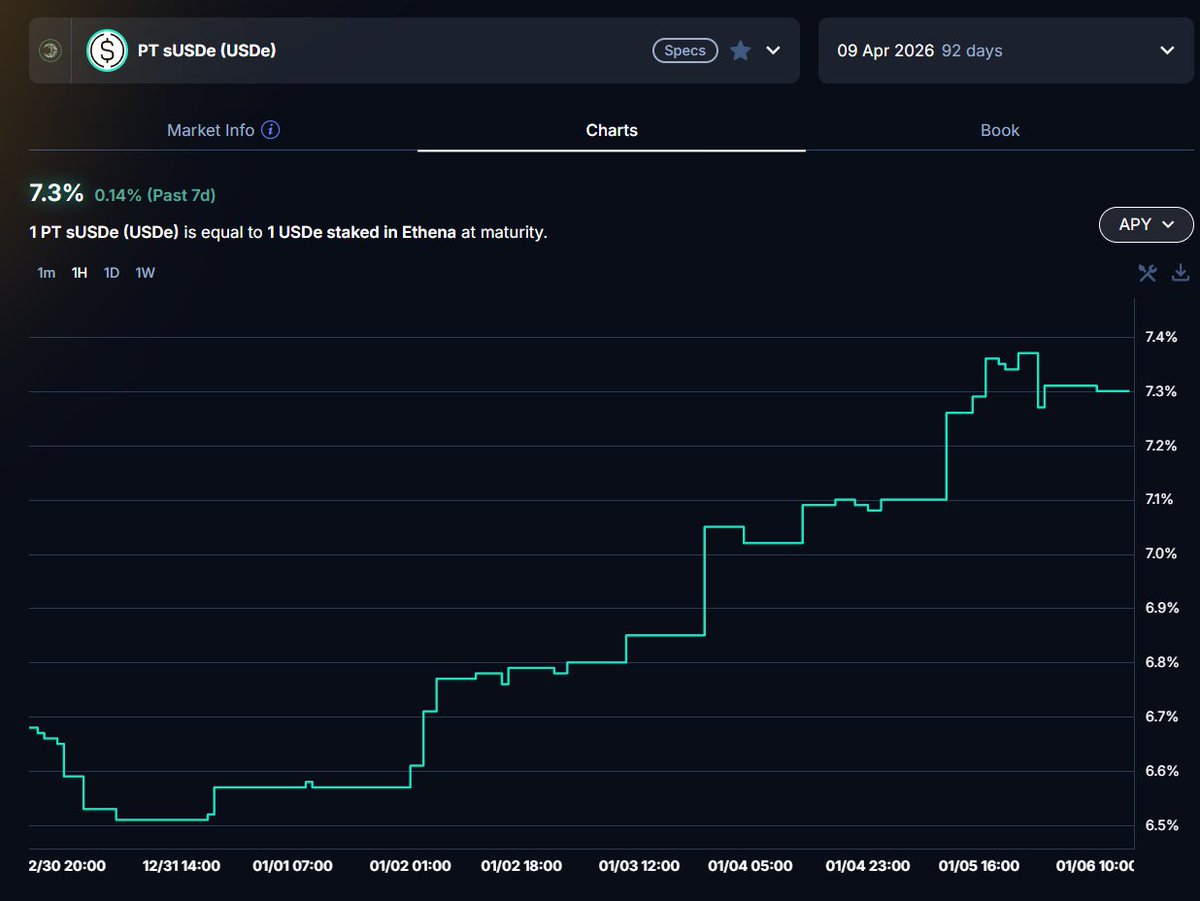
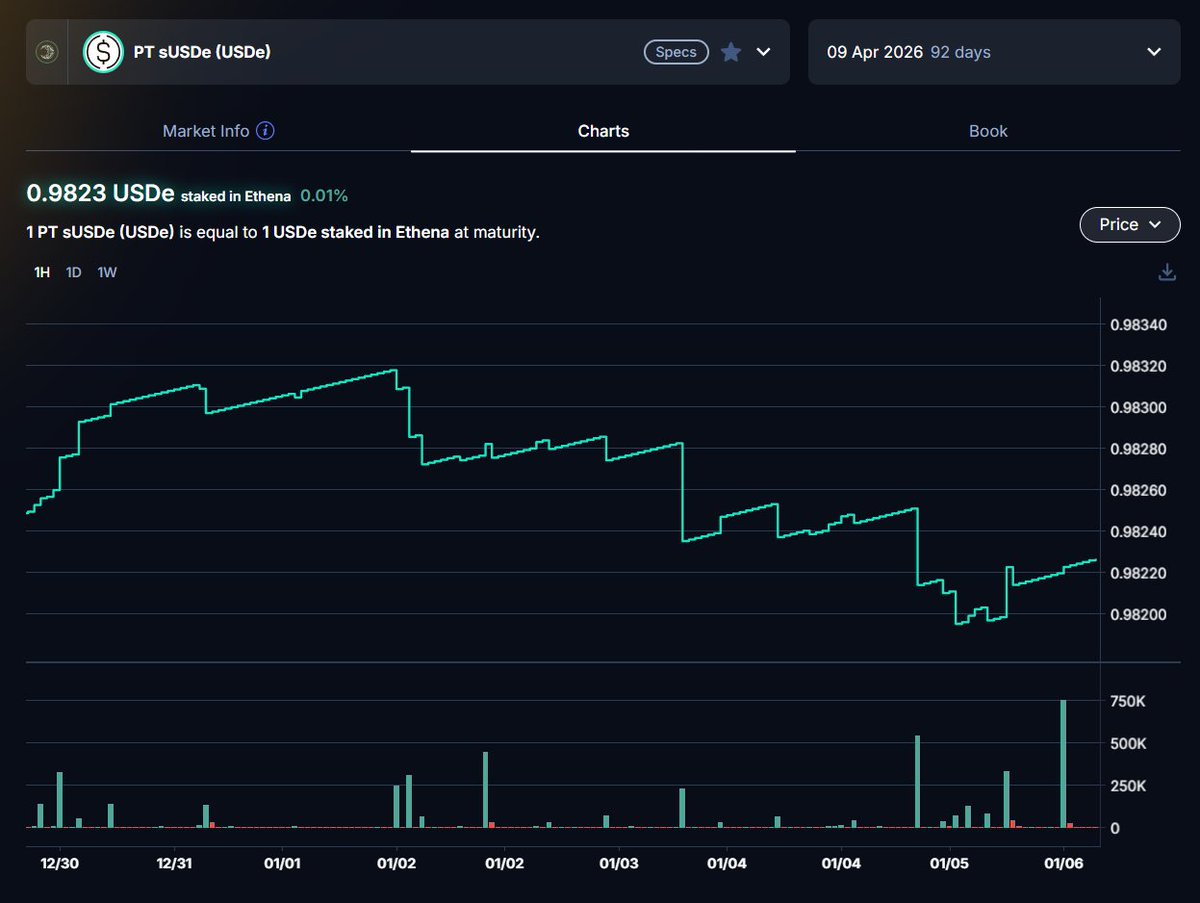
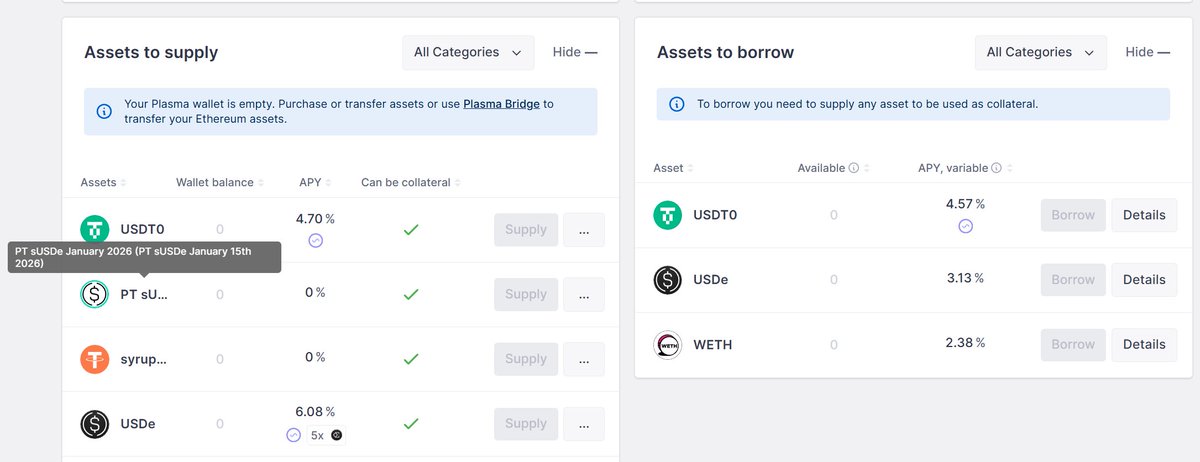
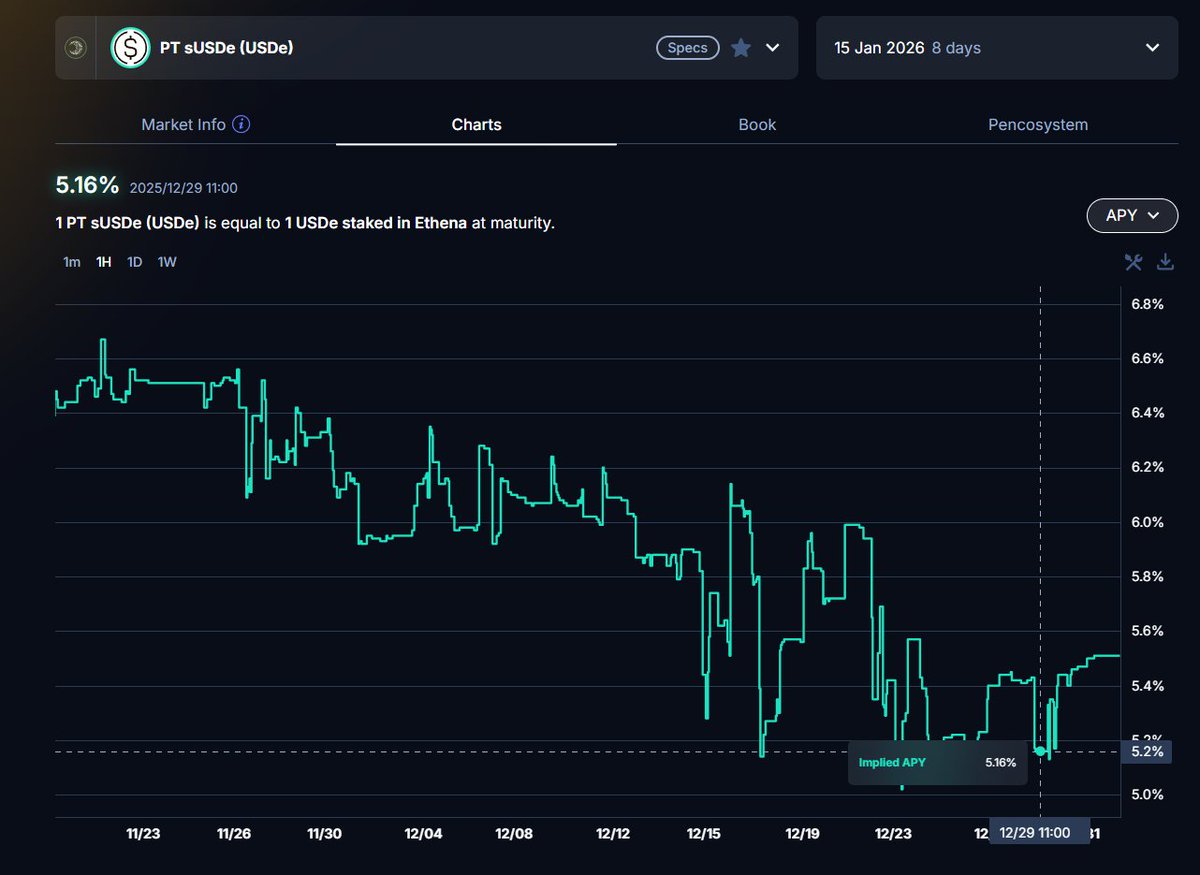
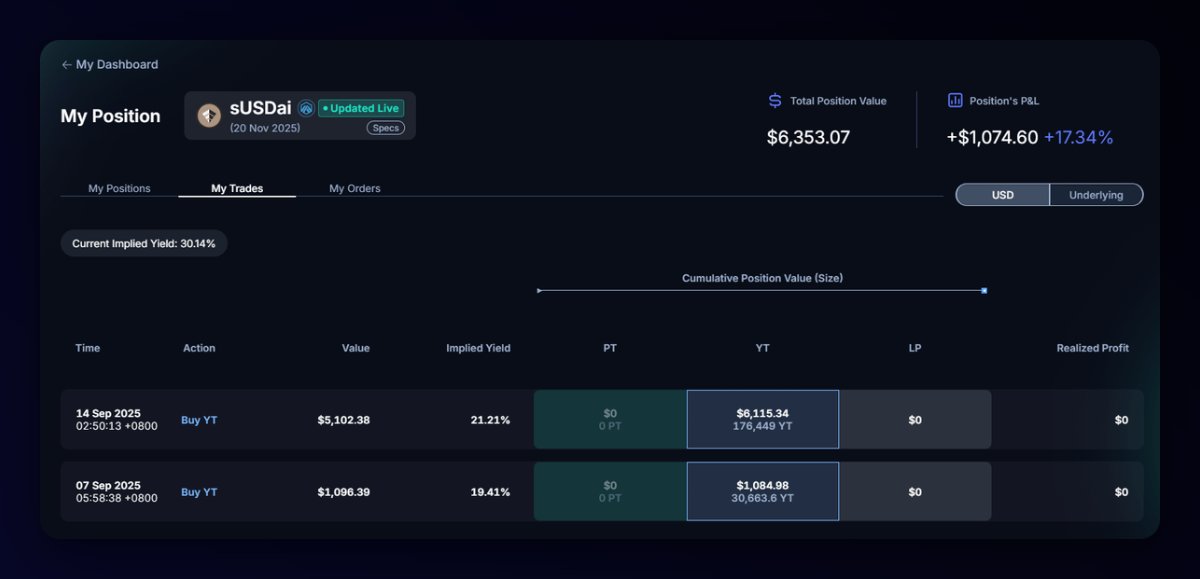
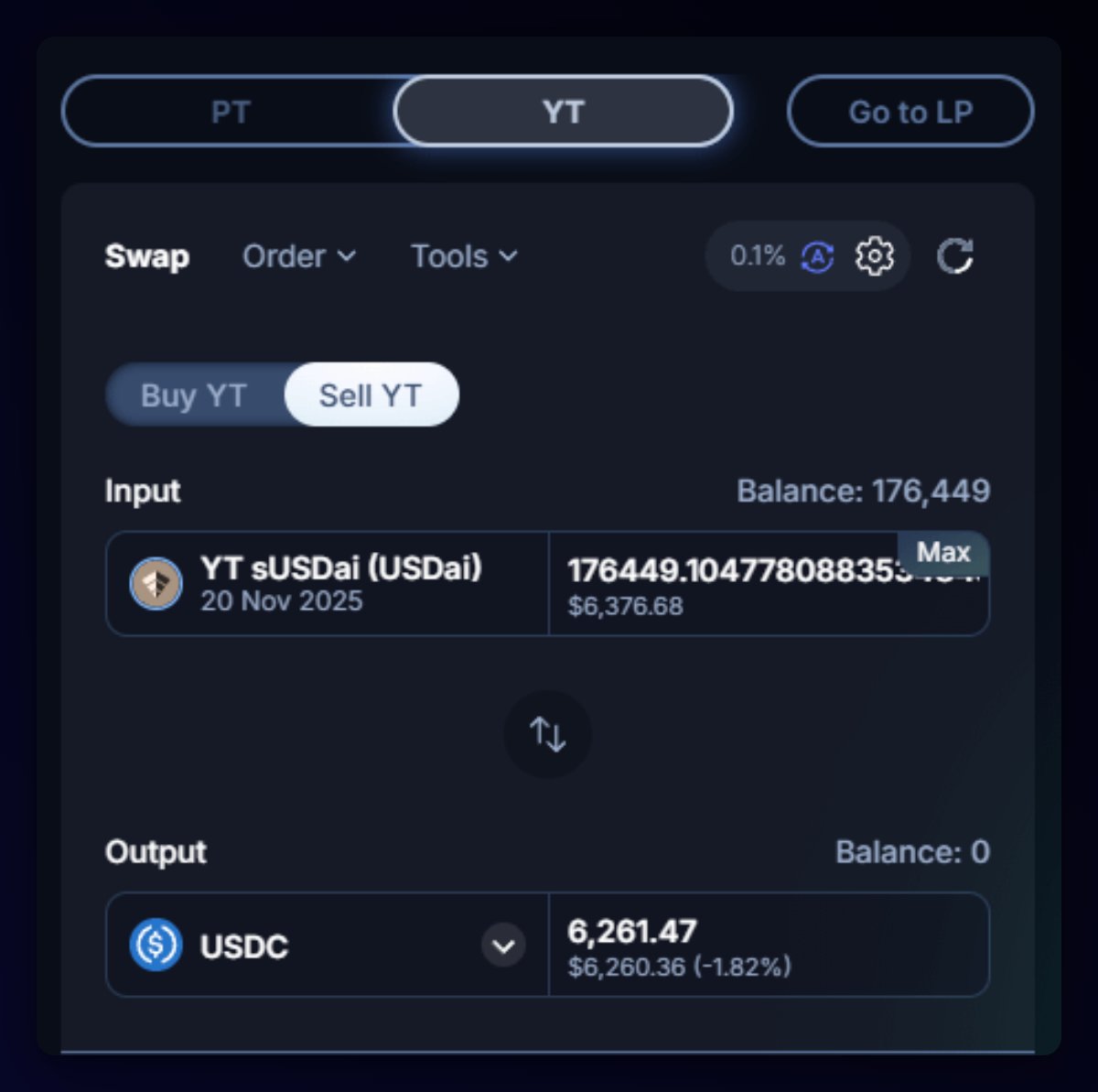
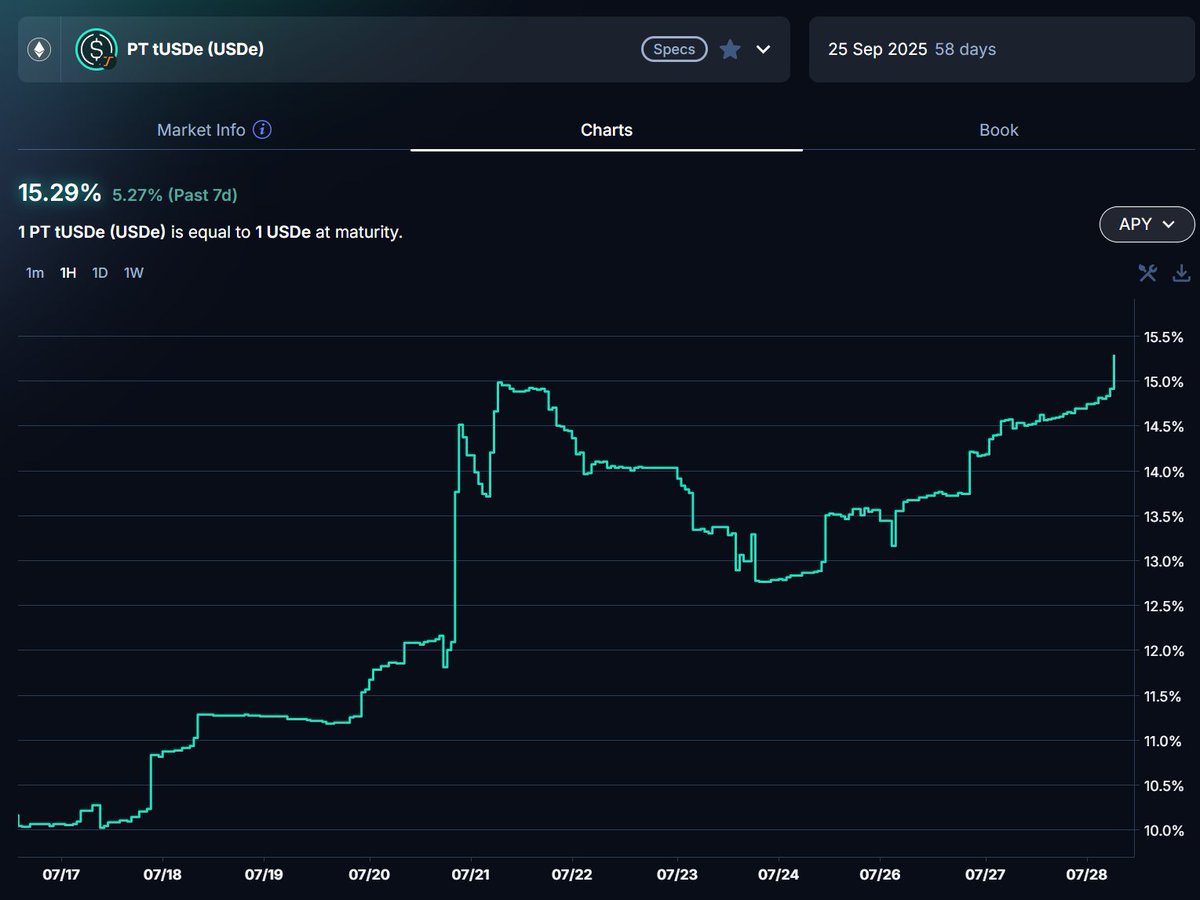
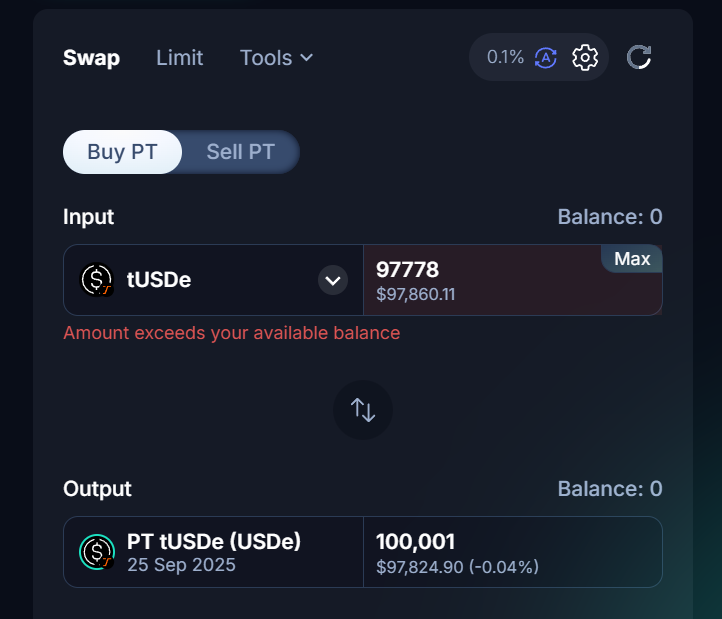
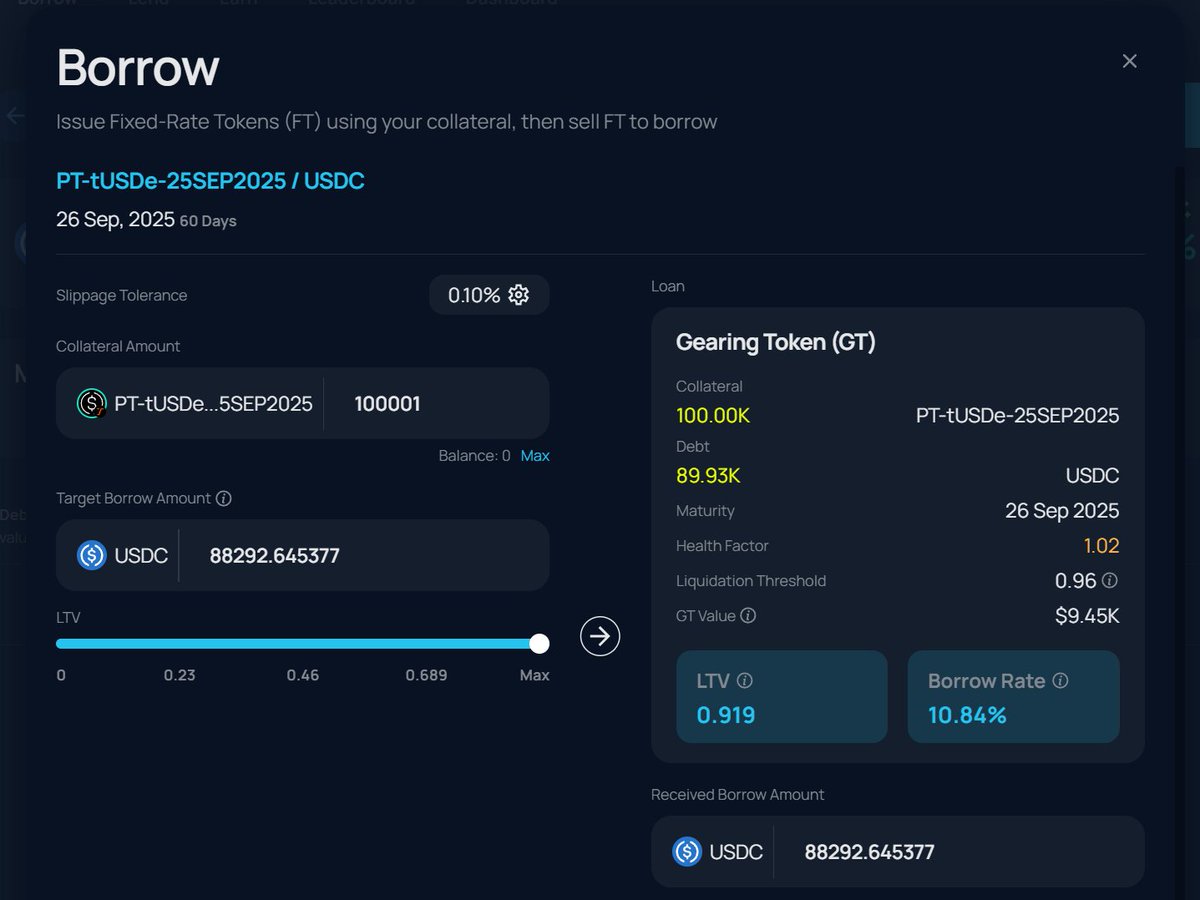
Crypto's a dangerous world, fraught with scams, frauds, and unscrupulous characters.
Here's the Ultimate Opsec Guide that EVERYONE needs to protect your magic internet money 👇🏻
1/69
Here's the Ultimate Opsec Guide that EVERYONE needs to protect your magic internet money 👇🏻
1/69

2/ Never reuse passwords
"Don't put all your eggs in one basket"
This old adage applies to passwords too. You don't want ALL of your accounts and wallets going down in flames just because of ONE password.
Always use long, complex, alphanumeric + special characters passwords
"Don't put all your eggs in one basket"
This old adage applies to passwords too. You don't want ALL of your accounts and wallets going down in flames just because of ONE password.
Always use long, complex, alphanumeric + special characters passwords
3/ Use a password manager
Can't remember all 699 of your passwords? Good news is you won't have to.
All you really need to remember is ONE strong master password and the password manager can do the rest.
P.S. @Bitwarden is open source + free.
Can't remember all 699 of your passwords? Good news is you won't have to.
All you really need to remember is ONE strong master password and the password manager can do the rest.
P.S. @Bitwarden is open source + free.
4/ Never save your passwords/private keys online
No emails. No iCloud. No Evernote.
The best way is the old fashioned way - write it down (in multiple copies) and store the physical copies in secure locations.
And if you feel like graduating from pen and paper...
No emails. No iCloud. No Evernote.
The best way is the old fashioned way - write it down (in multiple copies) and store the physical copies in secure locations.
And if you feel like graduating from pen and paper...
https://twitter.com/cryptosteel/status/1775501570194452654
5/ Anonymize your emails
It's the same logic as passwords - a478u5g_w1r@gmail.com makes it a lot harder to guess than john_wong@gmail.com, especially when your identity/personal details have been leaked.
It's the same logic as passwords - a478u5g_w1r@gmail.com makes it a lot harder to guess than john_wong@gmail.com, especially when your identity/personal details have been leaked.
6/ Use multiple emails
Again, "don't put all your eggs in one basket".
This way if shit goes down, at least the risk will be contained within just ONE email + ONE password.
Too much work? At least consider having a FEW different emails to mix and match.
Again, "don't put all your eggs in one basket".
This way if shit goes down, at least the risk will be contained within just ONE email + ONE password.
Too much work? At least consider having a FEW different emails to mix and match.
7/ 2FA everything
2FA so that you'll need more than just an email + password to login.
Consider using 2FA apps such as Google Authenticator, @Authy or even better...
2FA so that you'll need more than just an email + password to login.
Consider using 2FA apps such as Google Authenticator, @Authy or even better...
8/ Use a hardware security key
Hardware-based 2FA such as a Yubikey lets you authenticate the login by pressing a physical button, instead of having a code sent to you on your phone app.
Best practice is to have at least 3:
1 for daily use, 2 for backup (stored separately)
Hardware-based 2FA such as a Yubikey lets you authenticate the login by pressing a physical button, instead of having a code sent to you on your phone app.
Best practice is to have at least 3:
1 for daily use, 2 for backup (stored separately)

9/ Disable SMS authentication
Just don't. Your accounts will likely be more secure with this TURNED OFF (just remember to 2FA in other ways, please)
The risk of SIM swap attack is very real so be extra mindful of this.
Just don't. Your accounts will likely be more secure with this TURNED OFF (just remember to 2FA in other ways, please)
The risk of SIM swap attack is very real so be extra mindful of this.
https://twitter.com/cloakedwireless/status/1818096865742598310
10/ Use a hardware wallet
Hot wallets are fast and convenient yes. But if you really value your magic internet coins, start storing them on a @Trezor or @Ledger.
This way, thieves ahold your device(s) will need more than just your Metamask login password to steal everything
Hot wallets are fast and convenient yes. But if you really value your magic internet coins, start storing them on a @Trezor or @Ledger.
This way, thieves ahold your device(s) will need more than just your Metamask login password to steal everything
11/ Don't use the 1st address
This doesn't work as well these days since @Rabby_io will just display all the addresses but hey - anything to make it HARDER for them.
If your private key gets leaked, maaaaaybe they'll give up after seeing $0 in the 1st address (or 2nd, 3rd...)?
This doesn't work as well these days since @Rabby_io will just display all the addresses but hey - anything to make it HARDER for them.
If your private key gets leaked, maaaaaybe they'll give up after seeing $0 in the 1st address (or 2nd, 3rd...)?
12/ Don't approve infinite amount
Don't set unlimited spend limit when approving transactions.
Yes, more hassle, more gas fees when you want to change this down the road, but hey if shit hits the fan for the smart contract, at least your entire balance won't be drained
Don't set unlimited spend limit when approving transactions.
Yes, more hassle, more gas fees when you want to change this down the road, but hey if shit hits the fan for the smart contract, at least your entire balance won't be drained
13/ Double check the approval
Don't just blindly click-through those transactions!
It takes just ONE mistake to potentially lose everything, so be sure to double-check, triple-check the deets before you even hover your cursor over that "approve" button.
Don't just blindly click-through those transactions!
It takes just ONE mistake to potentially lose everything, so be sure to double-check, triple-check the deets before you even hover your cursor over that "approve" button.
https://twitter.com/1034728853002903552/status/1645709289082814464
14/ Revoke approvals periodically
This is a good practice to stop access to your wallet or funds, especially for contracts you haven't interacted with for quite some time.
Why? Because you never know. Malicious devs for instance could technically build in backdoor access


This is a good practice to stop access to your wallet or funds, especially for contracts you haven't interacted with for quite some time.
Why? Because you never know. Malicious devs for instance could technically build in backdoor access


15/ Eliminate/minimize browser extensions
These little buggers may come with an extra serving of malware, and some may even have excessive permissions to read your data.
Unless you 100% trust the developer, best to just rid of them despite the inconvenience.
These little buggers may come with an extra serving of malware, and some may even have excessive permissions to read your data.
Unless you 100% trust the developer, best to just rid of them despite the inconvenience.

16/ Use separate browser profiles
Multiple emails. Multiple passwords. Multiple profiles. Same logic.
Isolate your wallet extensions like @rabby_io and @MetaMask into their own browser profiles.
Multiple emails. Multiple passwords. Multiple profiles. Same logic.
Isolate your wallet extensions like @rabby_io and @MetaMask into their own browser profiles.

17/ Double-check the site
Don't just click on the 1st link that pops up on your Google search.
Often times, the first link could be a fake. Be extra cautious when it's an ad.
Always cross-check sources for the right URL - official X account, @CoinGecko, @CoinMarketCap etc.
Don't just click on the 1st link that pops up on your Google search.
Often times, the first link could be a fake. Be extra cautious when it's an ad.
Always cross-check sources for the right URL - official X account, @CoinGecko, @CoinMarketCap etc.

@SlowMist_Team 18/ Dedicated device for dedicated purpose(s)
It’s NOT a good idea to crypto on the same device you use for torrents, XXX contents, deep web surfing etc.
To be extra safe, use a separate, dedicated device for crypto + an OFFLINE only mobile device for 2FAs.
It’s NOT a good idea to crypto on the same device you use for torrents, XXX contents, deep web surfing etc.
To be extra safe, use a separate, dedicated device for crypto + an OFFLINE only mobile device for 2FAs.
19/ Beware of fake X accounts
Fakes, fakes, fakes everywhere.
Example - this fake @pendle_fi account:
✅ Got a golden @X checkmark
✅ Has its reply featured BEFORE the 2nd post in this thread
See how easy it is?
Rule of thumb - if it sounds too good to be true, it probably is
Fakes, fakes, fakes everywhere.
Example - this fake @pendle_fi account:
✅ Got a golden @X checkmark
✅ Has its reply featured BEFORE the 2nd post in this thread
See how easy it is?
Rule of thumb - if it sounds too good to be true, it probably is

20/ Don't just rawdog crypto, remember to always use protection, folks!
I'm sure there are plenty more "best practices" out there but these should serve as a good starting point for all of us.
If you have any other good threads/suggestions, please leave them in the replies 👇🏻
I'm sure there are plenty more "best practices" out there but these should serve as a good starting point for all of us.
If you have any other good threads/suggestions, please leave them in the replies 👇🏻
21/ Remember, the rule of thumb here is to doubt and double-check everything - the website URL, approval transaction, Telegram/Discord ID, make sure that "I" is not an "L"....
https://twitter.com/1377493693762969600/status/1676247060839038976
22/ Also shoutout to @bobbyong for this amazing opsec guides:
https://twitter.com/bobbyong/status/1403881080902471680
23/ And also our dearest beloved TVL inhouse TVL whisperer @imkenchia 🫶
https://twitter.com/279512403/status/1404111515507068928
"Search any protocol to go straight into their website, avoiding scam results from Google."
Nifty little tool by @DefiLlama 👇🏻
But still, remember to cross-check, double-check, triple-check the URL JUST IN CASE
Nifty little tool by @DefiLlama 👇🏻
But still, remember to cross-check, double-check, triple-check the URL JUST IN CASE
https://x.com/urule33/status/1818562739100422499
• • •
Missing some Tweet in this thread? You can try to
force a refresh