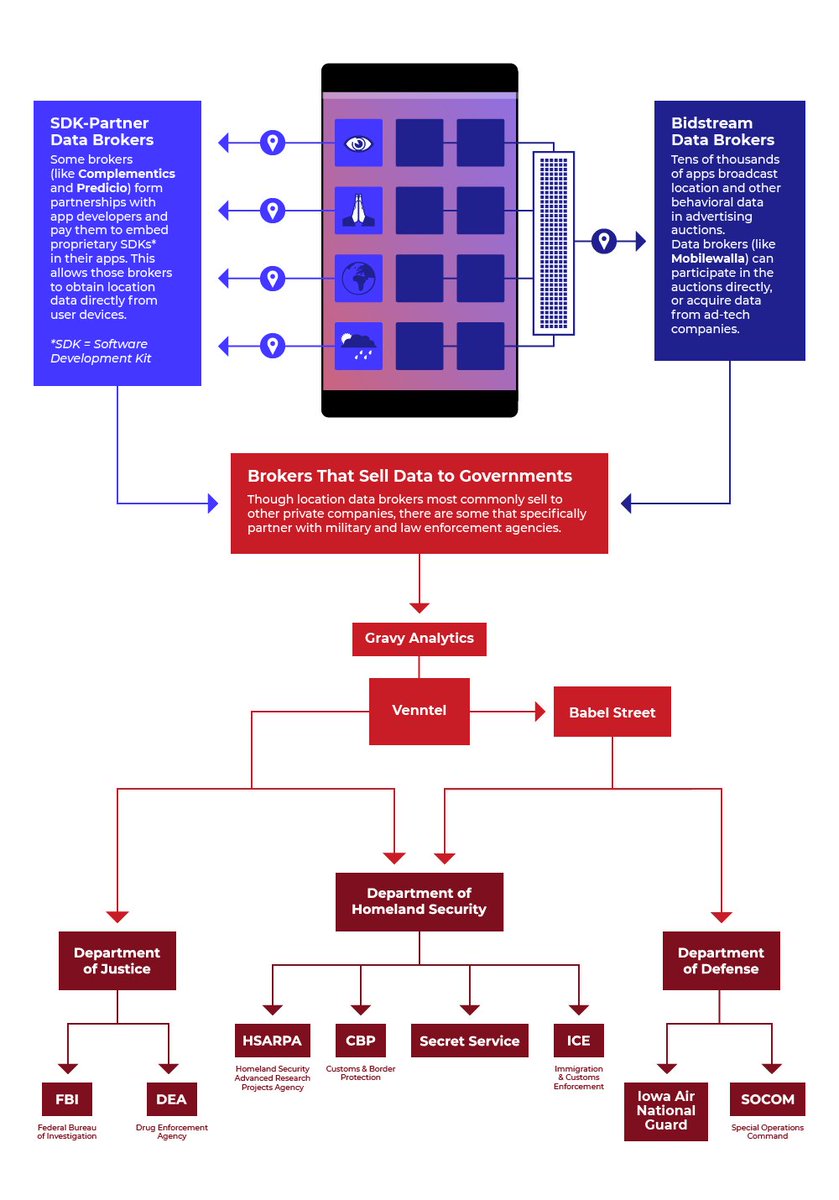
Hackers are using Google Tag Manager (GTM) to inject credit card skimmers into E-commerce sites.
At least 6 compromised sites identified so far. Here's what we're seeing. 👇
At least 6 compromised sites identified so far. Here's what we're seeing. 👇
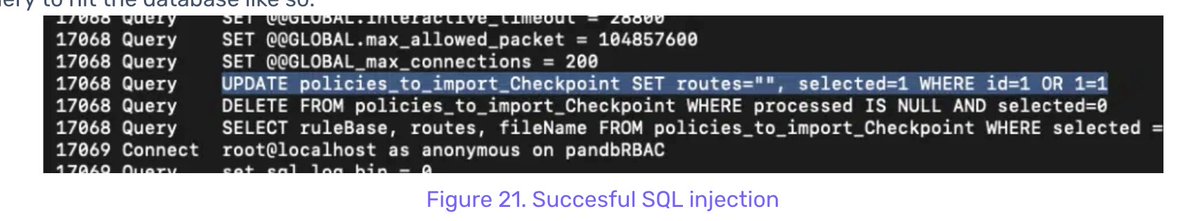
Malicious GTM script reference (GTM-MLHK2N68) stored in Magento's cms_block.content table.
Attackers using GTM as delivery mechanism to bypass security controls.
Attackers using GTM as delivery mechanism to bypass security controls.

Obfuscated JS skimmer activates on checkout pages, exfiltrating card data to C2 domain eurowebmonitortool[.]com.
Additional persistence achieved via PHP backdoor in media/index.php allowing remote code execution through base64-encoded commands.
Gives attackers ongoing access post-cleanup.
Additional persistence achieved via PHP backdoor in media/index.php allowing remote code execution through base64-encoded commands.
Gives attackers ongoing access post-cleanup.

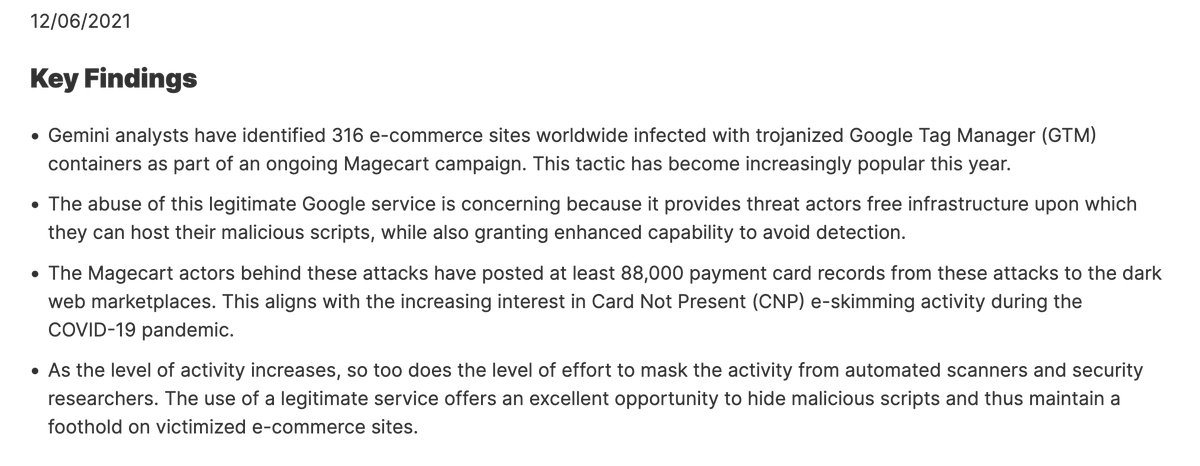
This campaign bears striking similarity to 2021 GTM-based Magecart operation that hit 316 sites and compromised 88,000 cards.
Same core TTPs being recycled.
Same core TTPs being recycled.

Why GTM works so well for attackers:
- Auto-executes JS
- Trusted Google infrastructure
- Security tools typically allow list
- Dynamic updates without site access
- Auto-executes JS
- Trusted Google infrastructure
- Security tools typically allow list
- Dynamic updates without site access
This is familiar territory for me, remembering my 2013 Million Browser Botnet talk @ Blackhat where me and @jeremiahg demonstrated JavaScript injection via ad networks.
Same concept, different delivery mechanism.
Same concept, different delivery mechanism.

@jeremiahg IOCs to watch for:
- Suspicious GTM container IDs
- Unexpected scripts in cms_block.content
- PHP files in media directory
- Unusual outbound connections during checkout flows
- Suspicious GTM container IDs
- Unexpected scripts in cms_block.content
- PHP files in media directory
- Unusual outbound connections during checkout flows
@jeremiahg Check my full writeup here ->
Subscribe and follow for more like this every week! <3vulnu.com/p/hackers-use-…
Subscribe and follow for more like this every week! <3vulnu.com/p/hackers-use-…
• • •
Missing some Tweet in this thread? You can try to
force a refresh