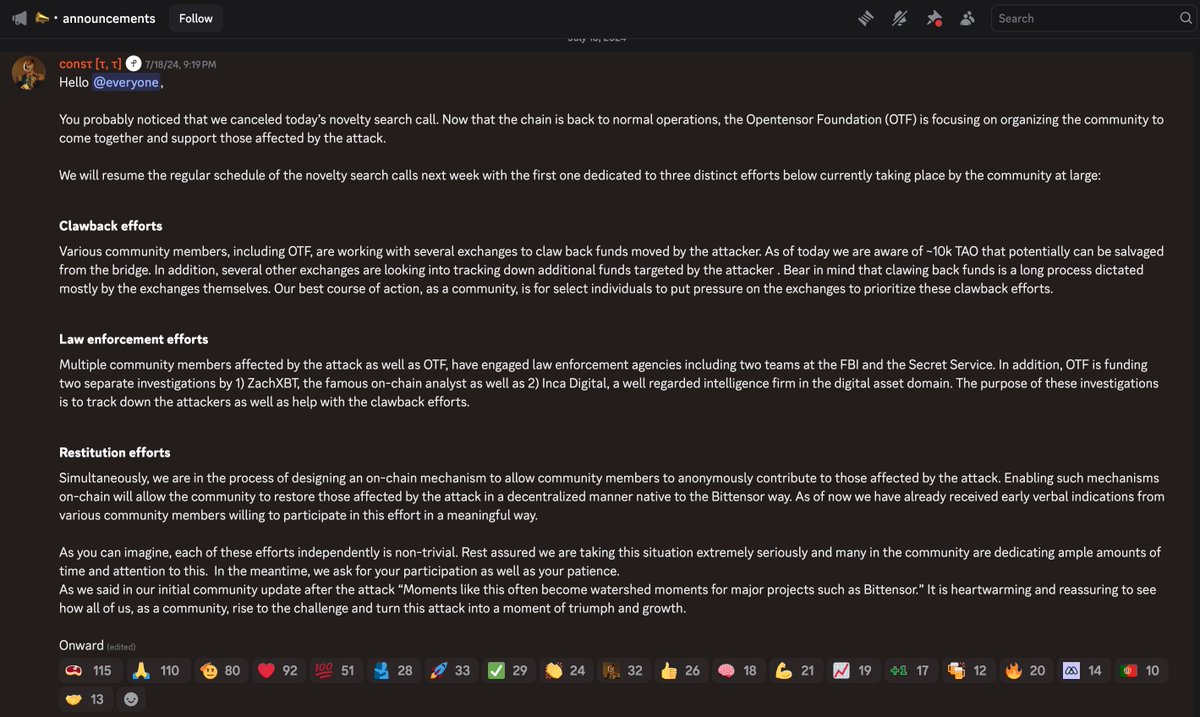
1/ An investigation into how Greavys (Malone Iam), Wiz (Veer Chetal), and Box (Jeandiel Serrano) stole $243M from a single person last month in a highly sophisticated social engineering attack and my efforts which have helped lead to multiple arrests and millions frozen. 



2/ Incident Summary: On August 19, 2024 the threat actors targeted a single Genesis creditor by:
1) Calling as Google Support via spoofed number to compromise personal accounts
2) Calling after as Gemini support claiming account is hacked
3) Social engineered victim into resetting 2FA and sending Gemini funds to compromised wallet
4) Got victim to use AnyDesk to share screen and leaked private keys from Bitcoin core.
Gemini txn hash
59.34 BTC - Aug 19 at 1:48 am UTC
e747b963a463334c164b0a8fff844f73693272bb2b331adbe2147d70ec196360
14.88 BTC - Aug 19 at 2:30 am UTC
7c7ebed785f0b4d4335d559b14b8215862fbe29db329e3ee0f2a7e64a16ce9e3


1) Calling as Google Support via spoofed number to compromise personal accounts
2) Calling after as Gemini support claiming account is hacked
3) Social engineered victim into resetting 2FA and sending Gemini funds to compromised wallet
4) Got victim to use AnyDesk to share screen and leaked private keys from Bitcoin core.
Gemini txn hash
59.34 BTC - Aug 19 at 1:48 am UTC
e747b963a463334c164b0a8fff844f73693272bb2b331adbe2147d70ec196360
14.88 BTC - Aug 19 at 2:30 am UTC
7c7ebed785f0b4d4335d559b14b8215862fbe29db329e3ee0f2a7e64a16ce9e3



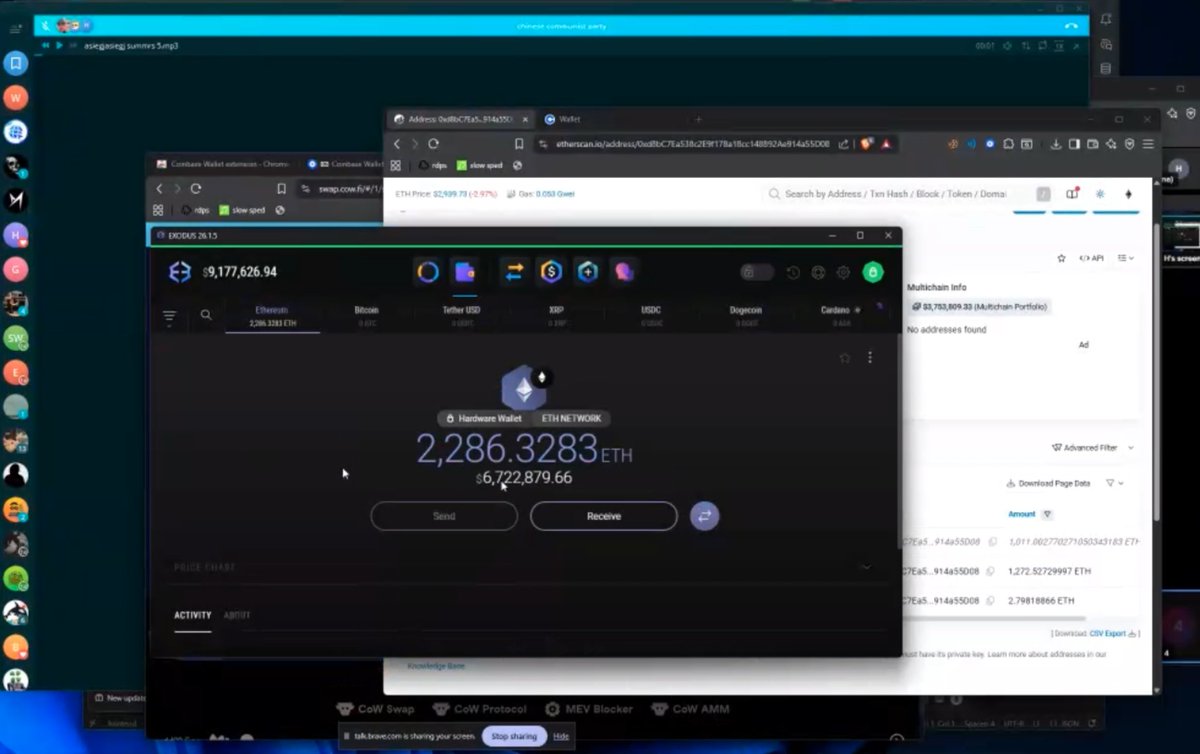
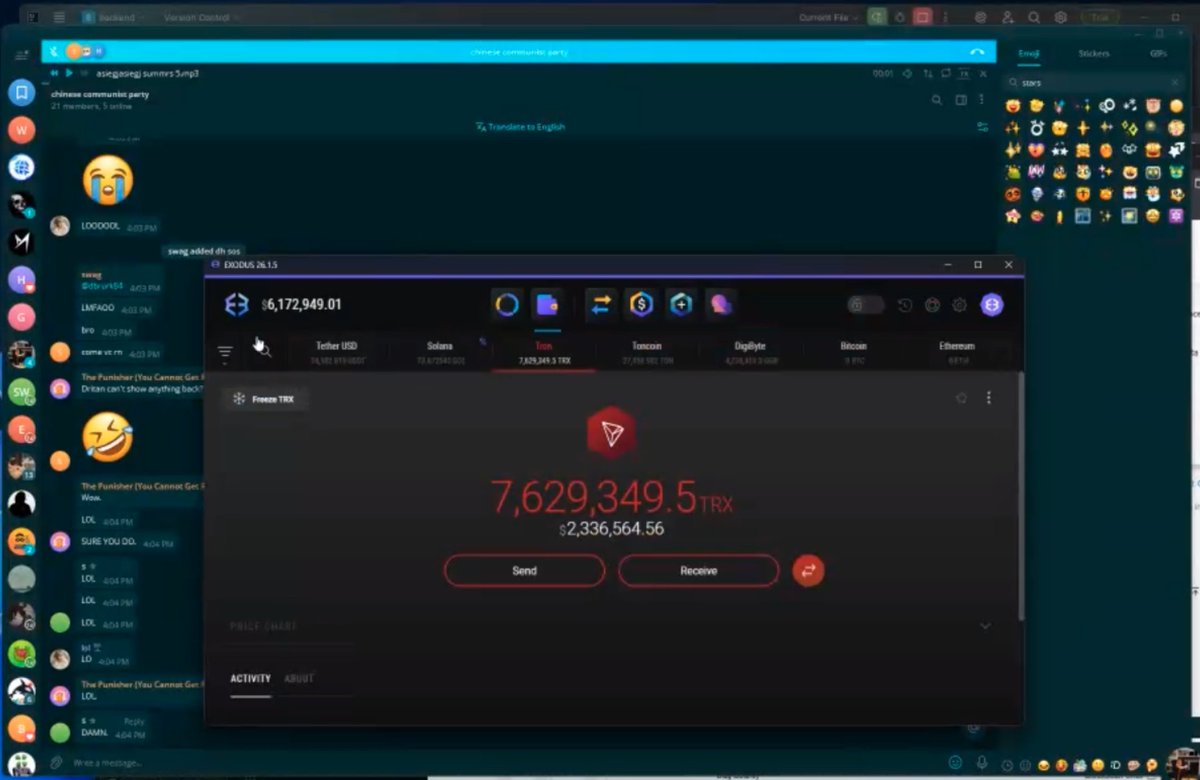
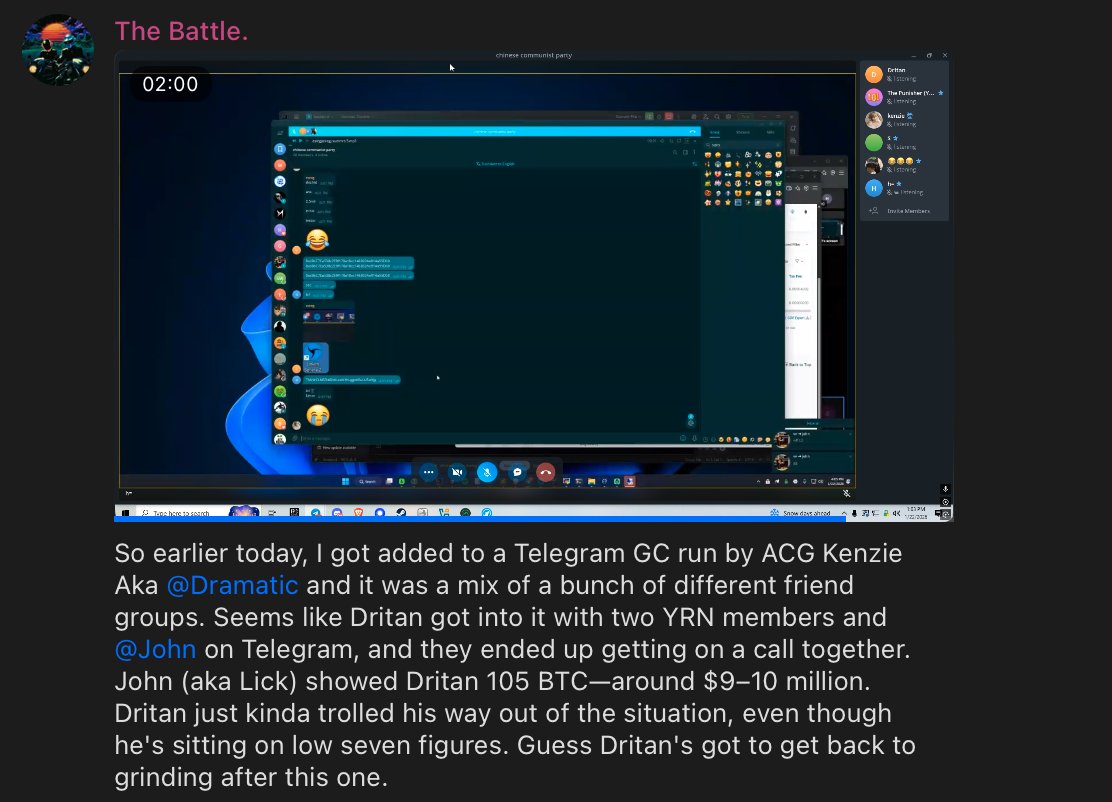
3/ Here is a private video recording showing the live reaction by multiple of the threat actors to receiving $238M.
Theft txn hash
4064 BTC - Aug 19 at 4:05 am UTC
4b277ba298830ea538086114803b9487558bb093b5083e383e94db687fbe9090
Theft txn hash
4064 BTC - Aug 19 at 4:05 am UTC
4b277ba298830ea538086114803b9487558bb093b5083e383e94db687fbe9090
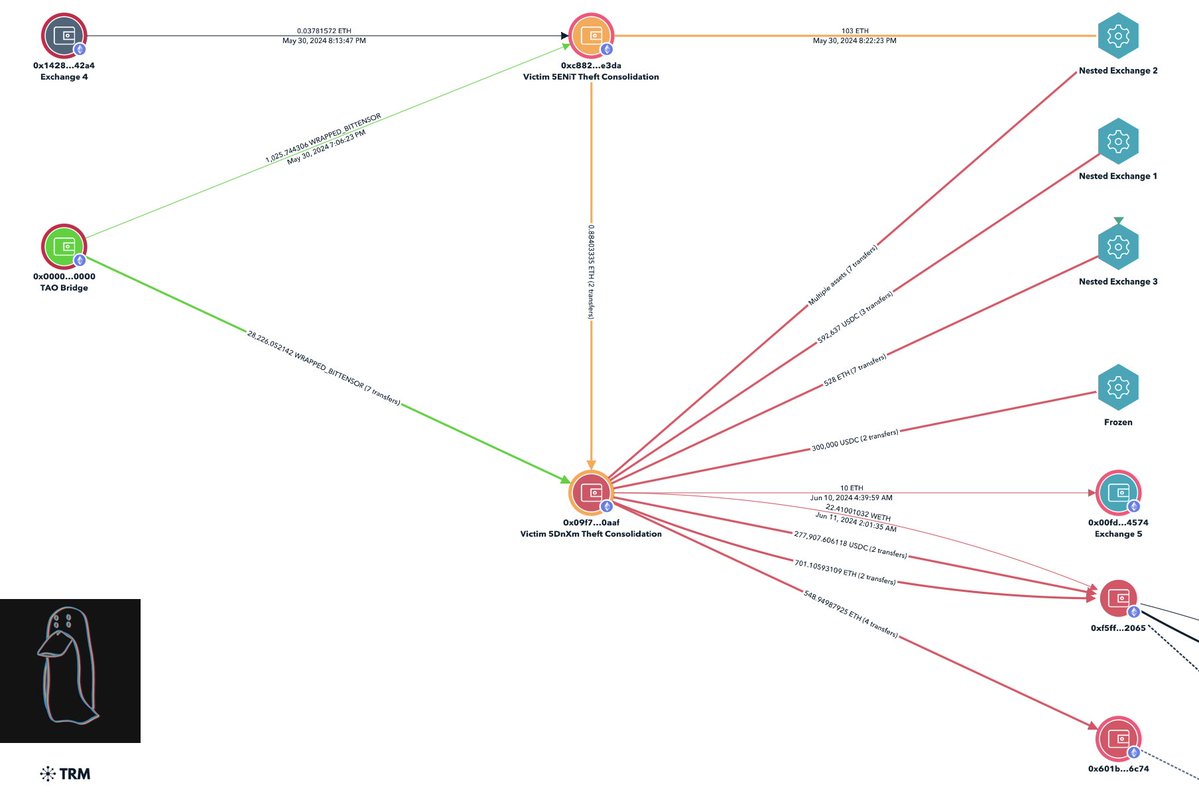
4/ An initial tracing showed $243M split multiple ways between each party before funds quickly peeled off to 15+ exchanges immediately swapping back and forth between Bitcoin, Litecoin, Ethereum, and Monero. 

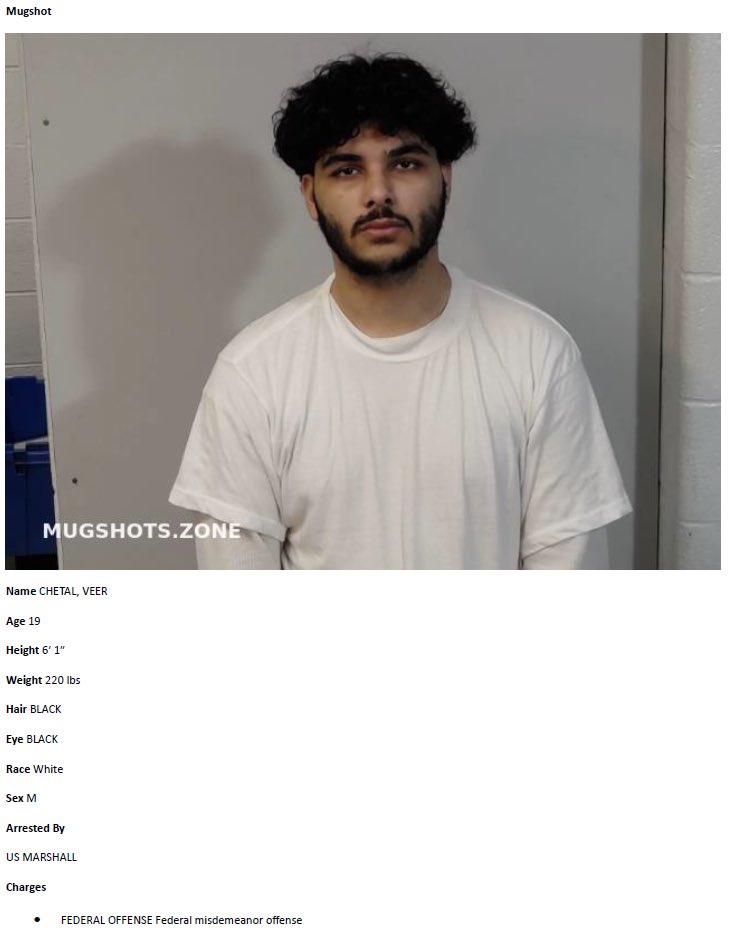
5/ Wiz (Veer) received a large % cut from theft and slipped up during screenshare by leaking his full name during the theft.
Additional comfort was gained as throughout multiple recordings accomplices referred to him as Veer on audio and in chats.
$34.5M of his funds sit here
0x3c7a5f2795e73d2b94a9120a643f608cfc45c935

Additional comfort was gained as throughout multiple recordings accomplices referred to him as Veer on audio and in chats.
$34.5M of his funds sit here
0x3c7a5f2795e73d2b94a9120a643f608cfc45c935


6/ Wiz’s friend Light/Dark (Aakaash) helped launder the funds for him using eXch and Thorswap.
Similar to Wiz he also leaked his name during screen share.
Wiz TC Destination address confirmed in video
0xa212d7441fed6db9ab666ba34e8c440c565f4af8
Similar to Wiz he also leaked his name during screen share.
Wiz TC Destination address confirmed in video
0xa212d7441fed6db9ab666ba34e8c440c565f4af8
7/ Greavys (Malone) lives a flashy lifestyle with the stolen funds having purchased 10+ cars and going out to clubs in LA and Miami with friends spending $250K-500K / night and giving out Birkin bags to girls.
During video clips and in chats multiple people refer to him as Malone and was flexing stolen funds on Discord.
Currently $3.5M tied to Greavys sits here
0x21d7d256be564191a43553e574c06a4d0e629767


During video clips and in chats multiple people refer to him as Malone and was flexing stolen funds on Discord.
Currently $3.5M tied to Greavys sits here
0x21d7d256be564191a43553e574c06a4d0e629767


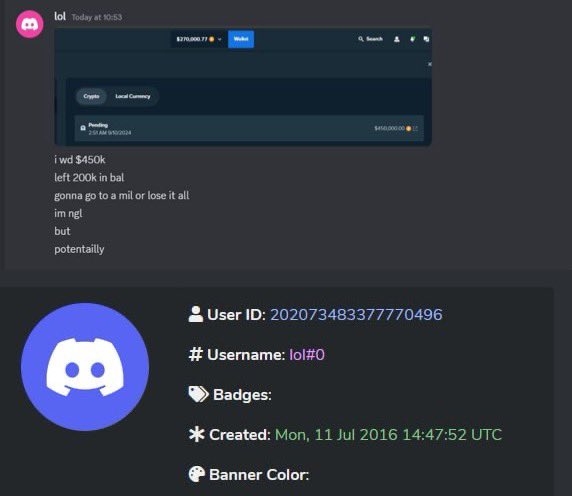
8/ Greavys was located via OSINT in LA/Miami due to friends/girls posting his location on social media each night.
He also has an Instagram account where he posted photos of himself using his name earlier this year.

He also has an Instagram account where he posted photos of himself using his name earlier this year.


9/ Box (Jeandiel/John) played a role by calling the victim as the Gemini exchange rep.
On Discord, Telegram, and other platform Box reuses the same pfp.
Currently $18M tied to Box sits here
0x98b0811e2cc7530380caf1a17440b18f71f51f4e
Danny Trauma (Danish) was active in the inner Telegram chat as Meech although it’s not immediately clear his exact role although it is known he has access to multiple bankruptcy dbs.
His ex-gf leaked all of his photos on social media however so his info has been public.

On Discord, Telegram, and other platform Box reuses the same pfp.
Currently $18M tied to Box sits here
0x98b0811e2cc7530380caf1a17440b18f71f51f4e
Danny Trauma (Danish) was active in the inner Telegram chat as Meech although it’s not immediately clear his exact role although it is known he has access to multiple bankruptcy dbs.
His ex-gf leaked all of his photos on social media however so his info has been public.


10/ A cluster of eth addresses tied to both Box/Wiz received $41M+ from two exchanges over the past few weeks primarily flowing to luxury goods brokers to purchase cars, watches, jewelry, and designer clothes.
This is also backed up by what was said in chats about spending the funds.

This is also backed up by what was said in chats about spending the funds.


11/ While most of the funds were converted to XMR both Box and Wiz accidentally linked the laundered funds with the dirty funds on multiple instances.
a) Wiz during screenshare showed an address he sent funds to for designer clothes which had millions in exposure to the cluster above.
0xb98b8ac004cea6617adcf3e94106d0eec1792bd9
b) Box linked the dirty funds with the cleans funds by accidentally reusing a deposit address.
0x6d865235ebb2504d3478fc1dd839100d210144df

a) Wiz during screenshare showed an address he sent funds to for designer clothes which had millions in exposure to the cluster above.
0xb98b8ac004cea6617adcf3e94106d0eec1792bd9
b) Box linked the dirty funds with the cleans funds by accidentally reusing a deposit address.
0x6d865235ebb2504d3478fc1dd839100d210144df


12/ With the assistance of @CFInvestigators @zeroshadow_io and the Binance Security Team more than $9M+ has been frozen and $500K+ has already been returned back after working closely with the victim to investigate the incident.
13/ As a result of the investigation Box and Greavys were arrested yesterday evening in Miami and LA.
I would expect law enforcement seized additional funds during the arrests due to large transfers around that period of time.

I would expect law enforcement seized additional funds during the arrests due to large transfers around that period of time.


14/ My post will be updated as the legal case progresses.
In the meantime mint a free collectible to commemorate the investigation of the stolen $243M below on Zora.
zora.co/collect/base:0…
In the meantime mint a free collectible to commemorate the investigation of the stolen $243M below on Zora.
zora.co/collect/base:0…
Update: Box (Jeandiel) and Greavys (Malone) just had the indictment for the case unsealed
justice.gov/usao-dc/pr/ind…
justice.gov/usao-dc/pr/ind…

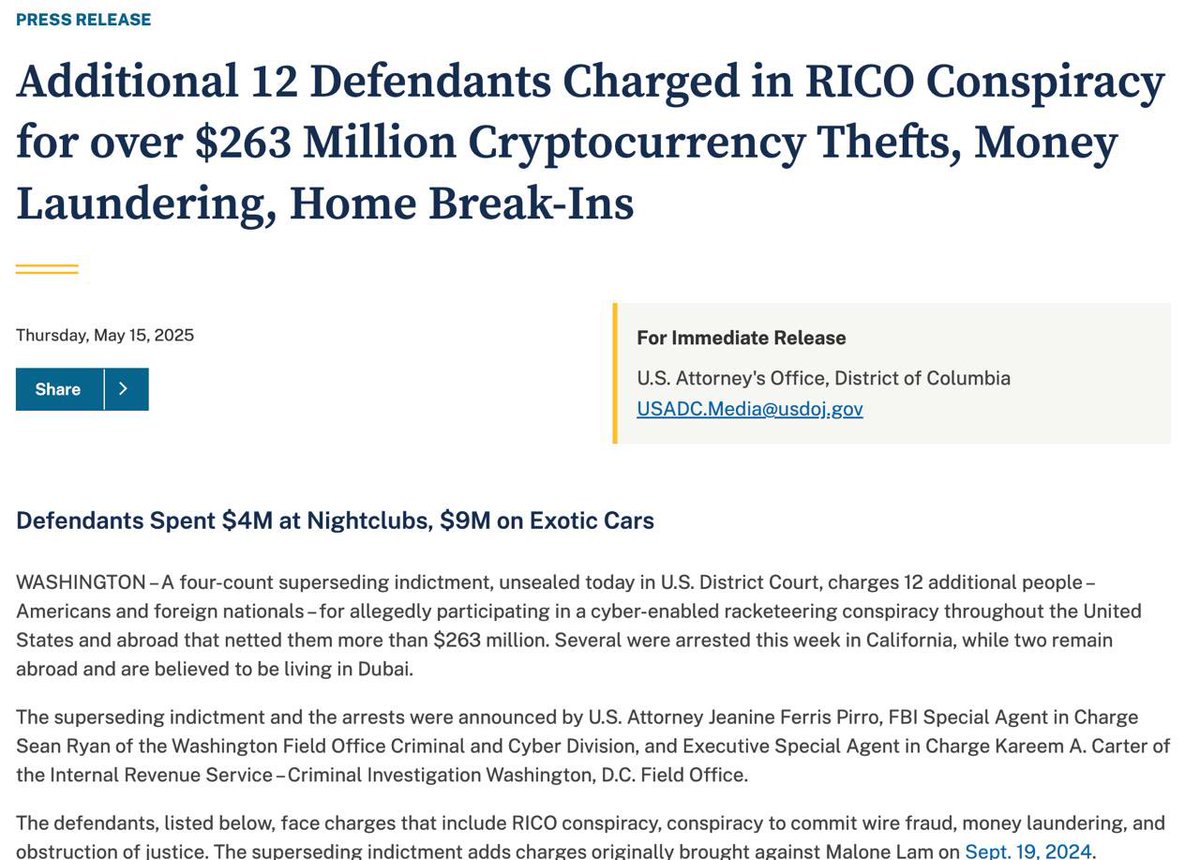
Update: Today twelve people were charged for the $243M Genesis creditor theft.
Aakaash Anand was featured in the clip on 6/ laundering funds for Veer/Wiz.

Aakaash Anand was featured in the clip on 6/ laundering funds for Veer/Wiz.

• • •
Missing some Tweet in this thread? You can try to
force a refresh