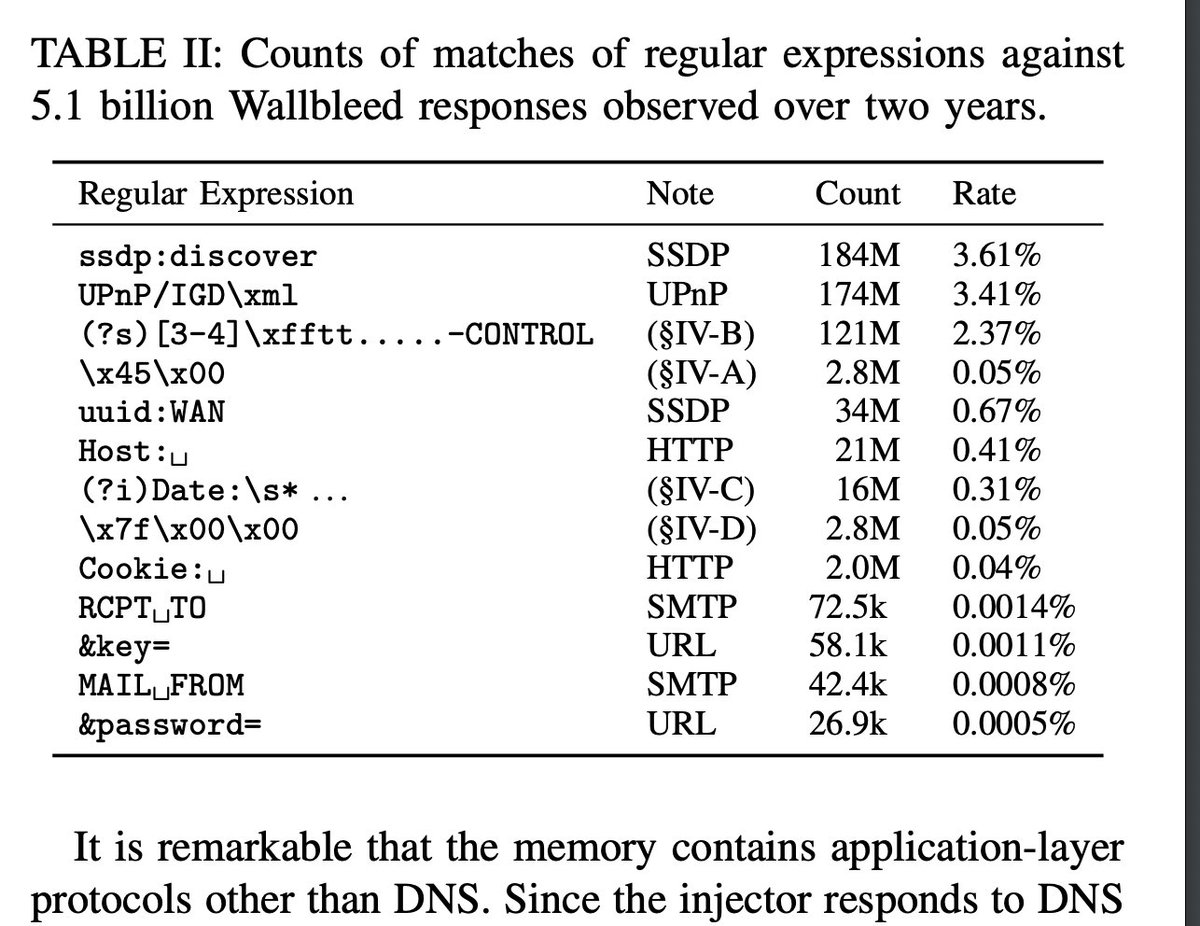
Chinese Great Firewall (website access blockade and. content filter for internet traffic) was leaking data! It's a fascinating discovery of security and privacy vulnerability in a large-scale technical censorship system. "Traffic with no relation to China could be leaked".

Chinese firewall leaked memory due to a buffer overrun. "DNS injection devices had a parsing bug that would, under certain conditions, cause them to include up to 125 bytes of their own memory in the forged DNS responses they sent" 
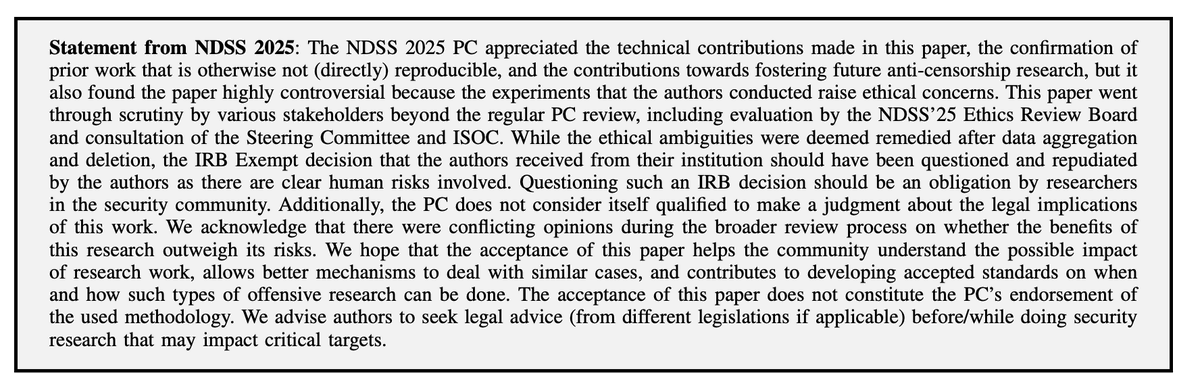
The conference chairs found that this research is ethically sensitive but decided that the benefits of publishing outweigh the risks. It's good that such research work is possible and is being accepted and presented, too! So the process works. gfw.report/publications/n…
• • •
Missing some Tweet in this thread? You can try to
force a refresh