1/ The promised laughs/tears of the day have arrived!
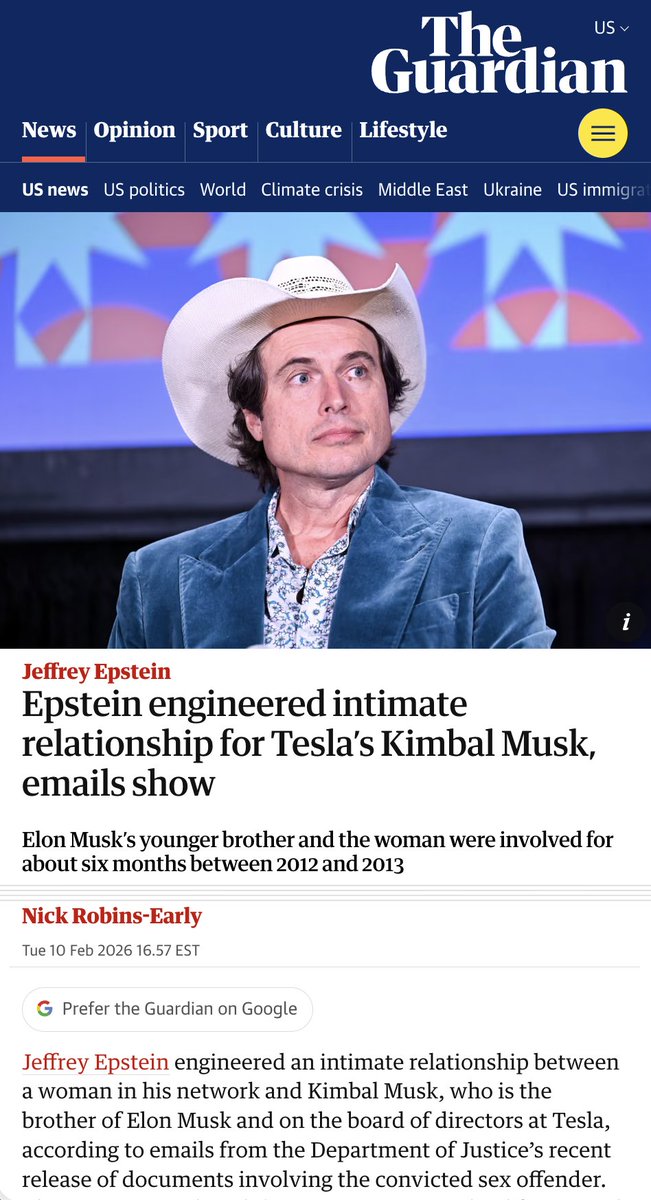
Buckle up y'all! Remember that incel loser who came at me the other day (image below, top left)? 👇🤠
Let's talk about it. Signals indicate the account belongs to Vladislav "Artem" Klyushin, a convicted hacker who was recently traded back to Moscow (Artem is a common diminutive for Vladislav).
He's wealthy and well-connected, is an associate of a GRU operative already indicted by the U.S. for interference in the 2016 election, runs cybersecurity firm "M-13" which does IT work for Putin's office, and was–and may still actively be–one of Putin's "Musketeers" (bodyguards, somewhat akin to the Secret Service) in the Federal Protective Service (FSO), which is reportedly assigned some level of responsibility over information warfare.
ARTEM_KLYUSHIN represents a high-level Kremlin influence actor who combines cyber and info warfare capabilities, financial operations, and direct policy influence through social media channels owned by his partners to achieve the goals of the man to whom he is loyal.
KEY FINDINGS
> Direct operational connection to GRU through indicted business partner Yermakov
> Demonstrated ability to predict and potentially influence major U.S. policy decisions
> Pre-arranged platform access on X
> Evidence of active, long-running coordination with Trump world + Musk
> Visible systematic strategy to degrade U.S. institutional safeguards
I apologize if images are a bit fuzzy, as the size limit on X is 10mb–I can also mirror these elsewhere later.
Buckle up y'all! Remember that incel loser who came at me the other day (image below, top left)? 👇🤠
Let's talk about it. Signals indicate the account belongs to Vladislav "Artem" Klyushin, a convicted hacker who was recently traded back to Moscow (Artem is a common diminutive for Vladislav).
He's wealthy and well-connected, is an associate of a GRU operative already indicted by the U.S. for interference in the 2016 election, runs cybersecurity firm "M-13" which does IT work for Putin's office, and was–and may still actively be–one of Putin's "Musketeers" (bodyguards, somewhat akin to the Secret Service) in the Federal Protective Service (FSO), which is reportedly assigned some level of responsibility over information warfare.
ARTEM_KLYUSHIN represents a high-level Kremlin influence actor who combines cyber and info warfare capabilities, financial operations, and direct policy influence through social media channels owned by his partners to achieve the goals of the man to whom he is loyal.
KEY FINDINGS
> Direct operational connection to GRU through indicted business partner Yermakov
> Demonstrated ability to predict and potentially influence major U.S. policy decisions
> Pre-arranged platform access on X
> Evidence of active, long-running coordination with Trump world + Musk
> Visible systematic strategy to degrade U.S. institutional safeguards
I apologize if images are a bit fuzzy, as the size limit on X is 10mb–I can also mirror these elsewhere later.

2/ Klyushin's cyber capabilities and social media operations likely stem from FSO training/connections rather than just GRU links. His relative ease of access to both Putin and elite western figures fits the operational pattern of FSO based on what is publicly known.
> FSO training/connection explains combination of technical and social capabilities
> Part of Putin's "Musketeers" system of trusted operators in strategic positions
> Activities mirror FSO's evolution from protection to Active Measures
> Uses FSO-style elite access patterns (ex. social events)
> Demonstrates FSO's characteristic focus on info warfare and institutional penetration
FSO officers being "elevated to ministerial posts and regional leadership positions" as described in the article below contextualizes Klyushin's focus on U.S. personnel appointments and institutional restructuring in his recent social media activity.
> FSO training/connection explains combination of technical and social capabilities
> Part of Putin's "Musketeers" system of trusted operators in strategic positions
> Activities mirror FSO's evolution from protection to Active Measures
> Uses FSO-style elite access patterns (ex. social events)
> Demonstrates FSO's characteristic focus on info warfare and institutional penetration
FSO officers being "elevated to ministerial posts and regional leadership positions" as described in the article below contextualizes Klyushin's focus on U.S. personnel appointments and institutional restructuring in his recent social media activity.

3/ Following his August 2024 release in a prisoner swap with the Kremlin in which he was exchanged for Evan Gershkovich, Paul Whelan, and others, he has publicly demonstrated a coordinated strategy of malicious targeting of U.S. institutions in collusion with domestic elected officials and unelected actors from the safety of his newly Russian digs.
Klyushin's post-release strategy shows three phases:
1. Electoral predictions and maps (establishing credibility, suggesting control)
2. Institutional restructuring "proposals" (targeting security apparatus)
3. "The Plan" narrative (coordinating multiple actors)
Each phase demonstrates increasing operational boldness–but who really needs a covert channel when you can publicly direct your men Donald Trump and Elon Musk from the safety of the platform and administration they purchased and own?
OPERATIONAL METHODS
Info Ops
> Multi-phase messaging strategy progressing from cryptic to explicit
> Uses accurate predictions to build credibility
> Coordinates timing of releases with official announcements
> Maintains parallel Russian/English messaging tracks
Platform Manipulation
> Direct communication channel with platform ownership
> Sophisticated understanding of engagement metrics
> Strategic use of reposting and amplification
> Extremely low engagement relative to bot/follower activity
Network Activation
> Direct tagging of key figures (realDonaldTrump, elonmusk)
> Interaction with Trump Jr. regarding nominations
> Signs of coordinated messaging with other platform actors
> Strategic amplification of specific proposals
Klyushin's post-release strategy shows three phases:
1. Electoral predictions and maps (establishing credibility, suggesting control)
2. Institutional restructuring "proposals" (targeting security apparatus)
3. "The Plan" narrative (coordinating multiple actors)
Each phase demonstrates increasing operational boldness–but who really needs a covert channel when you can publicly direct your men Donald Trump and Elon Musk from the safety of the platform and administration they purchased and own?
OPERATIONAL METHODS
Info Ops
> Multi-phase messaging strategy progressing from cryptic to explicit
> Uses accurate predictions to build credibility
> Coordinates timing of releases with official announcements
> Maintains parallel Russian/English messaging tracks
Platform Manipulation
> Direct communication channel with platform ownership
> Sophisticated understanding of engagement metrics
> Strategic use of reposting and amplification
> Extremely low engagement relative to bot/follower activity
Network Activation
> Direct tagging of key figures (realDonaldTrump, elonmusk)
> Interaction with Trump Jr. regarding nominations
> Signs of coordinated messaging with other platform actors
> Strategic amplification of specific proposals

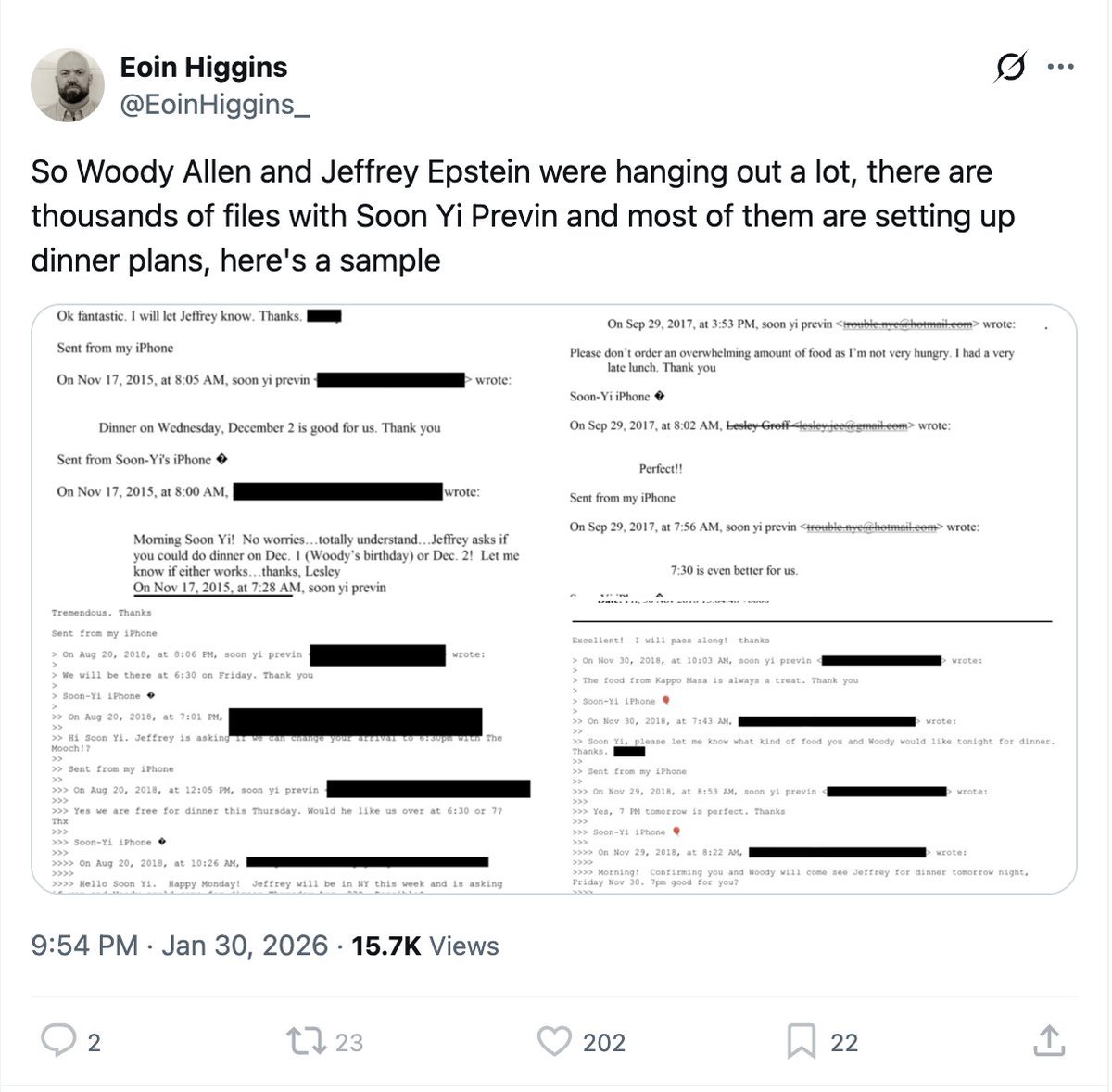
4/ Below is a sample of aligned and/or coordinated messaging with a known-bad actor, Felix Sater.
en.wikipedia.org/wiki/Felix_Sat…
en.wikipedia.org/wiki/Felix_Sat…

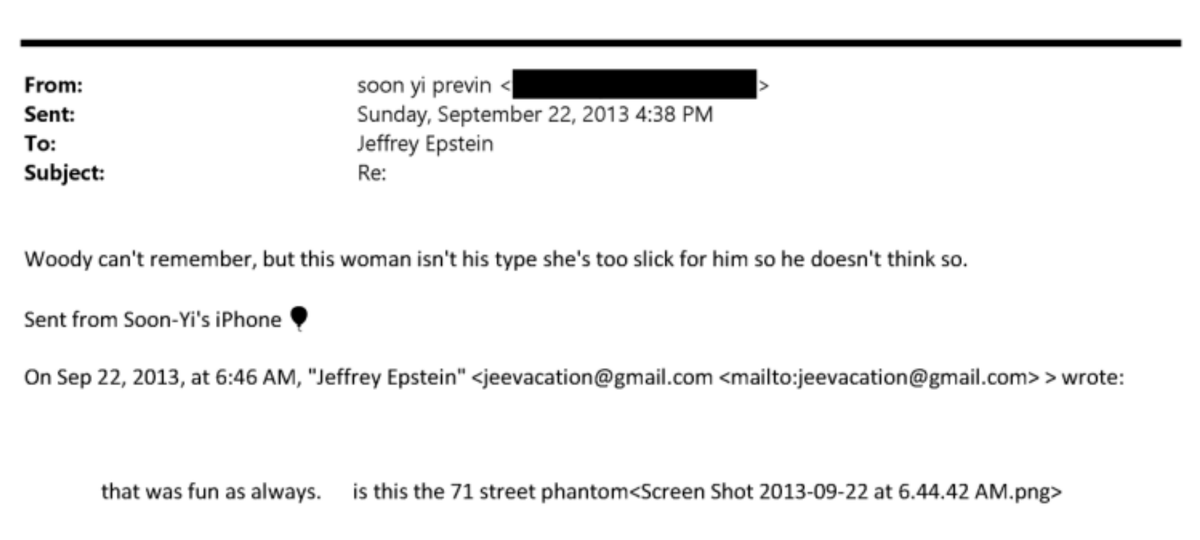
5/ His personnel predictions and public behaviors suggest a potentially high level of access to Trump's policy and decision making.
In 2018, he ordered John Kelly's firing, calling for "more compromising person."
Within 24 hours, Kelly was out.
In 2020, he directed Amy Coney Barrett's Supreme Court nomination–implemented within days.

In 2018, he ordered John Kelly's firing, calling for "more compromising person."
Within 24 hours, Kelly was out.
In 2020, he directed Amy Coney Barrett's Supreme Court nomination–implemented within days.


6/ This year, same pattern with Kash Patel for FBI.
STRATEGIC OBJECTIVES
Institutional Degradation
> Disable FBI counterintelligence capabilities
> Bypass State Department security protocols
> Install compromised individuals in key positions
> Create parallel power structures outside oversight
Network Establishment
> Position trusted actors in key roles
> Create direct communication channels
> Bypass traditional diplomatic protocols
> Establish family-based foreign policy apparatus
Systematic Vulnerability Creation
> Remove career intelligence professionals
> Disable internal security mechanisms
> Create unmonitored communication channels
> Establish deniable influence pathways
STRATEGIC OBJECTIVES
Institutional Degradation
> Disable FBI counterintelligence capabilities
> Bypass State Department security protocols
> Install compromised individuals in key positions
> Create parallel power structures outside oversight
Network Establishment
> Position trusted actors in key roles
> Create direct communication channels
> Bypass traditional diplomatic protocols
> Establish family-based foreign policy apparatus
Systematic Vulnerability Creation
> Remove career intelligence professionals
> Disable internal security mechanisms
> Create unmonitored communication channels
> Establish deniable influence pathways

7/ Klyushin represents a new model of open influence operations–one in which cover for direct institutional targeting is barely required.
His operation demonstrates planning, integration, sophisticated understanding of America's vulnerabilities, and unprecedented boldness in openly proposing their exploitation.
His success rate in directing US personnel changes suggests sophisticated network of influence requiring immediate counterintelligence focus.
@DOJNatSec @FBI Anyone home? 👀
See also: x.com/davetroy/statu…
His operation demonstrates planning, integration, sophisticated understanding of America's vulnerabilities, and unprecedented boldness in openly proposing their exploitation.
His success rate in directing US personnel changes suggests sophisticated network of influence requiring immediate counterintelligence focus.
@DOJNatSec @FBI Anyone home? 👀
See also: x.com/davetroy/statu…
@threadreaderapp unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh