This is an absolutely wild one by @iangcarroll and @samwcyo
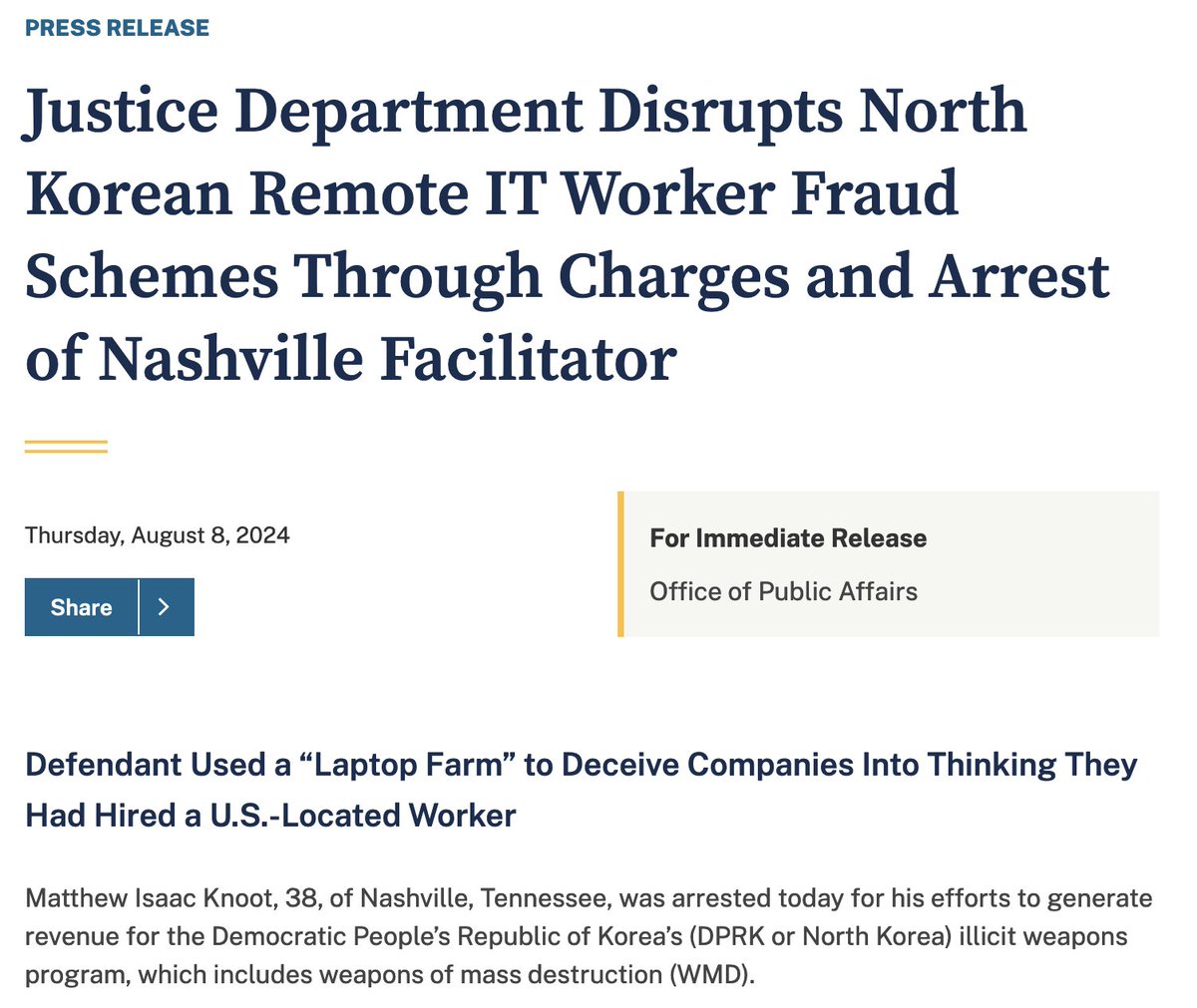
The most basic SQL injection ever in the Known Crewmember (KCM) and Cockpit Access Security System (CASS) used by airlines and TSA.
Literally ' OR 1=1 got them admin access. Here's what we know:
The most basic SQL injection ever in the Known Crewmember (KCM) and Cockpit Access Security System (CASS) used by airlines and TSA.
Literally ' OR 1=1 got them admin access. Here's what we know:
@iangcarroll @samwcyo The vulnerability was found in FlyCASS, a web-based interface used by smaller airlines to manage KCM and CASS.
A simple SQL injection in the login page allowed unauthorized access to the admin panel for Air Transport International.
A simple SQL injection in the login page allowed unauthorized access to the admin panel for Air Transport International.

@iangcarroll @samwcyo Once inside, the Ian and Sam discovered they could add or modify employee records without any additional authentication.
This meant they could potentially add anyone as an authorized to this system. Or swap exting pilot's photos.
This meant they could potentially add anyone as an authorized to this system. Or swap exting pilot's photos.

@iangcarroll @samwcyo The researchers stated they believe an attacker could potentially bypass security screening and gain access to commercial airline cockpits by exploiting this vulnerability.
@iangcarroll @samwcyo The issue was responsibly disclosed to the Department of Homeland Security on April 23rd.
FlyCASS was subsequently disabled in KCM/CASS and later remediated the issues.
FlyCASS was subsequently disabled in KCM/CASS and later remediated the issues.
@iangcarroll @samwcyo However, the disclosure process wasn't smooth. DHS stopped responding to the researchers.
The TSA press office issued statements that contradicted the researchers' findings. - which they they retracted.
The TSA press office issued statements that contradicted the researchers' findings. - which they they retracted.

@iangcarroll @samwcyo The TSA claimed that a vetting process for new KCM members would prevent exploitation, but this doesn't account for manual employee ID entry at checkpoints or the ability to modify existing user records.
Web Archive: web.archive.org/web/2022081008…

Web Archive: web.archive.org/web/2022081008…

@iangcarroll @samwcyo Other potential attack vectors included changing photos and names of existing KCM members or enrolling unenrolled KCM barcodes to employee IDs through the KCM website. 

@iangcarroll @samwcyo Web hackers - when was the last time you saw ' OR 1=1 work outside of purposefully vulnerable web apps? It's been a while for me.
@iangcarroll @samwcyo Wild one, thanks Ian and Sam - SOLID work, and glad you shared it publicly.
Read up - ian.sh/tsa
Read up - ian.sh/tsa
@iangcarroll @samwcyo I sent this out in my newsletter on Friday. Join 15k+ other folks who got it then if you're into that sort of thing (I really appreciate the support)
vulnu.com
vulnu.com
• • •
Missing some Tweet in this thread? You can try to
force a refresh