On Friday, December 20, 2024, the U.S. DOJ charged Rostislav Panev, a dual Russian-Israeli national, as a LockBit ransomware developer. Arrested in Israel, he awaits extradition to the U.S.
It's OSINT time!
It's OSINT time!
https://twitter.com/vxunderground/status/1871024288431587725

You know the drill: with predictasearch.com and predictagraph.com, I traced and mapped Rostislav Panev's complete digital footprint.
Explore the graph here: predictagraph.com/graph/snapshot…
Explore the graph here: predictagraph.com/graph/snapshot…

First things first, here’s the official information available:
- DOJ Press Release: justice.gov/opa/pr/united-…
- Superseding Complaint: justice.gov/opa/media/1381…

- DOJ Press Release: justice.gov/opa/pr/united-…
- Superseding Complaint: justice.gov/opa/media/1381…

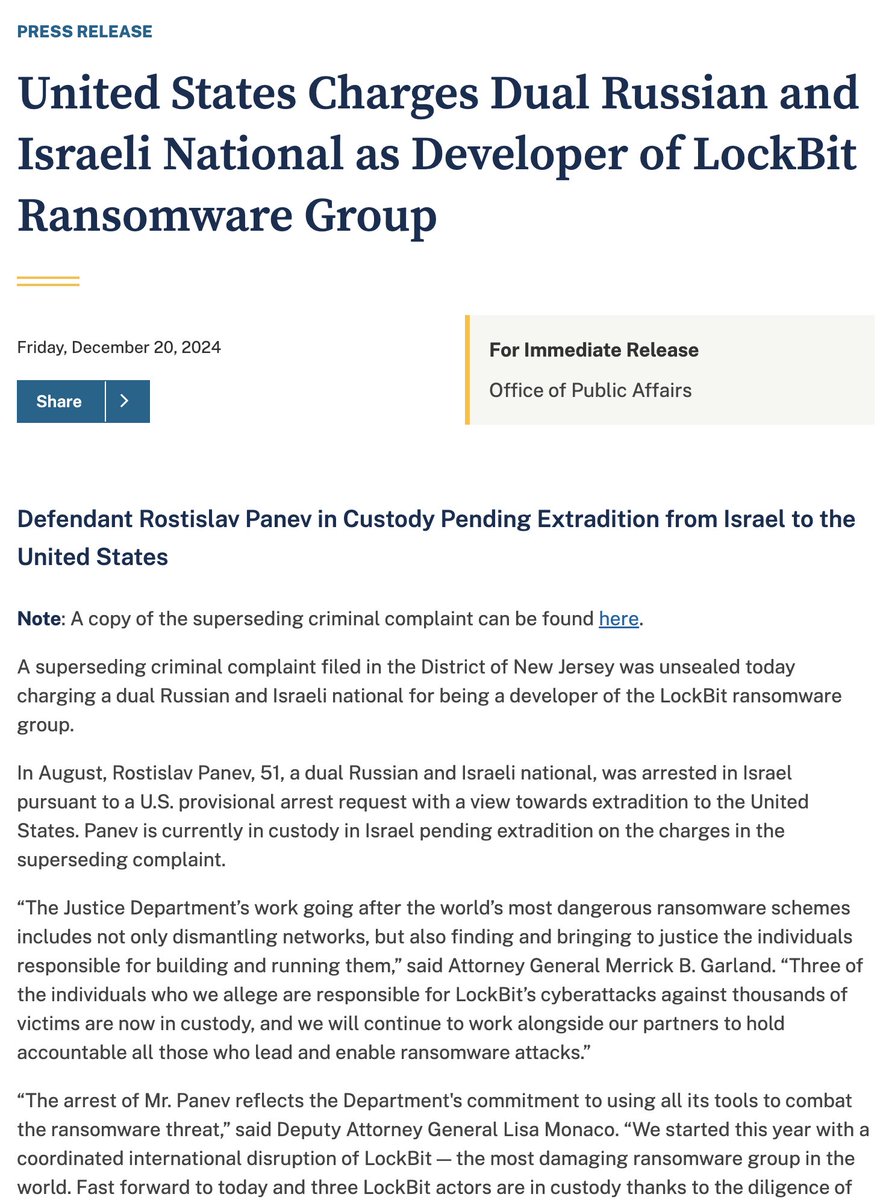
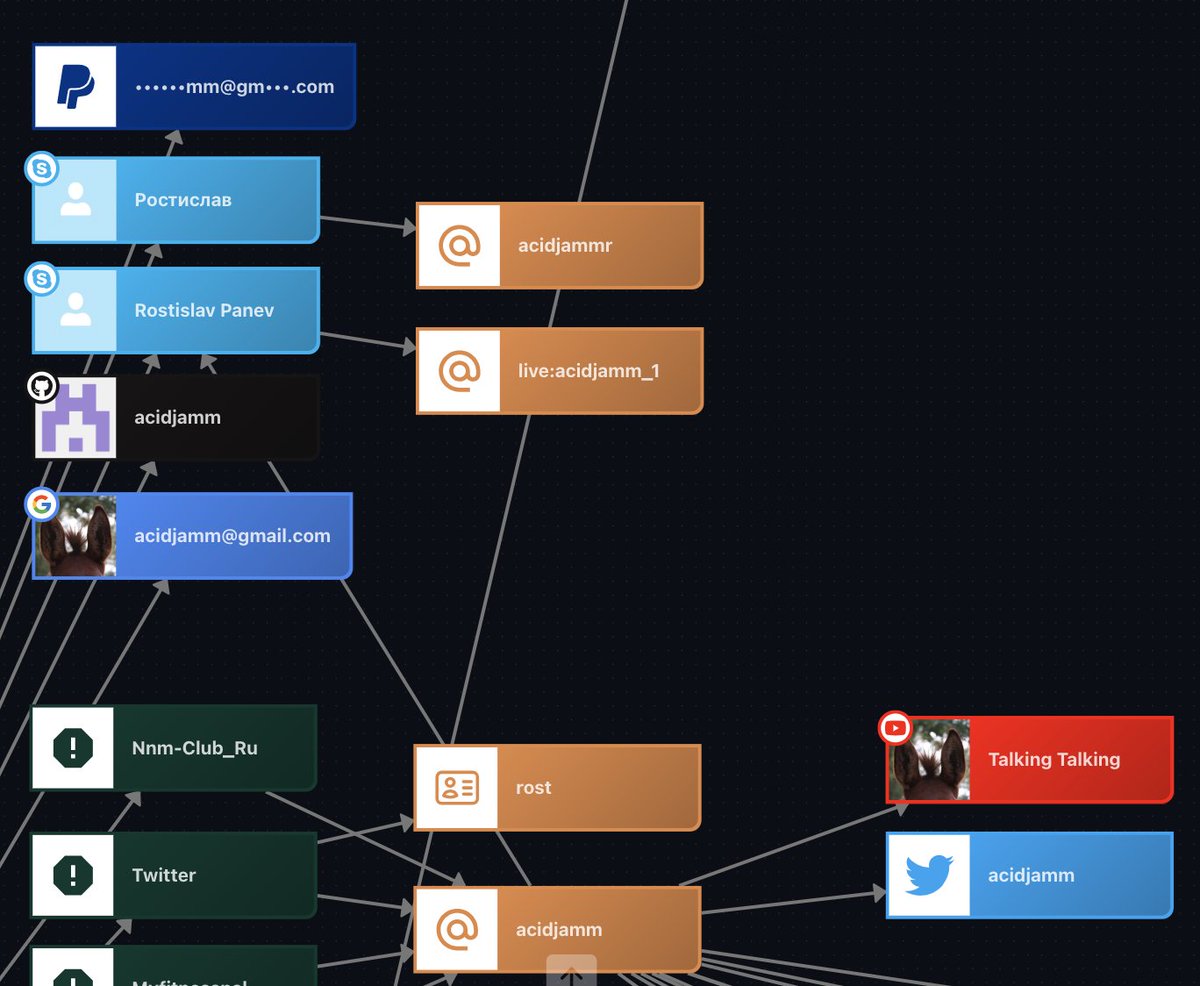
By searching the name "Rostislav Panev" in leaked data, we identified the email acidjamm@gmail.com appearing in two leaks.
At this stage, there's no confirmation that it belongs to "our Rostislav Panev".
At this stage, there's no confirmation that it belongs to "our Rostislav Panev".
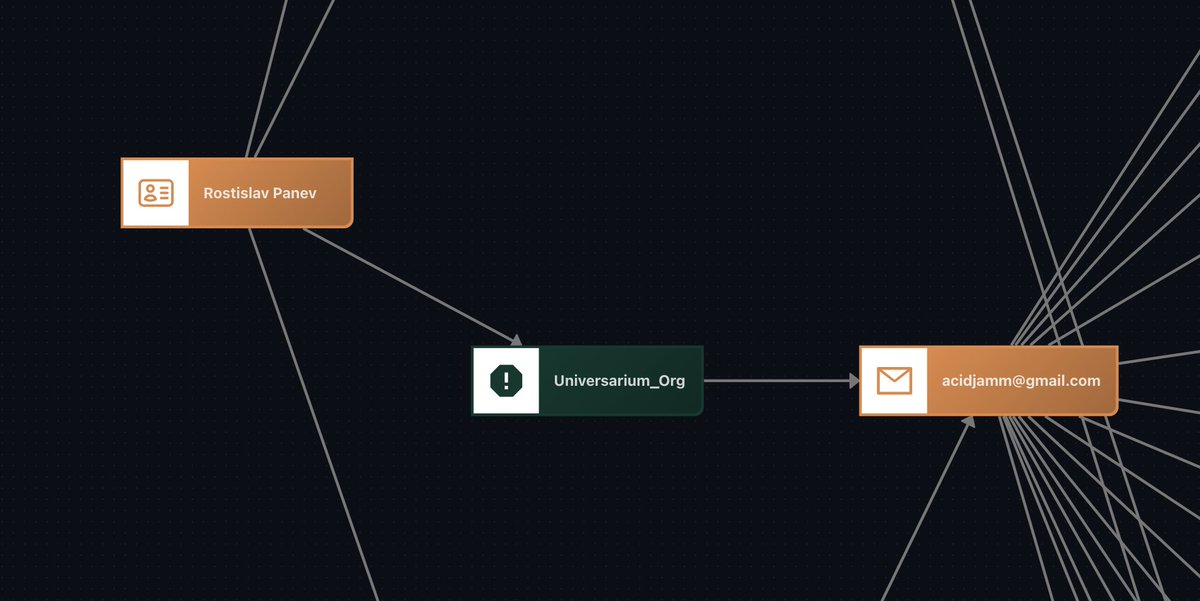
By searching the email acidjamm@gmail.com in leaked data, we uncovered additional details:
- Passwords: Several passwords associated with this email
- Phone: +79255540757
- Username: @acidjamm
- Passwords: Several passwords associated with this email
- Phone: +79255540757
- Username: @acidjamm
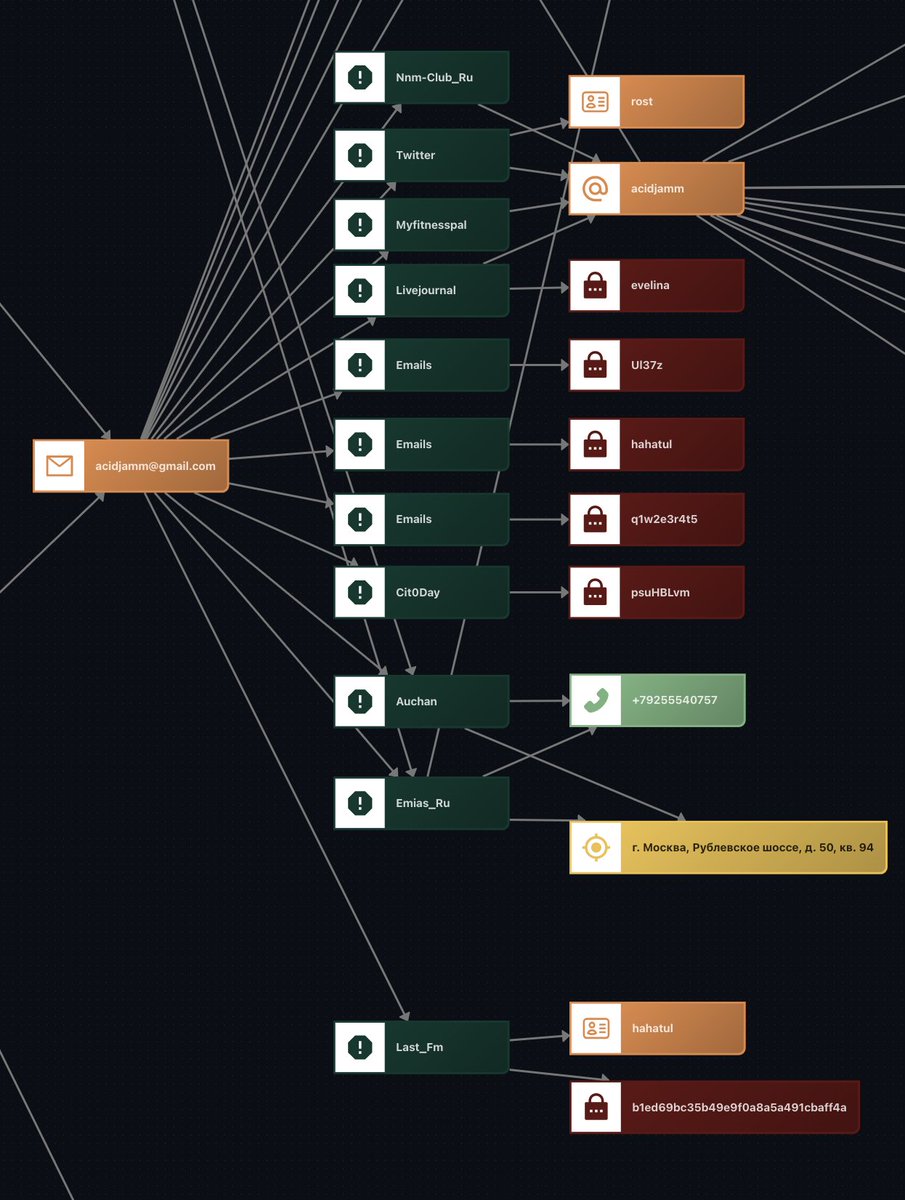
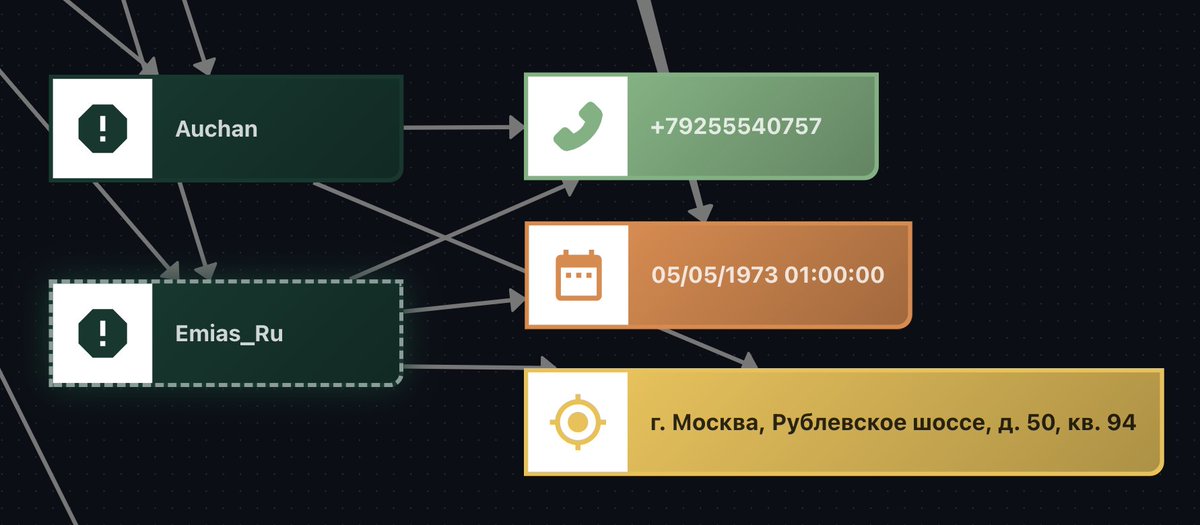
The emias_ru leak provided the confirmation we needed, revealing a date of birth: 1973-05-05. This aligns perfectly with the age of 51 mentioned in the DOJ press release. 

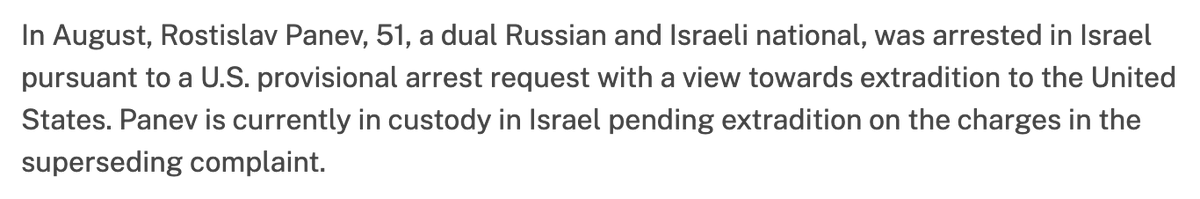
The intriguing detail comes from the username acidjamm, which links to a YouTube channel.
This channel has uploaded videos using a robotic voice, suggesting the entire operation was likely automated.
And the channel’s listed location? Israel.
youtube.com/@acidjamm


This channel has uploaded videos using a robotic voice, suggesting the entire operation was likely automated.
And the channel’s listed location? Israel.
youtube.com/@acidjamm
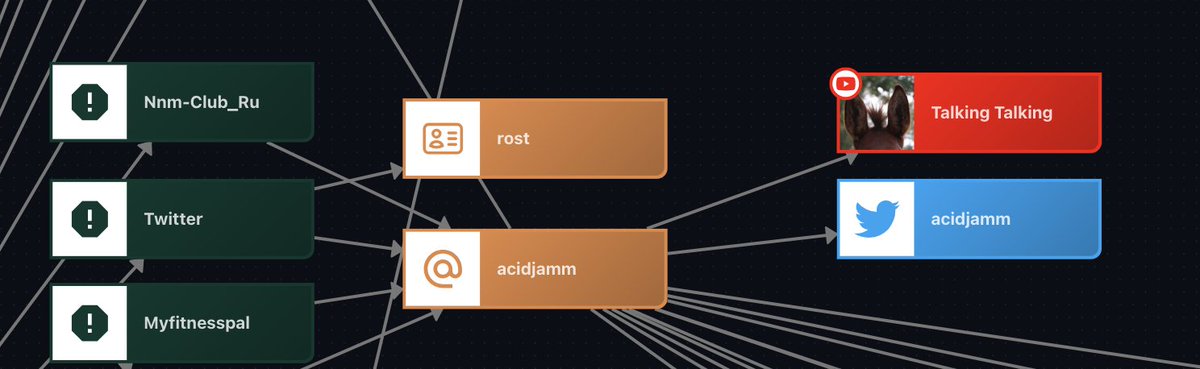
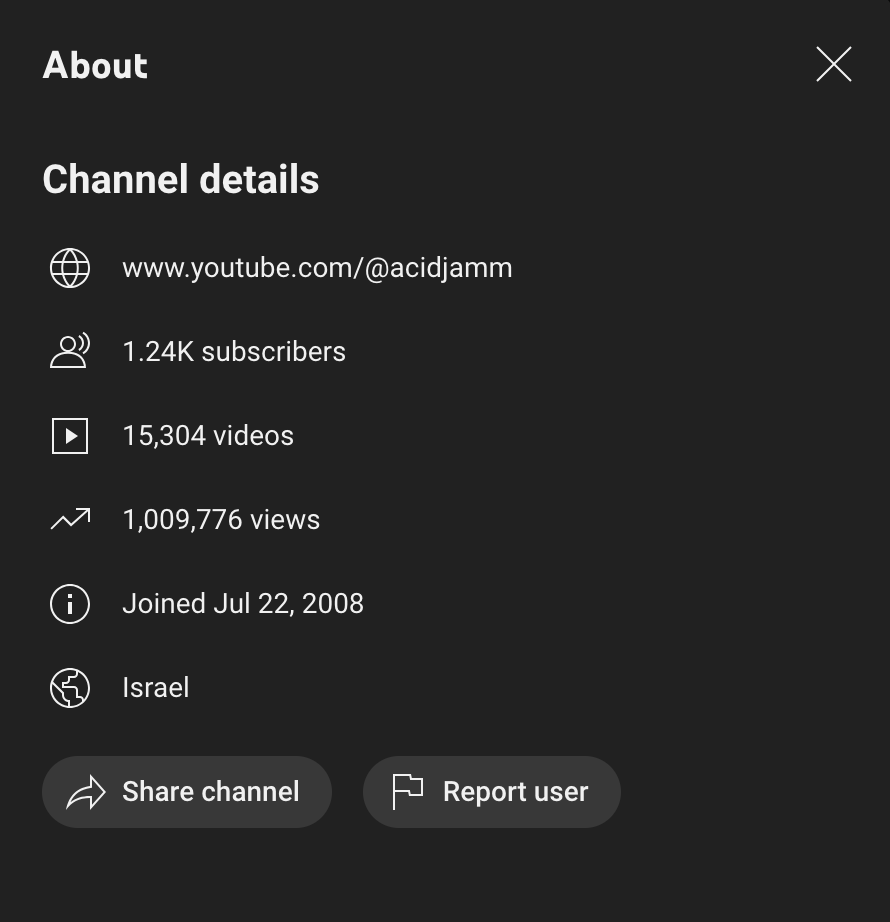
Another confirmation: the profile picture of the "Talking Talking" YouTube channel matches the profile picture of the Google account associated with acidjamm@gmail.com. 
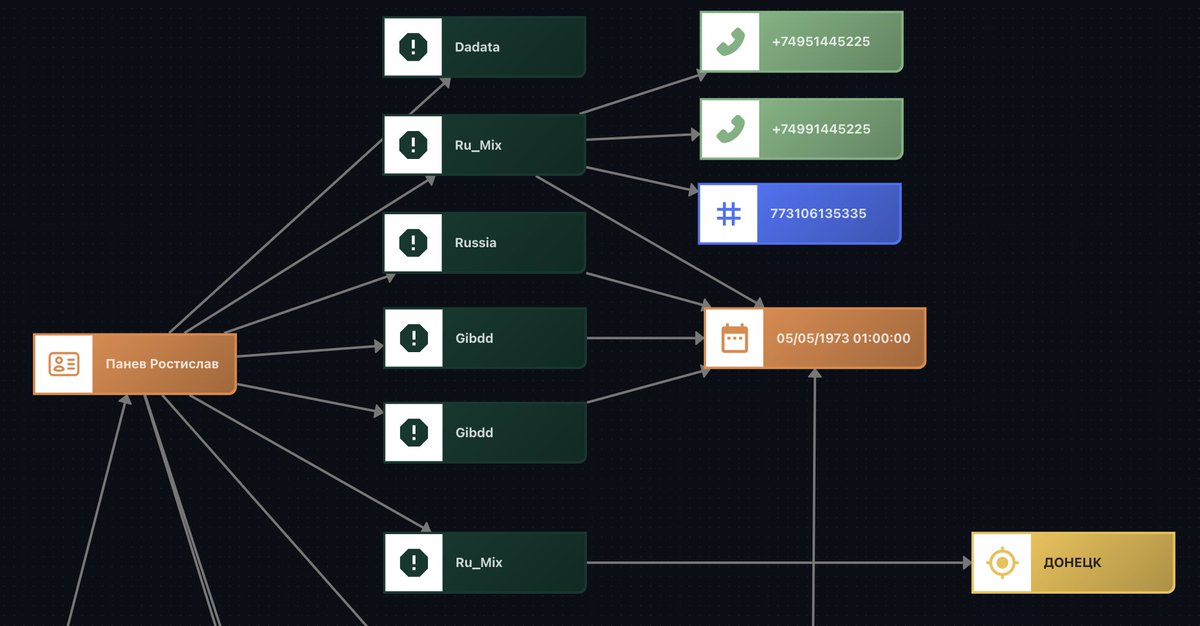
Searching his Cyrillic name "Панев Ростислав" revealed his INN, phone numbers, birthplace ДОНЕЦК, and once again confirmed his birth date! 
Finally, searching his name on Odnoklassniki, a major Russian social network, led us to his complete profile: . ok.ru/profile/539604…
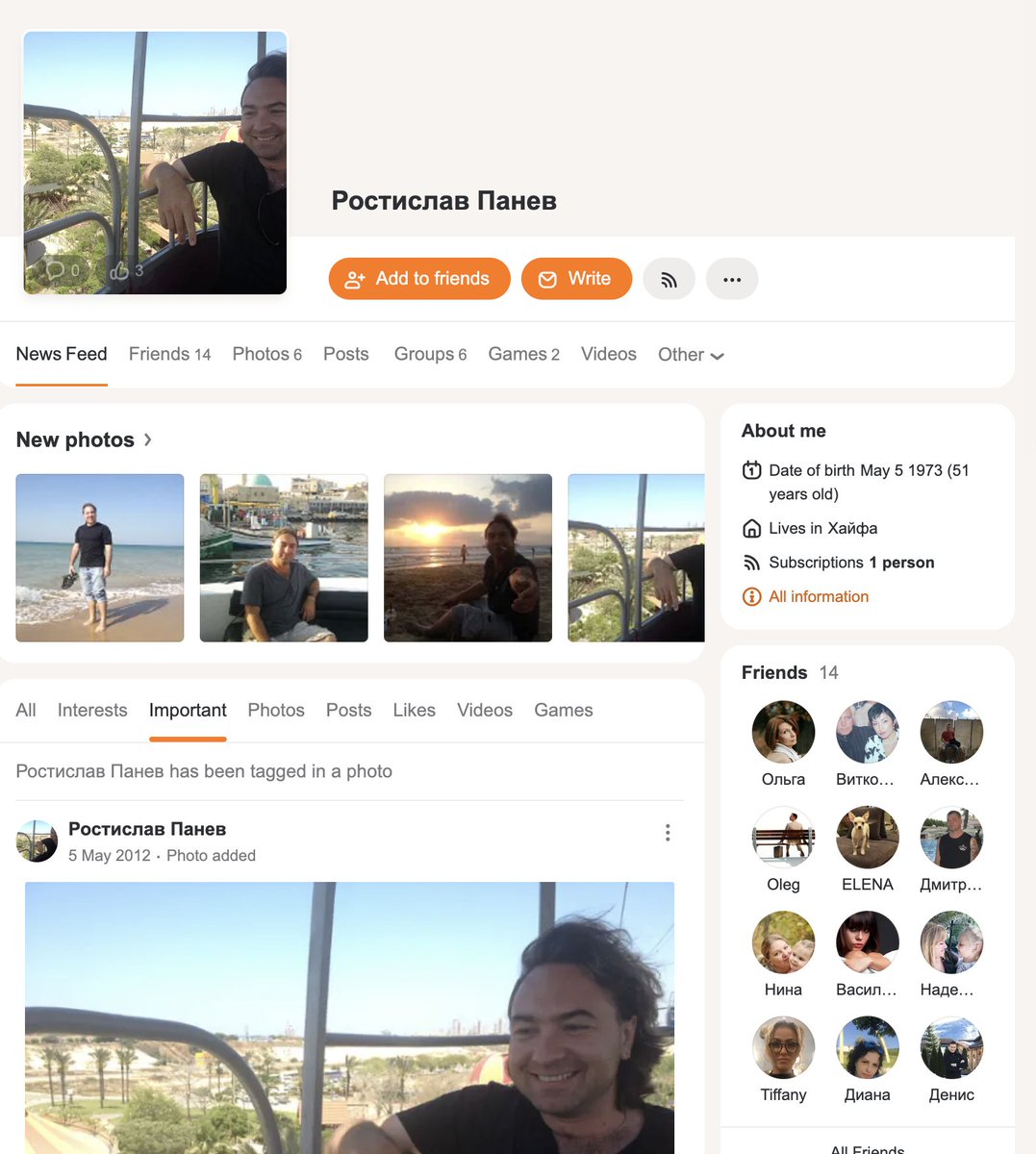
The last post on the profile dates back to 2012. One photo, for instance, was taken on Leopld ha-Sheni St, Acre, Israel.
google.com/maps/@32.91967…

google.com/maps/@32.91967…


And that's a wrap! 🎉
Check out the full graph here: predictagraph.com/graph/snapshot…
Remember to leverage predictasearch.com and predictagraph.com for your investigations!
Stay updated
x.com/fs0c131y/statu…
Check out the full graph here: predictagraph.com/graph/snapshot…
Remember to leverage predictasearch.com and predictagraph.com for your investigations!
Stay updated
x.com/fs0c131y/statu…
• • •
Missing some Tweet in this thread? You can try to
force a refresh

























