1/ An investigation into the social engineering scammer Ronaldd (Ronald Spektor) who allegedly helped steal $6.5M last month from a single victim by impersonating Coinbase support. 





2/ A US based victim sent me a DM on Oct 7, 2024 after receiving a call from a spoofed number impersonating Coinbase support where they were coerced in to using a phishing site.
Theft address
bc1qra7s4wl8z2el335k40sdnaka04c2sdwjx5hs6q
0x730082b1847e1cef889ea6dce57641c96c104f2d
Phishing site: https(:)//19960018-coinbase(.)com
Theft address
bc1qra7s4wl8z2el335k40sdnaka04c2sdwjx5hs6q
0x730082b1847e1cef889ea6dce57641c96c104f2d
Phishing site: https(:)//19960018-coinbase(.)com

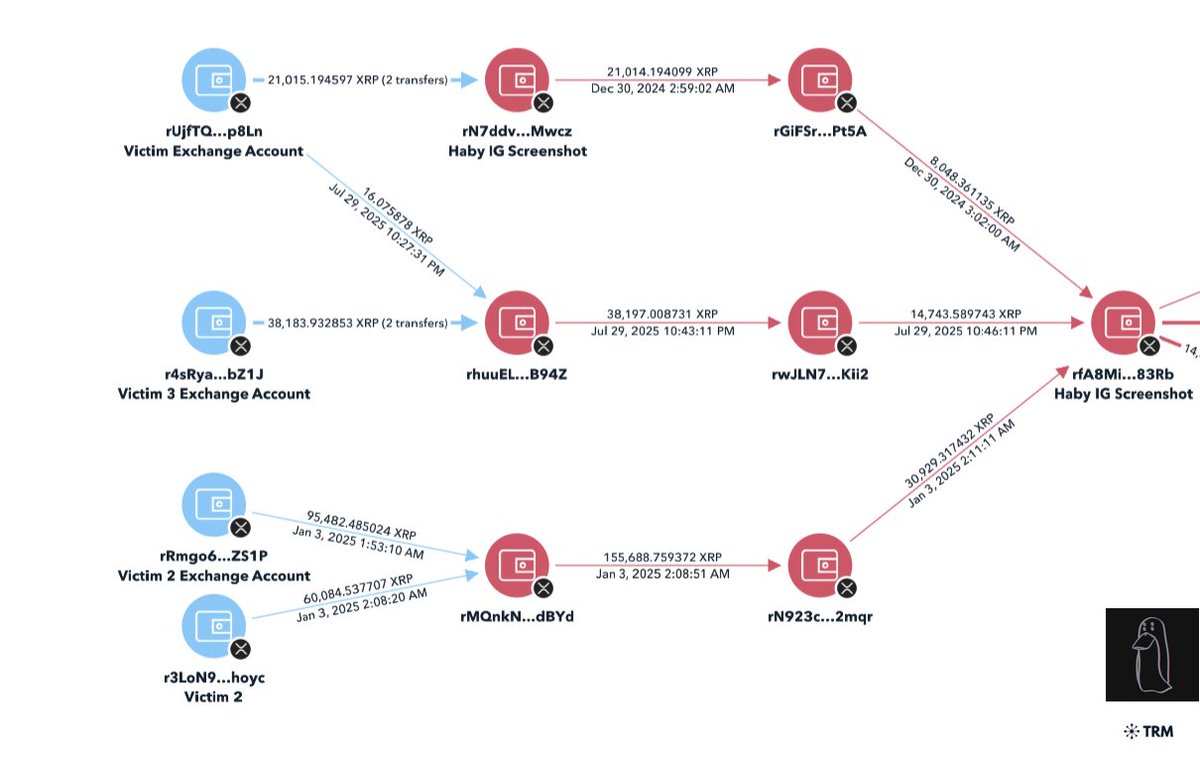
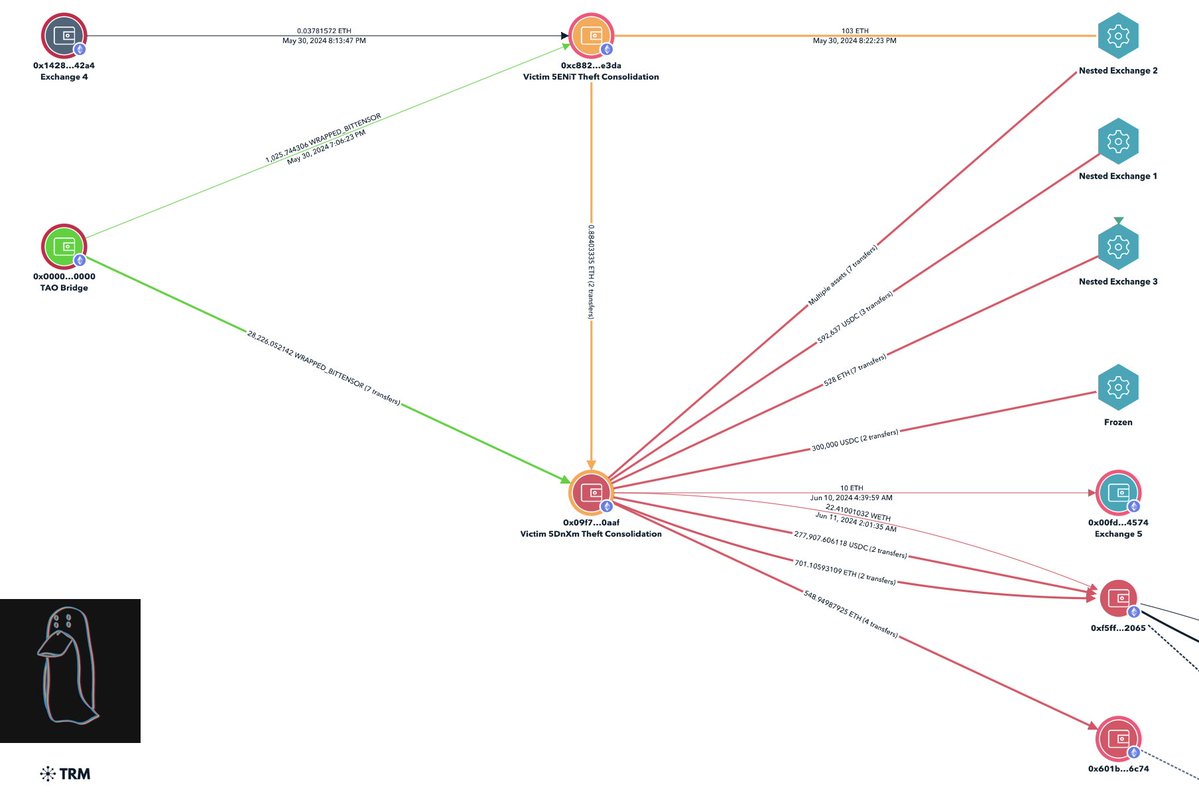
3/ An initial tracing of the theft saw all of the stolen funds flow to eXch on Ethereum and Bitcoin where funds were converted to Litecoin and transferred to numerous services. 

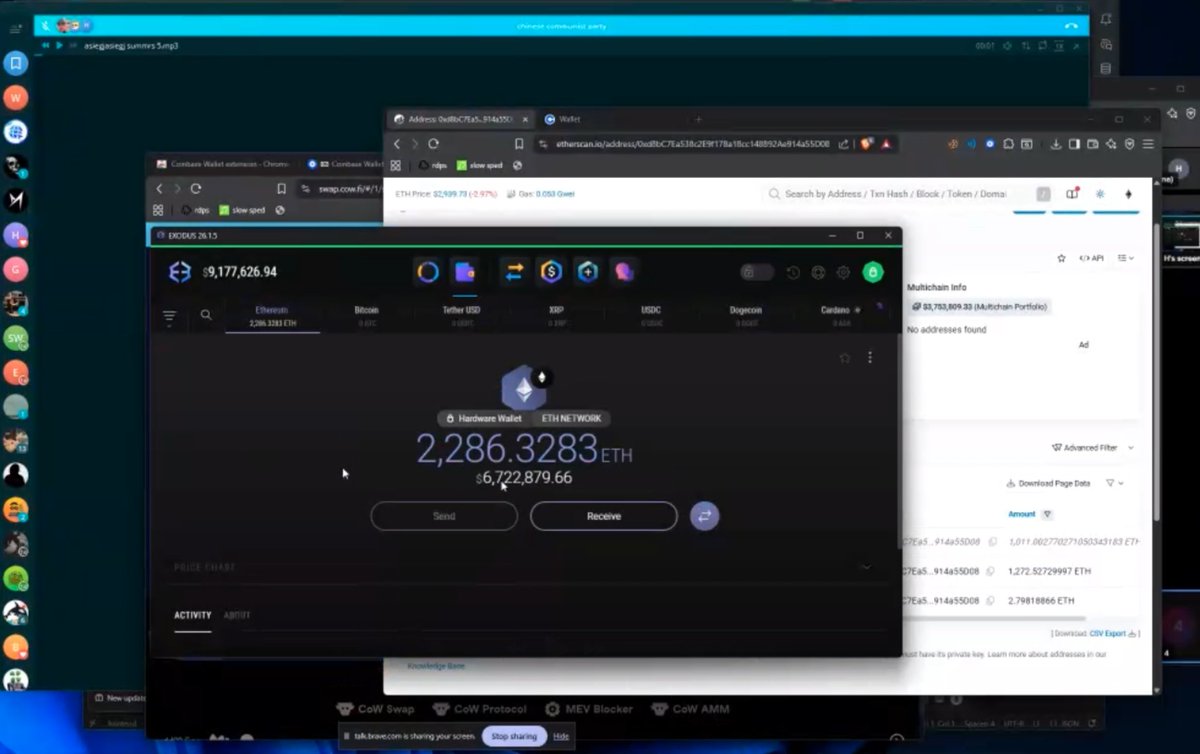
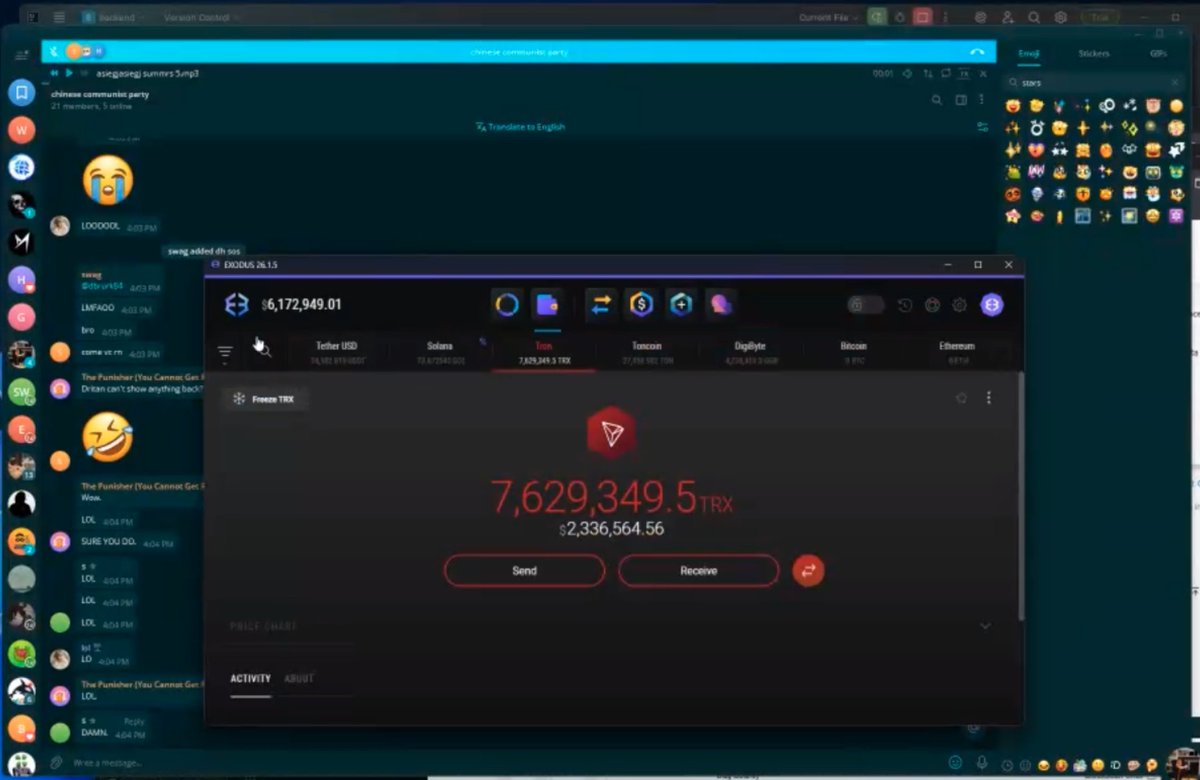
4/ However just days after the theft Ronald began flexing his Ledger Live via Discord screenshare showing $3.1M received on October 8th, 2024.
Discord ID: 367190432507232257
Discord ID: 367190432507232257

5/ Further strengthening the connection to Ronald, a now deleted Telegram channel in his bio associated with fraud shared screenshots of a wallet address only one hop from the $6.5M theft. 




6/ When reviewing the TON address which owns Ronald’s Telegram number you can see it was funded from multiple exchanges.
You can perform a timing analysis to trace through the exchange and find the funding address.
That address is tied to multiple other Coinbase withdrawals indicating more potential victims from impersonation scams.
TON source address
EQC7hYcQ_54HWpPhhT_i3gExFeCKspqdJmwGrZYBGTB09Ot4
ETH destination address
0x09d51a41434149b2f85358e518631f7004b0ae68

You can perform a timing analysis to trace through the exchange and find the funding address.
That address is tied to multiple other Coinbase withdrawals indicating more potential victims from impersonation scams.
TON source address
EQC7hYcQ_54HWpPhhT_i3gExFeCKspqdJmwGrZYBGTB09Ot4
ETH destination address
0x09d51a41434149b2f85358e518631f7004b0ae68


7/ Multiple databreaches have publicly exposed Ronald’s information such as the Flipd/OG User breaches leaking his email and New York IPs which link to other breaches containing his alleged full name.
8/ Unfortunately this case does not have a happy ending as the victim deleted his X account after receiving bad advice from a friend to not trust people who online.
It still remains uncertain who Ronald’s accomplices were for the theft as the Ledger screenshots only shows $3.1M out of the $6.5M that was stolen.
It still remains uncertain who Ronald’s accomplices were for the theft as the Ledger screenshots only shows $3.1M out of the $6.5M that was stolen.

• • •
Missing some Tweet in this thread? You can try to
force a refresh