Worried about a TikTok ban? Americans are now flocking to Xiaohongshu (REDnote), another Chinese app.
Spoiler: Yes, it tracks its users.
Time to dive in! ⬇️
Spoiler: Yes, it tracks its users.
Time to dive in! ⬇️

When creating an account, you must verify your phone number by entering a code received via SMS.
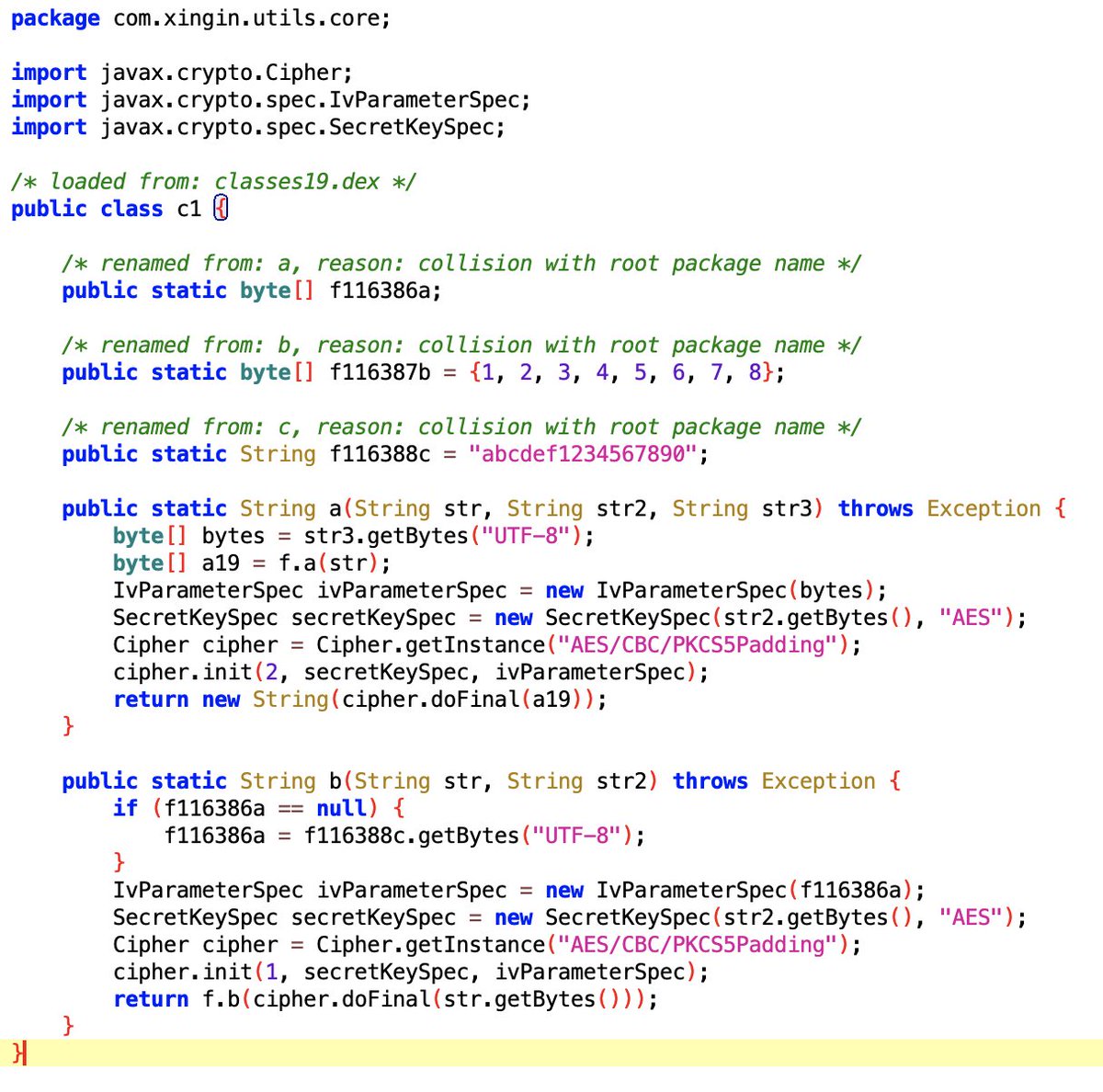
The request sent to Xiaohongshu's server includes your phone number (of course), along with your IDFA and IDFV.

The request sent to Xiaohongshu's server includes your phone number (of course), along with your IDFA and IDFV.


What’s an IDFA? The Identifier for Advertisers (IDFA) is a unique device ID assigned by Apple to every iOS device.
Many actors, like data brokers, use it to profile you, track your location, and more.
Many actors, like data brokers, use it to profile you, track your location, and more.
https://x.com/fs0c131y/status/1876975966334964076
When the user is activated, both the IDFA and IDFV are sent again.
Because why send it once when you can send it twice, right?
Because why send it once when you can send it twice, right?

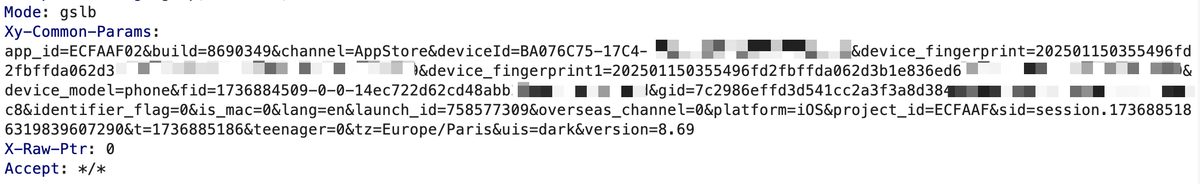
Nearly every request sent to Xiaohongshu's servers includes the Xy-Common-Params header, which contains:
- Device ID
- Device Fingerprint
- Device Model
- Language
- Platform
- Teenager Status
- Timezone
- And more...
- Device ID
- Device Fingerprint
- Device Model
- Language
- Platform
- Teenager Status
- Timezone
- And more...
During the process, your device information is also sent to Xiaohongshu's servers, enabling them to fingerprint your device.
This request includes:
- RAM size
- Boot time
- IP
- Carrier
- Country
- OS version
- HW model
- Timezone
- Language
- IDFA (yes, again!)
- Disk size
This request includes:
- RAM size
- Boot time
- IP
- Carrier
- Country
- OS version
- HW model
- Timezone
- Language
- IDFA (yes, again!)
- Disk size
Spending just 10 minutes on Xiaohongshu is enough to conclude that this app tracks user behavior and sends device information to its servers.
https://x.com/fs0c131y/status/1879298068702724568
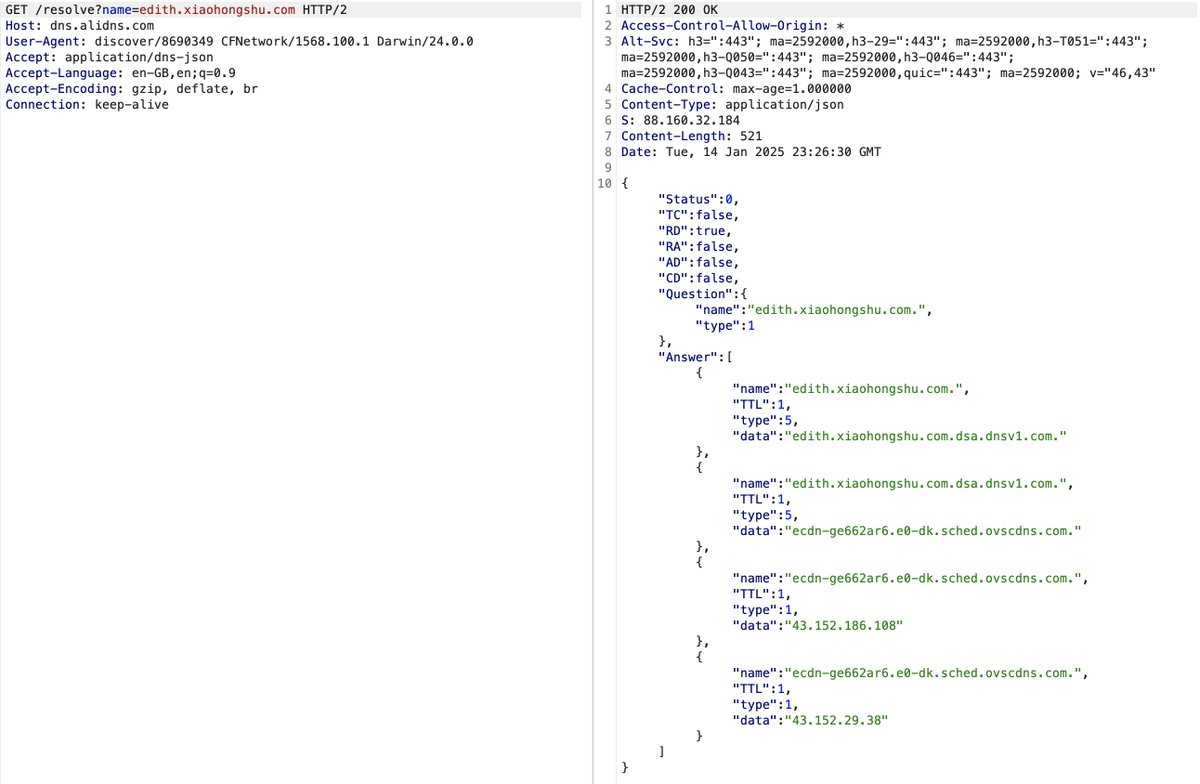
Where is the information sent aka where are the server located?
They use Tencent Cloud CDN, which makes sense for a Chinese app.
They use Tencent Cloud CDN, which makes sense for a Chinese app.
Spoiler: User tracking is widespread across apps, no matter their origin.
It threatens privacy and can pose national security risks.
The Gravy leak shows the dangers of centralizing massive amounts of data.
It threatens privacy and can pose national security risks.
The Gravy leak shows the dangers of centralizing massive amounts of data.
https://x.com/fs0c131y/status/1876975966334964076
This entire thread focuses on iOS, but it applies equally to Android. The Android equivalent of IDFA is called AAID.
Four years ago, I analyzed the data TikTok was transmitting, wrote a series of articles about it, and ultimately found myself testifying before a U.S. congressional committee.
baptisterobert.com/posts/tiktok-l…
baptisterobert.com/posts/tiktok-l…
• • •
Missing some Tweet in this thread? You can try to
force a refresh