Security & Privacy. Data Protection. Research. Engineering. Analyst. Policy. W3C. Consultant. Author.
Ph.D, LL.M. @warstudies
3 subscribers
How to get URL link on X (Twitter) App



 It's one of the best written security policies out there in recent years. It also has nice observations: "The effects of quantum technology and biotechnology for security policy are not yet sufficiently foreseeable."
It's one of the best written security policies out there in recent years. It also has nice observations: "The effects of quantum technology and biotechnology for security policy are not yet sufficiently foreseeable."

https://twitter.com/lukOlejnik/status/1961324187068334466



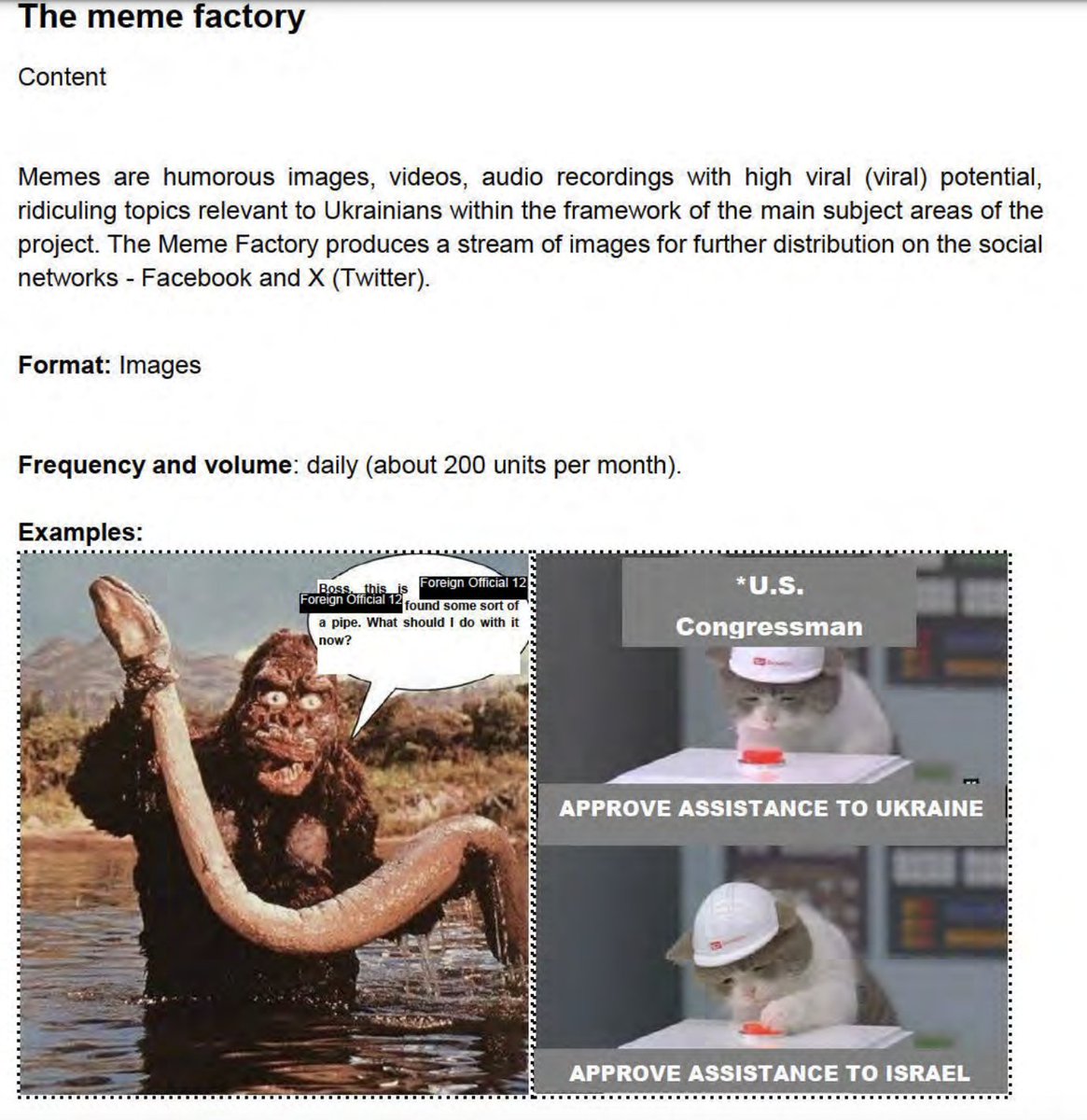
 AI allows unprecedented content manufacturing mechanisation. The mechanised persona agents may remember context, adapt tone, coordinate across platforms, and simulate consensus. LINK to FP piece: foreignpolicy.com/2025/09/18/ai-…
AI allows unprecedented content manufacturing mechanisation. The mechanised persona agents may remember context, adapt tone, coordinate across platforms, and simulate consensus. LINK to FP piece: foreignpolicy.com/2025/09/18/ai-…


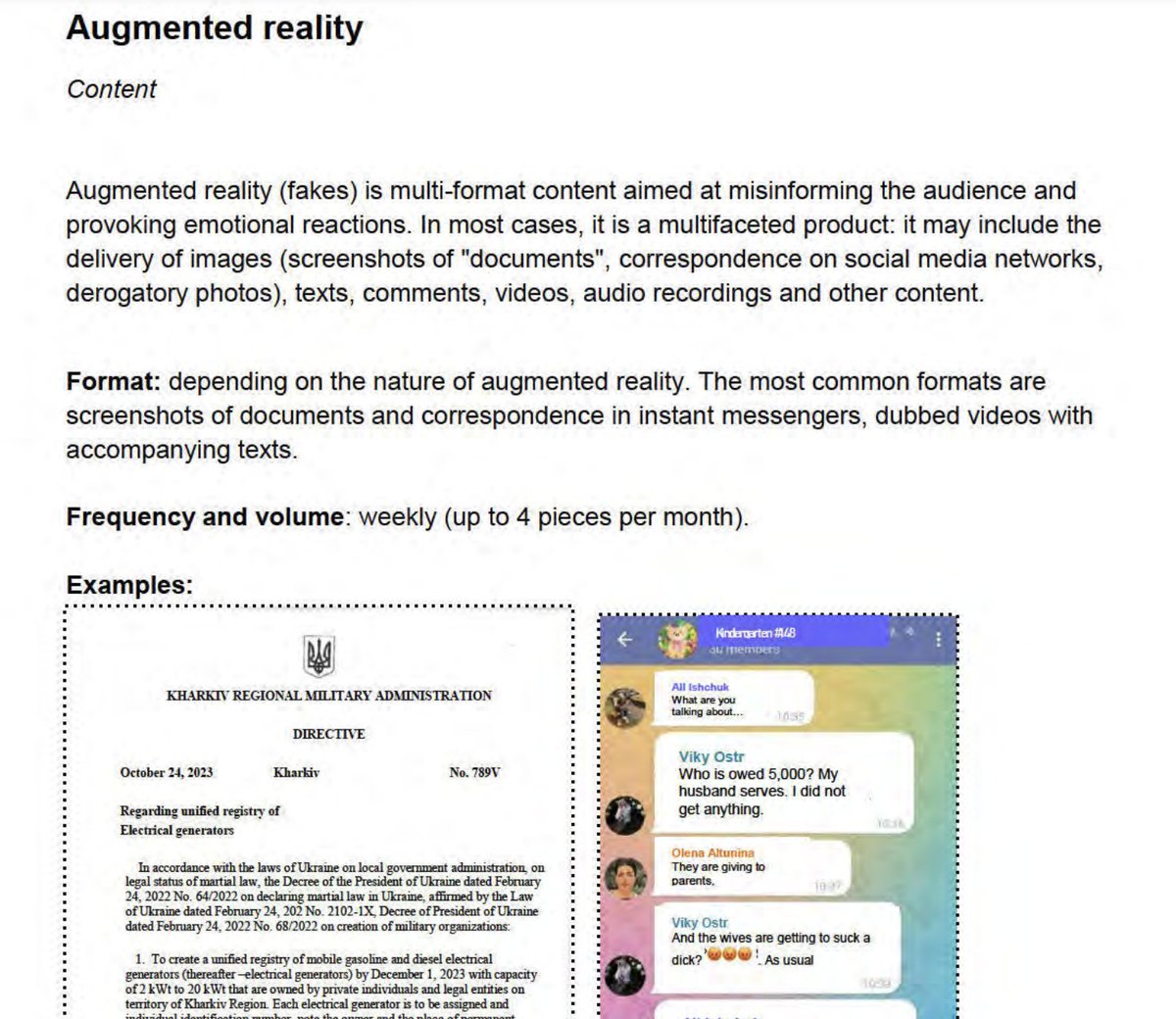
 Targeted ads also in use. And to remind you, all of this comes from U.S. Department of Justice. justice.gov/archives/opa/m…
Targeted ads also in use. And to remind you, all of this comes from U.S. Department of Justice. justice.gov/archives/opa/m…




 They put loads of effort into this design. Technically, it probably can’t be made much better. Cloud servers perform computations in a way that does not retain any user data after processing, enhancing security.
They put loads of effort into this design. Technically, it probably can’t be made much better. Cloud servers perform computations in a way that does not retain any user data after processing, enhancing security.

https://twitter.com/lukOlejnik/status/1473637010019598339It may then be evidently and completely "legal" to self-defend, including by sending a tank division for an invasion, possibly with airborne support, why not.




 "Values" not only guide the building of technologies in aspects such as privacy or cybersecurity, accessibility, freedom of expression, or censorship. There are past examples of political-technology clashes/interventions, too. On-demand decryption or OS changes are examples.
"Values" not only guide the building of technologies in aspects such as privacy or cybersecurity, accessibility, freedom of expression, or censorship. There are past examples of political-technology clashes/interventions, too. On-demand decryption or OS changes are examples. 





 "Below approximately 80% state of charge, both wired and wireless charging side-channels observed in this experiment do not leak information. ... consistently classify traces with a battery state 90%". Privacy-preserving advice: have less than 80% battery charge? :-)
"Below approximately 80% state of charge, both wired and wireless charging side-channels observed in this experiment do not leak information. ... consistently classify traces with a battery state 90%". Privacy-preserving advice: have less than 80% battery charge? :-) 


https://twitter.com/lukOlejnik/status/1367159400193003527The testing environment ('Fledge') have a bit relaxed privacy properties. So let's hope the final solution is more tight with respect to privacy protection. It'q quite a complex proposal. github.com/WICG/turtledov… chromestatus.com/feature/573358…





https://twitter.com/lukOlejnik/status/1012262516200824833

 Third-party (chatbot provider) was breached. This spilled to Ticketmaster. Had this functionality not included on the payment site, this breach would not happen (this way, at least). Fun fact: ICO decided to enforce PCI-DSS requirements. #GDPR #ePrivacy
Third-party (chatbot provider) was breached. This spilled to Ticketmaster. Had this functionality not included on the payment site, this breach would not happen (this way, at least). Fun fact: ICO decided to enforce PCI-DSS requirements. #GDPR #ePrivacy 


 Sovereignty as a matter of rule applies to cyberspace. But it's extent is not clear. Some investigations may (or may not) be breaching sovereignty of other countries.
Sovereignty as a matter of rule applies to cyberspace. But it's extent is not clear. Some investigations may (or may not) be breaching sovereignty of other countries. 




 My analysis of @ICRC report selection. Cyberoperations. What impacts on exploit cost? Why supply chain attacks are a risk? Targeting health care (lethal cyberattacks; can you even detect?), ICS. Armed conflict context. How to move forward? #CyberICRC blog.lukaszolejnik.com/icrc-report-on…
My analysis of @ICRC report selection. Cyberoperations. What impacts on exploit cost? Why supply chain attacks are a risk? Targeting health care (lethal cyberattacks; can you even detect?), ICS. Armed conflict context. How to move forward? #CyberICRC blog.lukaszolejnik.com/icrc-report-on…

 English press release related to the first PL #GDPR fine. 6M user data scraped from public registers. Not informed data subjects about their rights. €220k fine. No tech component; purely lawful case. uodo.gov.pl/en/553/1009
English press release related to the first PL #GDPR fine. 6M user data scraped from public registers. Not informed data subjects about their rights. €220k fine. No tech component; purely lawful case. uodo.gov.pl/en/553/1009

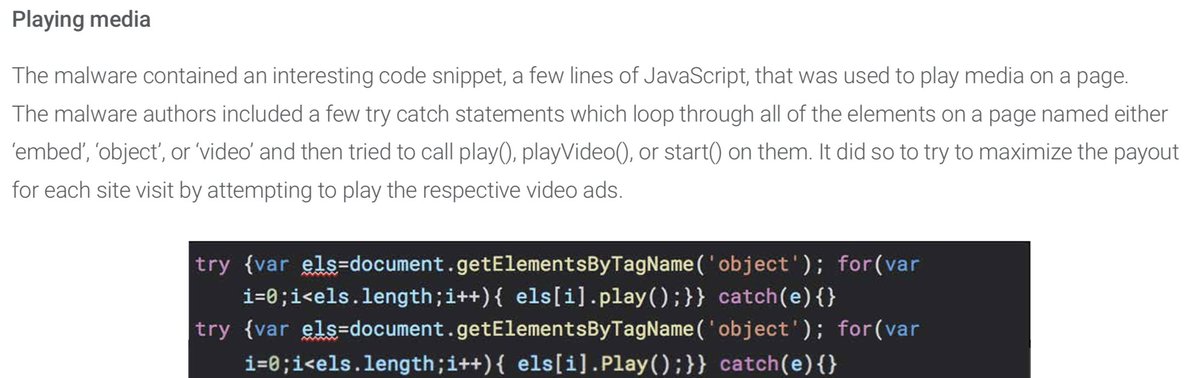 The scale of the operation is huge. Over 3 Billion bid request fraud, over 1 million of compromised machines. Border Gateway Protocol hijacking was even used. The biggest and most sophisticated operation like that ever.
The scale of the operation is huge. Over 3 Billion bid request fraud, over 1 million of compromised machines. Border Gateway Protocol hijacking was even used. The biggest and most sophisticated operation like that ever.