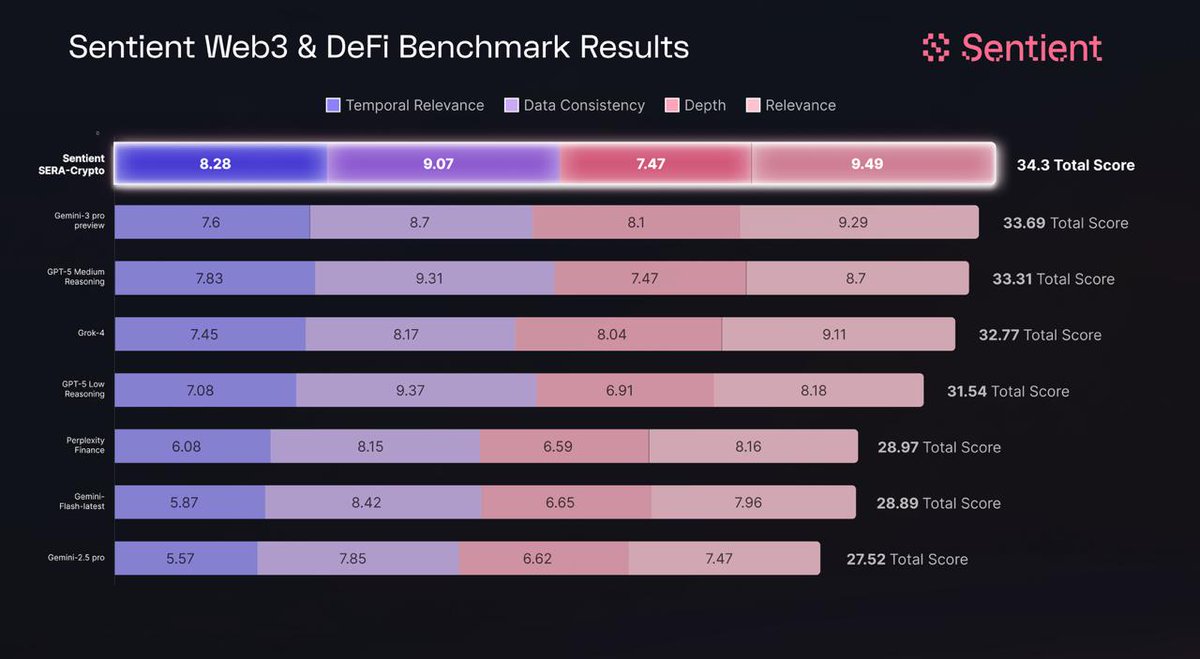
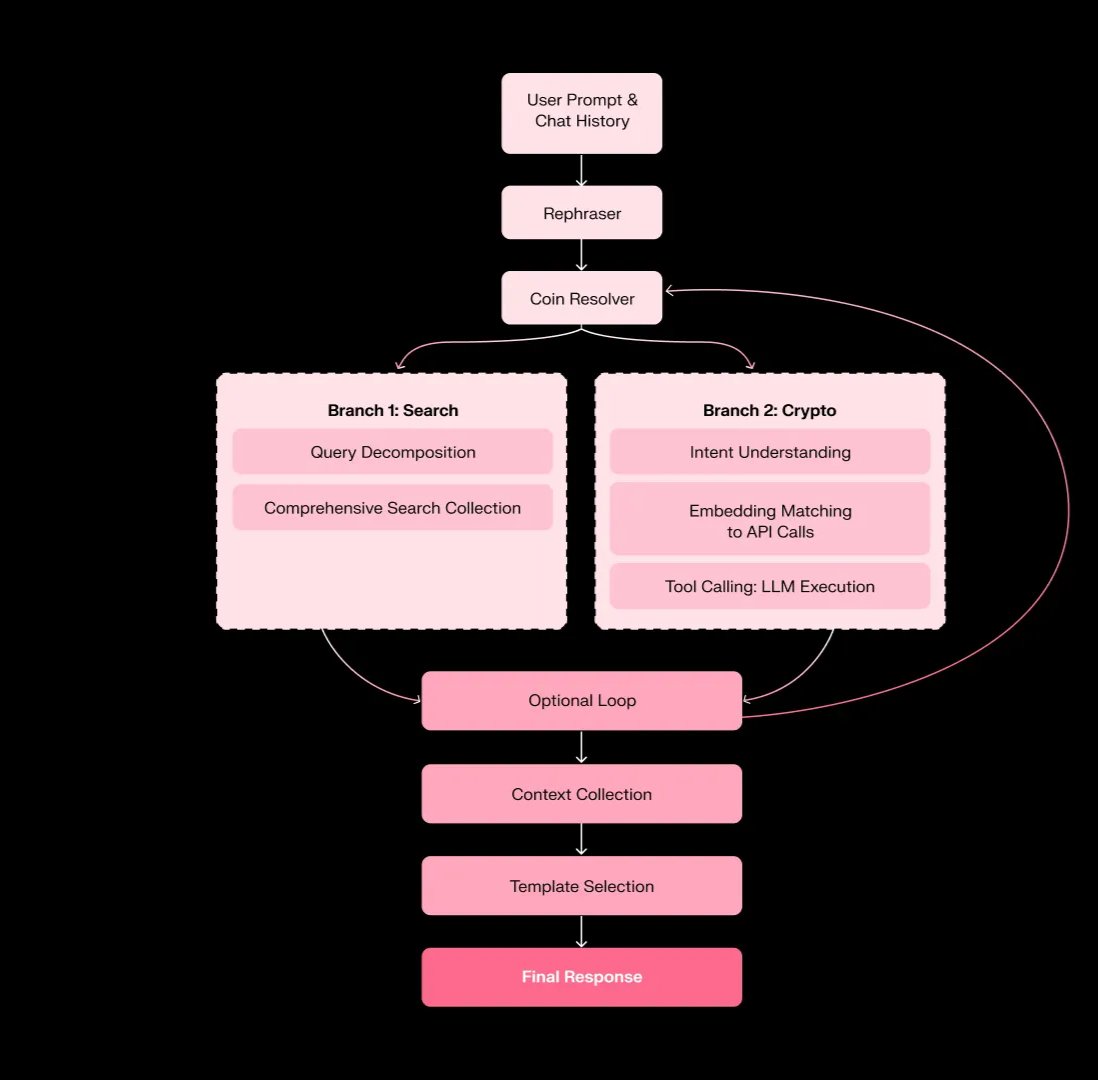
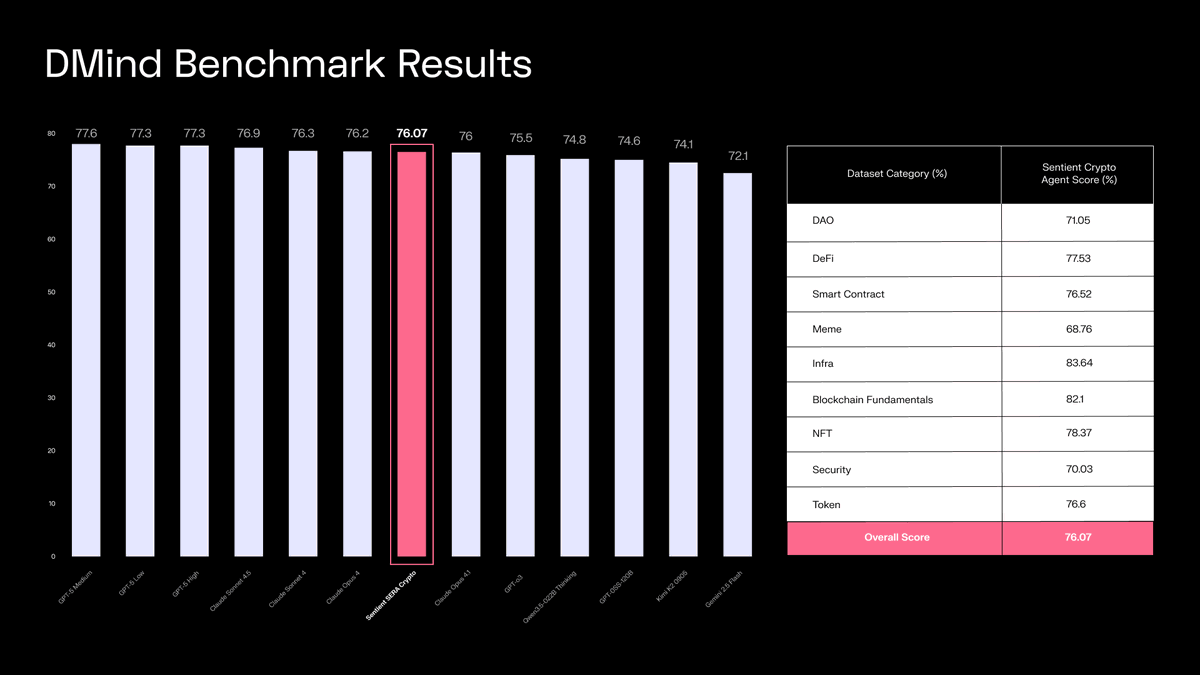
1/ We proudly present the Sentient Protocol, unveiled at the @openagisummit this week.
Sentient is an open source AI monetization protocol that enables community-built AGI. The key innovation is Model Loyalty and a new format, the OML format, for representing models that enables them to be Open (download and use locally), Monetizable (track and monetize their usage remotely), and Loyal (locked for usage that do not conform to safe, ethical, values espoused by the model owner). More details follow.
Sentient is an open source AI monetization protocol that enables community-built AGI. The key innovation is Model Loyalty and a new format, the OML format, for representing models that enables them to be Open (download and use locally), Monetizable (track and monetize their usage remotely), and Loyal (locked for usage that do not conform to safe, ethical, values espoused by the model owner). More details follow.

2/ Current forms of predominant AI were built on public goods from years of open innovation, but they extracted the value maximally from these public goods without sharing anything with the contributors - and created closed source hegemonies and empires out of it. Additionally, it censored information and imposed cultural preferences, which stifles innovation.
Open models are torch-bearers of resistance. They provide an alternative for AI innovators to participate in the large AI economy. However, there’s no way to monetize them, nor is there a way to ensure they are used safely and ethically.
We need a new ecosystem where open-source public goods of AI drive 𝗼𝗽𝗲𝗻 AGI innovation. There is an urgent need for a new technology that allows builders to share models openly and yet get rewarded when those models are used. There is a need for a new protocol that aligns incentives of AI builders with AI innovation. @viswanathpramod
Open models are torch-bearers of resistance. They provide an alternative for AI innovators to participate in the large AI economy. However, there’s no way to monetize them, nor is there a way to ensure they are used safely and ethically.
We need a new ecosystem where open-source public goods of AI drive 𝗼𝗽𝗲𝗻 AGI innovation. There is an urgent need for a new technology that allows builders to share models openly and yet get rewarded when those models are used. There is a need for a new protocol that aligns incentives of AI builders with AI innovation. @viswanathpramod
3/ The Sentient Protocol is a blockchain protocol for solving the alignment problem of community-built open AGI. It comprises contracts for incentives (ownership, usage, rewards) and nodes to enable decentralized control for access and alignment. The incentives and the necessary crypto-economic security is enforced via AVSs from the @eigenlayer ecosystem along with a trustless blockchain connected to @0xpolygon Agg layer. @hstyagi
4/ Underlying the Sentient protocol is a new cryptographic primitive called OML (open, monetizable, loyal). The goal is to allow the model to be transparently downloadable and yet retain the ability to track usage (monetization) and ensure safe and ethical usage (loyalty). The cryptographic primitive of program obfuscation will also solve OML, but that is a long standing open problem.
Sentient is devising 𝗔𝗜 𝗺𝗲𝘁𝗵𝗼𝗱𝘀 𝘁𝗵𝗲𝗺𝘀𝗲𝗹𝘃𝗲𝘀 to create OML libraries for AI models – the birth of a new area that we call 𝗔𝗜-𝗻𝗮𝘁𝗶𝘃𝗲 𝗰𝗿𝘆𝗽𝘁𝗼𝗴𝗿𝗮𝗽𝗵𝘆. In the first version, we convert backdoor attacks (security threat in AI) into model fingerprinting methods to authenticate model ownership. @sewoong79
Sentient is devising 𝗔𝗜 𝗺𝗲𝘁𝗵𝗼𝗱𝘀 𝘁𝗵𝗲𝗺𝘀𝗲𝗹𝘃𝗲𝘀 to create OML libraries for AI models – the birth of a new area that we call 𝗔𝗜-𝗻𝗮𝘁𝗶𝘃𝗲 𝗰𝗿𝘆𝗽𝘁𝗼𝗴𝗿𝗮𝗽𝗵𝘆. In the first version, we convert backdoor attacks (security threat in AI) into model fingerprinting methods to authenticate model ownership. @sewoong79
5/ The Sentient protocol is modular and can be composed with other implementations of OML (say, using trusted hardware) in the distribution layer or different decentralized storage or compute networks.
6/ A detailed description of this thread is available here:
The release of our complete whitepaper is coming soon, stay tuned. Sign up for Open AGI Research Discourse to get more updates: openagi.discourse.group/t/oml-and-the-…
openagi.discourse.group

The release of our complete whitepaper is coming soon, stay tuned. Sign up for Open AGI Research Discourse to get more updates: openagi.discourse.group/t/oml-and-the-…
openagi.discourse.group

• • •
Missing some Tweet in this thread? You can try to
force a refresh