1/ Recently a team reached out to me for assistance after $1.3M was stolen from the treasury after malicious code had been pushed.
Unbeknownst to the team they had hired multiple DPRK IT workers as devs who were using fake identities.
I then uncovered 25+ crypto projects with related devs that have been active since June 2024.

Unbeknownst to the team they had hired multiple DPRK IT workers as devs who were using fake identities.
I then uncovered 25+ crypto projects with related devs that have been active since June 2024.


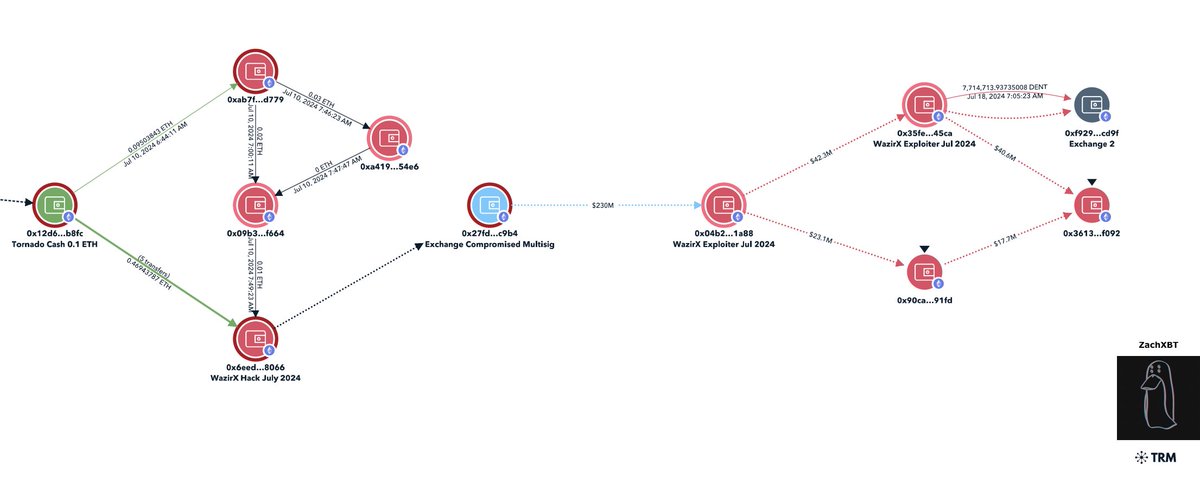
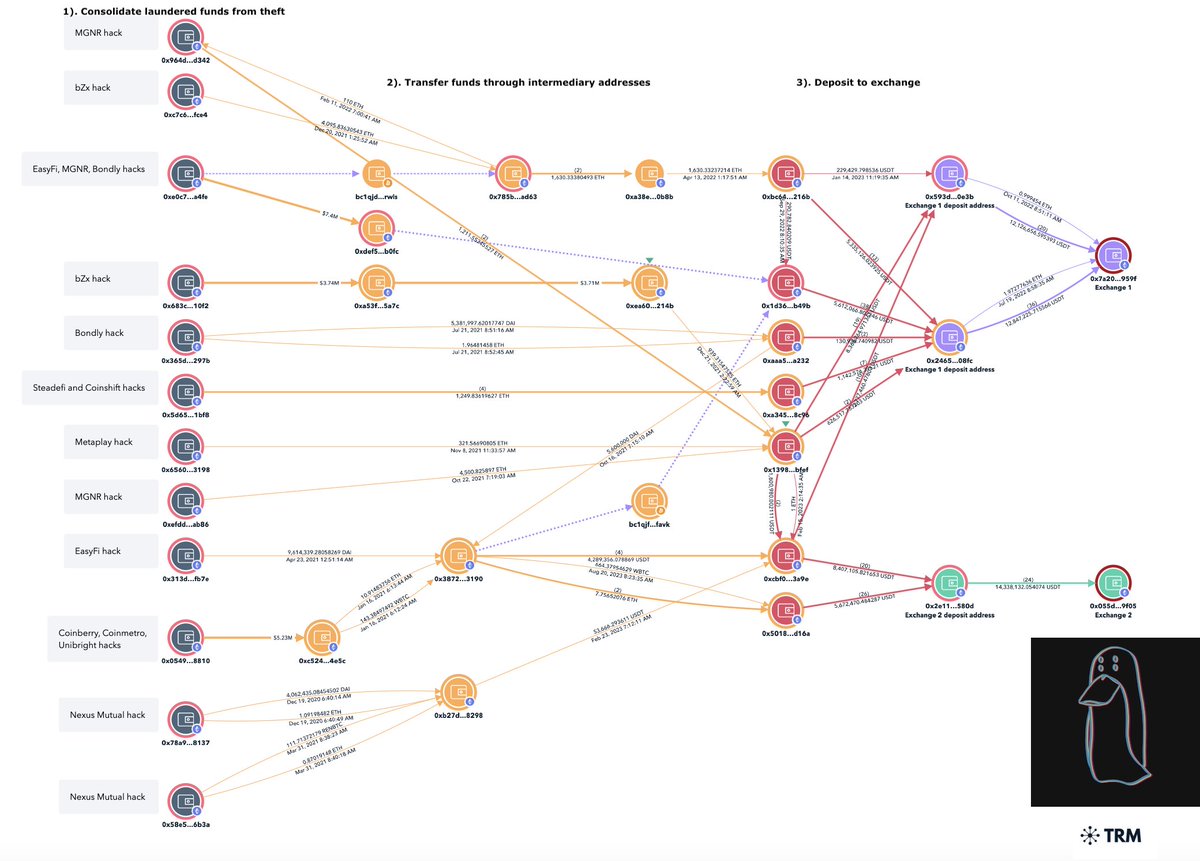
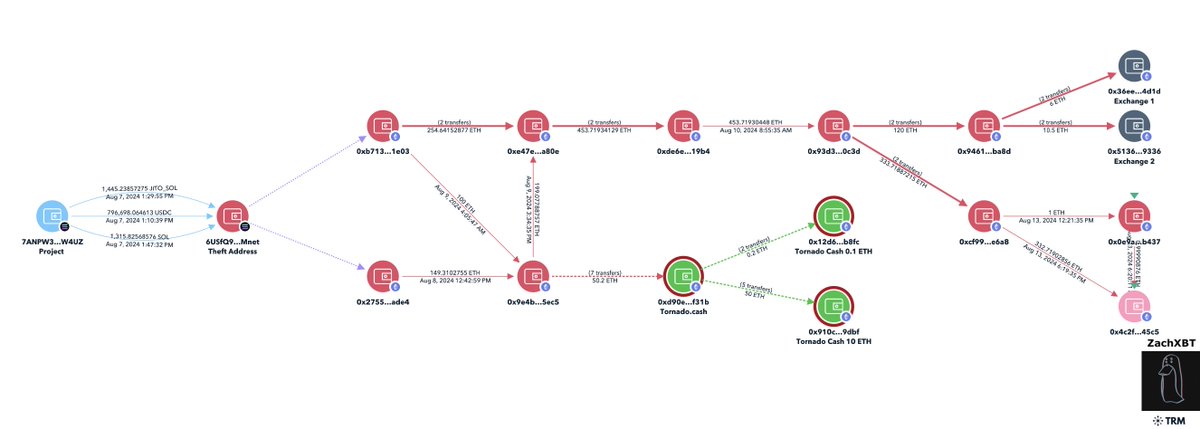
2/ The laundering path for the incident can be described as:
1) Transfer $1.3M to theft address
2) Bridge $1.3M from Solana to Etheruem via deBridge
3) Deposit 50.2 ETH to Tornado
4) Transfer 16.5 ETH to two exchanges
Theft address
6USfQ9BX33LNvuR44TXr8XKzyEgervPcF4QtZZfWMnet
1) Transfer $1.3M to theft address
2) Bridge $1.3M from Solana to Etheruem via deBridge
3) Deposit 50.2 ETH to Tornado
4) Transfer 16.5 ETH to two exchanges
Theft address
6USfQ9BX33LNvuR44TXr8XKzyEgervPcF4QtZZfWMnet
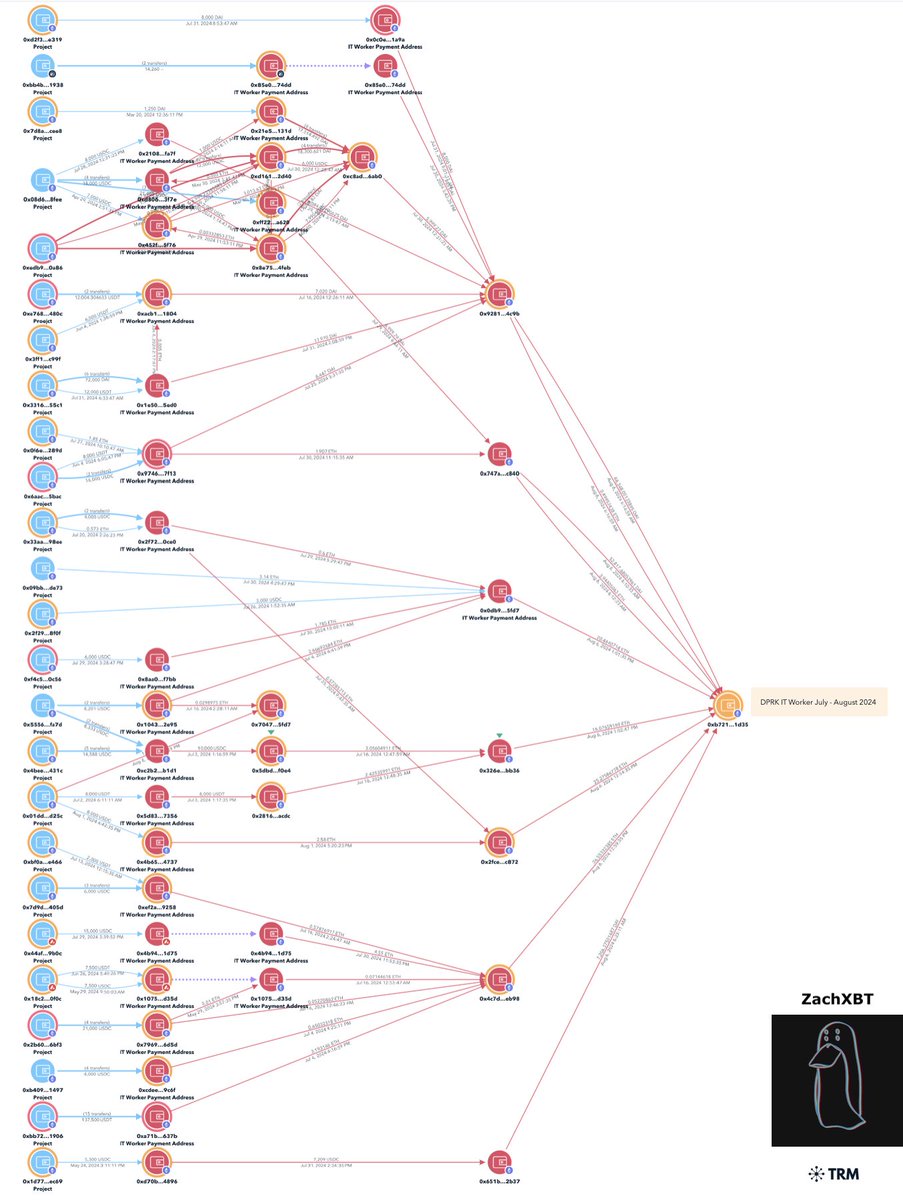
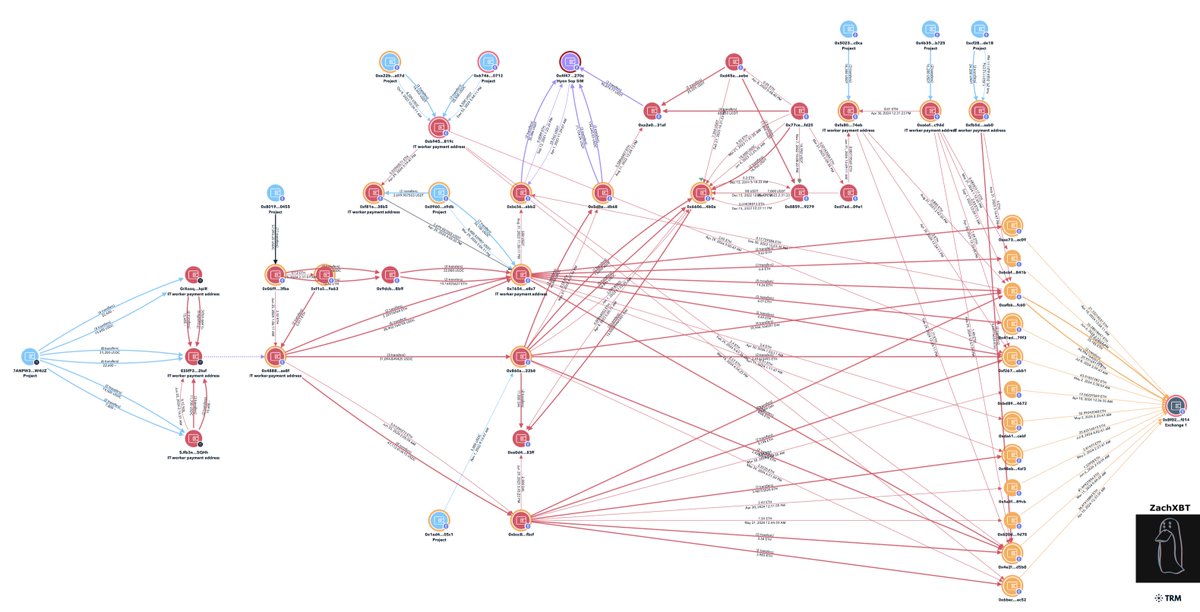
3/ Using multiple payment addresses for 21 devs I was able to map out a cluster with the most recent batch of payments for ~$375K over the last month.
0xb721adfc3d9fe01e9b3332183665a503447b1d35
In the past week you may have seen me tagging projects telling them to DM me.
0xb721adfc3d9fe01e9b3332183665a503447b1d35
In the past week you may have seen me tagging projects telling them to DM me.
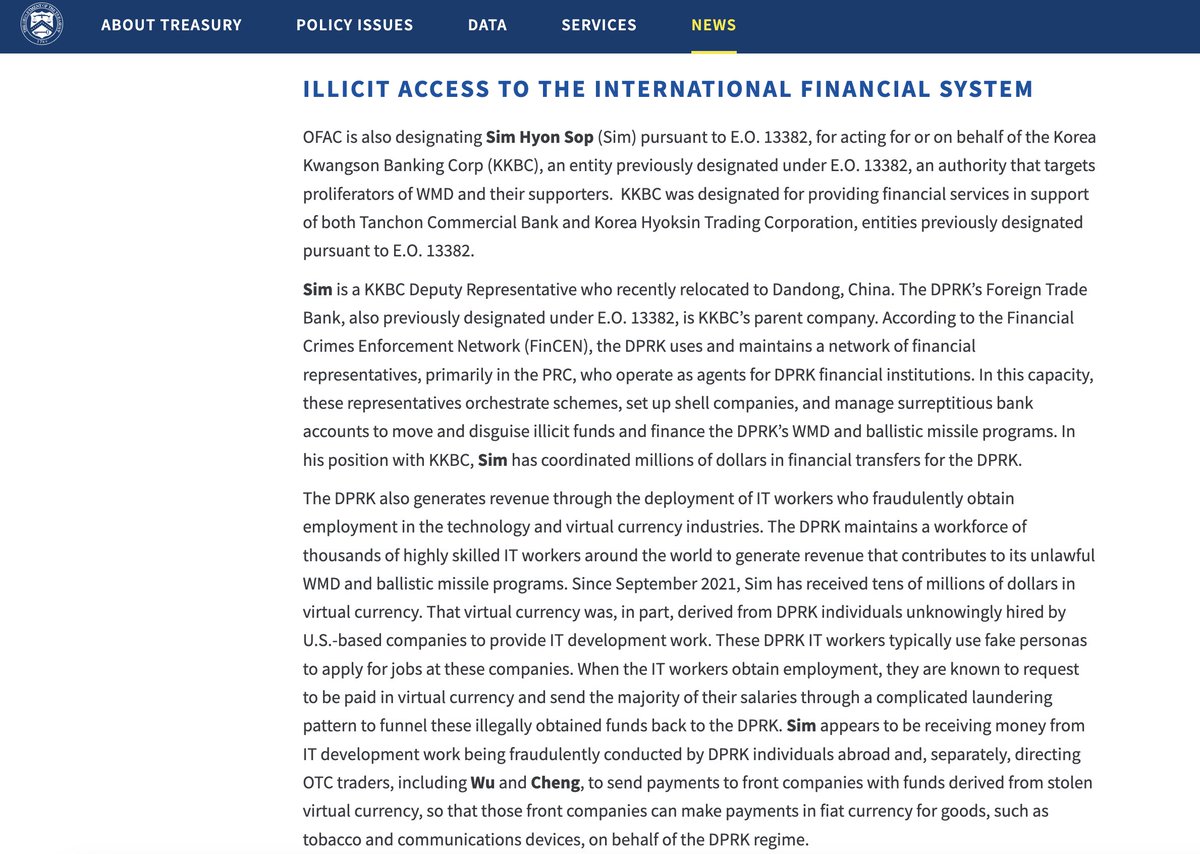
4/ Prior to this $5.5M flowed into an exchange deposit address with payments DPRK IT workers were receiving from July 2023 - 2024 and connections to Sim Hyon Sop who is OFAC sanctioned.
0x8f0212b1a77af1573c6ccdd8775ac3fd09acf014



0x8f0212b1a77af1573c6ccdd8775ac3fd09acf014

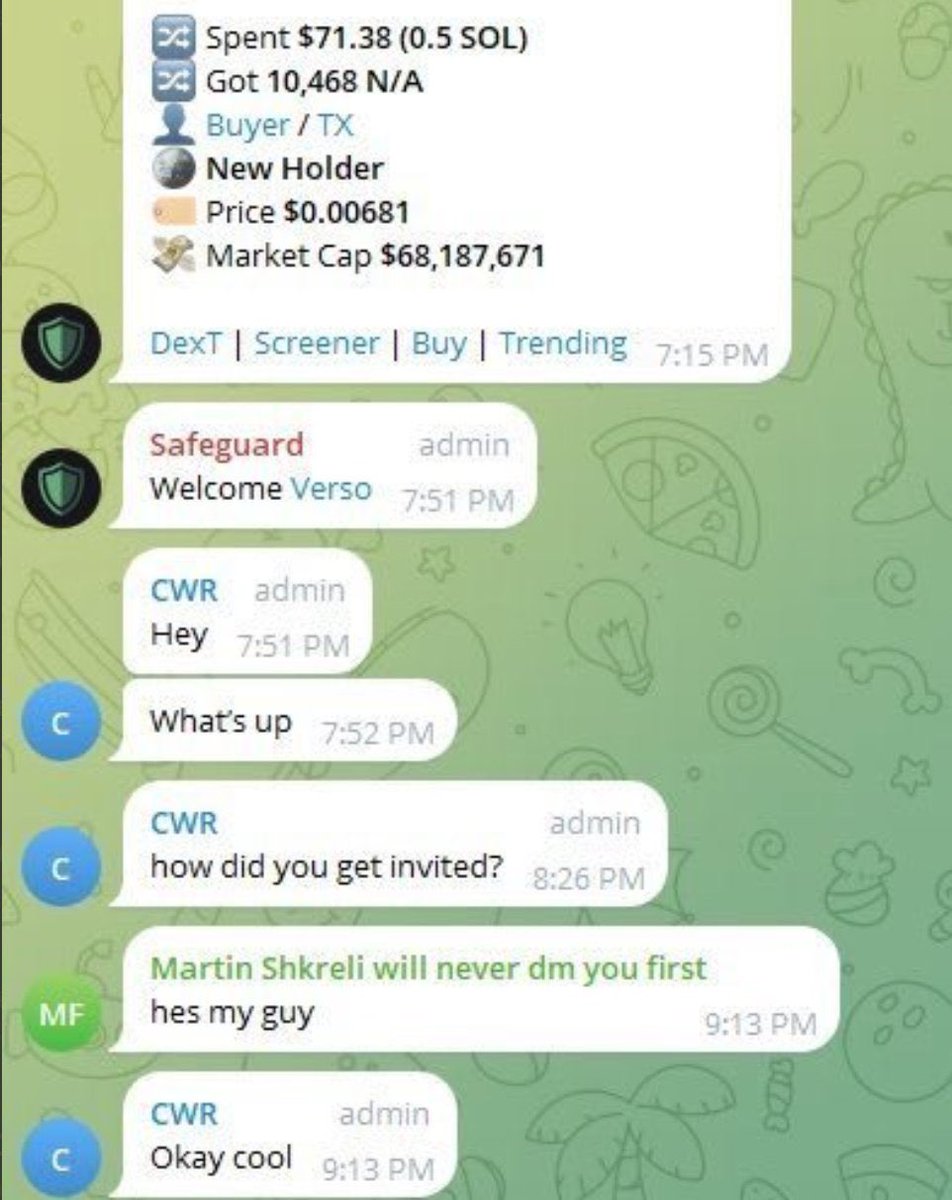
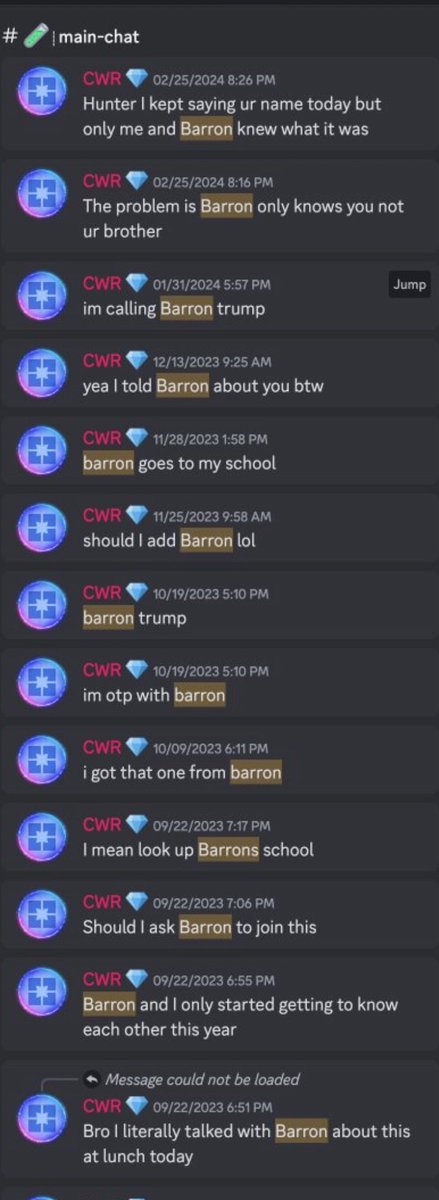
5/ Some funny moments from the investigation include:
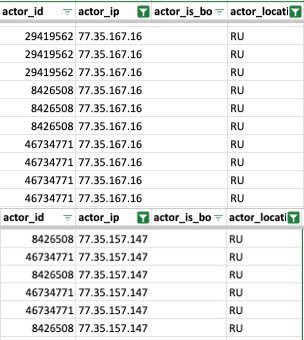
- Russia Telecom IP overlap between devs supposedly in US and Malaysia.
-Recorded dev and they accidentally leaked their other identities on a notepad
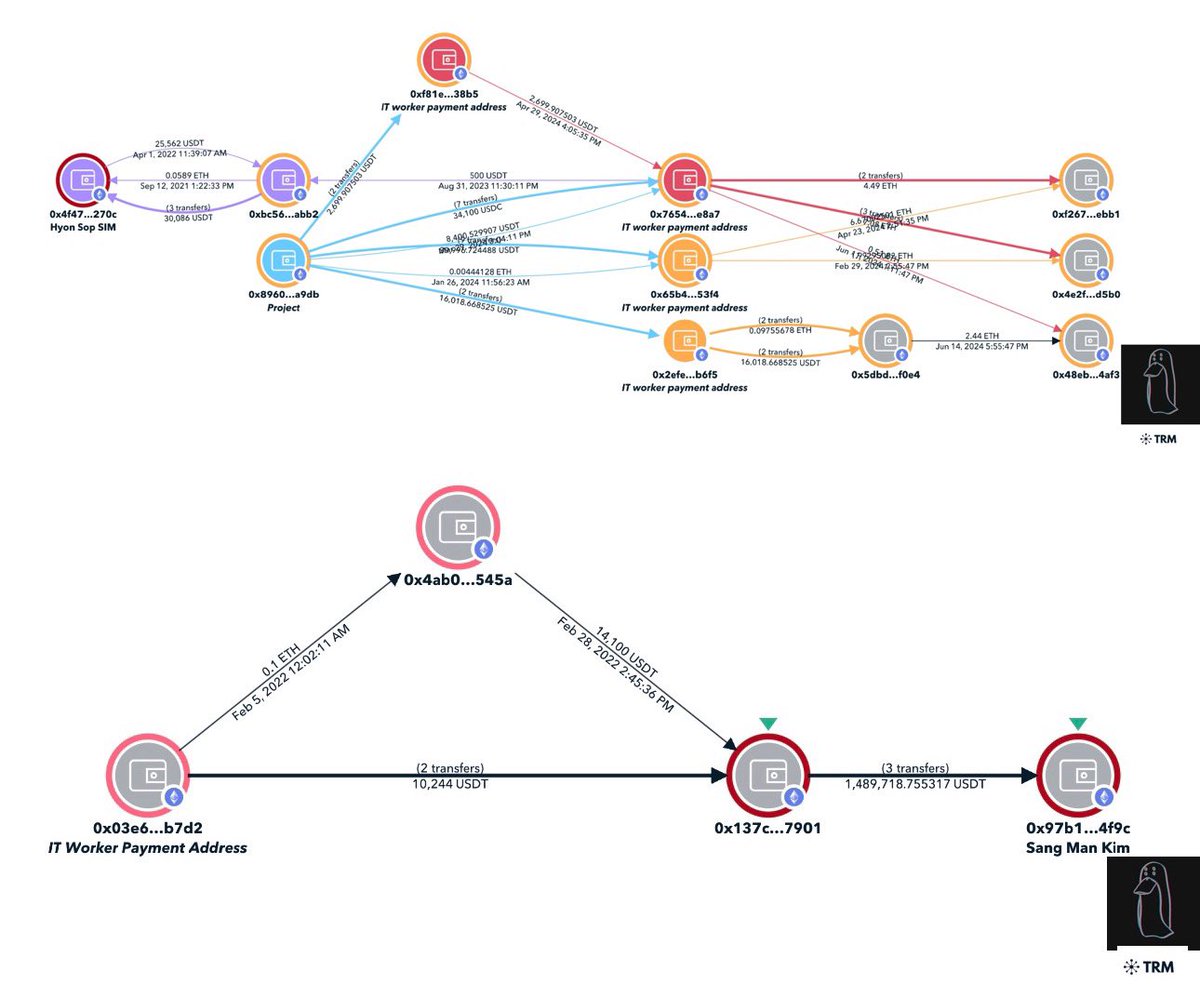
-Dev payment addresses a few hops from Sang Man Kim and Sim Hyon Sop who are on the OFAC sanctions list
-Some devs were placed by recruitment companies
-Multiple projects with 3+ IT workers who referred each other

- Russia Telecom IP overlap between devs supposedly in US and Malaysia.
-Recorded dev and they accidentally leaked their other identities on a notepad
-Dev payment addresses a few hops from Sang Man Kim and Sim Hyon Sop who are on the OFAC sanctions list
-Some devs were placed by recruitment companies
-Multiple projects with 3+ IT workers who referred each other
6/ A number of experienced teams have hired these devs so it’s not fair to them single as the ones to blame.
Some indicators teams can look out for in the future includes:
1) They refer each other for roles
2) Good looking resumes / GitHub activity although sometimes lie about work history.
3) Typically are happy to KYC but submit fake IDs in hopes teams do not investigate further
4) Ask specific questions about locations they claim to be from.
5) Dev is fired and immediately new accounts appear looking for work
6) May be good devs initially but typically start to underperform
7) Review logs
8) Like using popular NFT pfps
9) Asia accent
In case you are one of the people who calls everything attributed to North Korea a giant conspiracy.
Regardless this research proves:
A single entity in Asia is receiving $300K - $500k / month from working at 25+ projects at once by using fake identities.
Some indicators teams can look out for in the future includes:
1) They refer each other for roles
2) Good looking resumes / GitHub activity although sometimes lie about work history.
3) Typically are happy to KYC but submit fake IDs in hopes teams do not investigate further
4) Ask specific questions about locations they claim to be from.
5) Dev is fired and immediately new accounts appear looking for work
6) May be good devs initially but typically start to underperform
7) Review logs
8) Like using popular NFT pfps
9) Asia accent
In case you are one of the people who calls everything attributed to North Korea a giant conspiracy.
Regardless this research proves:
A single entity in Asia is receiving $300K - $500k / month from working at 25+ projects at once by using fake identities.
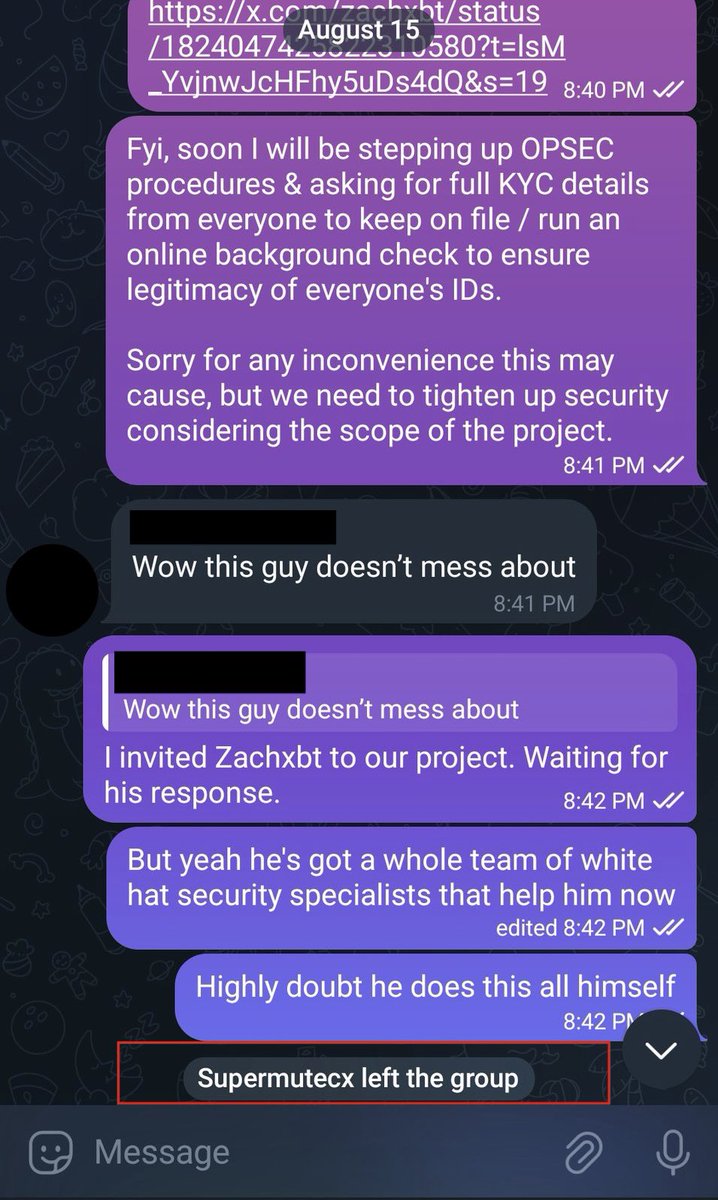
Update: Shortly after posting another project found out they had hired one of the DPRK IT worker (Naoki Murano) listed in my table and shared my post in their chat.
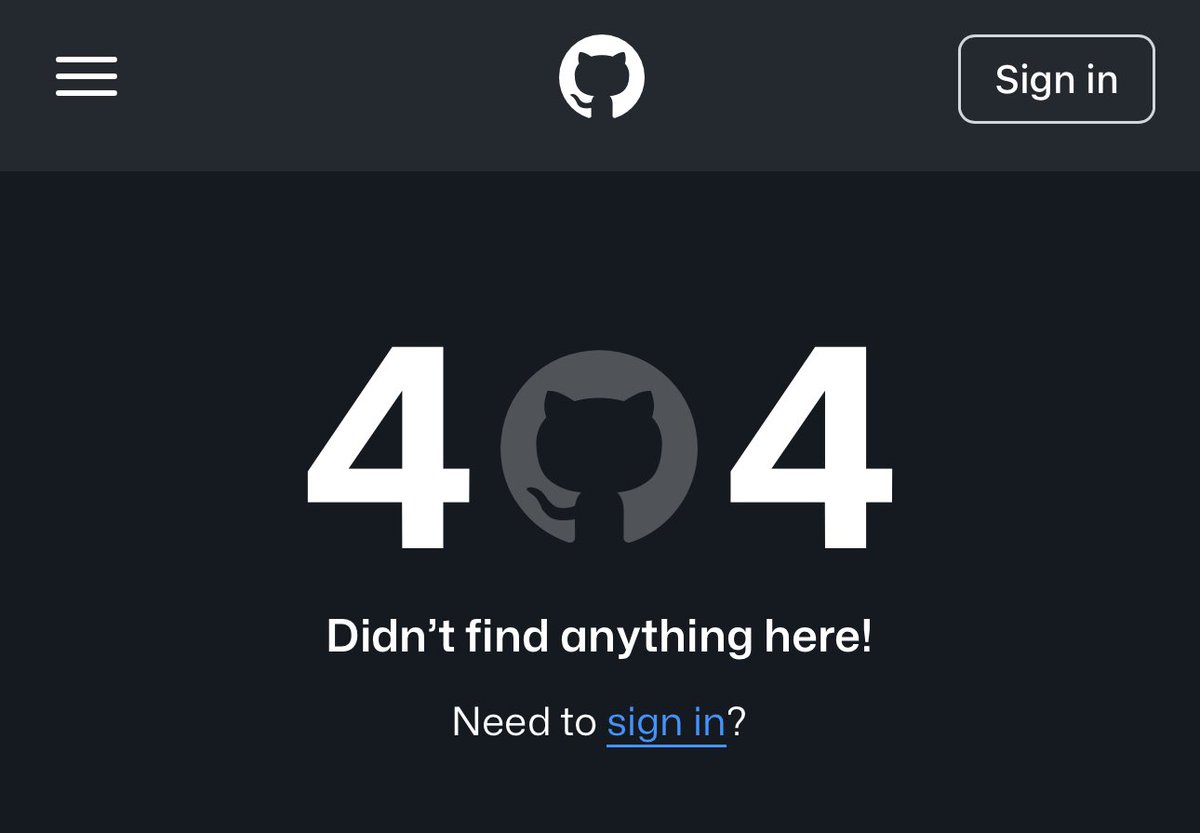
Immediately within two minutes Naoki left the chat and wiped his Github.


Immediately within two minutes Naoki left the chat and wiped his Github.
• • •
Missing some Tweet in this thread? You can try to
force a refresh