🧵 THREAD: A federal whistleblower just dropped one of the most disturbing cybersecurity disclosures I’ve ever read.
He's saying DOGE came in, data went out, and Russians started attempting logins with new valid DOGE passwords
Media's coverage wasn't detailed enough so I dug into his testimony:
He's saying DOGE came in, data went out, and Russians started attempting logins with new valid DOGE passwords
Media's coverage wasn't detailed enough so I dug into his testimony:

Who’s the whistleblower?
Daniel Berulis — a senior DevSecOps architect at the National Labor Relations Board (NLRB), formerly with TS/SCI clearance.
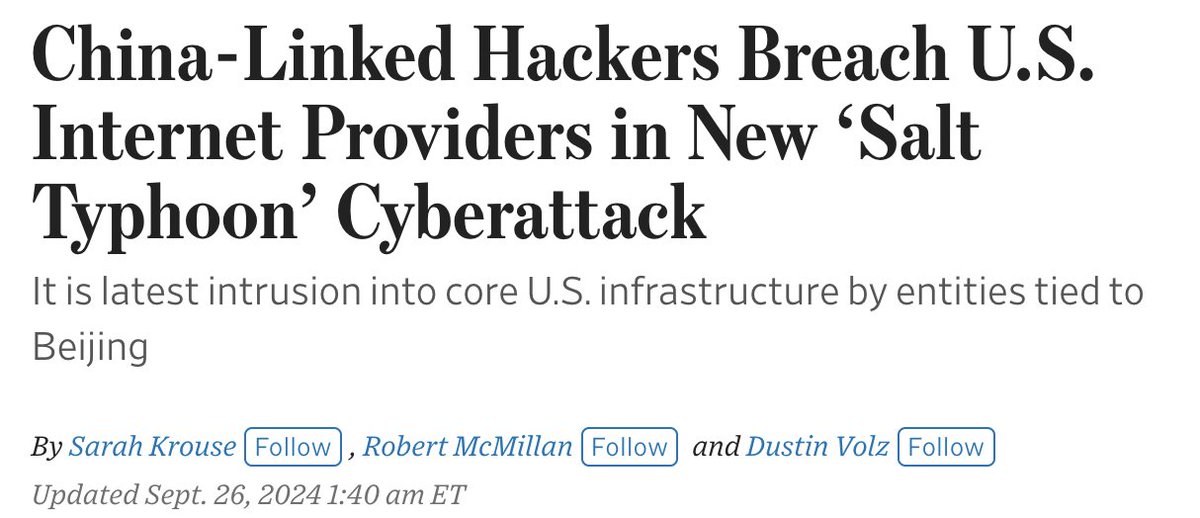
He just told Congress the Department of Government Efficiency (DOGE) pulled off a covert cyber op inside a federal agency.
Daniel Berulis — a senior DevSecOps architect at the National Labor Relations Board (NLRB), formerly with TS/SCI clearance.
He just told Congress the Department of Government Efficiency (DOGE) pulled off a covert cyber op inside a federal agency.
DOGE demanded root access.
Not auditor access. Not admin.
They were given “tenant owner” privileges in Azure — full control over the NLRB’s cloud, above the CIO himself.
This is never supposed to happen.
Not auditor access. Not admin.
They were given “tenant owner” privileges in Azure — full control over the NLRB’s cloud, above the CIO himself.
This is never supposed to happen.

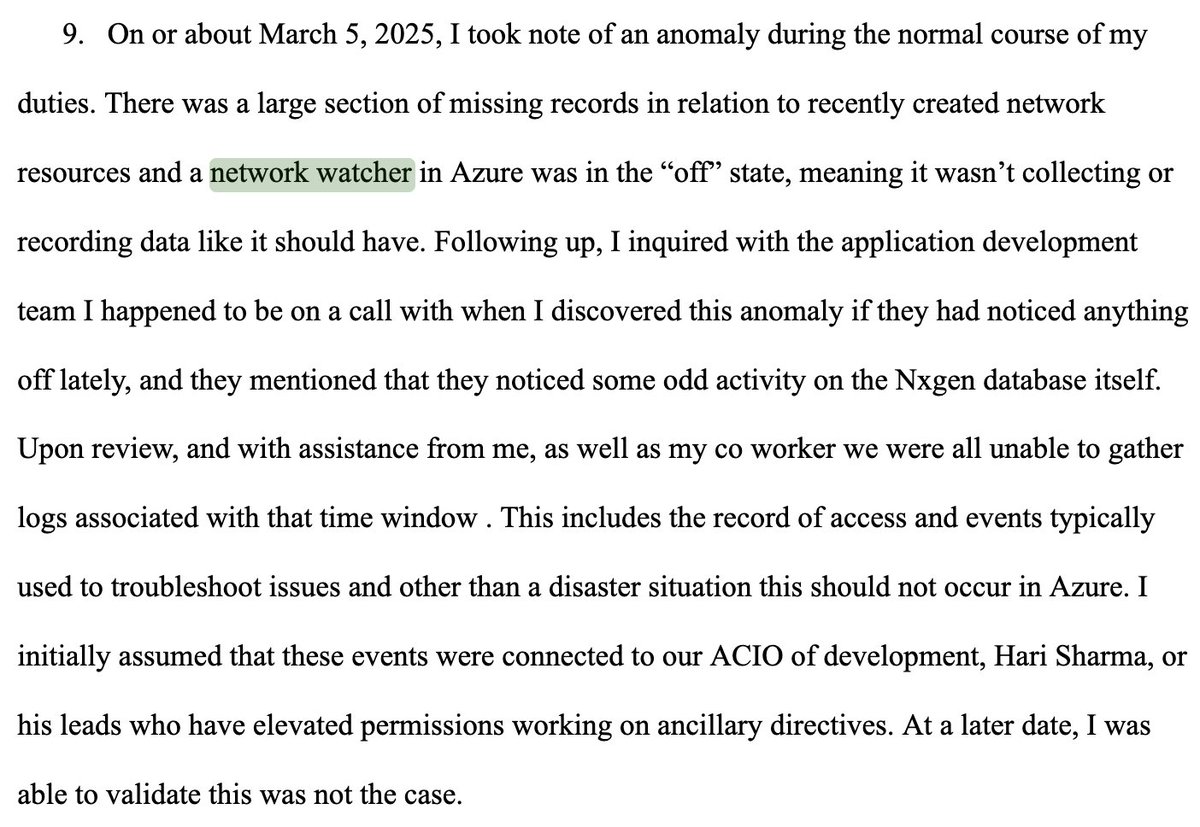
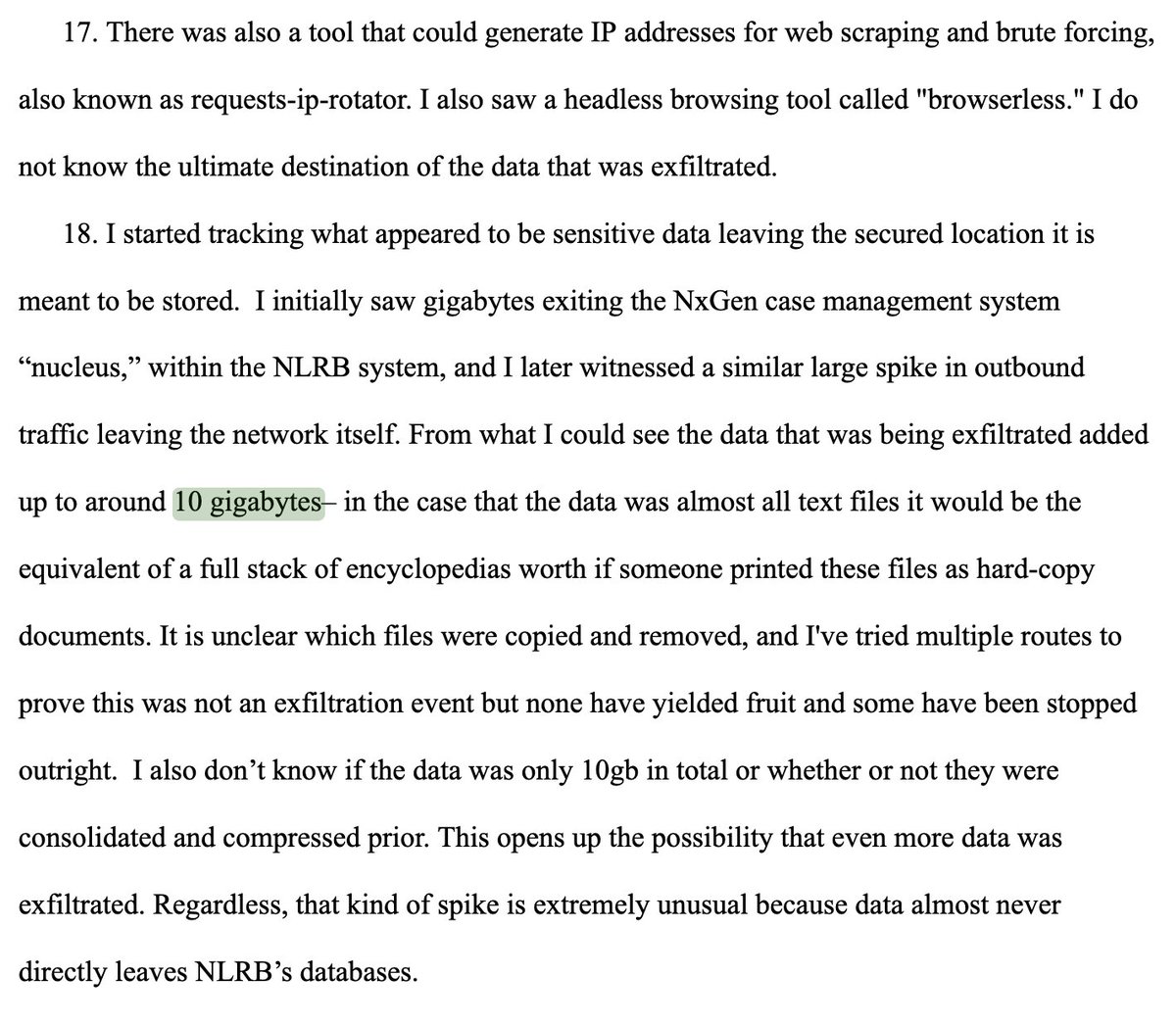
They disabled the logs.
Berulis says DOGE demanded account creation with no recordkeeping.
They even ordered security controls bypassed and disabled tools like network watcher so their actions wouldn’t be logged.
Berulis says DOGE demanded account creation with no recordkeeping.
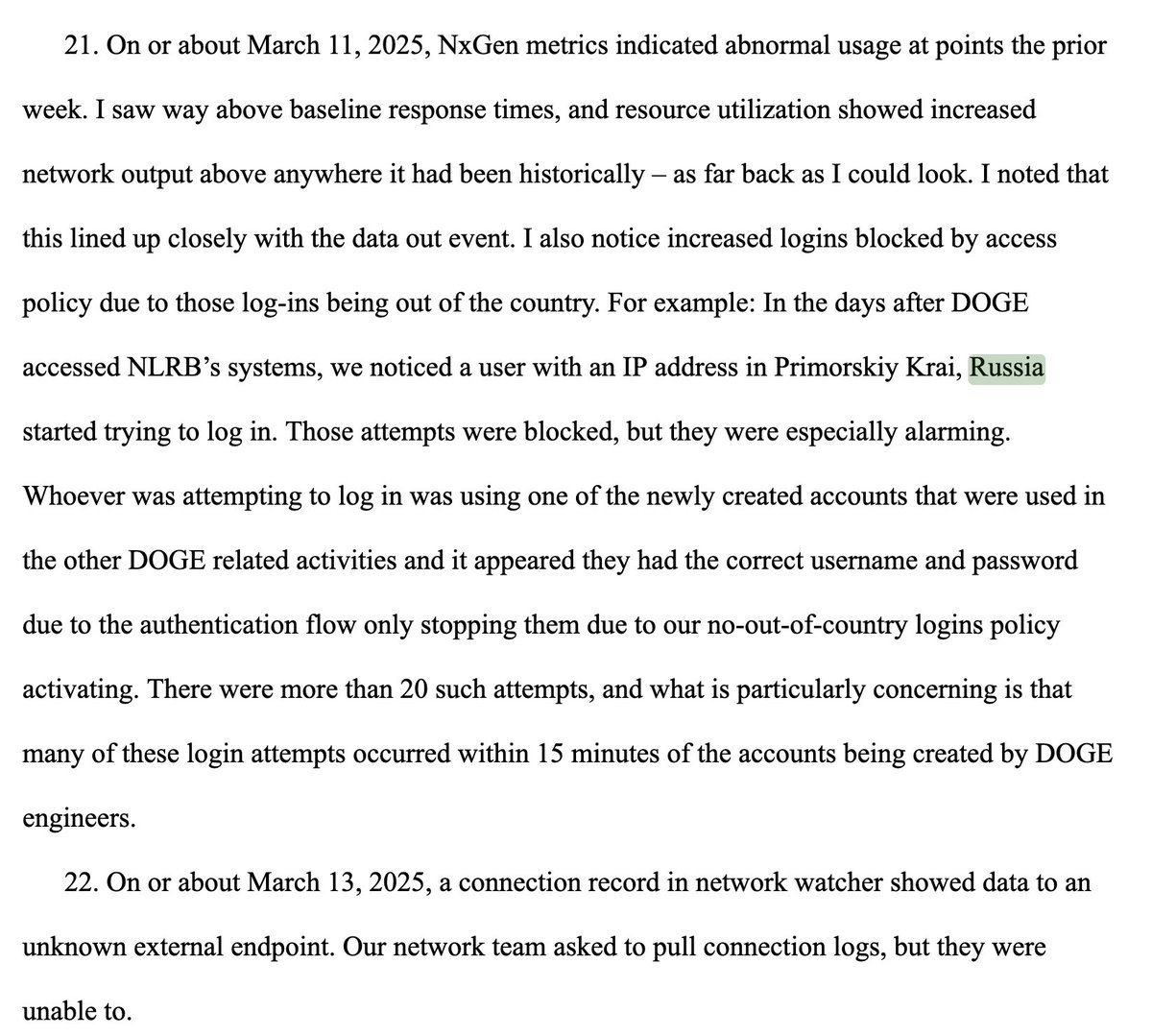
They even ordered security controls bypassed and disabled tools like network watcher so their actions wouldn’t be logged.
And then the data started flowing out.
10+ GB spike in outbound traffic
Exfiltration from NxGen, the NLRB's legal case database
No corresponding inbound traffic
Unusual ephemeral containers and expired storage tokens
10+ GB spike in outbound traffic
Exfiltration from NxGen, the NLRB's legal case database
No corresponding inbound traffic
Unusual ephemeral containers and expired storage tokens
They used an external library that used AWS IP pools to rotate IPs for scraping and brute force attacks.
They downloaded external GitHub tools like requests-ip-rotator and browserless — neither of which the agency uses.
They downloaded external GitHub tools like requests-ip-rotator and browserless — neither of which the agency uses.

The most daming claim in this statement IMO:
Within 15 minutes of DOGE accounts being created…
Attackers in Russia tried logging in using those new creds.
Correct usernames and passwords.
2 options here. The DOGE device was hacked. And I don't think I need to explain the 2nd.
Within 15 minutes of DOGE accounts being created…
Attackers in Russia tried logging in using those new creds.
Correct usernames and passwords.
2 options here. The DOGE device was hacked. And I don't think I need to explain the 2nd.
Multi-factor authentication? Disabled.
Someone downgraded Azure conditional access rules — MFA was off for mobile.
This was not approved and not logged.
Someone downgraded Azure conditional access rules — MFA was off for mobile.
This was not approved and not logged.

Cost spikes without new resources.
Azure billing jumped 8% — likely from short-lived high-cost compute used for data extraction, then deleted.
Azure billing jumped 8% — likely from short-lived high-cost compute used for data extraction, then deleted.

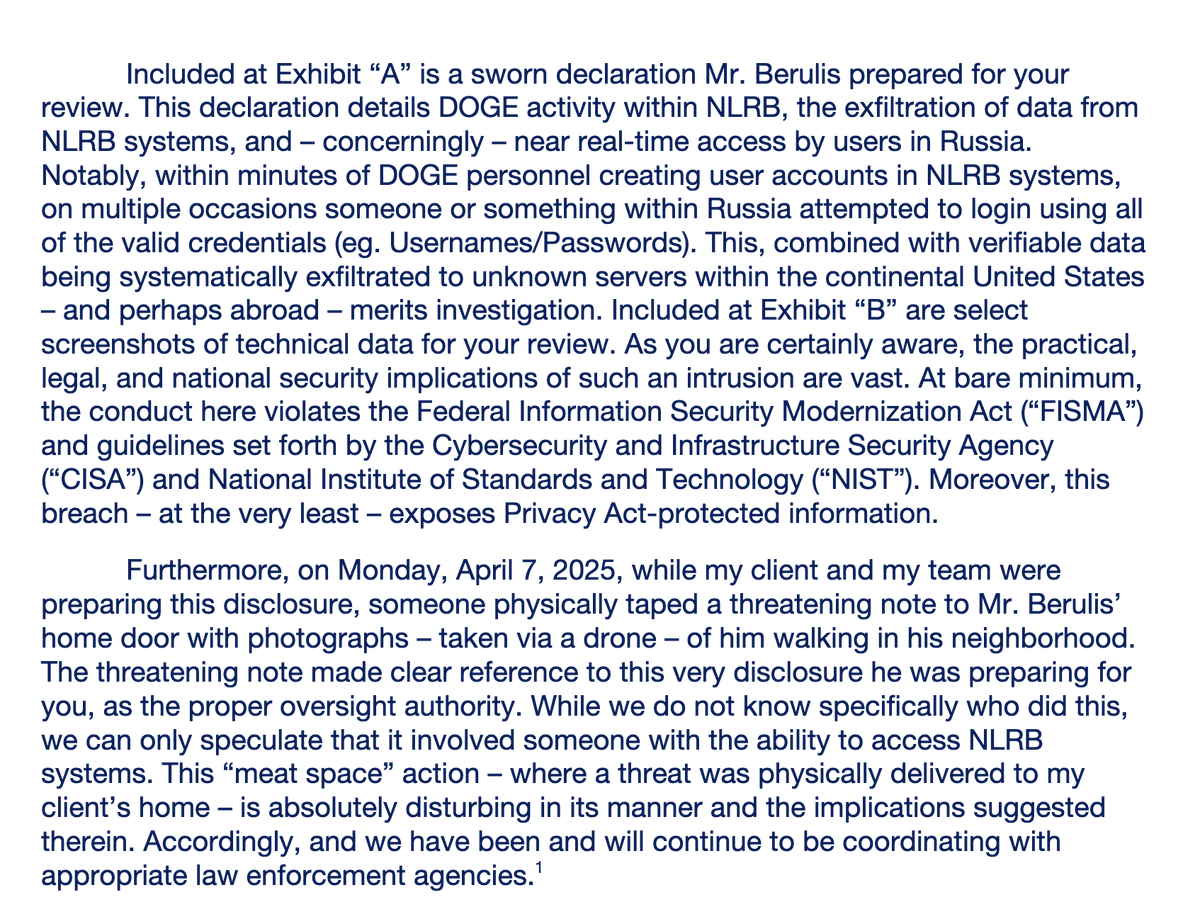
Then came the intimidation.
While preparing this disclosure, Berulis found a drone surveillance photo of himself taped to his front door with a threatening note.
This was just a few days ago.
While preparing this disclosure, Berulis found a drone surveillance photo of himself taped to his front door with a threatening note.
This was just a few days ago.

US-CERT was about to be called in.
CISA’s cyber response team.
But senior officials told them to stand down — no report, no investigation.
CISA’s cyber response team.
But senior officials told them to stand down — no report, no investigation.

• • •
Missing some Tweet in this thread? You can try to
force a refresh