Author - The Intent Model (Kindle Books) | Malware Geek | Curated Intel Member | Threat Intelligence Expert Extraordinaire
How to get URL link on X (Twitter) App

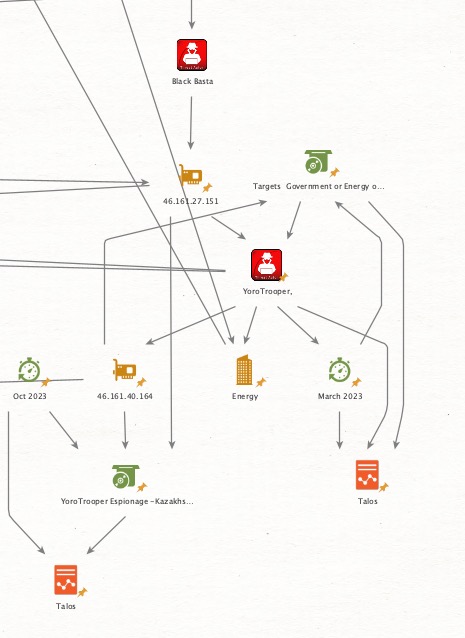
 Thread 2/ Keys to the Kingdom: A Deepening Threat in the #Energy Sector 🔍
Thread 2/ Keys to the Kingdom: A Deepening Threat in the #Energy Sector 🔍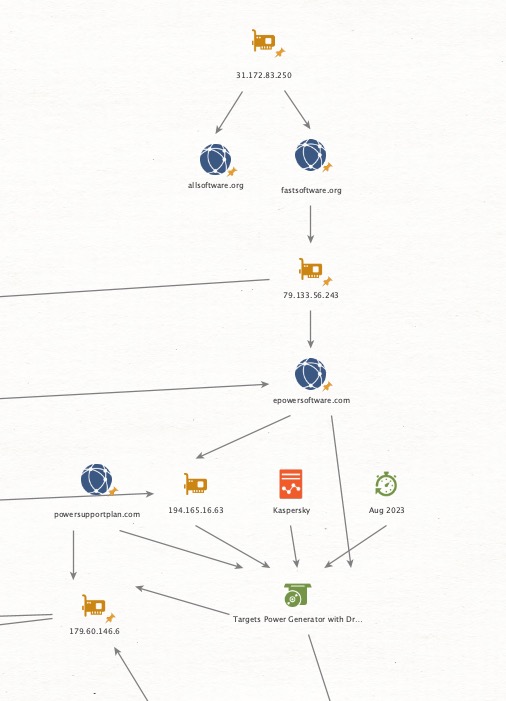
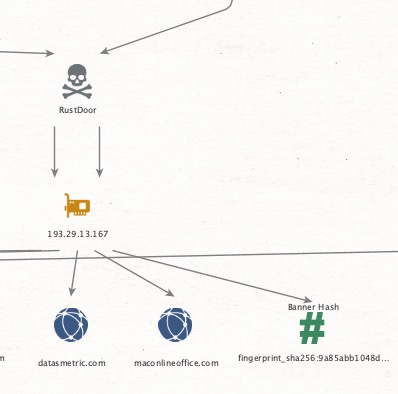
 2/ 🔎 Research Shift: Switched to FOFA, and it’s been a game-changer! #Fofa identified Port 22 (SSH) open on the IP, leading to a deep dive into public key fingerprints 🔑
2/ 🔎 Research Shift: Switched to FOFA, and it’s been a game-changer! #Fofa identified Port 22 (SSH) open on the IP, leading to a deep dive into public key fingerprints 🔑

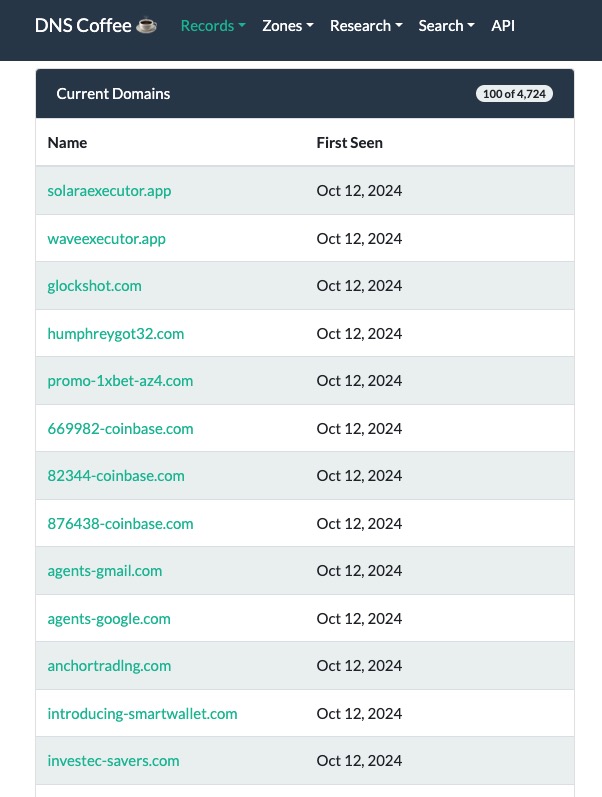
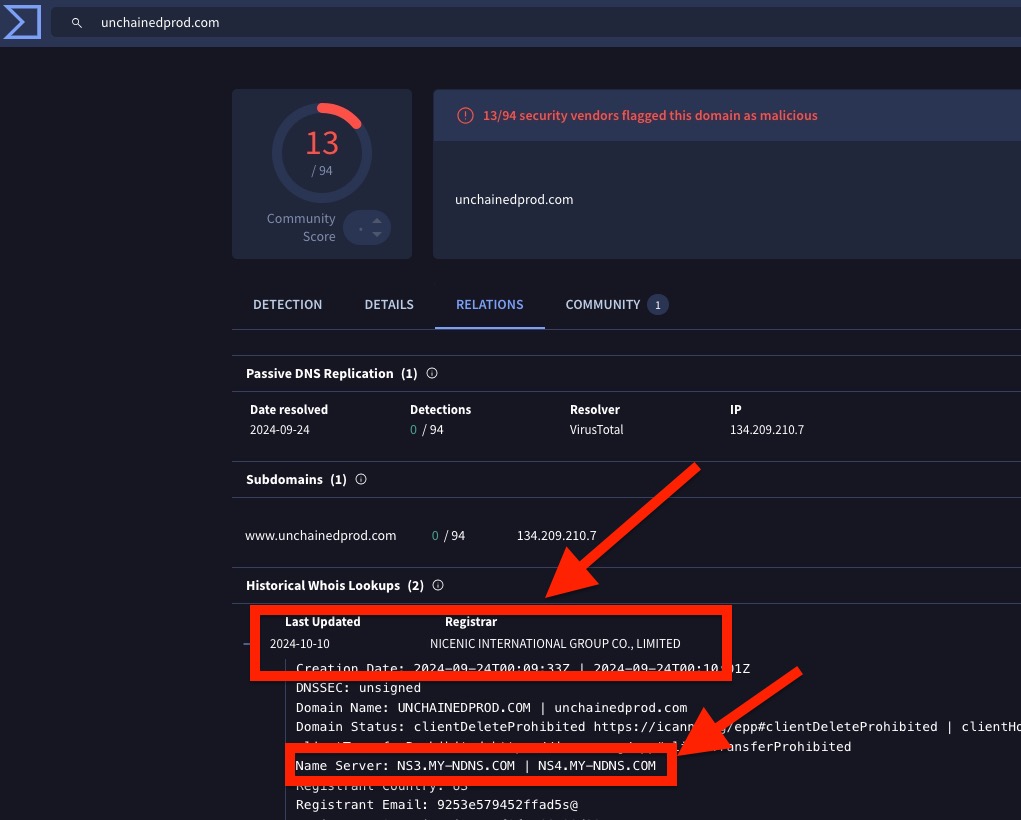
 🧵 Thread 2 / Each day, a list of new domains will appear in dns[.]coffee. Here's what we're looking for when trying to find the needle in the haystack🪡:
🧵 Thread 2 / Each day, a list of new domains will appear in dns[.]coffee. Here's what we're looking for when trying to find the needle in the haystack🪡: