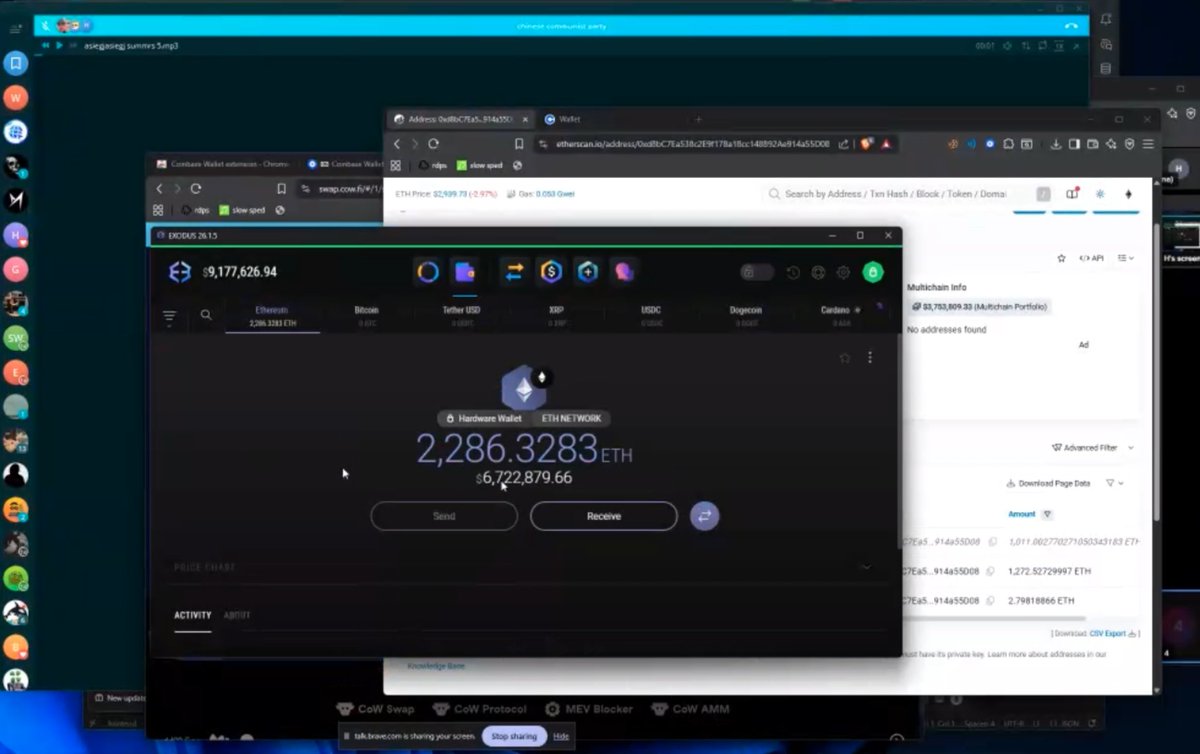
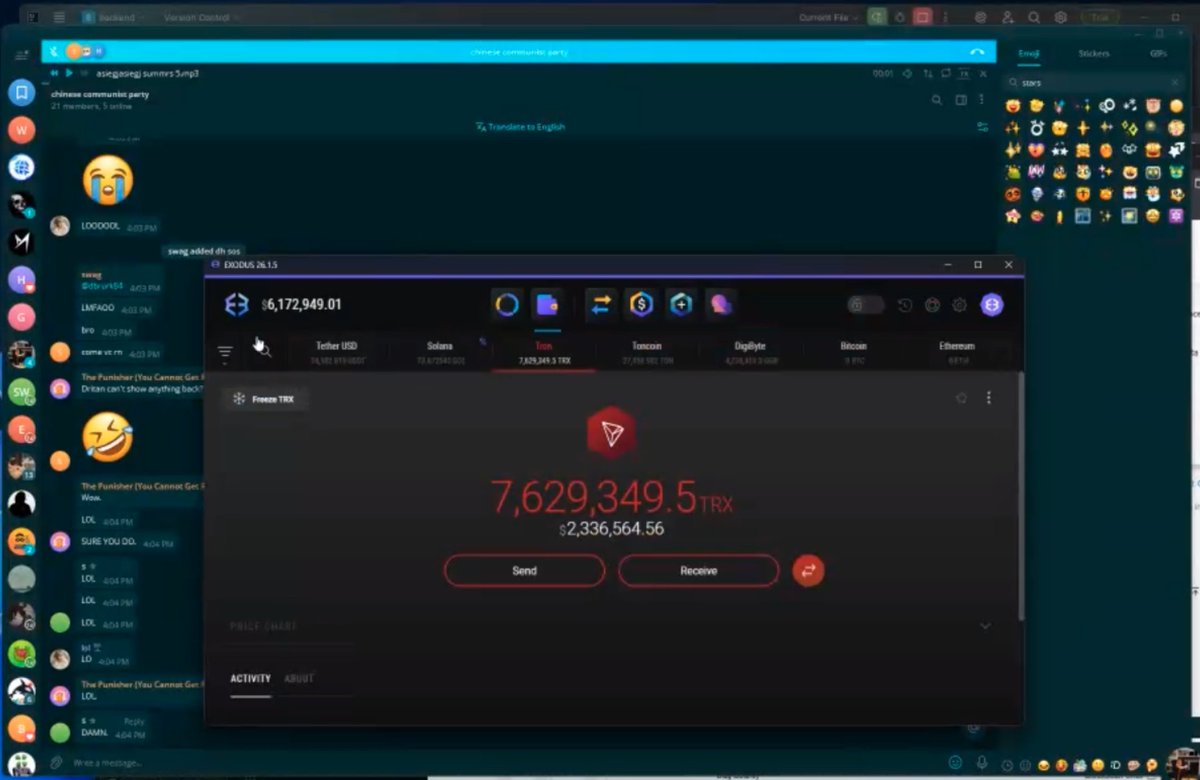
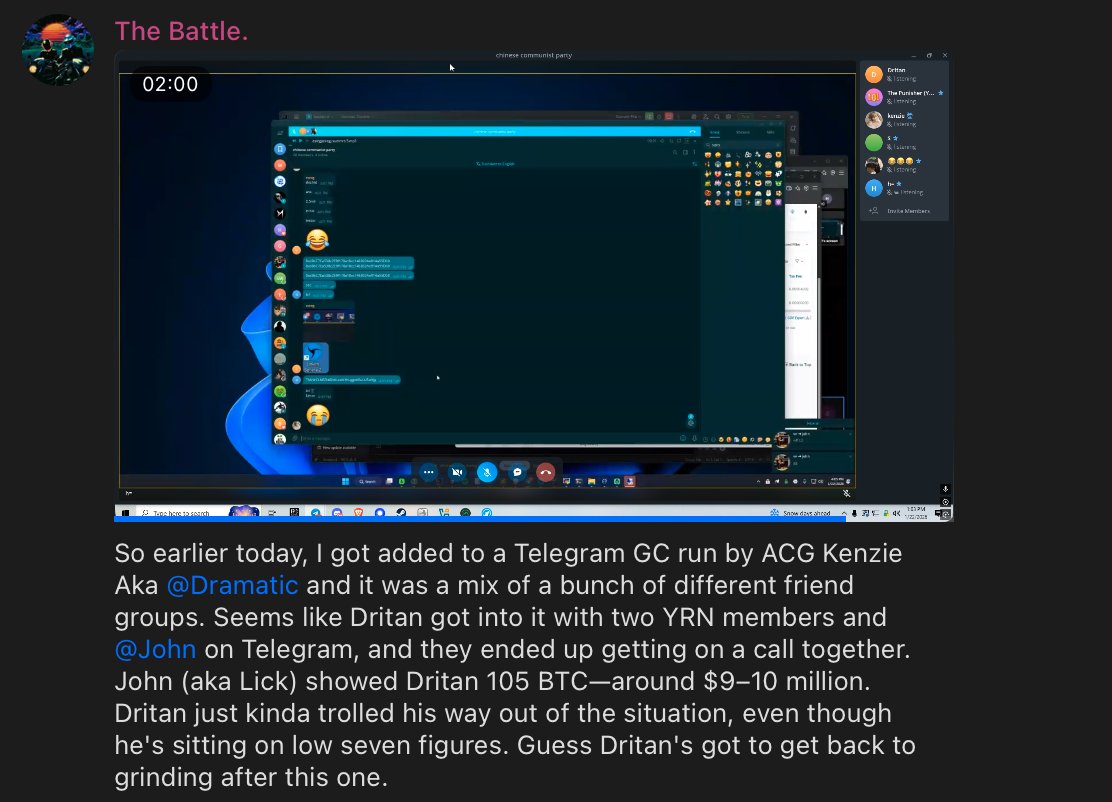
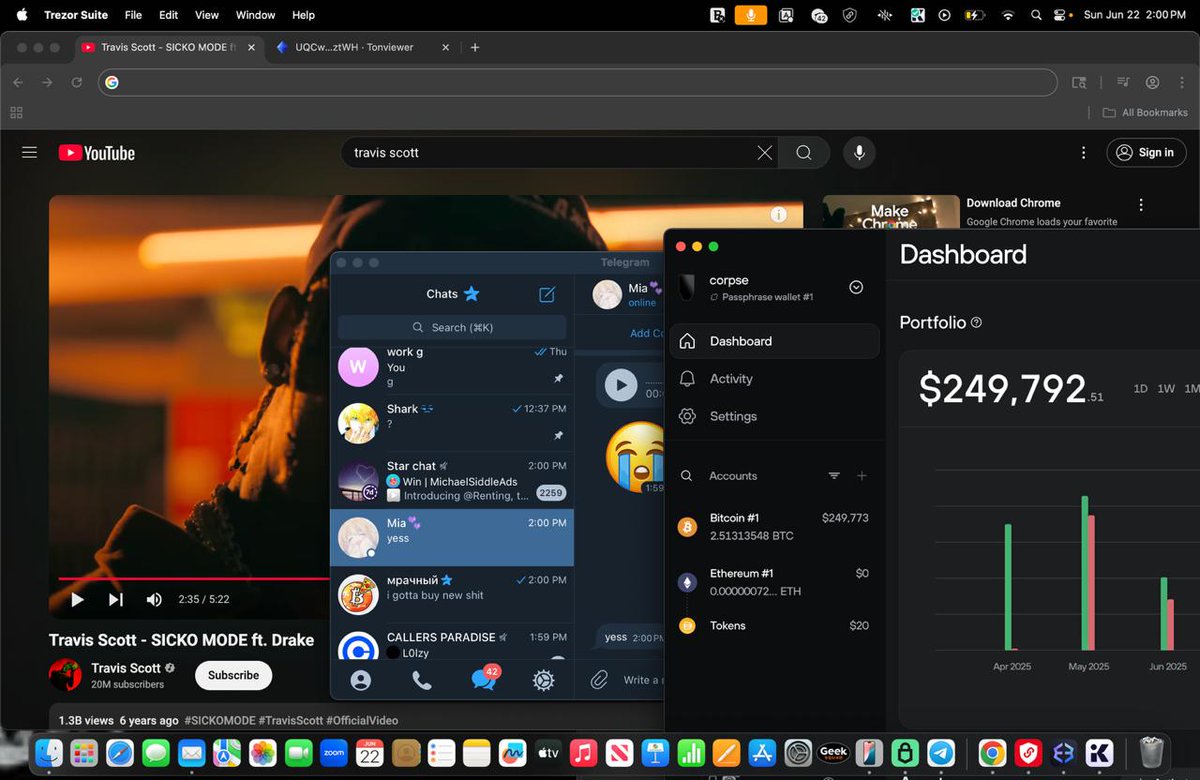
1/ Over the past few months I imagine you have seen many Coinbase users complain on X about their accounts suddenly being restricted.
This is the result of aggressive risk models and Coinbase’s failure to stop its users losing $300M+ per year to social engineering scams.

This is the result of aggressive risk models and Coinbase’s failure to stop its users losing $300M+ per year to social engineering scams.


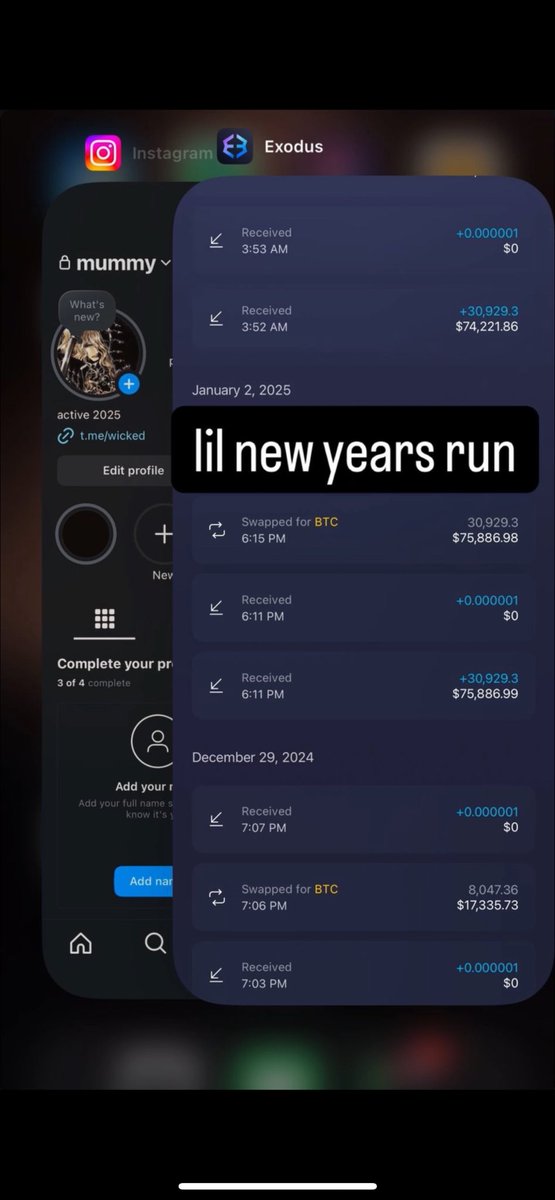
2/ Myself and @tanuki42_ spent time reviewing Coinbase withdrawals and gathering data from my DMs for high confidence thefts on various chains.
Below is a table we created which shows $65M stolen from Coinbase users in Dec 2024 - Jan 2025.
Our number is likely much lower than the actual amount stolen as our data was limited to my DMs and thefts we discovered on-chain which does not account for Coinbase support tickets and police reports we do not have access to.
Below is a table we created which shows $65M stolen from Coinbase users in Dec 2024 - Jan 2025.
Our number is likely much lower than the actual amount stolen as our data was limited to my DMs and thefts we discovered on-chain which does not account for Coinbase support tickets and police reports we do not have access to.

3/ Let’s walk through how these Coinbase social engineering scams work.
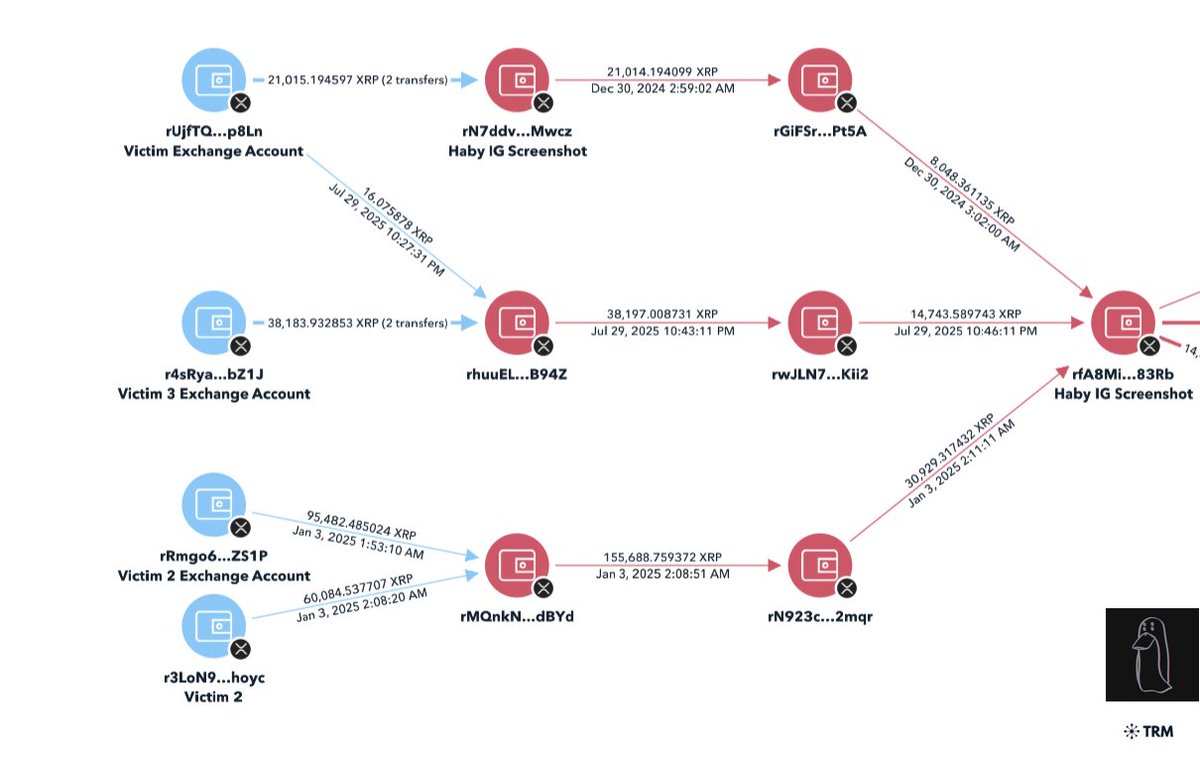
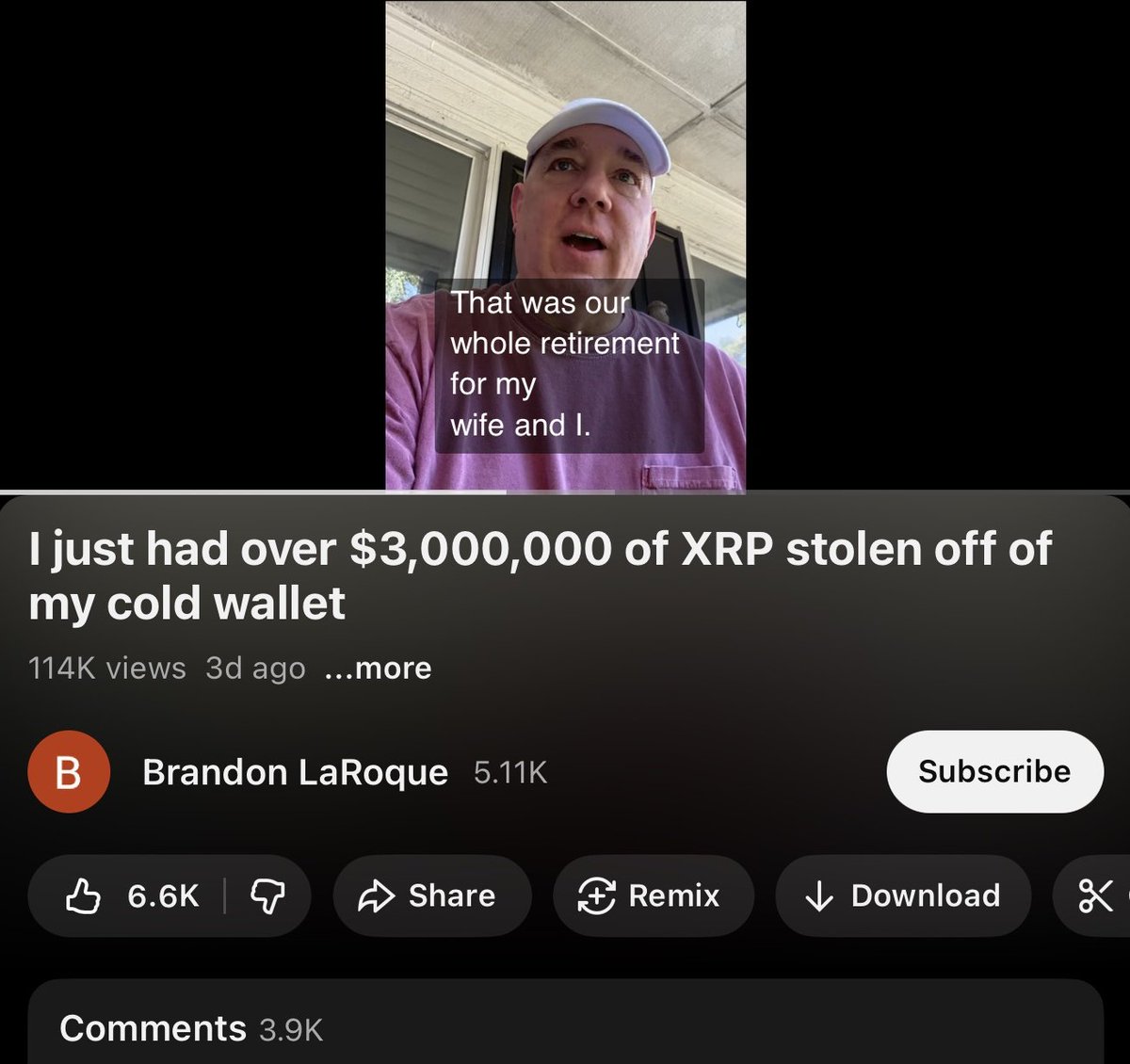
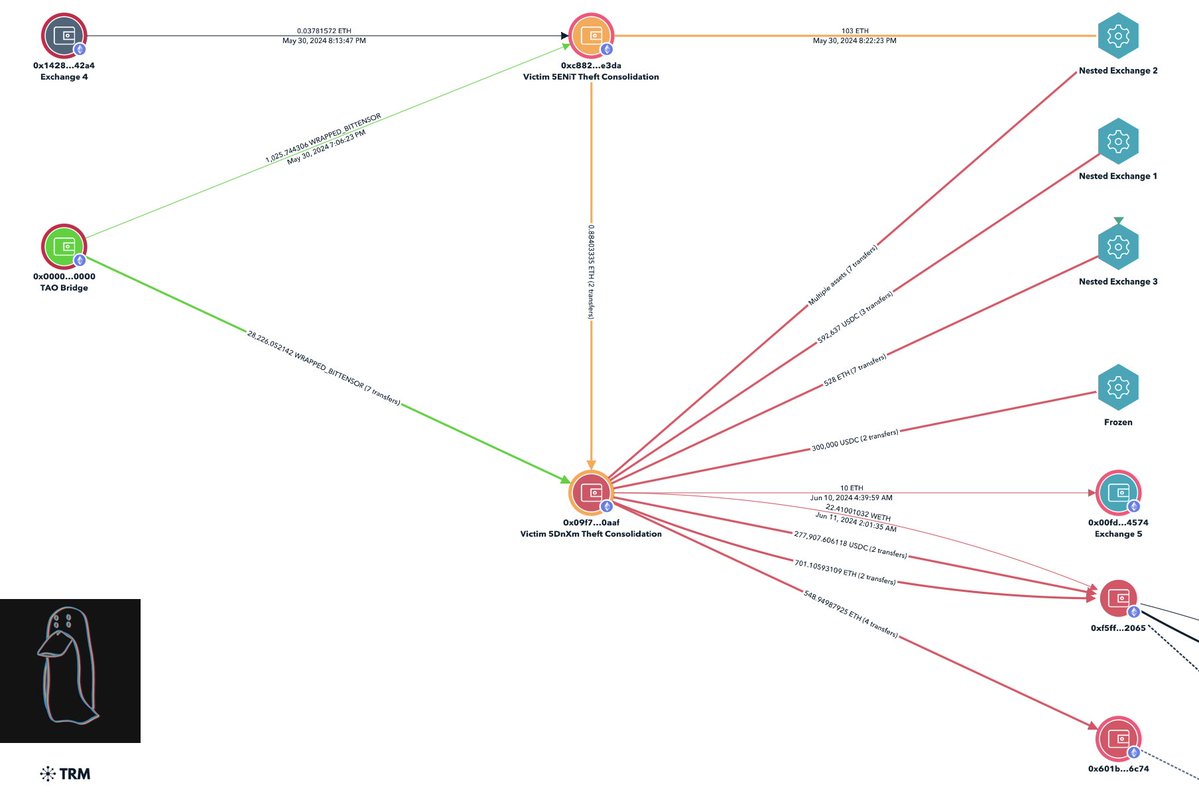
A victim reached out to me last month after losing ~$850K.
Graphing out this theft lead to a consolidation address with 25+ other victims tied to ‘coinbase-hold.eth’.
Theft address
0xc8234dda2bc3758eb90224d0025871001e8ee7b9
bc1q4ks5gus8uv88vk8yage4r89kv8uxlgwhemz545
A victim reached out to me last month after losing ~$850K.
Graphing out this theft lead to a consolidation address with 25+ other victims tied to ‘coinbase-hold.eth’.
Theft address
0xc8234dda2bc3758eb90224d0025871001e8ee7b9
bc1q4ks5gus8uv88vk8yage4r89kv8uxlgwhemz545

4/ The scammer called the victim from a spoofed phone number and used personal information obtained from private dbs to gain their trust.
After they told the victim their account had multiple unauthorized login attempts.
(Coinbase will NEVER call you)
After they told the victim their account had multiple unauthorized login attempts.
(Coinbase will NEVER call you)
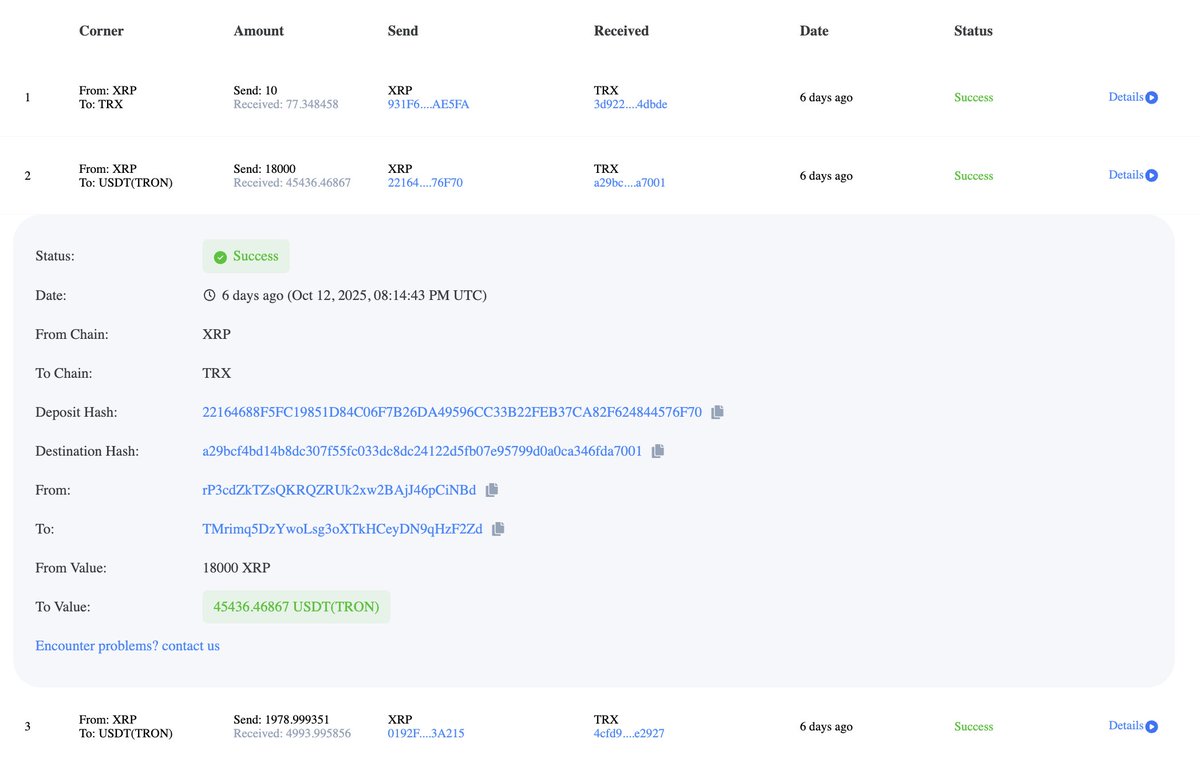
5/ They then sent a spoofed email which appeared to be from Coinbase with a fake Case ID further gaining trust.
They instructed the victim to transfer funds to a Coinbase Wallet and whitelist an address while “support” verified their accounts security.

They instructed the victim to transfer funds to a Coinbase Wallet and whitelist an address while “support” verified their accounts security.


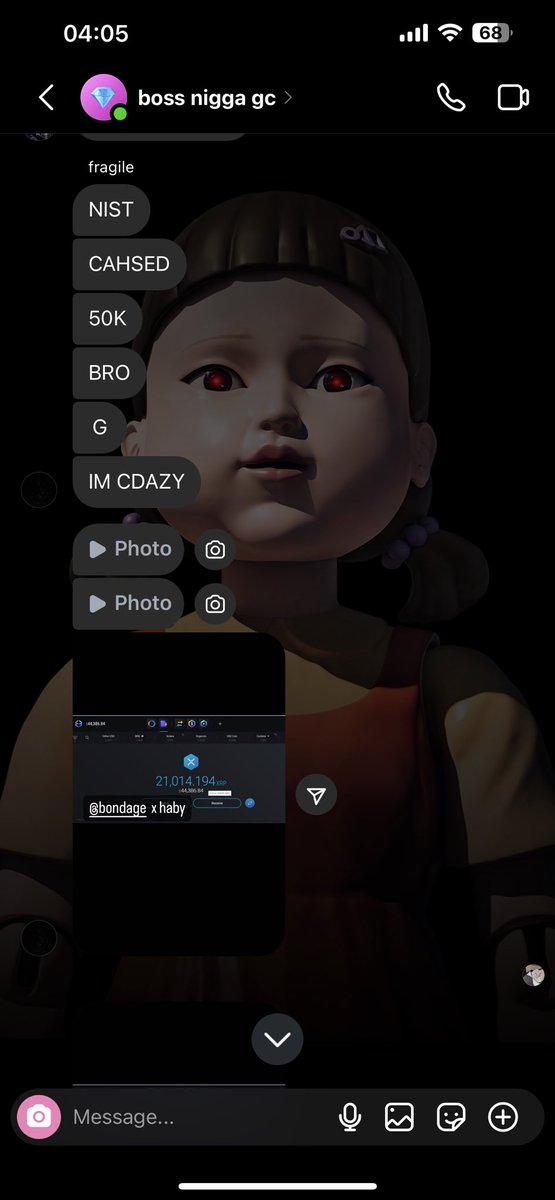
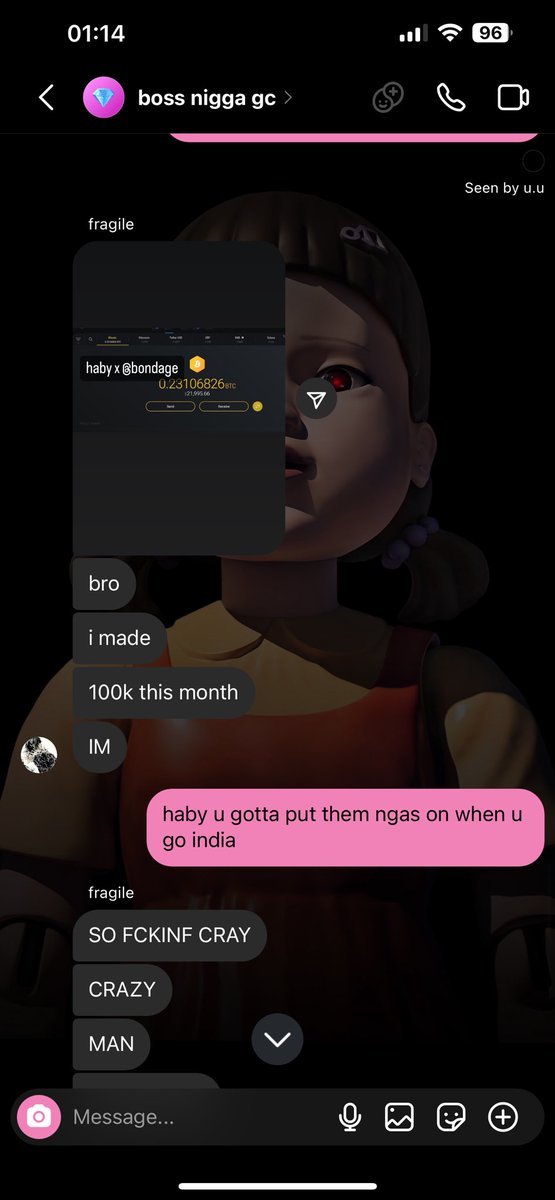
6/ Scammers clone the Coinbase site nearly 1:1 and allow the scammers to send different prompts to the target via spoofed emails using panels.
There are many Telegram channels where scammers advertise them.
See examples of various panels used by scammers below.


There are many Telegram channels where scammers advertise them.
See examples of various panels used by scammers below.


7/ Last year I posted multiple examples of Coinbase user thefts all for millions of dollars.
The two main groups conducting these scams are skids from the Com and threat actors located in India both primarily targeting US customers.



The two main groups conducting these scams are skids from the Com and threat actors located in India both primarily targeting US customers.




8/ The other month a Coinbase employee told people on X to stop using VPNs to avoid being flagged as suspicious meanwhile threat actors will explicitly block VPNs from phishing sites and not use them.
This shows Coinbase’s failure to diagnose the actual problem.


This shows Coinbase’s failure to diagnose the actual problem.



9/ Coinbase has quietly had related security incidents they did not publicly address:
a) For a number of users Coinbase with old API keys used for tax software which were hacked (was supposed to be read only perms)
b) Recent bugs like one which allowed you to send a verification code to any email even if the email did not have an account
c) $15.9M Coinbase Commerce theft last year
d) A threat actor was able to launder $38M from the BTCTurk hack via Coinbase over a few hours.



a) For a number of users Coinbase with old API keys used for tax software which were hacked (was supposed to be read only perms)
b) Recent bugs like one which allowed you to send a verification code to any email even if the email did not have an account
c) $15.9M Coinbase Commerce theft last year
d) A threat actor was able to launder $38M from the BTCTurk hack via Coinbase over a few hours.




10/ So where does the blame lie?
a) For the vast majority of the time these theft addresses are not being reported at all by Coinbase in popular compliance tools even after the thefts went on for weeks.
b) Multiple victims who have contacted me get stuck with useless customer support agents who never hear back.
c) Coinbase team can be incredibly hard to reach outside of US hours which is unacceptable when you operate in a 24/7 market as a large business.
The threats in this space are always evolving and you may only have minutes to react.
Competitors like Kraken, OKX, Binance do not have the same issue.
d) Many of the US based threat actors from the Com have bad opsec and Coinbase could easily choose to make an example out of them if they wanted.

a) For the vast majority of the time these theft addresses are not being reported at all by Coinbase in popular compliance tools even after the thefts went on for weeks.
b) Multiple victims who have contacted me get stuck with useless customer support agents who never hear back.
c) Coinbase team can be incredibly hard to reach outside of US hours which is unacceptable when you operate in a 24/7 market as a large business.
The threats in this space are always evolving and you may only have minutes to react.
Competitors like Kraken, OKX, Binance do not have the same issue.
d) Many of the US based threat actors from the Com have bad opsec and Coinbase could easily choose to make an example out of them if they wanted.


11/ I do not blame all Coinbase employees as most of the fault lies on leadership for these decisions.
While this post is critical of Coinbase what have they done well?
>providing good stablecoin on-ramp / off-ramp for retail
>attracting talent to build on Base
>recovery tool for users who deposit unsupported assets
>fighting the SEC
>Coinbase custody product
>allowing users to passively earn yield on stables easily
(Also there’s only so much you can do to educate people about threats such as email/call spoofing)
While this post is critical of Coinbase what have they done well?
>providing good stablecoin on-ramp / off-ramp for retail
>attracting talent to build on Base
>recovery tool for users who deposit unsupported assets
>fighting the SEC
>Coinbase custody product
>allowing users to passively earn yield on stables easily
(Also there’s only so much you can do to educate people about threats such as email/call spoofing)
12/ I strongly urge the Coinbase leadership team to consider:
a) Making phone numbers optional for advanced users with Authenticator app or Security key added who are fully KYC verified.
b) Add a beginner / elderly user account type that doesn’t allow withdrawals.
c) Improve community outreach (blog posts for recovering user funds, 24/7 IR, flag theft addresses, block phishing domains, etc)
d) Look into taking legal action against TLOxp / TransUnion for negligence on behalf of users as it’s the primary tool used by cybercriminals to harm users.
e) Initiate legal action against multiple US based threat actors running these scams to make an example out of them.
a ,b, & c are bare minimum for a top exchange.
d & e would be going above and beyond for its users.
a) Making phone numbers optional for advanced users with Authenticator app or Security key added who are fully KYC verified.
b) Add a beginner / elderly user account type that doesn’t allow withdrawals.
c) Improve community outreach (blog posts for recovering user funds, 24/7 IR, flag theft addresses, block phishing domains, etc)
d) Look into taking legal action against TLOxp / TransUnion for negligence on behalf of users as it’s the primary tool used by cybercriminals to harm users.
e) Initiate legal action against multiple US based threat actors running these scams to make an example out of them.
a ,b, & c are bare minimum for a top exchange.
d & e would be going above and beyond for its users.
13/ Coinbase needs to urgently make changes as more and more users are being scammed for tens of millions every month.
Other major exchanges do not have similar panels created by scammers for fraud.
While the victims are partially responsible it’s unreasonable to expect elderly victims to understand the nuances of email/phone spoofing.
Coinbase is in a position where they have the power to make these changes and set a good example but they have chosen to do little to nothing .
Other major exchanges do not have similar panels created by scammers for fraud.
While the victims are partially responsible it’s unreasonable to expect elderly victims to understand the nuances of email/phone spoofing.
Coinbase is in a position where they have the power to make these changes and set a good example but they have chosen to do little to nothing .

• • •
Missing some Tweet in this thread? You can try to
force a refresh