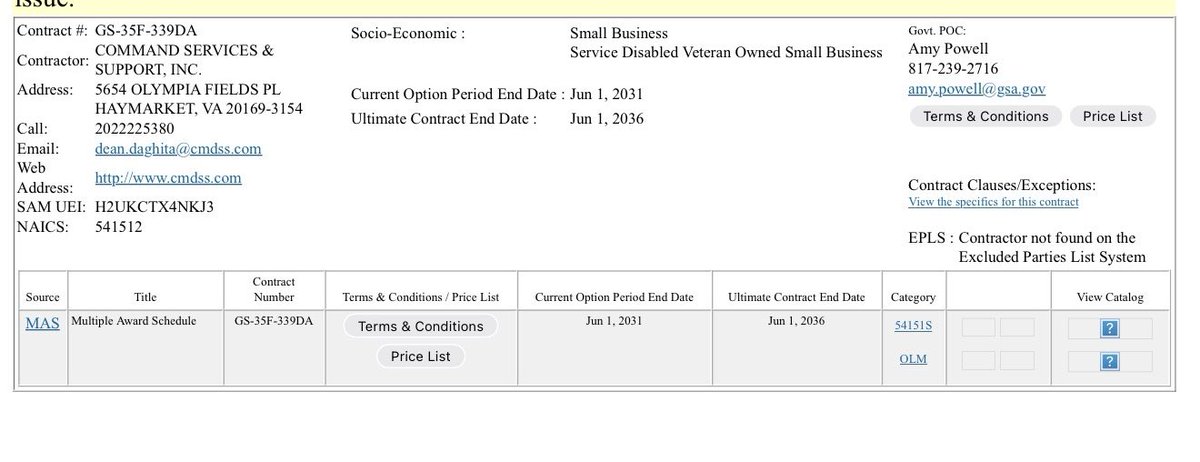
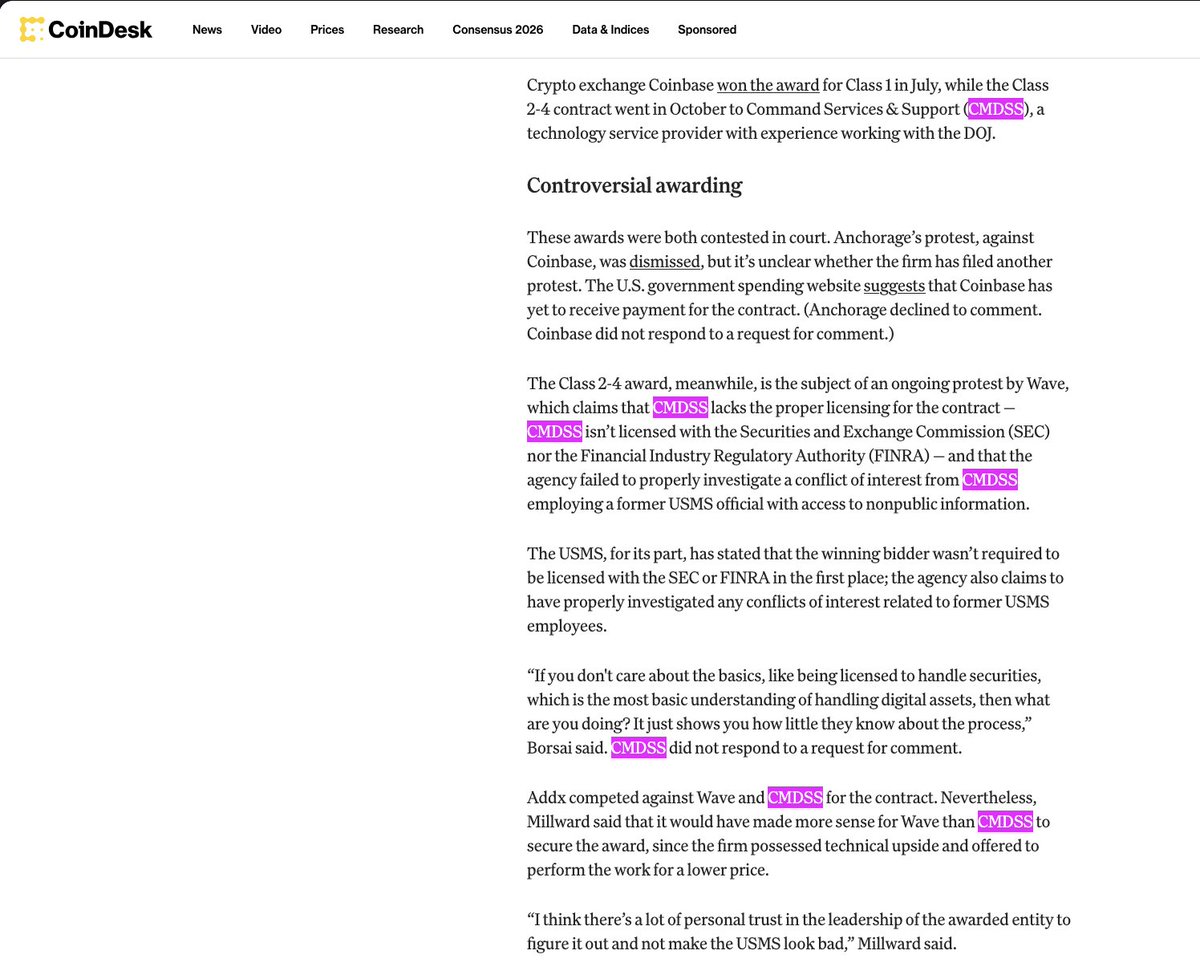
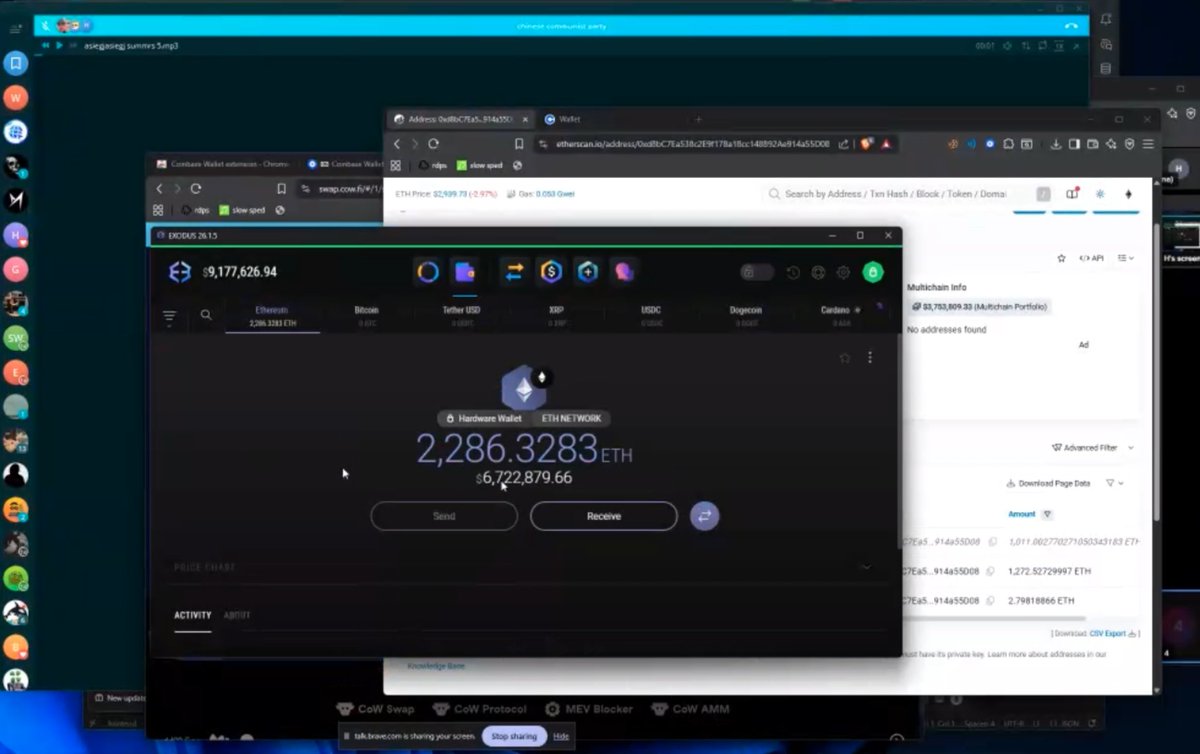
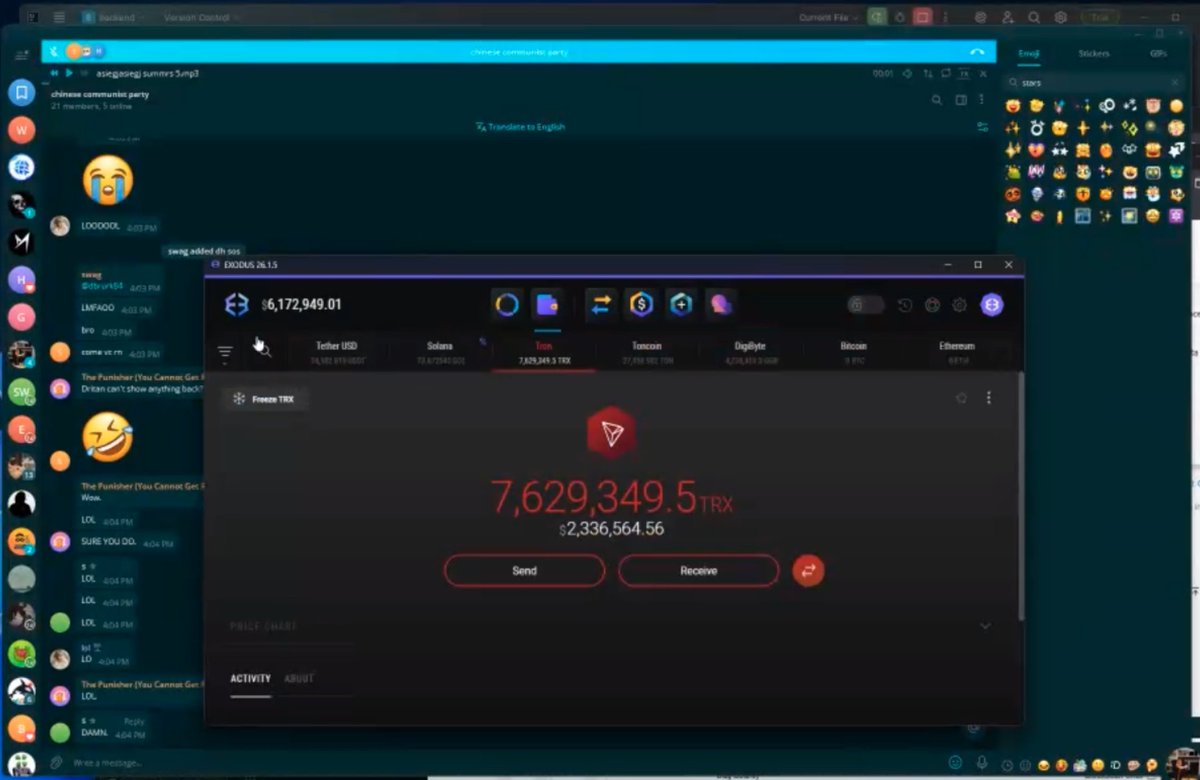
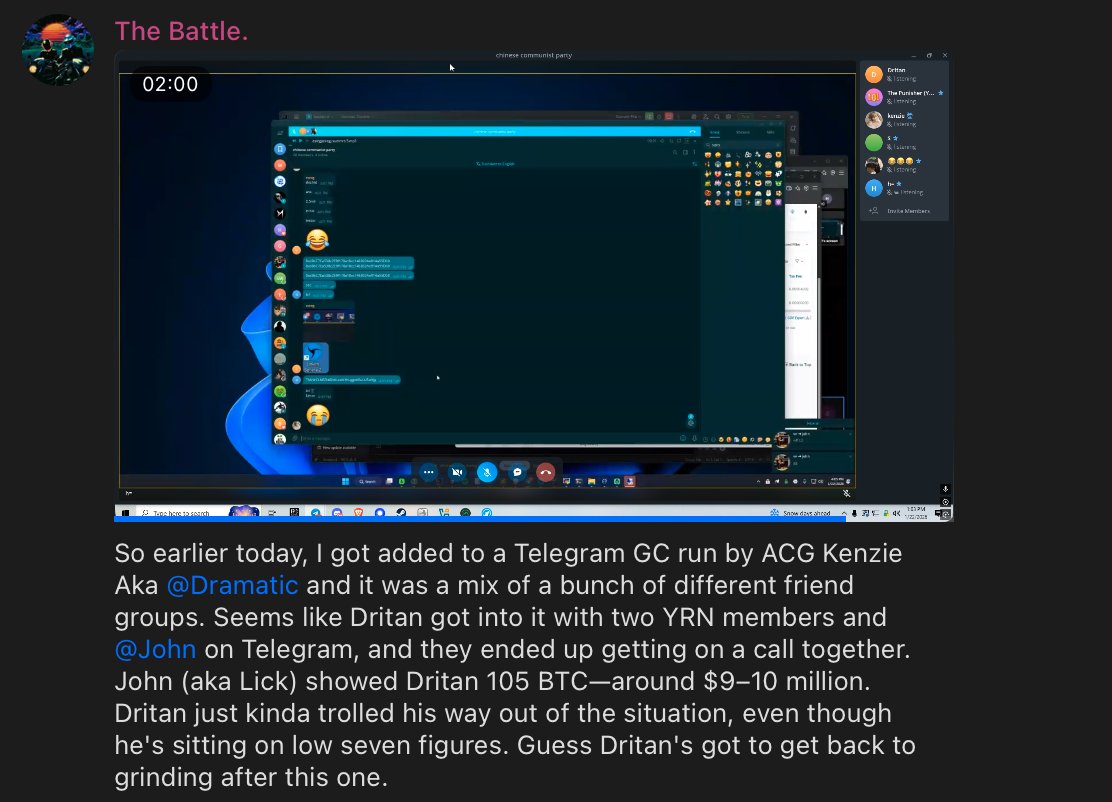
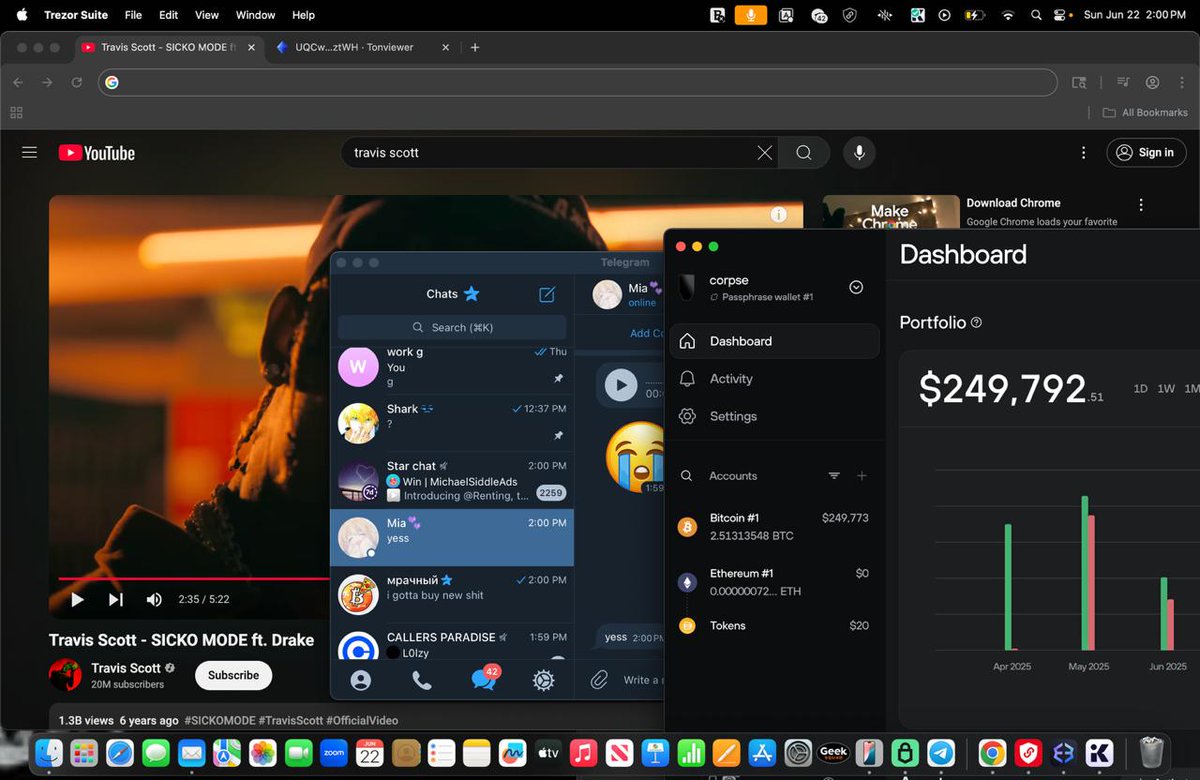
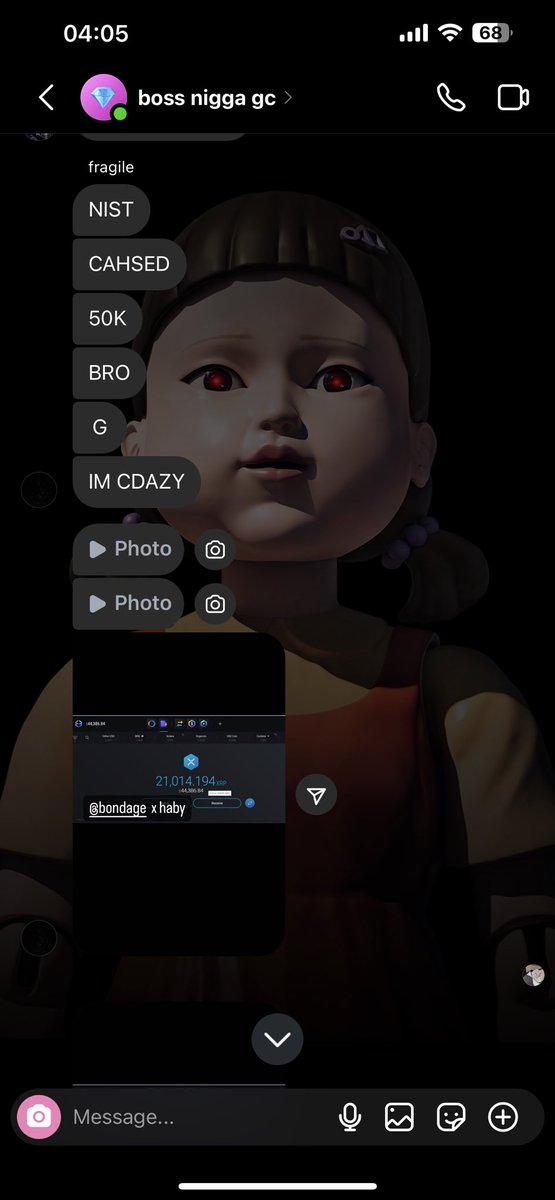
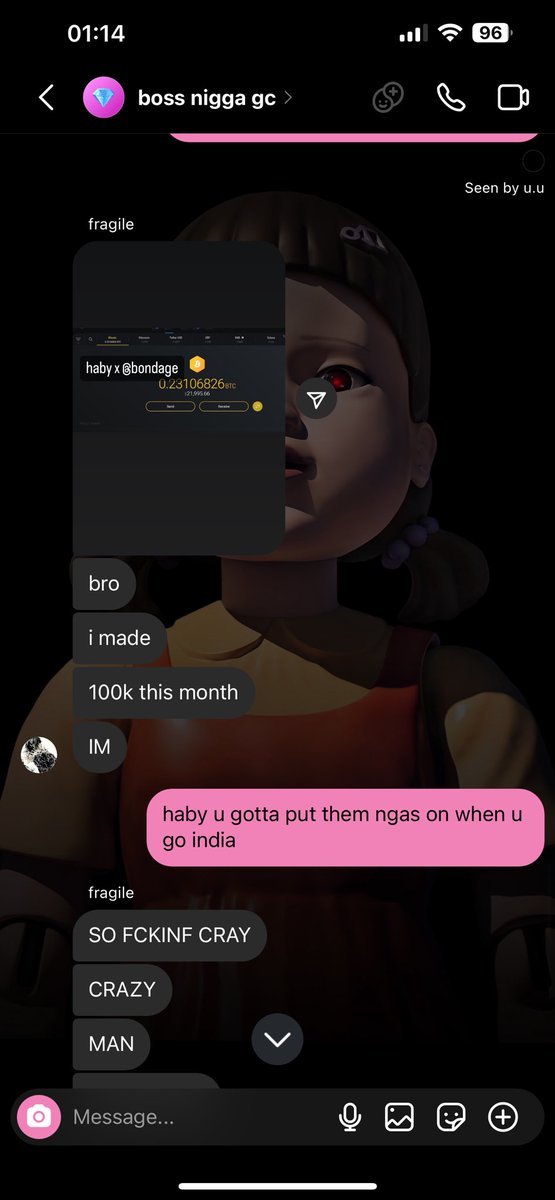
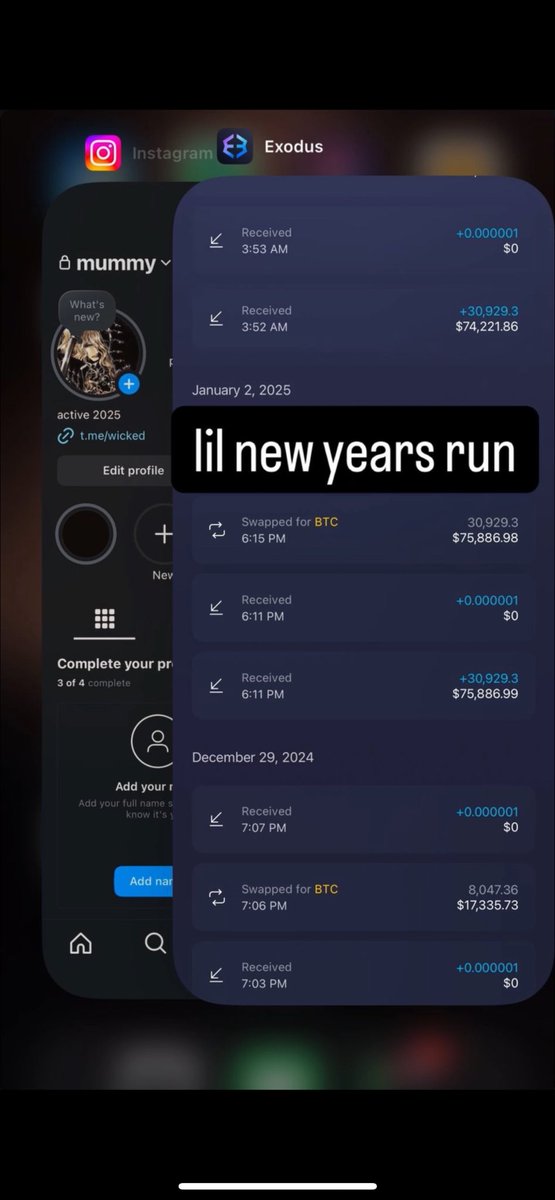
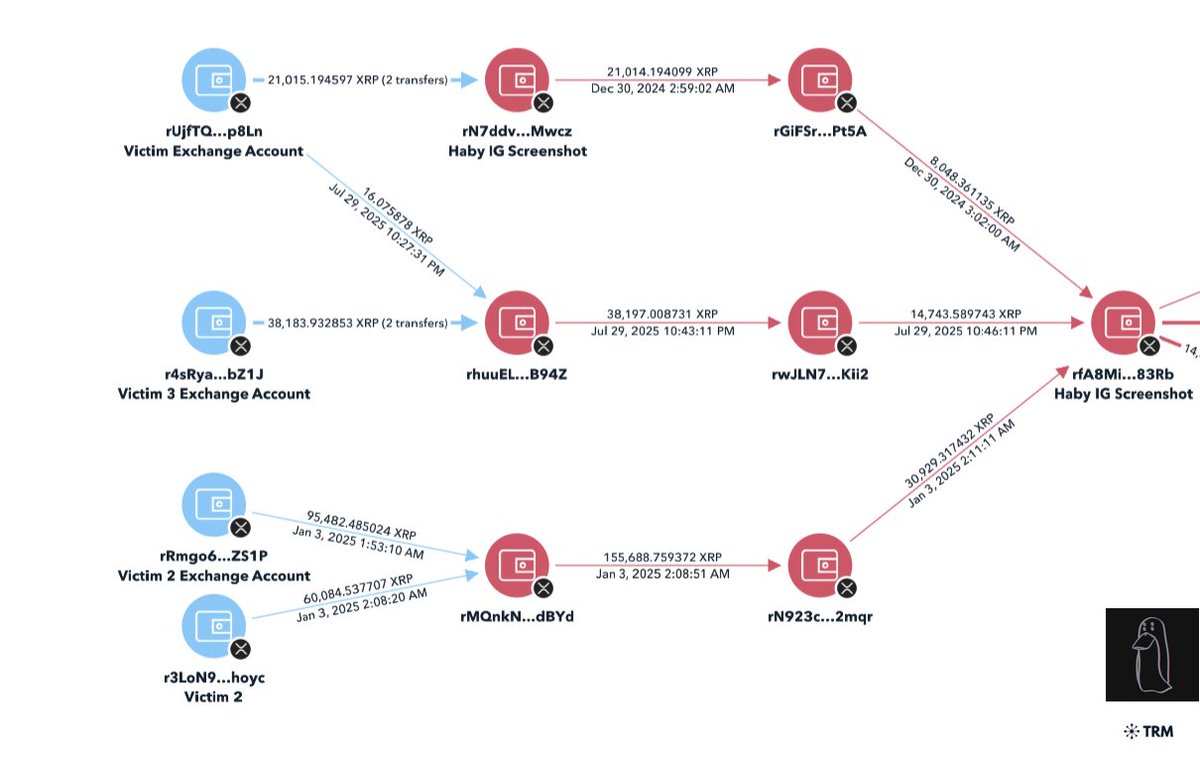
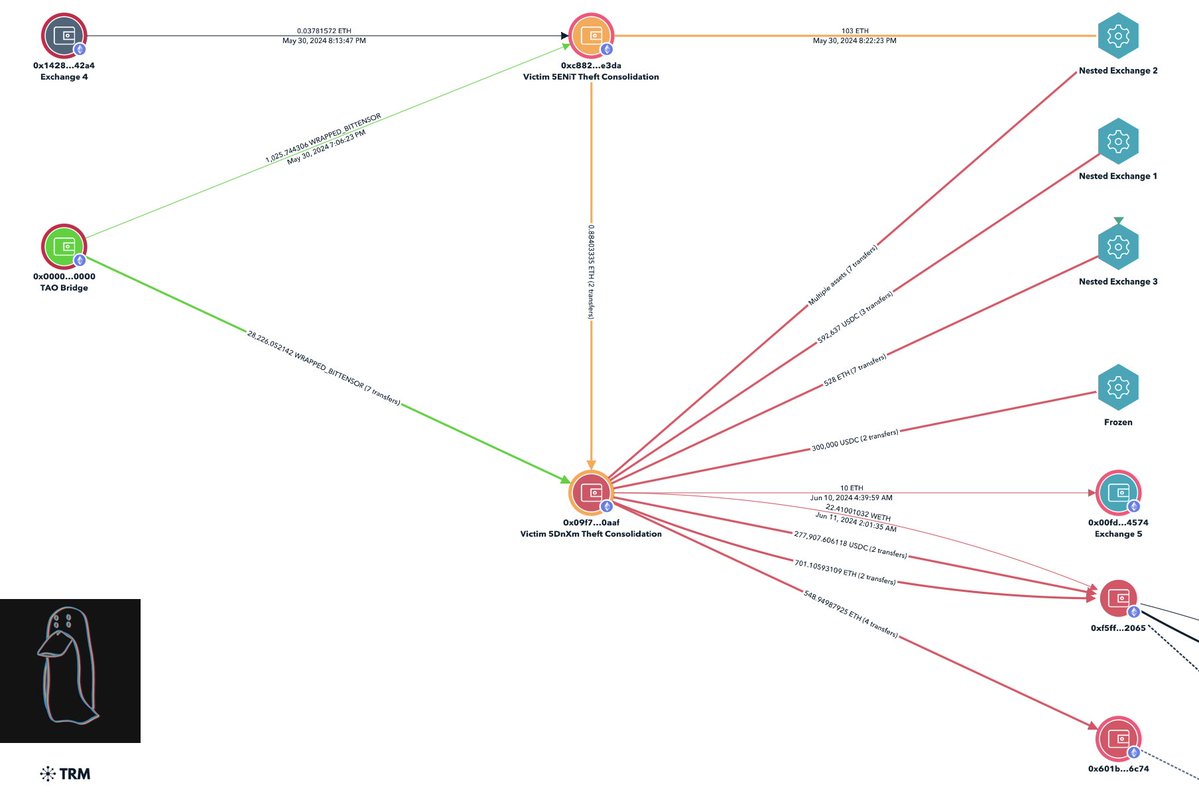
1/ Meet Yicong Wang (王逸聪), a Chinese OTC trader who has helped Lazarus Group convert tens of millions of stolen crypto to cash from various hacks via bank transfers since 2022. 





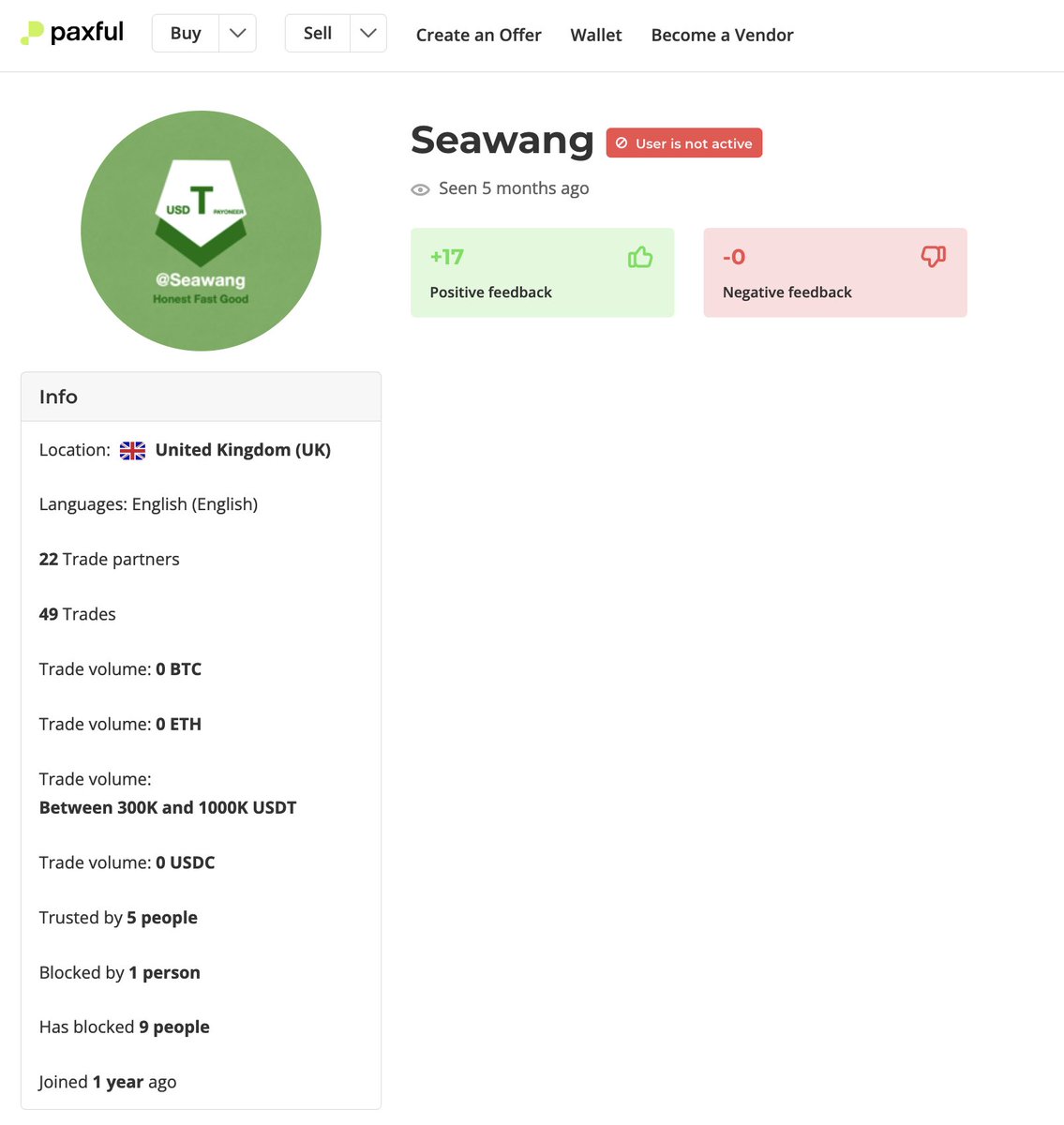
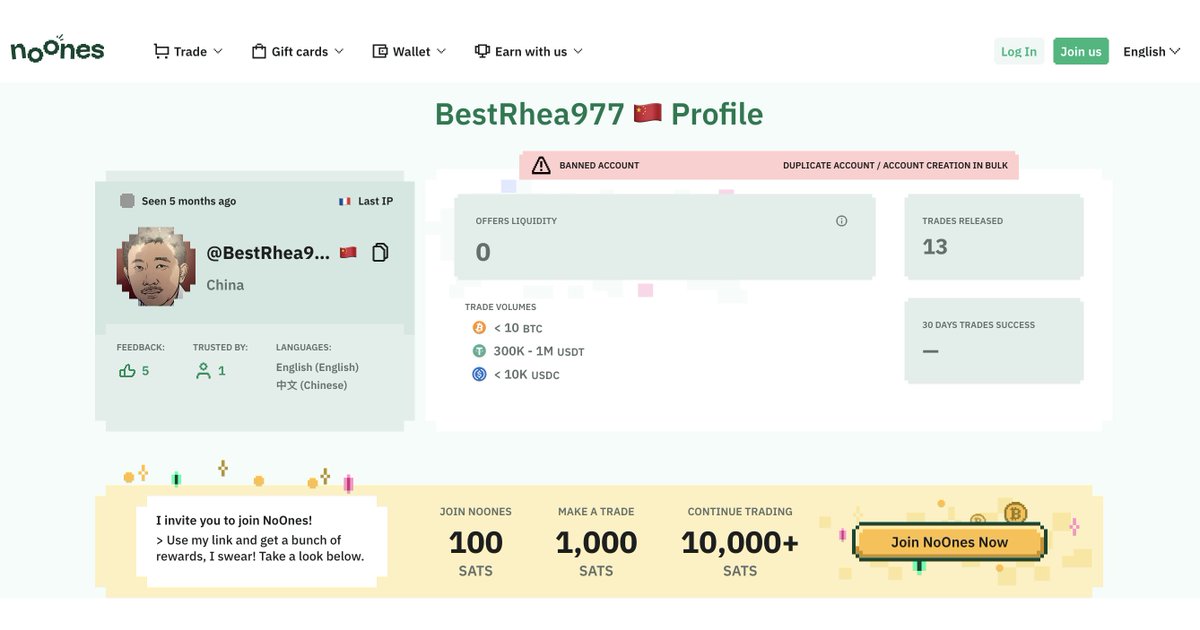
2/ A follower reached out to me a few months ago after having their exchange account frozen after completing a P2P transaction with Yicong Wang an OTC who has used pseudonyms like Seawang, Greatdtrader, & BestRhea977 

3/ They then shared one of Yicong Wang’s Tron wallet addresses with me from a screenshot of their WeChat conversation.
THsSCBGazjjho7u2BQQsmrpbDv1Q237FL4
THsSCBGazjjho7u2BQQsmrpbDv1Q237FL4

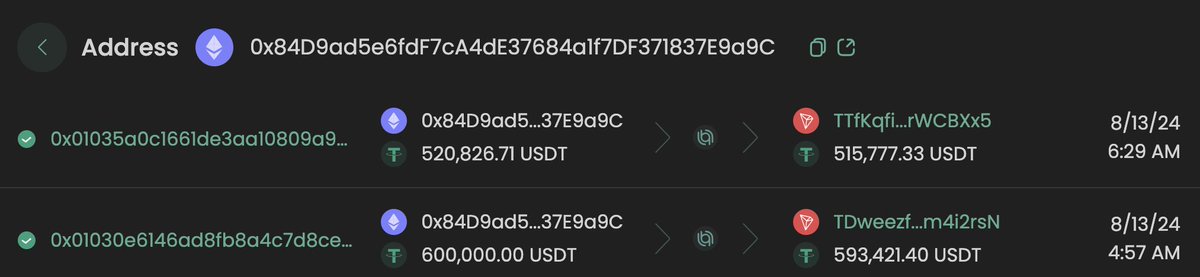
4/ Recently they reached back out after having been approached by Yicong Wang for a larger USDT -> CNY order on August 13, 2024 involving ~1.5M USDT at a rate much lower than the market rate.
THjaAygUNkzoXufwEoKCzbUZHpsehL9rAZ
THjaAygUNkzoXufwEoKCzbUZHpsehL9rAZ
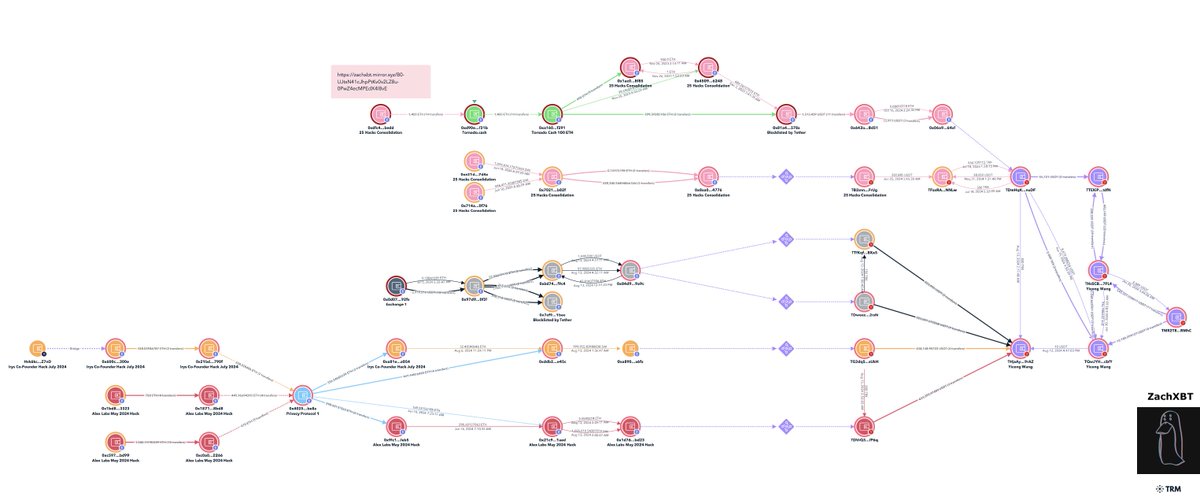
5/ When reviewing blockchain data tied to Yicong Wang you will notice high illicit fund exposure from the Alex Labs, Irys co-founder, and a consolidation of other hacks (EasyFi, Bondly, Maverick co-founder, etc). 
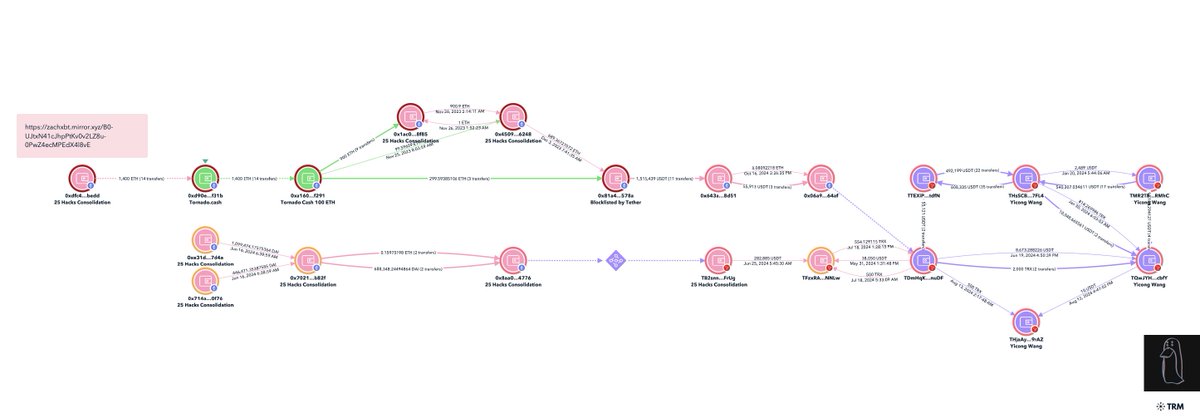
6/ $17M from 25+ Lazarus Group hacks consolidated to 0x5018cf5f48a09c46b4833890cc2cf0df2533d16a where 374K USDT was blacklisted by Tether in Nov 2023
After the blacklist the remaining funds were deposited to Tornado. Within days after the deposits 13 X 100 ETH was withdrawn and consolidated at 0x81a
In Dec 2023 $45K was bridged to Tron and transferred to multiple addresses tied to Yicong.
Read my investigation below for detailed tracing of the 25+ hacks.

After the blacklist the remaining funds were deposited to Tornado. Within days after the deposits 13 X 100 ETH was withdrawn and consolidated at 0x81a
In Dec 2023 $45K was bridged to Tron and transferred to multiple addresses tied to Yicong.
Read my investigation below for detailed tracing of the 25+ hacks.

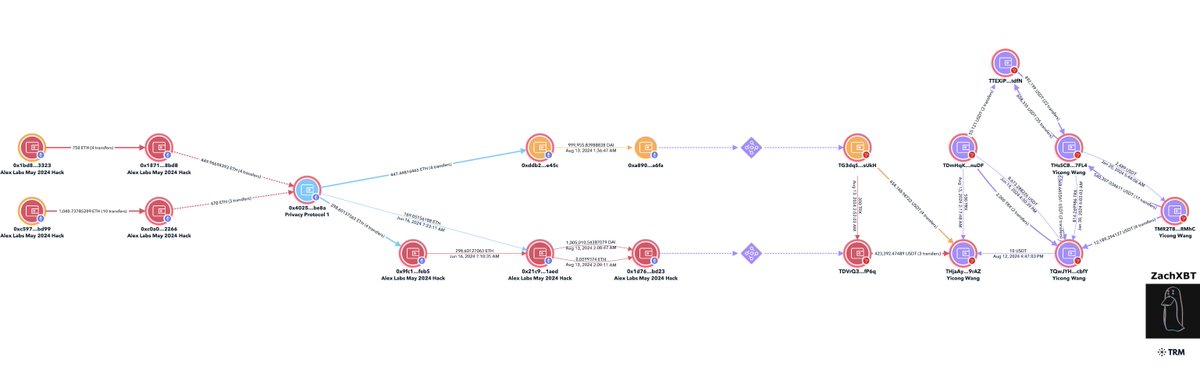
7/ Alex Labs was hacked for ~$4.5M in May 2024 by Lazarus Group.
One of the theft addresses deposited 470 ETH to a privacy protocol on June 16, 2024
0xc0a0ec4dbf170611cc76f31a9df910ad79bc2266
Matching amounts were withdrawn the same day to two addresses
0x9fc1350f80734044b7189fe7b8f288396f76feb5
0x21c926a1a328a4906feeb18664d00f3d85df1aed
Another theft address deposited 449 ETH from June 27-28th
0x1871bb6257b1f622548ef64a12ae5149eb208bd8
Shortly after a matching amount was withdrawn commingling with the Irys co-founder stolen funds.
0xddb2e9feaf0a122b43be14bc085cf713703ce45c
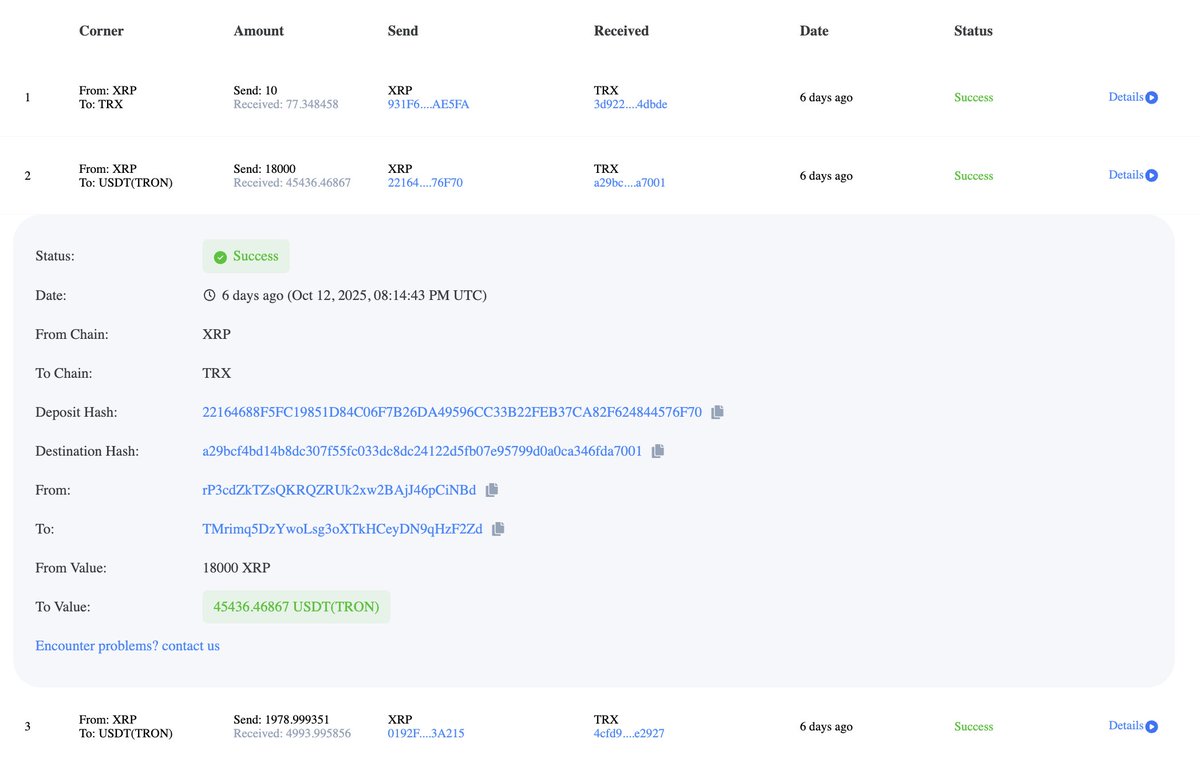
On August 13th funds were bridged from Ethereum to Tron address tied to Yicon.
One of the theft addresses deposited 470 ETH to a privacy protocol on June 16, 2024
0xc0a0ec4dbf170611cc76f31a9df910ad79bc2266
Matching amounts were withdrawn the same day to two addresses
0x9fc1350f80734044b7189fe7b8f288396f76feb5
0x21c926a1a328a4906feeb18664d00f3d85df1aed
Another theft address deposited 449 ETH from June 27-28th
0x1871bb6257b1f622548ef64a12ae5149eb208bd8
Shortly after a matching amount was withdrawn commingling with the Irys co-founder stolen funds.
0xddb2e9feaf0a122b43be14bc085cf713703ce45c
On August 13th funds were bridged from Ethereum to Tron address tied to Yicon.
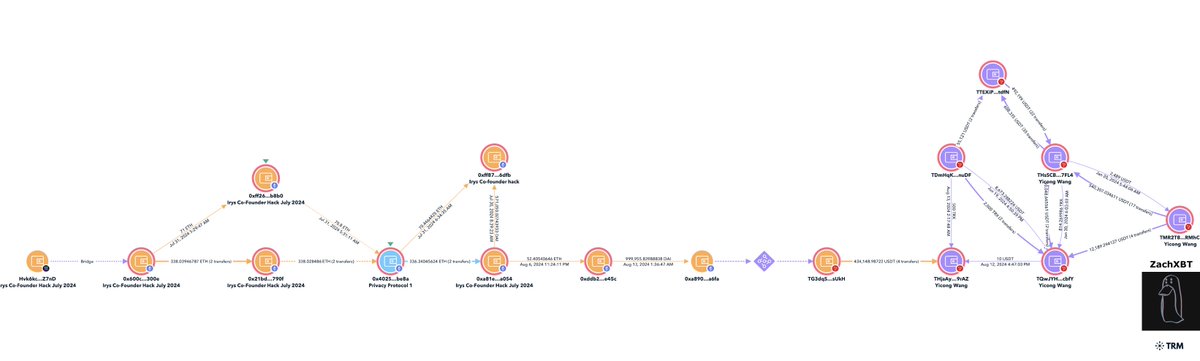
8/ Irys co-founder was hacked for ~$1.3M in July 2024 by Lazarus Group via email spear phishing campaign.
From the theft address 70.8 ETH was deposited to a privacy protocol and another 338 ETH shortly after on July 31st.
0x600cd901d0407753c212ed17d8c6cae014ee300e
By performing a timing analysis matching amounts were found hours after the deposits to two addresses.
0xff87a4df67068464e5f4e3b546f556b2dffb6dfb
0xa81eac50c0b17aee3132f40f7398087e457ca054
Funds were then commingled with the Alex hack and bridged to Tron addresses tied to Yicong on August 13th.
TG3dqSzpH3V2kEqTdJAYQrtZq1TQxysUkH

From the theft address 70.8 ETH was deposited to a privacy protocol and another 338 ETH shortly after on July 31st.
0x600cd901d0407753c212ed17d8c6cae014ee300e
By performing a timing analysis matching amounts were found hours after the deposits to two addresses.
0xff87a4df67068464e5f4e3b546f556b2dffb6dfb
0xa81eac50c0b17aee3132f40f7398087e457ca054
Funds were then commingled with the Alex hack and bridged to Tron addresses tied to Yicong on August 13th.
TG3dqSzpH3V2kEqTdJAYQrtZq1TQxysUkH
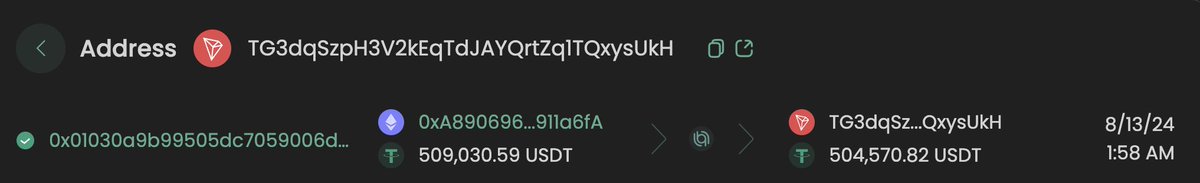
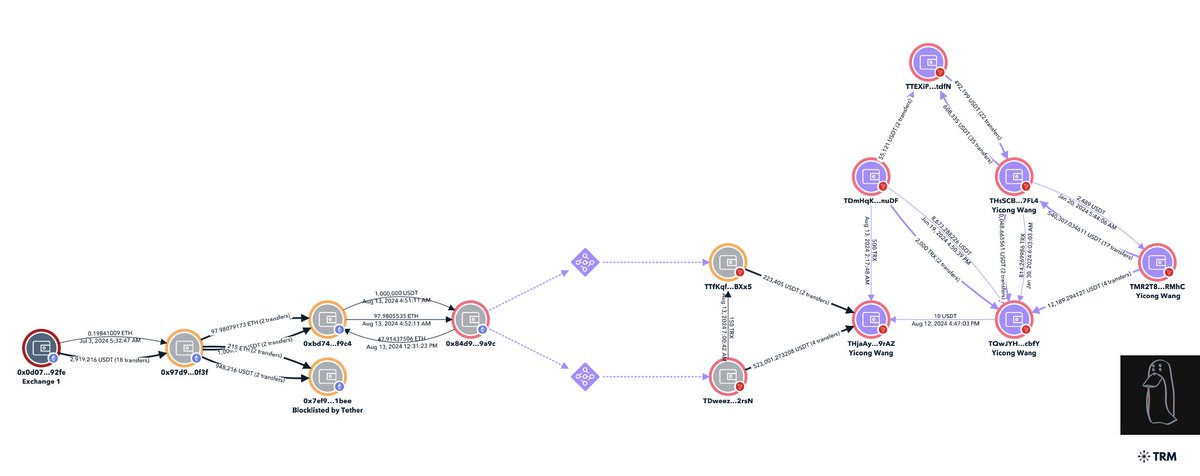
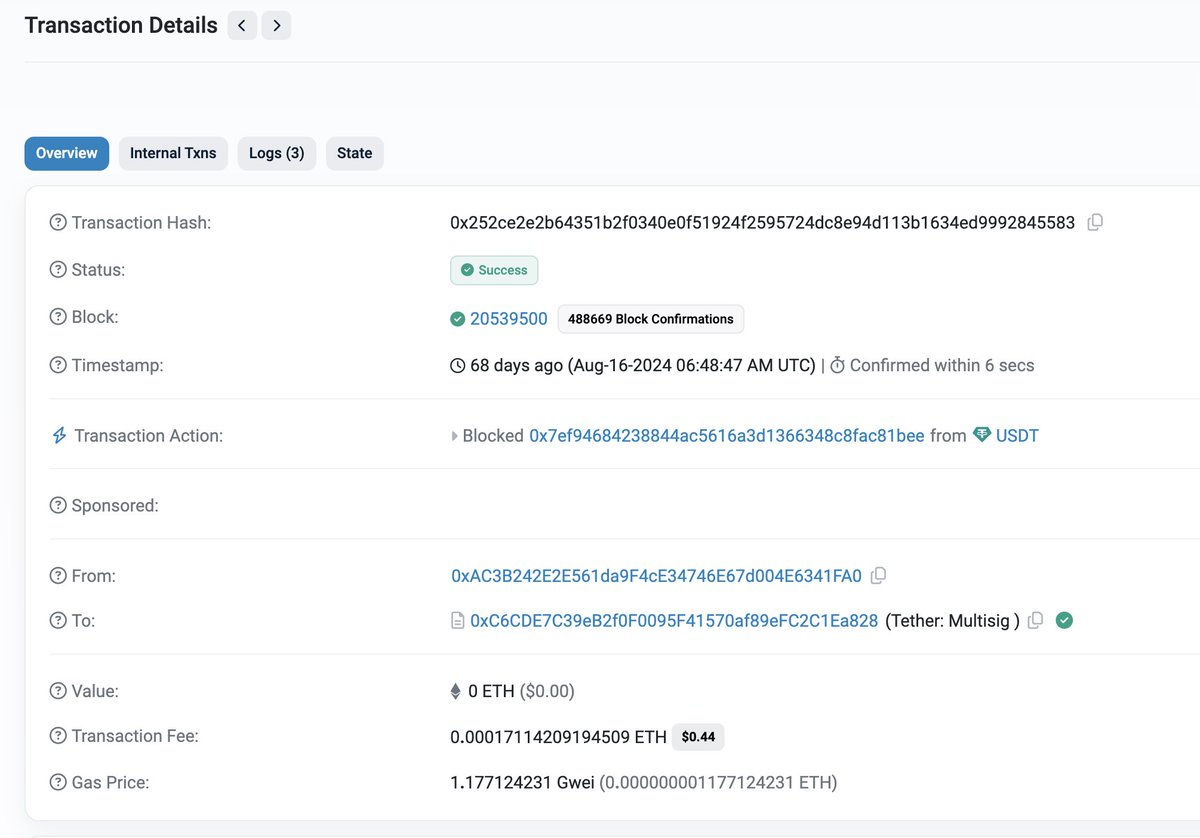
9/ An Ethereum address blacklisted by Tether in August 2024 with 948K is also directly tied to Yicong.
On Aug 13th 746K USDT was transferred to an address tied to Yicong
THjaAygUNkzoXufwEoKCzbUZHpsehL9rAZ
Shortly before the funds had been bridged over from Ethereum linking the blacklisted address
0x84d9ad5e6fdf7ca4de37684a1f7df371837e9a9c


On Aug 13th 746K USDT was transferred to an address tied to Yicong
THjaAygUNkzoXufwEoKCzbUZHpsehL9rAZ
Shortly before the funds had been bridged over from Ethereum linking the blacklisted address
0x84d9ad5e6fdf7ca4de37684a1f7df371837e9a9c
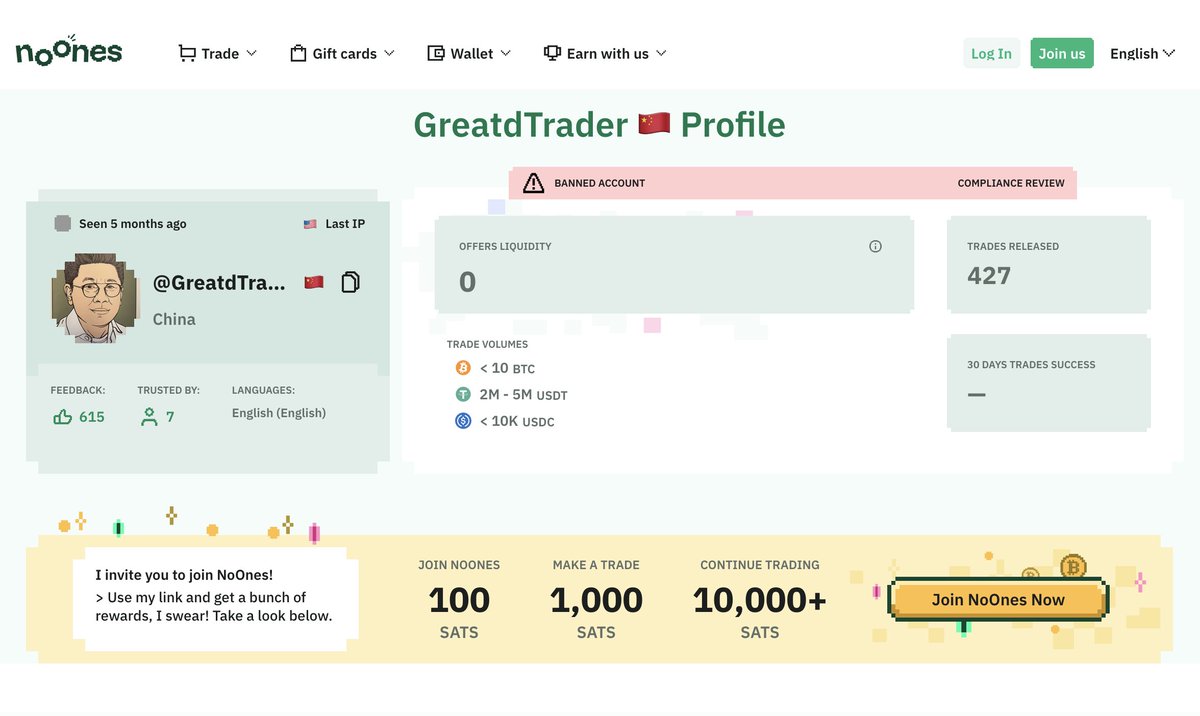
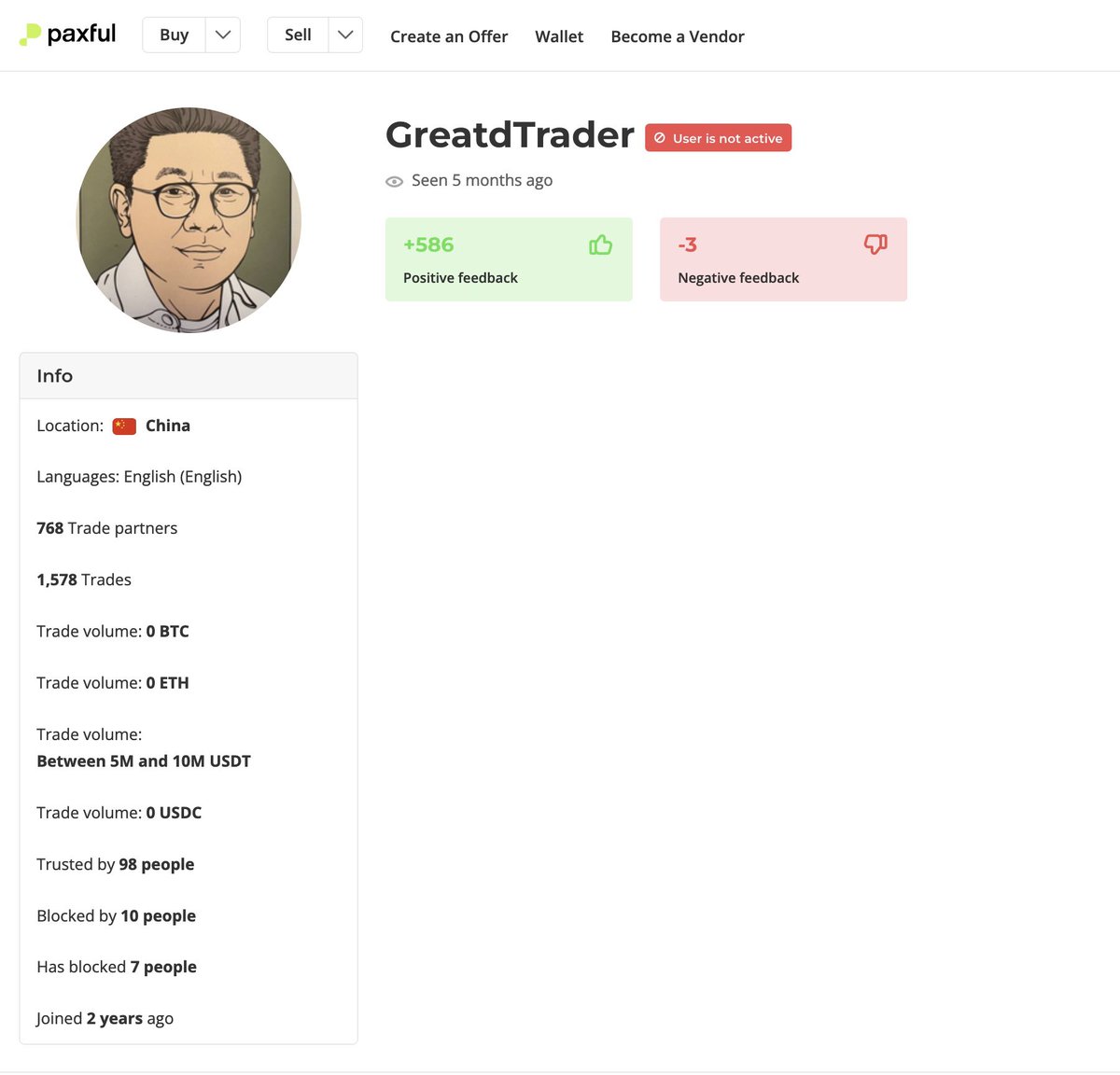
10/ While Yicong Wang has been banned from Paxful and Noones on multiple accounts (Seawang/Greatdtrader/BestRhea977) for laundering funds he has since moved to conducting business offsite.
It’s apparent from on-chain he has still been actively helping Lazarus Group within the past couple weeks.
Hopefully at some point in the future Yicong Wang will be held accountable for his actions.



It’s apparent from on-chain he has still been actively helping Lazarus Group within the past couple weeks.
Hopefully at some point in the future Yicong Wang will be held accountable for his actions.
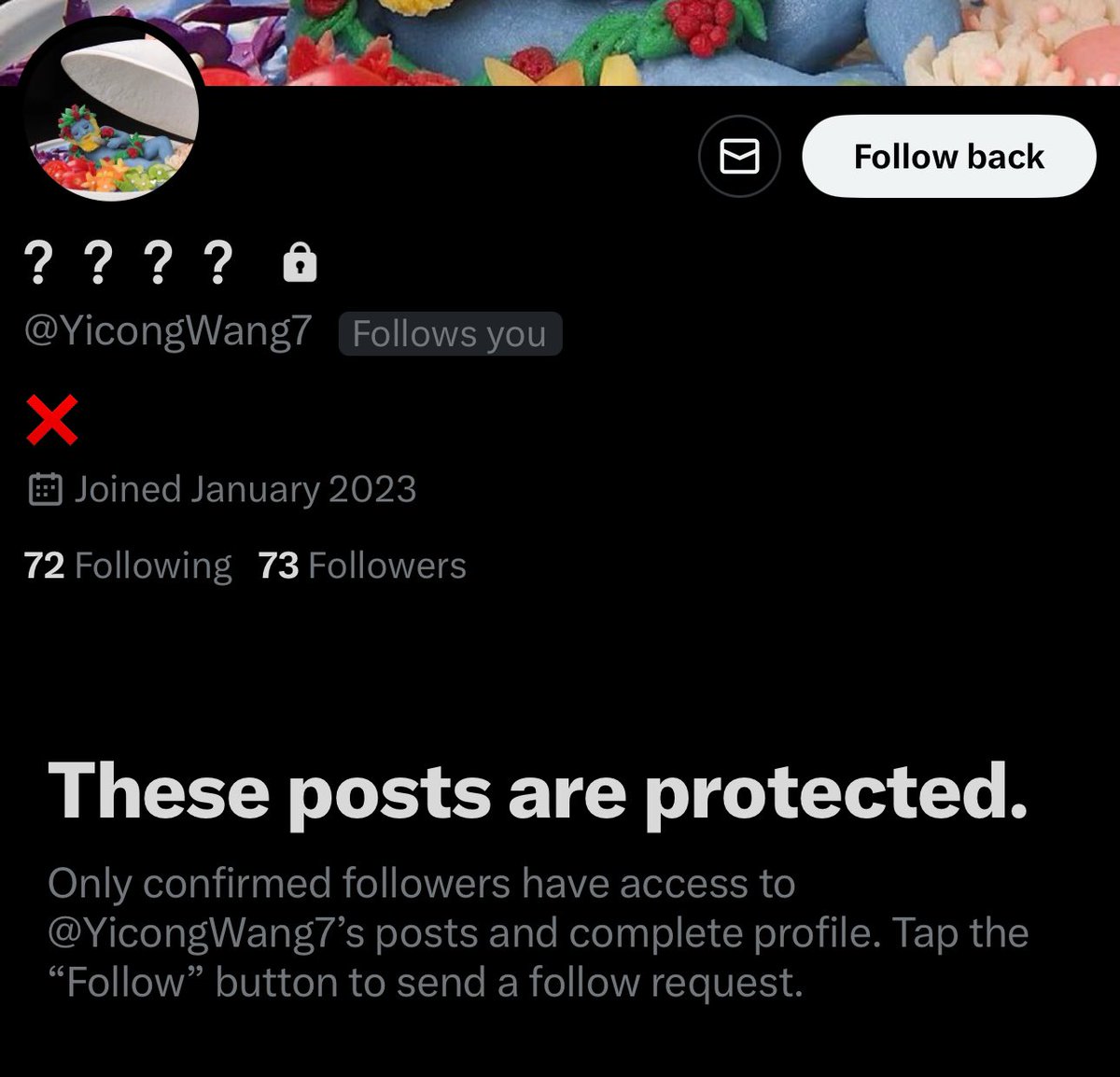
Update: Yicong Wang made his X account private and deleted a lot of the posts where he had asked exchange support for help unbanning his exchange accounts. 
• • •
Missing some Tweet in this thread? You can try to
force a refresh