MSFT released new research on Silk Typhoon's supply chain attacks.
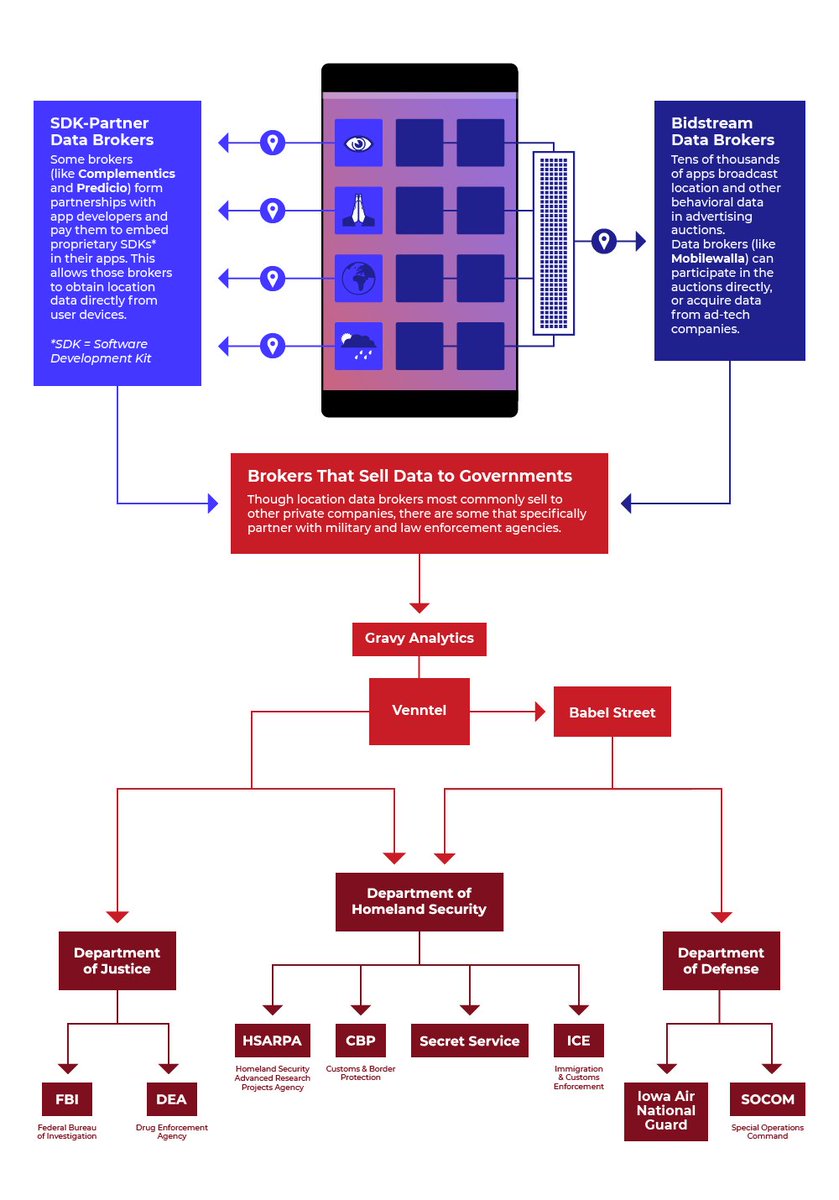
Key shift: Group now heavily leveraging stolen API keys and PAM credentials to hit downstream customers, particularly state/local gov and IT sector targets.
Here's what we know 🧵
Key shift: Group now heavily leveraging stolen API keys and PAM credentials to hit downstream customers, particularly state/local gov and IT sector targets.
Here's what we know 🧵
Initial access vectors include 0days, compromised third-party services, and password spraying.
Notable: Found several instances of corporate creds exposed via public GitHub repos being used in attacks. (They should be following @InsecureNature)
Notable: Found several instances of corporate creds exposed via public GitHub repos being used in attacks. (They should be following @InsecureNature)

@InsecureNature Post-compromise, actors use stolen API keys to access downstream customer environments.
Primary focus: Data collection related to China interests, US gov policy, and LE investigations.
Primary focus: Data collection related to China interests, US gov policy, and LE investigations.

@InsecureNature Persistence techniques include admin account resets via API keys, webshell deployment, and creation of additional user accounts.
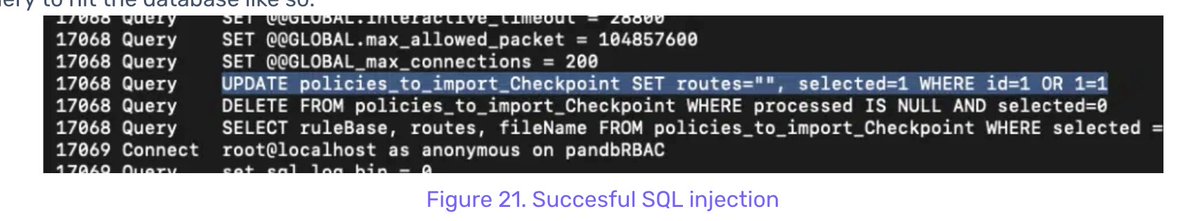
Actors methodically clear logs related to their activity.
Actors methodically clear logs related to their activity.

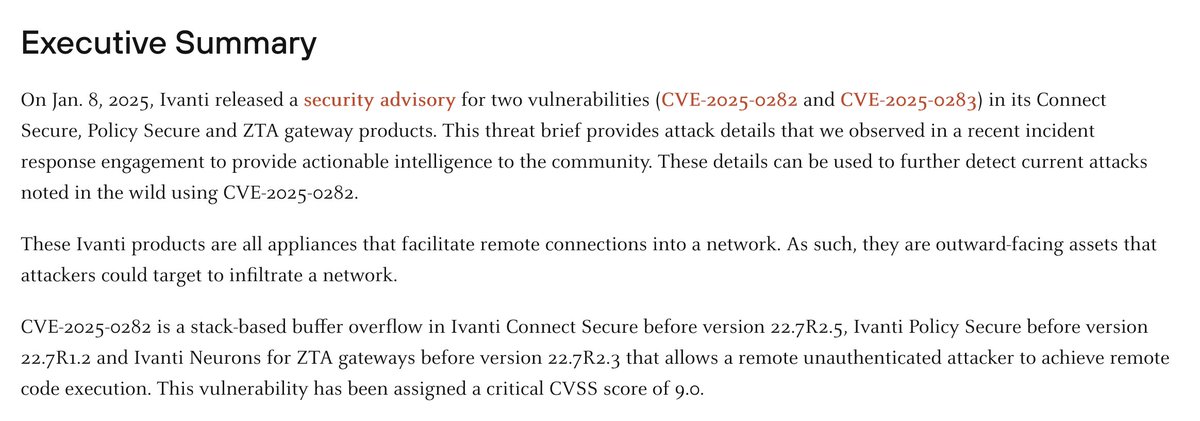
@InsecureNature Group recently exploited Ivanti Pulse Connect VPN 0day (CVE-2025-0282) in January.
Also abusing service principals and OAuth apps with admin perms for email/OneDrive/SharePoint exfil via MSGraph.
(screenshot from: ) unit42.paloaltonetworks.com/threat-brief-i…
Also abusing service principals and OAuth apps with admin perms for email/OneDrive/SharePoint exfil via MSGraph.
(screenshot from: ) unit42.paloaltonetworks.com/threat-brief-i…
@InsecureNature Interesting TTPs: Actors gaining access to existing OAuth-consented apps within tenant, adding their own passwords, then leveraging MSGraph API for email data theft.
Silk Typhoon has one of the largest targeting footprints among Chinese state actors, largely due to their ability to rapidly weaponize 0days.
Group was recently linked to December 2024 OFAC breach, where they leveraged stolen BeyondTrust API key to compromise Treasury dept systems.
Group was recently linked to December 2024 OFAC breach, where they leveraged stolen BeyondTrust API key to compromise Treasury dept systems.
• • •
Missing some Tweet in this thread? You can try to
force a refresh