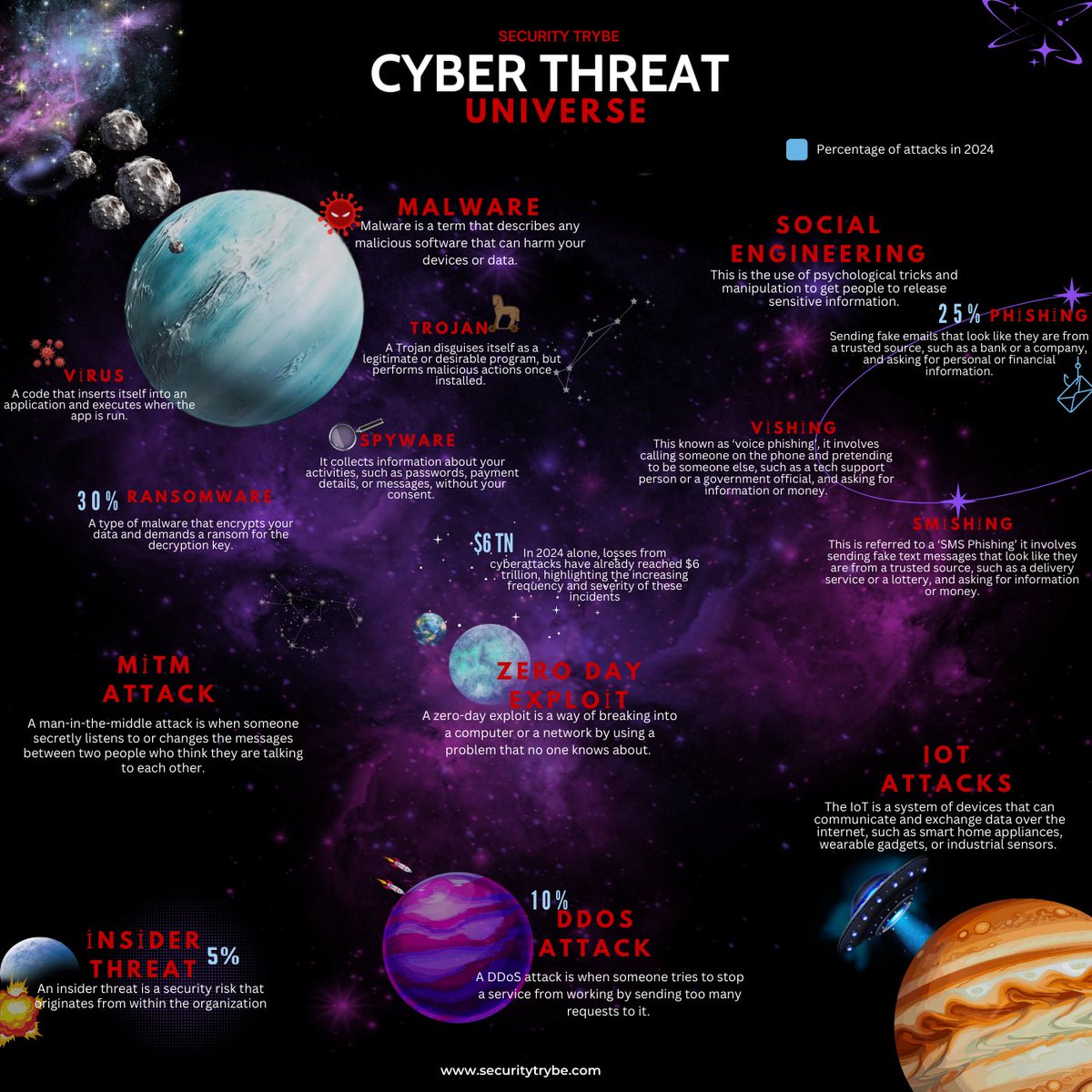
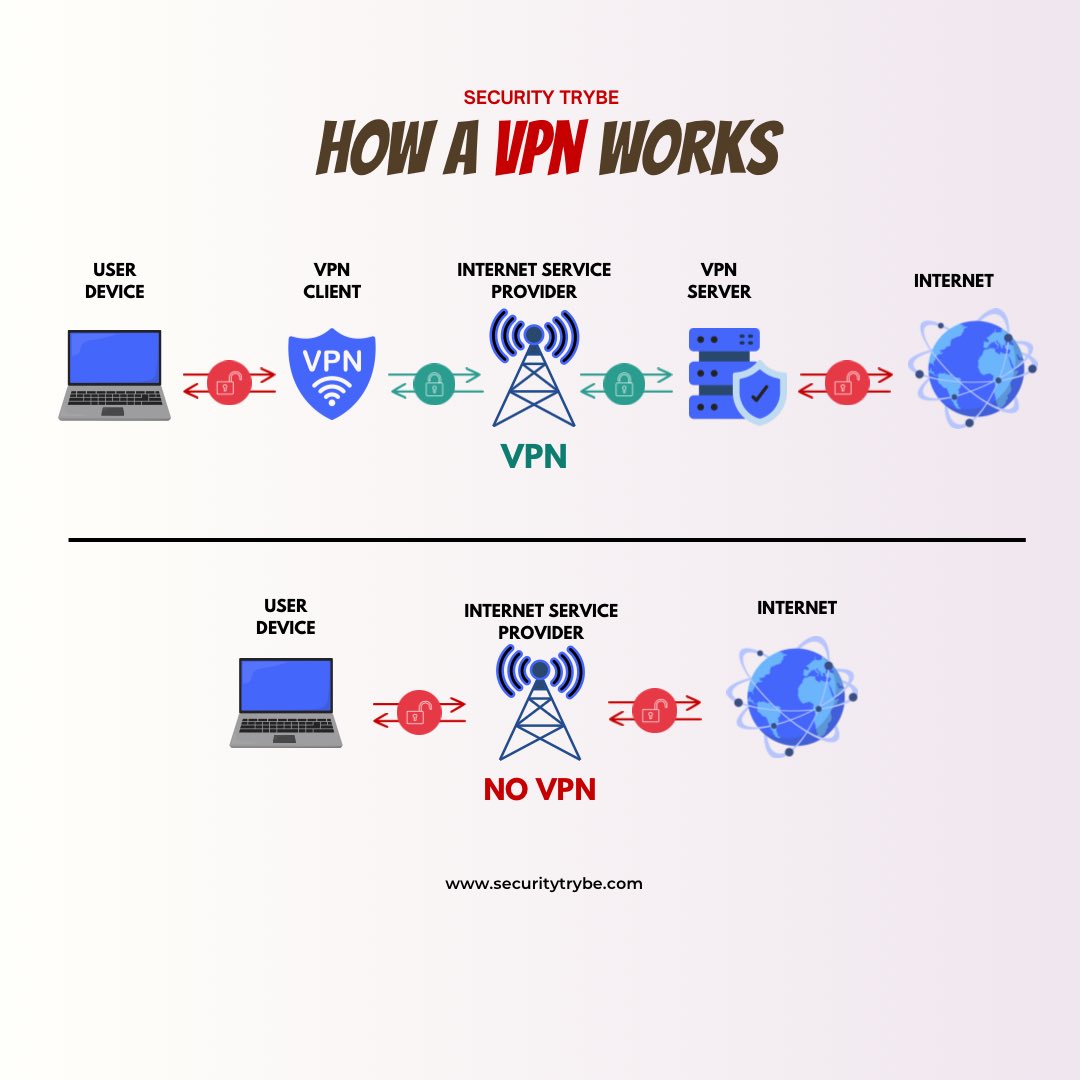
CyberSecurity Study Guide
Estimated Duration: 6-8 Months 👇
Estimated Duration: 6-8 Months 👇
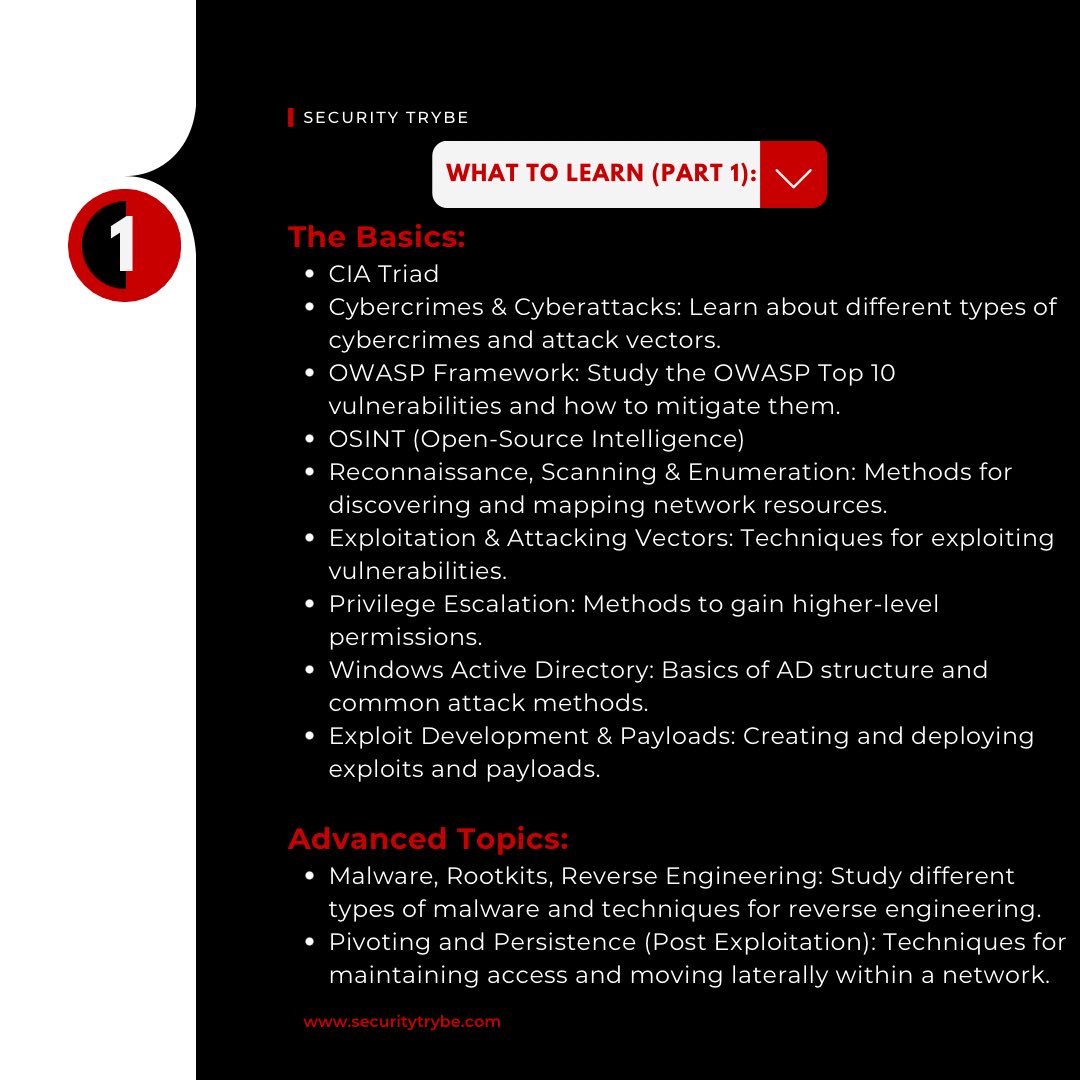
What To Learn (Part 1):
The Basics
*CIA Triad
*Cybercrimes & Cyberattacks
*OWASP Framework
*OSINT
*Recon,Scanning & Enumeration
*Exploitation & Attacking Vectors
*Privilege Escalation
*Windows Active Directory
*Exploit Dev & Payloads
Advanced
*Malwares, Rootkits, Reserve Engineering
*Pivoting and Persistence
(Post Exploitation)
The Basics
*CIA Triad
*Cybercrimes & Cyberattacks
*OWASP Framework
*OSINT
*Recon,Scanning & Enumeration
*Exploitation & Attacking Vectors
*Privilege Escalation
*Windows Active Directory
*Exploit Dev & Payloads
Advanced
*Malwares, Rootkits, Reserve Engineering
*Pivoting and Persistence
(Post Exploitation)
What To Learn (Part 2):
*Linux
*Networking:
-OSI Models
-Network Topologies
-Common Protocols and their uses
-Common Ports and their uses
-IPv4 and IPv6
-Basics of Subnetting
*Programming Languages (At least 1 These):
-Python
-C/C++
-JavaScript
-HTML
*Linux
*Networking:
-OSI Models
-Network Topologies
-Common Protocols and their uses
-Common Ports and their uses
-IPv4 and IPv6
-Basics of Subnetting
*Programming Languages (At least 1 These):
-Python
-C/C++
-JavaScript
-HTML
Tools to Master (Must Learn):
*Nmap
*BurpSuite
*Wireshark
*Metasploit
Operating System (OS):
Kali Linux
Playgrounds :
*TryHackMe
*HackTheBox
*Cybrary
*HackerOne (BugBounty)
*Nmap
*BurpSuite
*Wireshark
*Metasploit
Operating System (OS):
Kali Linux
Playgrounds :
*TryHackMe
*HackTheBox
*Cybrary
*HackerOne (BugBounty)
Resources- YouTube (FREE)
*Ethical Hacking in 15 Hours- The Cyber Mentor
*Beginner to Advanced Bug Bounty- PHD Security
*Wireshark Master Class- Chris Greer
*The 50 Most Popular Linux & Terminal Commands (Full Course of Beginners) - FreeCodeCamp
*Ethical Hacking in 15 Hours- The Cyber Mentor
*Beginner to Advanced Bug Bounty- PHD Security
*Wireshark Master Class- Chris Greer
*The 50 Most Popular Linux & Terminal Commands (Full Course of Beginners) - FreeCodeCamp
Resources (Paid)
*
-By far the best collection in one place
*Getting Started with Wireshark (Udemy) - Chris Greer
*The Complete NMAP Ethical Hacking Course (Udemy) - Nathan House
*Web Hacking: Become a Professional Web PenTesters (Udemy)- Geri Revayacademy.tcm-sec.com
*
-By far the best collection in one place
*Getting Started with Wireshark (Udemy) - Chris Greer
*The Complete NMAP Ethical Hacking Course (Udemy) - Nathan House
*Web Hacking: Become a Professional Web PenTesters (Udemy)- Geri Revayacademy.tcm-sec.com
Certifications To Get:
* eLearnSecurity Junior Penetration Tester (eJPT)
*Certified Ethical Hacker (CEH)
*CompTIA Security+
*CompTIA PenTest+
* eLearnSecurity Junior Penetration Tester (eJPT)
*Certified Ethical Hacker (CEH)
*CompTIA Security+
*CompTIA PenTest+
Additional Subjects:
*MITRE ATT&CK
*NIST Framework - GRC
*ISO 27001 - GRC
*MITRE ATT&CK
*NIST Framework - GRC
*ISO 27001 - GRC
For More Cybersecurity Posts and Updates
Follow us on TikTok-@thesecuritytrybe
Link- tiktok.com/@thesecuritytr…
Follow us on IG-@SecurityTrybe
Link- instagram.com/securitytrybe
Follow us on TikTok-@thesecuritytrybe
Link- tiktok.com/@thesecuritytr…
Follow us on IG-@SecurityTrybe
Link- instagram.com/securitytrybe
• • •
Missing some Tweet in this thread? You can try to
force a refresh