It's mathematically impossible to stop malware.
Due to Rice's Theorem, it's impossible to write a program that can perfectly determine if any given program is malicious.
This is because "being malicious" is a behavioral property of the program.
Due to Rice's Theorem, it's impossible to write a program that can perfectly determine if any given program is malicious.
This is because "being malicious" is a behavioral property of the program.
Even if we could perfectly define what "malicious behavior" *is* (which is a huge problem in of itself), any property about what a program will eventually do is undecidable.
Security in the traditional sense is probabilistic.
Security in the traditional sense is probabilistic.
In other words, we can make AVs very likely to catch malware, but you cannot mathematically guarantee it.
You can't:
- analyze all execution paths
- run for infinite time
- simulate all possible environments.
- predict all possible transformations
You can't:
- analyze all execution paths
- run for infinite time
- simulate all possible environments.
- predict all possible transformations
Look, I just created a perfect wiper, you can never know if it's malicious!
See, in practice, the concept is kind of silly. Just because you theoretically *can*, doesn't mean it's practical.
See, in practice, the concept is kind of silly. Just because you theoretically *can*, doesn't mean it's practical.
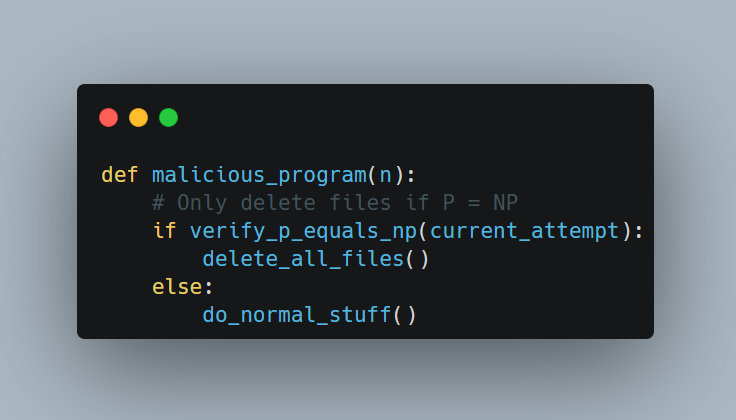
AV's can be *really* clever with signature detection, behavioral monitoring, and sandboxing.
The point is, it's an arms race, not a solved problem.
There's always going to be wild implementations of polymorphic and metamorphic code that execute malicious behavior.
The point is, it's an arms race, not a solved problem.
There's always going to be wild implementations of polymorphic and metamorphic code that execute malicious behavior.
All that said, it's neat to think about that even a theoretical superintelligence can't beat Rice's Theorem.
Perhaps the best defense against a rogue AGI is some undectable malware.
Perhaps the best defense against a rogue AGI is some undectable malware.
• • •
Missing some Tweet in this thread? You can try to
force a refresh