🧵Thread / 🕵️♂️ Ever wanted to hunt down APTs like #TheCom via DNS but can't be bothered with all the searching and clicking?
Want to get a list of interesting 'live' domains to investigate in under 60 seconds ⏰!!
No worries! Let's automate the process with a Python script that's fast and safe.
No APIs or expensive subscriptions needed — just 1.1.1.1 and some threading magic! 🧵👇
#ScatteredSpider #TheCom #VirtuoSpider #Phishkit #CTI #Hunting #Automation
Want to get a list of interesting 'live' domains to investigate in under 60 seconds ⏰!!
No worries! Let's automate the process with a Python script that's fast and safe.
No APIs or expensive subscriptions needed — just 1.1.1.1 and some threading magic! 🧵👇
#ScatteredSpider #TheCom #VirtuoSpider #Phishkit #CTI #Hunting #Automation
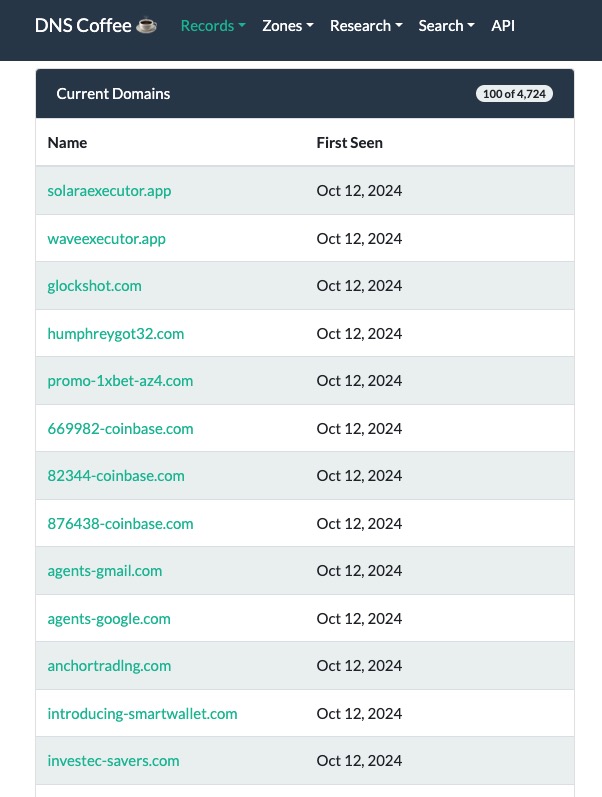
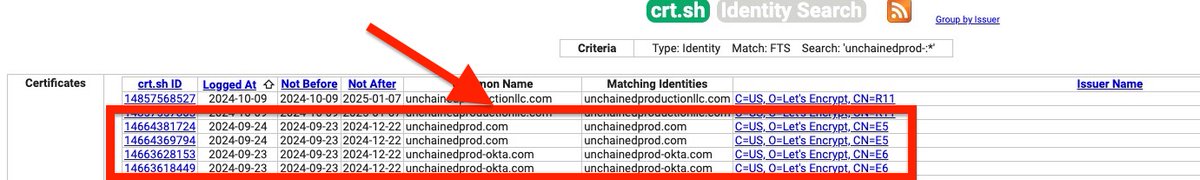
1️⃣ First, we define the nameserver we're targeting. In this case, it's ns3.my-ndns[.]com. This is where Virtuospider might be lurking! 🕸️ 
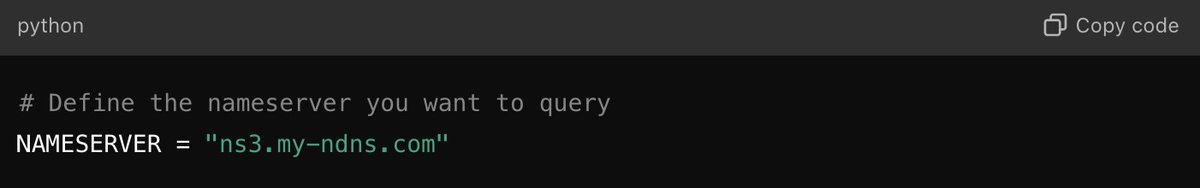
2️⃣ Next, we fetch all domains associated with this nameserver using a simple curl command.
No fancy APIs or subscriptions—just pure OSS (Open Source Simplicity)! 🌐
No fancy APIs or subscriptions—just pure OSS (Open Source Simplicity)! 🌐
3️⃣ Time to parse the data! We read the JSON response from coffee.txt and extract domain names using regular expressions. 📜🔍 

4️⃣ We clean up the domain list by removing duplicates and any known domains (if you have a known.txt file). Clean data is happy data! 🧹😄 

5️⃣ Let's process these domains! We use threading to speed things up because patience is a virtue we don't always have. 🚀 

6️⃣ For each domain, we resolve its IP address using Cloudflare's 1.1.1.1 DNS resolver.
This means we're only querying DNS records, not connecting to the domains themselves—keeping our investigation safe and stealthy! 🕵️♂️
By using 1.1.1.1, we're leveraging a fast and privacy-focused DNS service. We're simply asking, "What's the IP address for this domain?" Since DNS queries are public and don't interact with the domain's server, we're not making any direct connections that could expose us or alert the threat actors.
This means we're only querying DNS records, not connecting to the domains themselves—keeping our investigation safe and stealthy! 🕵️♂️
By using 1.1.1.1, we're leveraging a fast and privacy-focused DNS service. We're simply asking, "What's the IP address for this domain?" Since DNS queries are public and don't interact with the domain's server, we're not making any direct connections that could expose us or alert the threat actors.

7️⃣ We handle possible errors gracefully. If a domain doesn't resolve or there's a DNS issue, we catch it and log the error without stopping the script. This ensures our automation keeps running smoothly! ⚙️
Error handling is crucial! If a domain doesn't exist or there's a timeout, we catch the exception and keep going. This way, one problematic domain won't derail the entire process. It's all about resilience! 💪
Error handling is crucial! If a domain doesn't exist or there's a timeout, we catch the exception and keep going. This way, one problematic domain won't derail the entire process. It's all about resilience! 💪

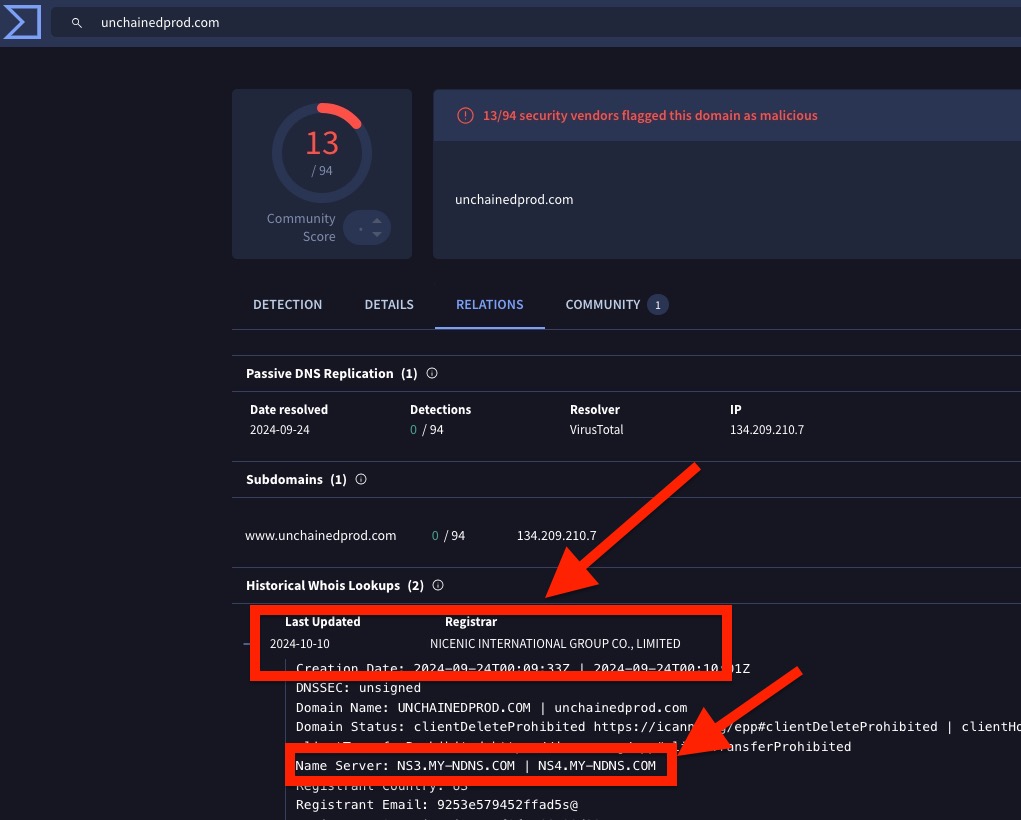
8️⃣ Without connecting to the domains, we perform an RDAP (Registration Data Access Protocol) lookup on the IP addresses. RDAP is like a modern version of WHOIS—it provides public info about who owns an IP address or domain. This helps us identify potential threats without risking direct contact. 🔎
RDAP allows us to retrieve registration details for IP addresses from public databases. We're still not connecting to the domains—just gathering publicly available info about who owns the IPs. It's like checking a phone book without making a call! 📖
RDAP allows us to retrieve registration details for IP addresses from public databases. We're still not connecting to the domains—just gathering publicly available info about who owns the IPs. It's like checking a phone book without making a call! 📖

9️⃣ We store the domain, IP, and AS Owner info. This gives us a neat summary of who's hosting what. 📄 

🔟 Now, we generate an intelligence report in PDF format, focusing on specific AS Owners (e.g., 'DigitalOcean', 'Virtuo'). Time to catch those spiders! 🕷️📊 

1️⃣1️⃣ The report includes the domain, IP, and AS Owner, making it easier to spot suspicious activity. Plus, PDFs are professional, right? 😉 

1️⃣2️⃣ And that's it! You've automated your DNS hunt for potential Spider domains, making your cyber threat intelligence gathering faster. No manual checks, no expensive tools—just Python and some creativity! 🐍💡
Ready to dive in? Here's the full script for you to try out! 👉 pastebin.com/GVpQcxZw
Ready to dive in? Here's the full script for you to try out! 👉 pastebin.com/GVpQcxZw
• • •
Missing some Tweet in this thread? You can try to
force a refresh