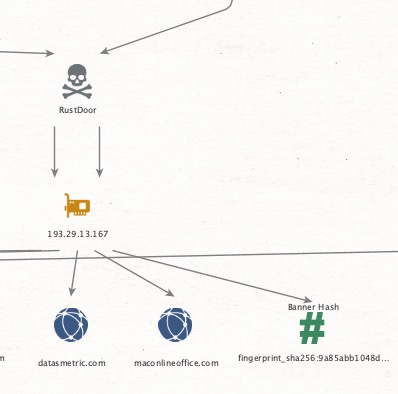
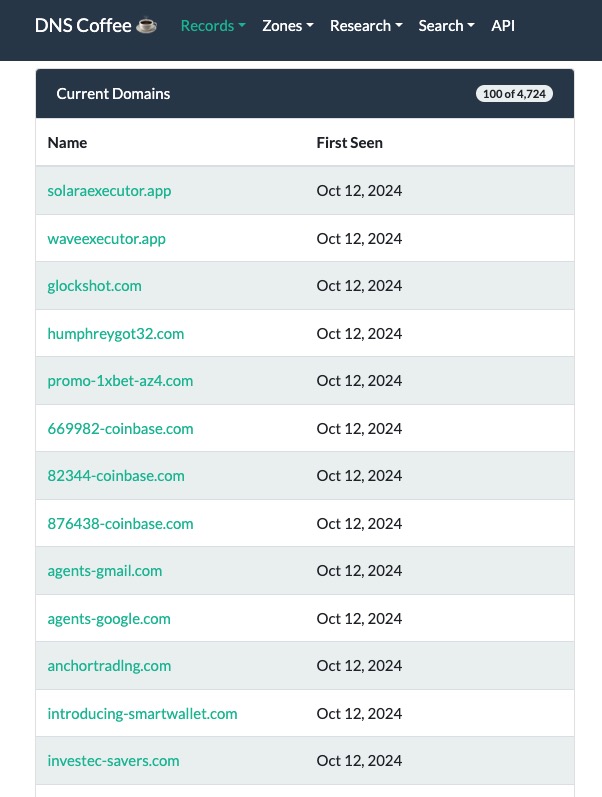
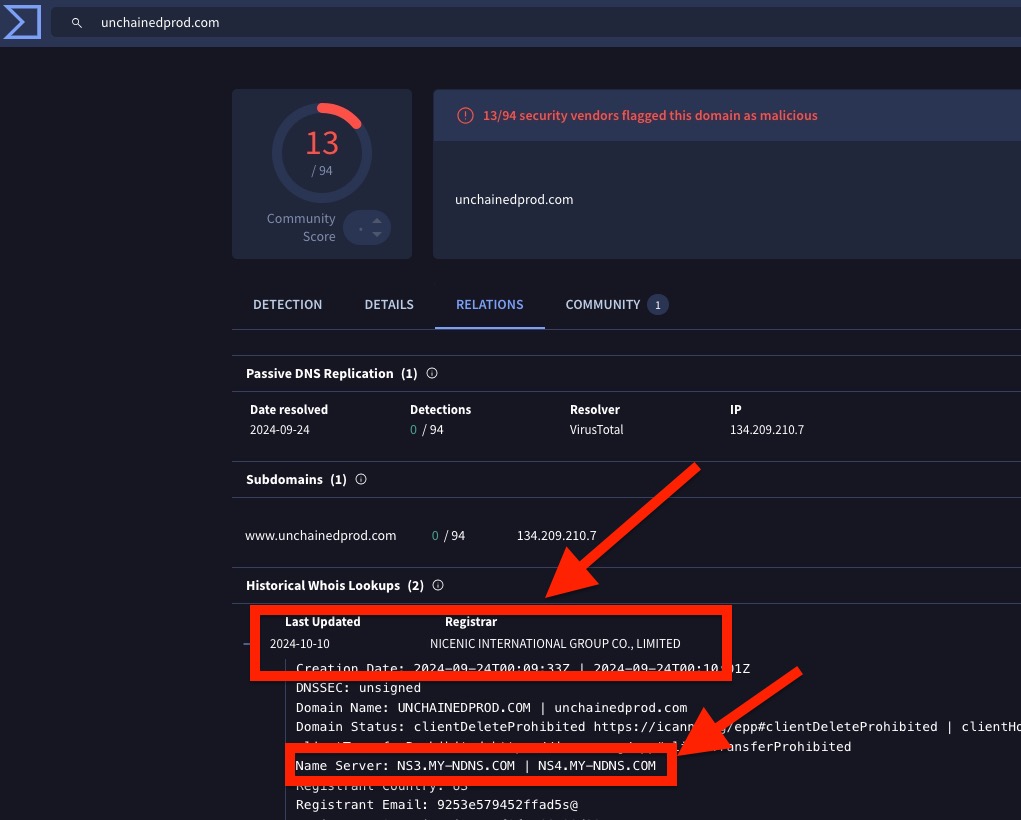
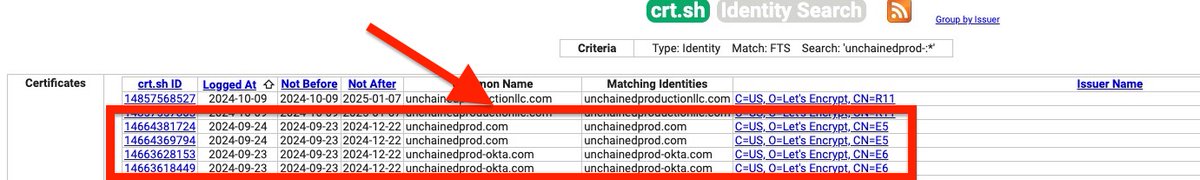
Thread 1/🚨 Uncovering the Keys to the Kingdom: A Dive into Deep-State Espionage Entangled in a Ransomware Network for Cover! 🚨
Ever thought a simple SSH key could be the link to a sprawling espionage network? After months of research, I’ve traced exposed public SSH keys that reveal connections far deeper than initially believed.
Once suspected as the work of a ransomware affiliate, these keys hint at something much more sinister possible nation-state involvement.
💥March 2023: Talos published a bombshell report on #YoroTrooper, exposing an #espionage campaign targeting EU Governing Entities in CIS countries, embassies, and the EU healthcare sector.
💥Buried in the details was an IP 46.161.40.164 with an SSH key (fingerprint_sha256: f95812cbb46f0a664a8f2200592369b105d17dfe8255054963aac4e2df53df51) that set off alarms. 🕵️♂️
And here’s why, this key has reappeared on over 120 servers, forming clusters with alarming patterns of activity.
💥October 26, 2023: Another #Talos report on YoroTrooper exposed another IOC tied to that same key, linking two IPs (46.161.40.164, 46.161.27.151) to espionage activity.
My analysis shows even deeper connections here it’s where we start seeing links to ransomware: the Shadow Syndicate, a ransomware affiliate potentially linked to espionage.
July 2024: A #Mandiant report flags the same IP, 46.161.27.151, connected to the notorious #BlackBasta ransomware group. But as we dig deeper, it’s clear the server may be controlled by a much bigger player.
Could this SSH key be the thread tying espionage and ransomware together? Are these ransomware affiliates merely proxies for nation-states, muddying their tracks?
🕵️♂️ Buckle up for what’s next—this thriller is just getting started.
#CyberEspionage #ThreatIntel #YoroTrooper #BlackBasta #ShadowSyndicate #NationStateHacking #CyberThriller
Ever thought a simple SSH key could be the link to a sprawling espionage network? After months of research, I’ve traced exposed public SSH keys that reveal connections far deeper than initially believed.
Once suspected as the work of a ransomware affiliate, these keys hint at something much more sinister possible nation-state involvement.
💥March 2023: Talos published a bombshell report on #YoroTrooper, exposing an #espionage campaign targeting EU Governing Entities in CIS countries, embassies, and the EU healthcare sector.
💥Buried in the details was an IP 46.161.40.164 with an SSH key (fingerprint_sha256: f95812cbb46f0a664a8f2200592369b105d17dfe8255054963aac4e2df53df51) that set off alarms. 🕵️♂️
And here’s why, this key has reappeared on over 120 servers, forming clusters with alarming patterns of activity.
💥October 26, 2023: Another #Talos report on YoroTrooper exposed another IOC tied to that same key, linking two IPs (46.161.40.164, 46.161.27.151) to espionage activity.
My analysis shows even deeper connections here it’s where we start seeing links to ransomware: the Shadow Syndicate, a ransomware affiliate potentially linked to espionage.
July 2024: A #Mandiant report flags the same IP, 46.161.27.151, connected to the notorious #BlackBasta ransomware group. But as we dig deeper, it’s clear the server may be controlled by a much bigger player.
Could this SSH key be the thread tying espionage and ransomware together? Are these ransomware affiliates merely proxies for nation-states, muddying their tracks?
🕵️♂️ Buckle up for what’s next—this thriller is just getting started.
#CyberEspionage #ThreatIntel #YoroTrooper #BlackBasta #ShadowSyndicate #NationStateHacking #CyberThriller
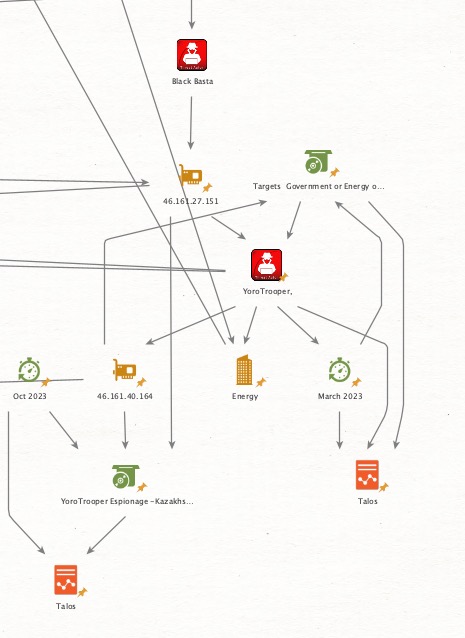
Thread 2/ Keys to the Kingdom: A Deepening Threat in the #Energy Sector 🔍
💥 In March 2023, Talos highlighted the Energy sector as a specific target in an espionage campaign. Then, in August 2023, #Kaspersky reported on suspicious activity against an electric utility in Southern Africa, revealing #Cobalt Strike #beacons and a new #SystemBC payload variant, dubbed #DroxiDat. According to Kaspersky, this attack occurred in March 2023 and was likely the initial stage of a #ransomware operation.
💥Yet, there’s more to this than meets the eye. The SSH key fingerprint_sha256: f95812cbb46f0a664a8f2200592369b105d17dfe8255054963aac4e2df53df51 resurfaces here, linked to IP 179.60.146.6:22.
💥This aligns almost too well with Talos’s original indicators, connecting tactics, techniques, and procedures (TTPs) across both campaigns.
💥Notably, the attackers used bespoke, energy-themed domains, indicating a level of precision beyond typical ransomware affiliate activity.
💥The alignment with Talos’s intelligence and the calculated nature of these tactics hint at something far more sophisticated. Could this be a nation-state operation, using ransomware as a convenient cloak for their espionage efforts?
Buckle up this thriller is only getting deeper!
#EnergySector #CyberEspionage #NationState #Ransomware #ThreatIntel #CobaltStrike #SystemBC #DroxiDat #TalosIntel
💥 In March 2023, Talos highlighted the Energy sector as a specific target in an espionage campaign. Then, in August 2023, #Kaspersky reported on suspicious activity against an electric utility in Southern Africa, revealing #Cobalt Strike #beacons and a new #SystemBC payload variant, dubbed #DroxiDat. According to Kaspersky, this attack occurred in March 2023 and was likely the initial stage of a #ransomware operation.
💥Yet, there’s more to this than meets the eye. The SSH key fingerprint_sha256: f95812cbb46f0a664a8f2200592369b105d17dfe8255054963aac4e2df53df51 resurfaces here, linked to IP 179.60.146.6:22.
💥This aligns almost too well with Talos’s original indicators, connecting tactics, techniques, and procedures (TTPs) across both campaigns.
💥Notably, the attackers used bespoke, energy-themed domains, indicating a level of precision beyond typical ransomware affiliate activity.
💥The alignment with Talos’s intelligence and the calculated nature of these tactics hint at something far more sophisticated. Could this be a nation-state operation, using ransomware as a convenient cloak for their espionage efforts?
Buckle up this thriller is only getting deeper!
#EnergySector #CyberEspionage #NationState #Ransomware #ThreatIntel #CobaltStrike #SystemBC #DroxiDat #TalosIntel
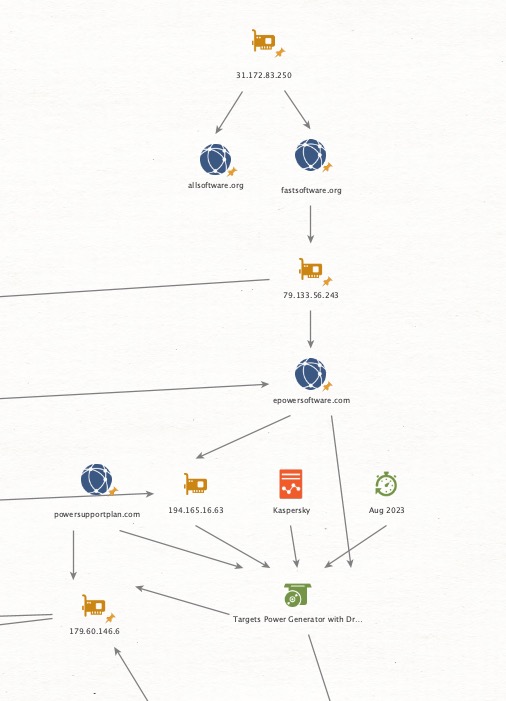
Thread 3/ 🔍 Keys to the Kingdom: Is APT28 Using Play Ransomware as a Smokescreen? 🔍
💥By May 2024, #TrendMicro’s report, Cybercriminals and Nation-States Sharing Compromised Networks, brought to light a shared infrastructure between cybercriminals and nation-state actors.
💥But as I dig deeper, a disturbing pattern emerges: the ShadowSyndicate SSH key fingerprint_sha256: bd613b3be57f18c3bceb0aaf86a28ad8b6df7f9bccacf58044f1068d1787f8a5, linked to multiple IPs, potentially links with APT28 activity.
💥More intriguing, one of these IPs also overlaps with #Play_ransomware indicators, hinting at a potential smokescreen operation.
Key questions are now taking shape:
🔒While Trend Micro observed that nation-states and cybercriminals might be “sharing” infrastructure, could APT28 be doing much more than that?
🔒My research suggests they might be controlling these routers outright, using them as a stealth layer for their espionage efforts.
🔒Trend Micro pointed out that #PawnStorm (#APT28) had access to a criminal-run botnet of compromised Ubiquiti EdgeRouters. But with the SSH key and IP overlaps pointing to APT28, could they be running this botnet rather than merely renting it?
Following the January 2024 disruption of this botnet by the FBI, the botnet’s rapid reassembly with new C&C infrastructure suggests a sophisticated and centralised approach, one likely orchestrated by APT28. This overlap between ransomware and nation-state TTPs hints that APT28 may be masking their operations behind a facade of criminal activity.
Could this be a glimpse into APT28’s playbook, leveraging cybercriminal groups as a smokescreen while they pursue far-reaching espionage goals?
#CyberEspionage #APT28 #PlayRansomware #PawnStorm #SystemBC #CyberThreat #NationState #ThreatIntel #RouterSecurity #TrendMicro
💥By May 2024, #TrendMicro’s report, Cybercriminals and Nation-States Sharing Compromised Networks, brought to light a shared infrastructure between cybercriminals and nation-state actors.
💥But as I dig deeper, a disturbing pattern emerges: the ShadowSyndicate SSH key fingerprint_sha256: bd613b3be57f18c3bceb0aaf86a28ad8b6df7f9bccacf58044f1068d1787f8a5, linked to multiple IPs, potentially links with APT28 activity.
💥More intriguing, one of these IPs also overlaps with #Play_ransomware indicators, hinting at a potential smokescreen operation.
Key questions are now taking shape:
🔒While Trend Micro observed that nation-states and cybercriminals might be “sharing” infrastructure, could APT28 be doing much more than that?
🔒My research suggests they might be controlling these routers outright, using them as a stealth layer for their espionage efforts.
🔒Trend Micro pointed out that #PawnStorm (#APT28) had access to a criminal-run botnet of compromised Ubiquiti EdgeRouters. But with the SSH key and IP overlaps pointing to APT28, could they be running this botnet rather than merely renting it?
Following the January 2024 disruption of this botnet by the FBI, the botnet’s rapid reassembly with new C&C infrastructure suggests a sophisticated and centralised approach, one likely orchestrated by APT28. This overlap between ransomware and nation-state TTPs hints that APT28 may be masking their operations behind a facade of criminal activity.
Could this be a glimpse into APT28’s playbook, leveraging cybercriminal groups as a smokescreen while they pursue far-reaching espionage goals?
#CyberEspionage #APT28 #PlayRansomware #PawnStorm #SystemBC #CyberThreat #NationState #ThreatIntel #RouterSecurity #TrendMicro
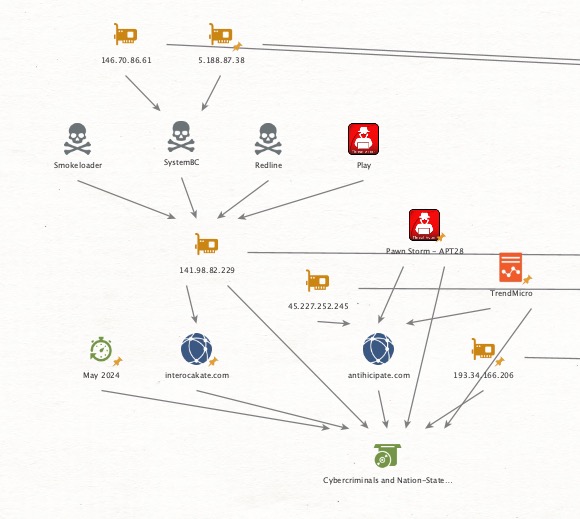
Thread 4/🔍 Keys to the Kingdom: New Links to Chinese Cyber Espionage Through Overlapping SSH Keys 🔍
💥Further analysis into overlapping SSH keys tied to ransomware has uncovered yet another nation-state connection—this time, with links to #China 🇨🇳.
One particular SSH key, fingerprint_sha256: c655bae831ca57a857b26d76a7c98a56a65d00fdab7d234a64addf8166e3cd09, associated with a network of over 150 servers, shows strong correlations to previous LockBit ransomware activity.
But here’s where it gets interesting: in May 2023, SecureWorks reported that the Chinese cyber-espionage group #BRONZESILHOUETTE was actively targeting U.S. government and defence organisations.
The #SecureWorks report listed only three C2 IPs, and one of them 23.227.198.247 is controlled by this same SSH key.
Key questions arising from this twist:
💥Could this overlapping SSH key indicate that BRONZE SILHOUETTE is leveraging ransomware-like infrastructure as a smokescreen, similar to APT28’s tactics?
💥Is this a case of cybercriminal and nation-state interests aligning, or is there a deeper, coordinated effort from Chinese actors to repurpose criminal infrastructure for espionage?
💥With one of BRONZE SILHOUETTE’s C2 IPs directly linked to ransomware infrastructure, are we witnessing a trend where nation-state actors like China use ransomware networks as cover for high-stakes espionage?
This discovery raises new questions about how Chinese cyber-espionage may be blending with ransomware networks to obscure their operations.
#CyberEspionage #BRONZESILHOUETTE #LockBit #NationState #CyberThreat #China #ThreatIntel #SecureWorks
💥Further analysis into overlapping SSH keys tied to ransomware has uncovered yet another nation-state connection—this time, with links to #China 🇨🇳.
One particular SSH key, fingerprint_sha256: c655bae831ca57a857b26d76a7c98a56a65d00fdab7d234a64addf8166e3cd09, associated with a network of over 150 servers, shows strong correlations to previous LockBit ransomware activity.
But here’s where it gets interesting: in May 2023, SecureWorks reported that the Chinese cyber-espionage group #BRONZESILHOUETTE was actively targeting U.S. government and defence organisations.
The #SecureWorks report listed only three C2 IPs, and one of them 23.227.198.247 is controlled by this same SSH key.
Key questions arising from this twist:
💥Could this overlapping SSH key indicate that BRONZE SILHOUETTE is leveraging ransomware-like infrastructure as a smokescreen, similar to APT28’s tactics?
💥Is this a case of cybercriminal and nation-state interests aligning, or is there a deeper, coordinated effort from Chinese actors to repurpose criminal infrastructure for espionage?
💥With one of BRONZE SILHOUETTE’s C2 IPs directly linked to ransomware infrastructure, are we witnessing a trend where nation-state actors like China use ransomware networks as cover for high-stakes espionage?
This discovery raises new questions about how Chinese cyber-espionage may be blending with ransomware networks to obscure their operations.
#CyberEspionage #BRONZESILHOUETTE #LockBit #NationState #CyberThreat #China #ThreatIntel #SecureWorks
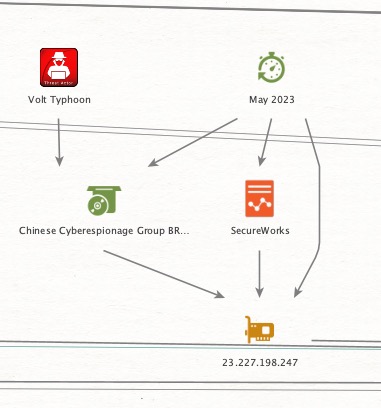
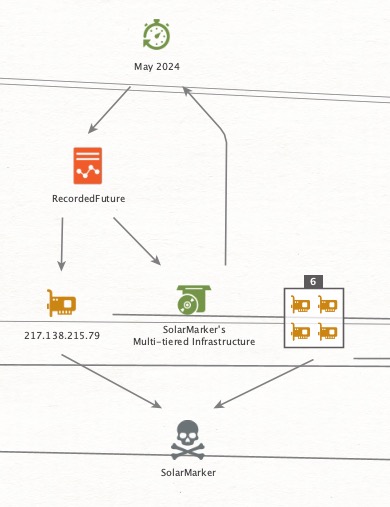
Thread 5/ 🔍 Keys to the Kingdom: SolarMarker’s Multi-Tiered Infrastructure Revealed 🔍
💥Tracking the same SSH key fingerprint_sha256: c655bae831ca57a857b26d76a7c98a56a65d00fdab7d234a64addf8166e3cd09, we uncover its role in various malware campaigns, with one standout operation, the SolarMarker campaign.
💥In May 2024, #RecordedFuture published a report titled Exploring the Depths of #SolarMarker's Multi-Tiered Infrastructure, shedding light on the sophisticated, layered design of SolarMarker’s infrastructure.
Key takeaways:
🔒SolarMarker’s operations revolve around a multi-tiered infrastructure, consisting of at least two distinct clusters: a primary cluster for active attacks and a secondary one likely used for testing strategies or focusing on specific targets.
🔒This layered structure enables SolarMarker to rapidly adapt, making it resilient against countermeasures and exceptionally difficult to dismantle.
🔒The overlap with the SSH key controlling over 150 servers raises questions about the cross-use of this infrastructure for both criminal and possibly nation-state purposes?
Could this SSH key be a core element of a larger, interconnected infrastructure supporting various cyber campaigns ie criminal and Nation-State?
#CyberEspionage #SolarMarker #NationState #CyberThreat #Malware #ThreatIntel #RecordedFuture #SSHKey
💥Tracking the same SSH key fingerprint_sha256: c655bae831ca57a857b26d76a7c98a56a65d00fdab7d234a64addf8166e3cd09, we uncover its role in various malware campaigns, with one standout operation, the SolarMarker campaign.
💥In May 2024, #RecordedFuture published a report titled Exploring the Depths of #SolarMarker's Multi-Tiered Infrastructure, shedding light on the sophisticated, layered design of SolarMarker’s infrastructure.
Key takeaways:
🔒SolarMarker’s operations revolve around a multi-tiered infrastructure, consisting of at least two distinct clusters: a primary cluster for active attacks and a secondary one likely used for testing strategies or focusing on specific targets.
🔒This layered structure enables SolarMarker to rapidly adapt, making it resilient against countermeasures and exceptionally difficult to dismantle.
🔒The overlap with the SSH key controlling over 150 servers raises questions about the cross-use of this infrastructure for both criminal and possibly nation-state purposes?
Could this SSH key be a core element of a larger, interconnected infrastructure supporting various cyber campaigns ie criminal and Nation-State?
#CyberEspionage #SolarMarker #NationState #CyberThreat #Malware #ThreatIntel #RecordedFuture #SSHKey
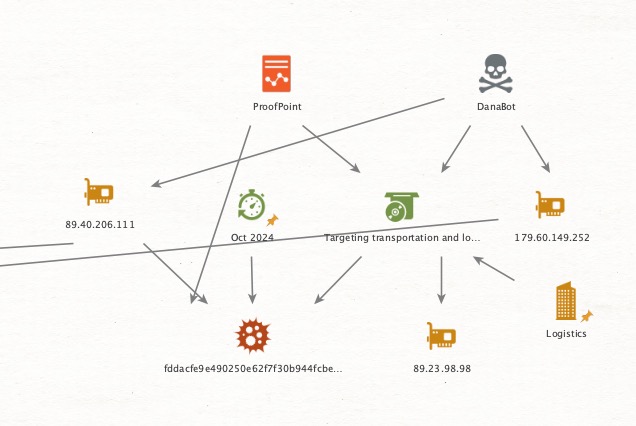
Thread 6/ 🔍 Keys to the Kingdom: Ongoing Campaign Targets Logistics Sector - China’s Involvement? 🔍
💥Fast forward to October 2024, and a new, active campaign is unfolding, with #Proofpoint reporting targeted attacks on North American transportation and #logistics firms.
In their latest brief, Security Brief: Actor Uses Compromised Accounts, Customised Social Engineering to Target Transport and Logistics Firms with Malware, Proofpoint researchers outline a sophisticated operation where compromised, legitimate email accounts from transportation and shipping companies are weaponised to deliver various malware payloads.
Key findings from Proofpoint’s report:
🔒This campaign uses compromised email accounts from legitimate transportation and logistics firms to inject malicious content into existing conversations, making messages appear authentic.
🔒Since May 2024, researchers have observed this activity cluster, initially delivering Lumma Stealer, StealC, and NetSupport. However, from August 2024, the actor introduced new infrastructure and delivery techniques, adding payloads like DanaBot and Arechclient2.
🔒The primary delivery method involves emails containing Google Drive URLs or directly attached .URL files that, when executed, connect via SMB to download malware from a remote share.
💥Here’s where things take an intriguing turn: one of the IPs, 89.40.206.111, linked to this campaign is associated with SSH key fingerprint_sha256: bd613b3be57f18c3bceb0aaf86a28ad8b6df7f9bccacf58044f1068d1787f8a5 the same SSH key connected to Chinese cyber activity.
🔍Could this connection mean China has a vested interest in the logistics and transportation sector?
🔍While historically linked to espionage, Chinese actors could see value in disrupting or surveilling global logistics for strategic insights or influence.
The reappearance of this SSH key highlights the possibility that this infrastructure is part of a broader, nation-state-backed campaign with multiple objectives.
Are we witnessing China using criminal tactics to obscure state-backed intelligence gathering in the logistics sector?
#CyberEspionage #LogisticsSector #China #Proofpoint #Malware #ThreatIntel #NationState #SSHKey #Transportation
💥Fast forward to October 2024, and a new, active campaign is unfolding, with #Proofpoint reporting targeted attacks on North American transportation and #logistics firms.
In their latest brief, Security Brief: Actor Uses Compromised Accounts, Customised Social Engineering to Target Transport and Logistics Firms with Malware, Proofpoint researchers outline a sophisticated operation where compromised, legitimate email accounts from transportation and shipping companies are weaponised to deliver various malware payloads.
Key findings from Proofpoint’s report:
🔒This campaign uses compromised email accounts from legitimate transportation and logistics firms to inject malicious content into existing conversations, making messages appear authentic.
🔒Since May 2024, researchers have observed this activity cluster, initially delivering Lumma Stealer, StealC, and NetSupport. However, from August 2024, the actor introduced new infrastructure and delivery techniques, adding payloads like DanaBot and Arechclient2.
🔒The primary delivery method involves emails containing Google Drive URLs or directly attached .URL files that, when executed, connect via SMB to download malware from a remote share.
💥Here’s where things take an intriguing turn: one of the IPs, 89.40.206.111, linked to this campaign is associated with SSH key fingerprint_sha256: bd613b3be57f18c3bceb0aaf86a28ad8b6df7f9bccacf58044f1068d1787f8a5 the same SSH key connected to Chinese cyber activity.
🔍Could this connection mean China has a vested interest in the logistics and transportation sector?
🔍While historically linked to espionage, Chinese actors could see value in disrupting or surveilling global logistics for strategic insights or influence.
The reappearance of this SSH key highlights the possibility that this infrastructure is part of a broader, nation-state-backed campaign with multiple objectives.
Are we witnessing China using criminal tactics to obscure state-backed intelligence gathering in the logistics sector?
#CyberEspionage #LogisticsSector #China #Proofpoint #Malware #ThreatIntel #NationState #SSHKey #Transportation
Thread 7/ 🔍 Keys to the Kingdom: The Big Picture Unfolds 🔍
From espionage to ransomware, overlapping SSH keys reveal a sprawling, multi-faceted campaign possibly involving nation-states.
Are these actors leveraging criminal tactics as cover, or is it a larger play in global cyber strategy? One thing's clear: the game is far from over.
#CyberEspionage #NationState #ThreatIntel #Logistics #Malware
From espionage to ransomware, overlapping SSH keys reveal a sprawling, multi-faceted campaign possibly involving nation-states.
Are these actors leveraging criminal tactics as cover, or is it a larger play in global cyber strategy? One thing's clear: the game is far from over.
#CyberEspionage #NationState #ThreatIntel #Logistics #Malware

mybad - pasted the wrong hash it should be fingerprint_sha256:c655bae831ca57a857b26d76a7c98a56a65d00fdab7d234a64addf8166e3cd09 🙃
• • •
Missing some Tweet in this thread? You can try to
force a refresh