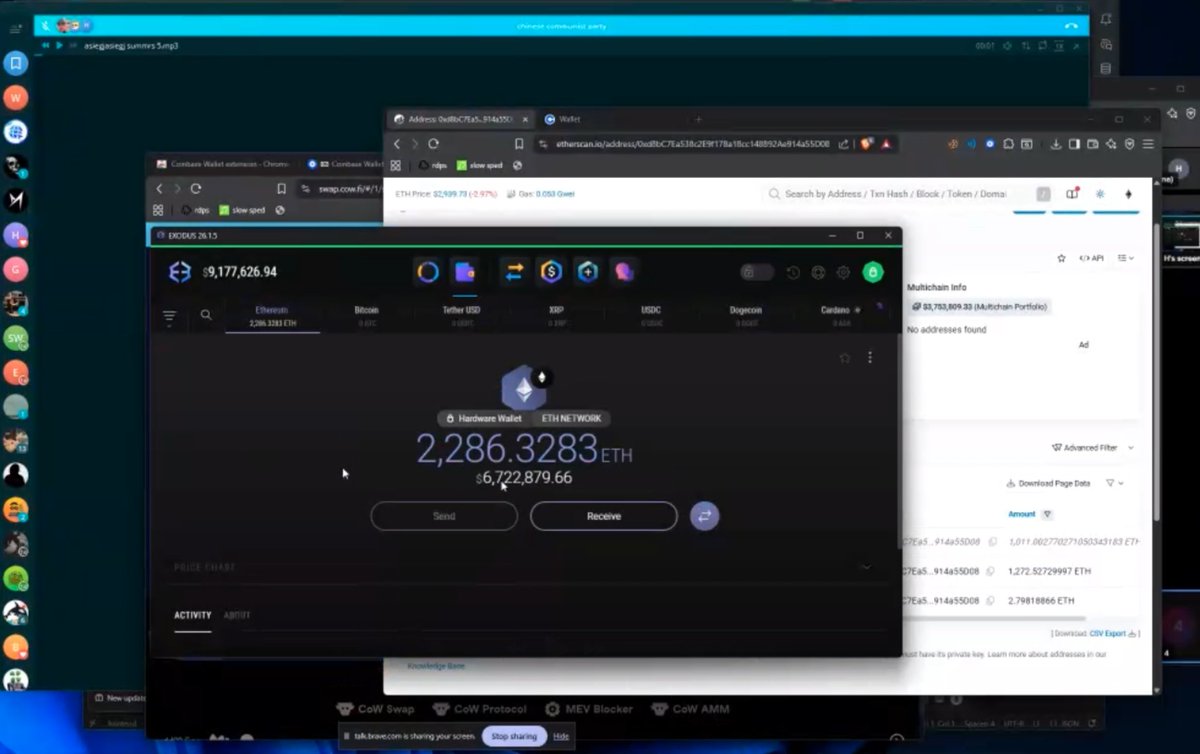
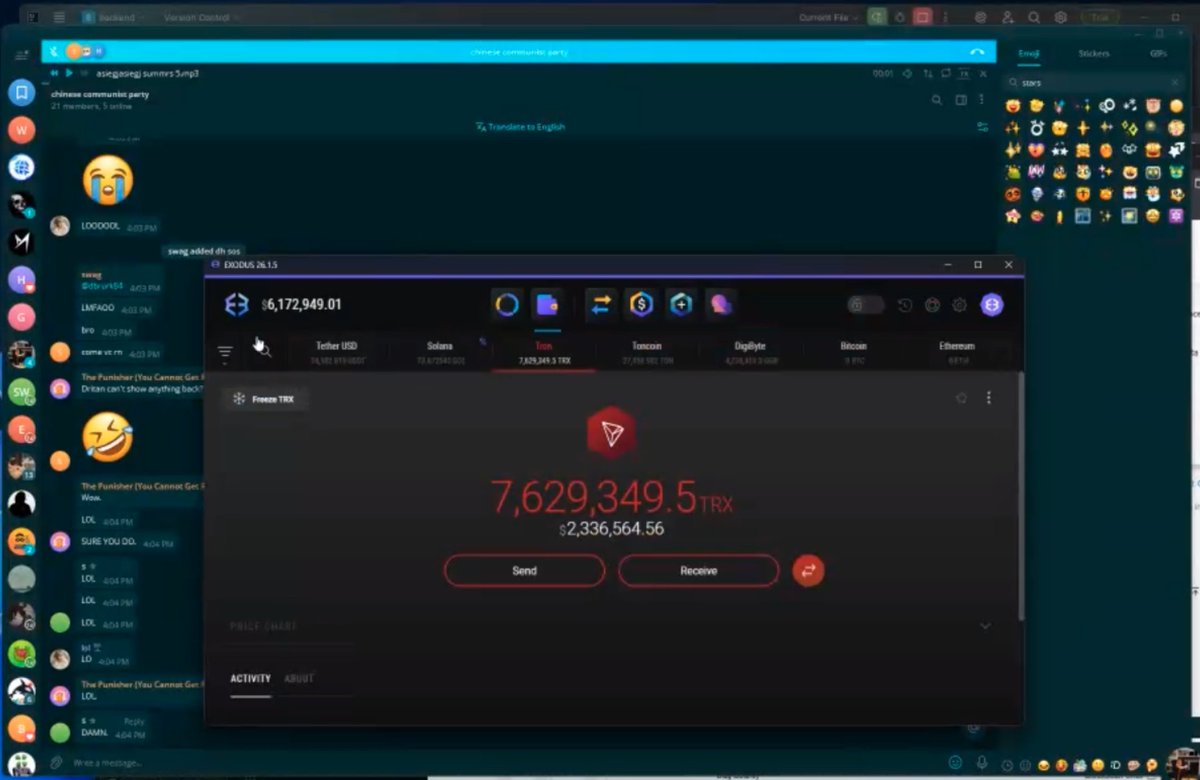
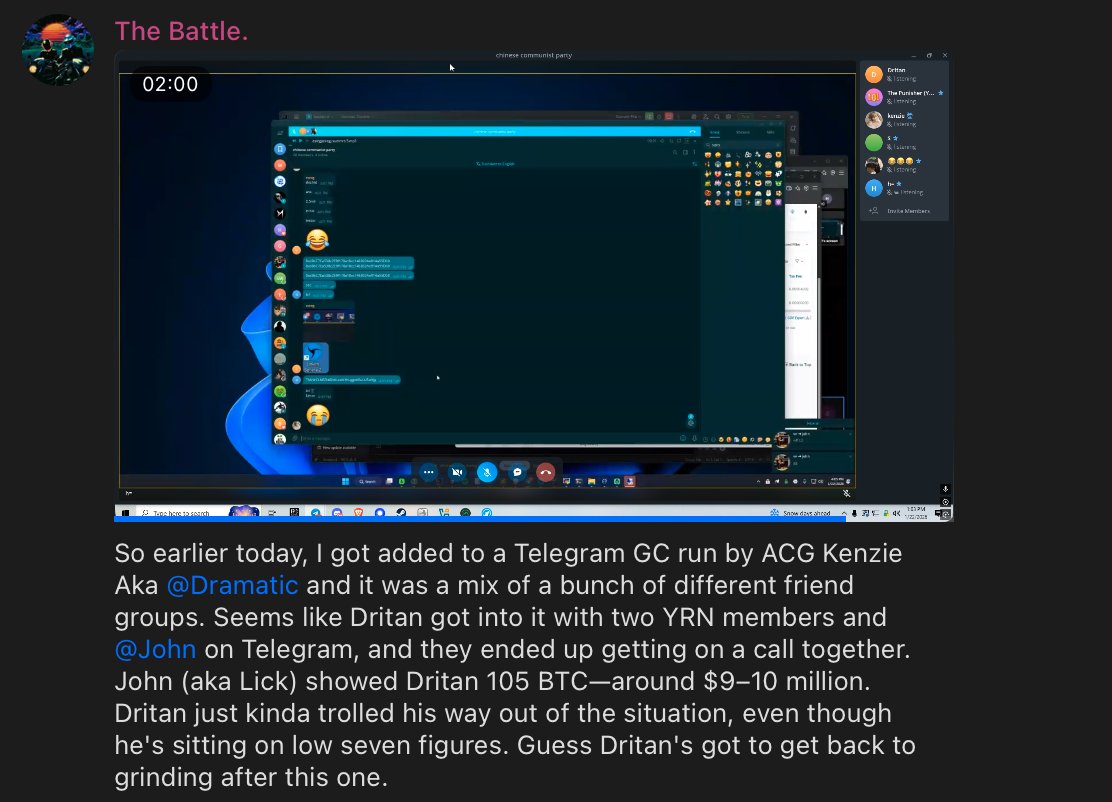
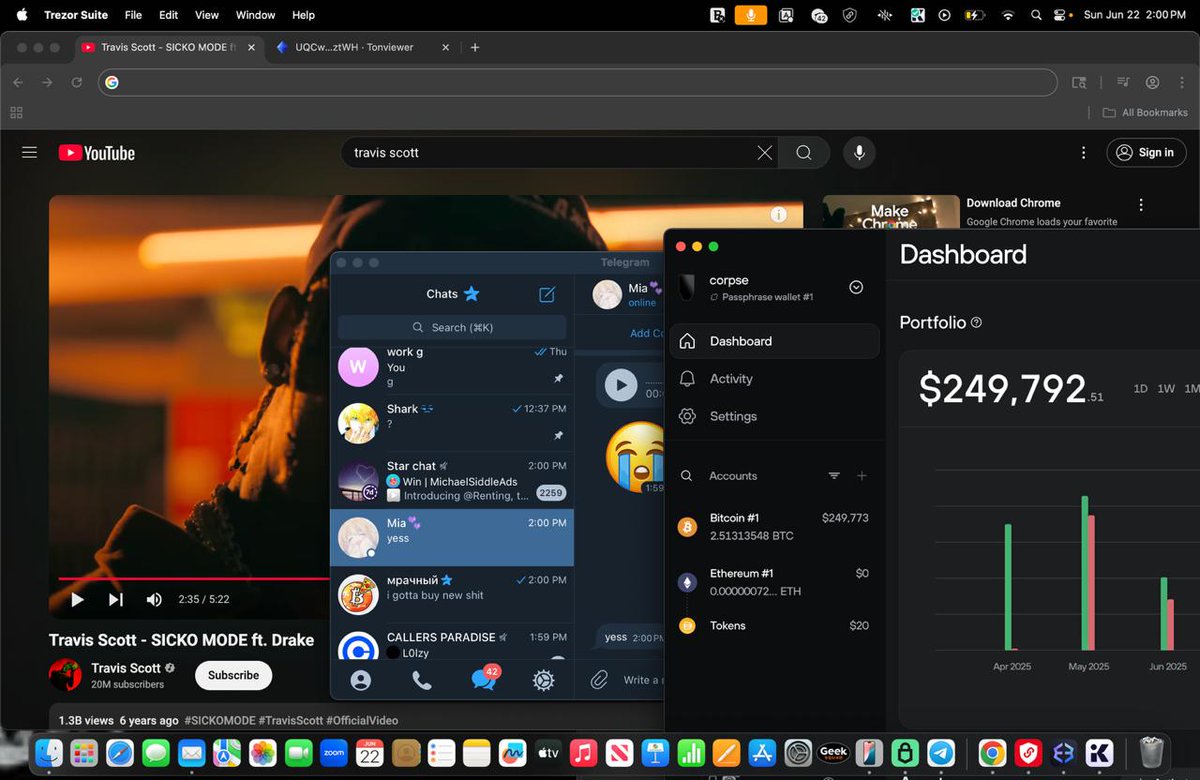
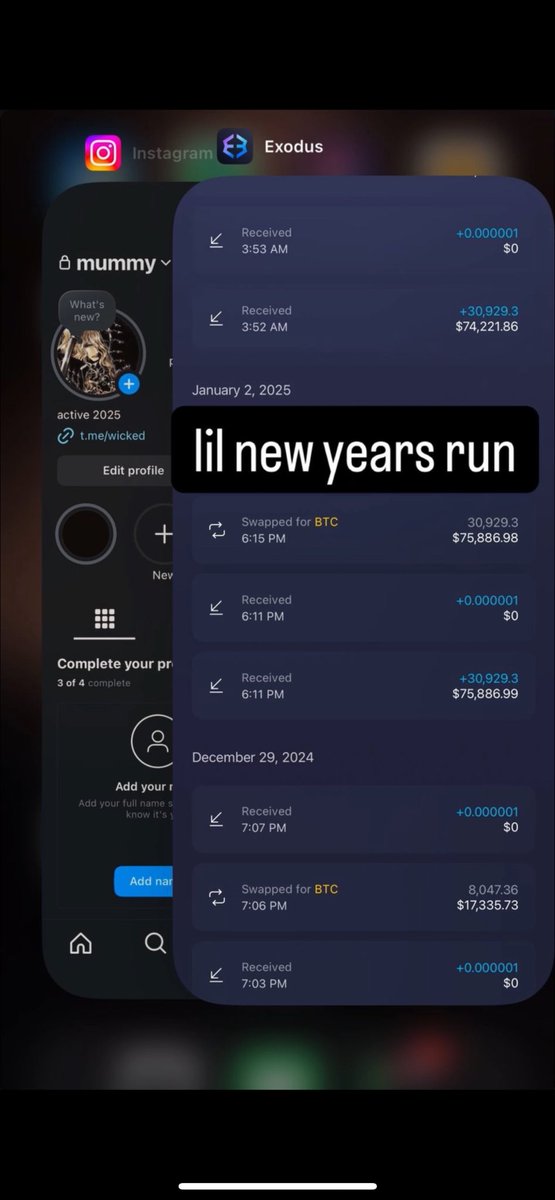
1/ My recent investigation uncovered more than $16.58M in payments since January 1, 2025 or $2.76M per month has been sent to North Korean IT workers hired as developers at various projects & companies.
To put this in perspective payments range from $3K-8K per month meaning they have infiltrated 345 jobs on the low end or 920 jobs on the high end.

To put this in perspective payments range from $3K-8K per month meaning they have infiltrated 345 jobs on the low end or 920 jobs on the high end.


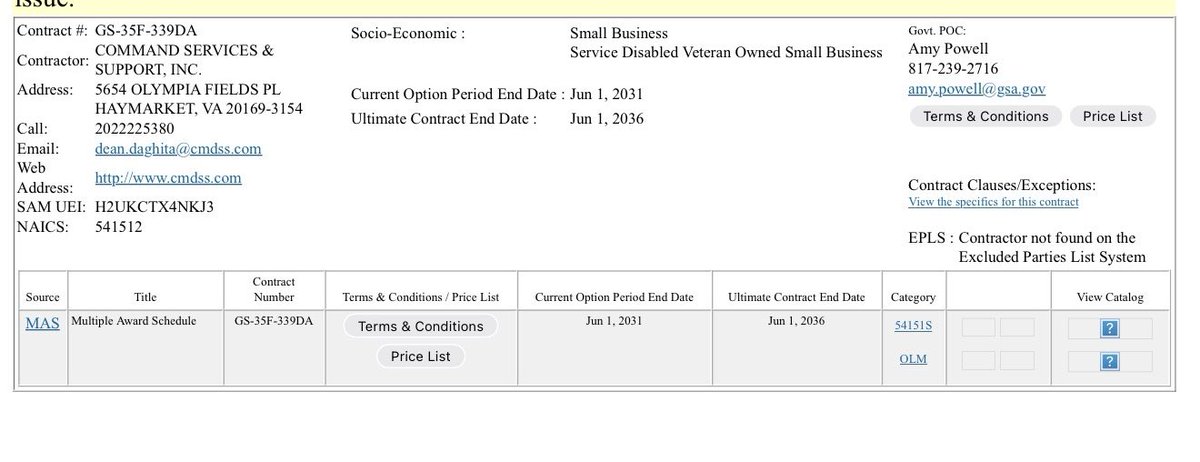
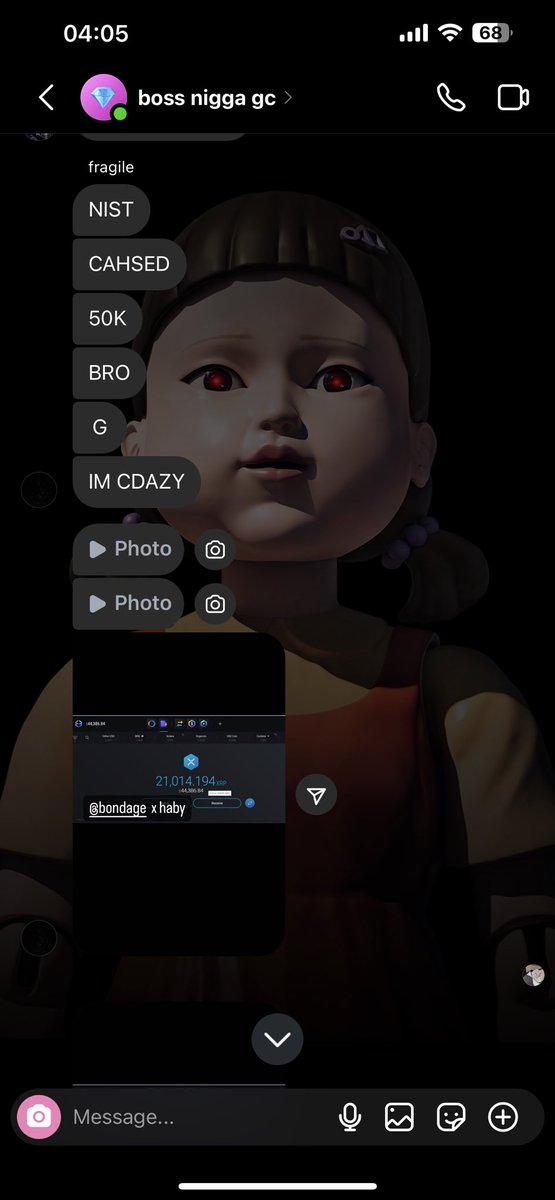
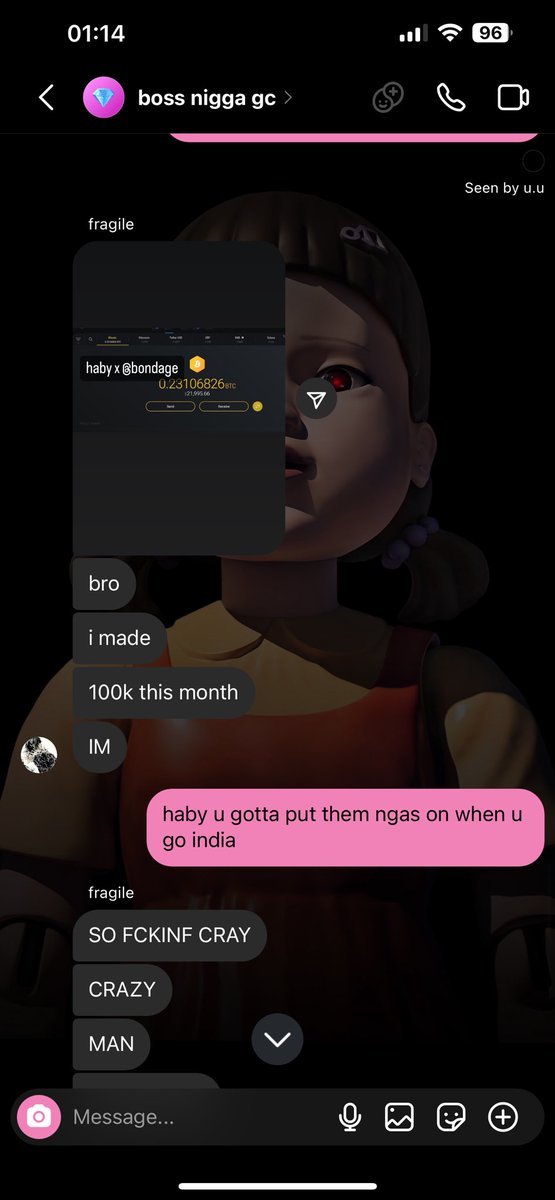
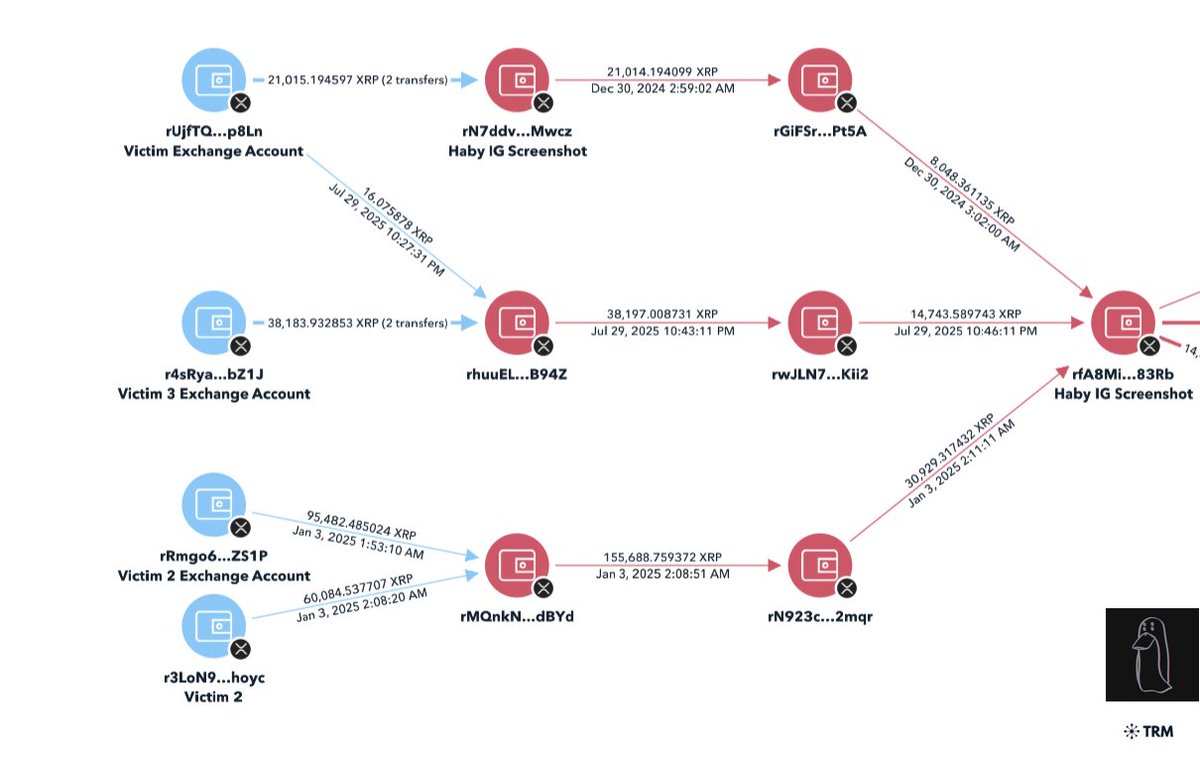
2/ Here’s a look into one of the six clusters I have been monitoring and was able to attribute 8 different DPRK ITWs that obtained roles at 12+ projects.
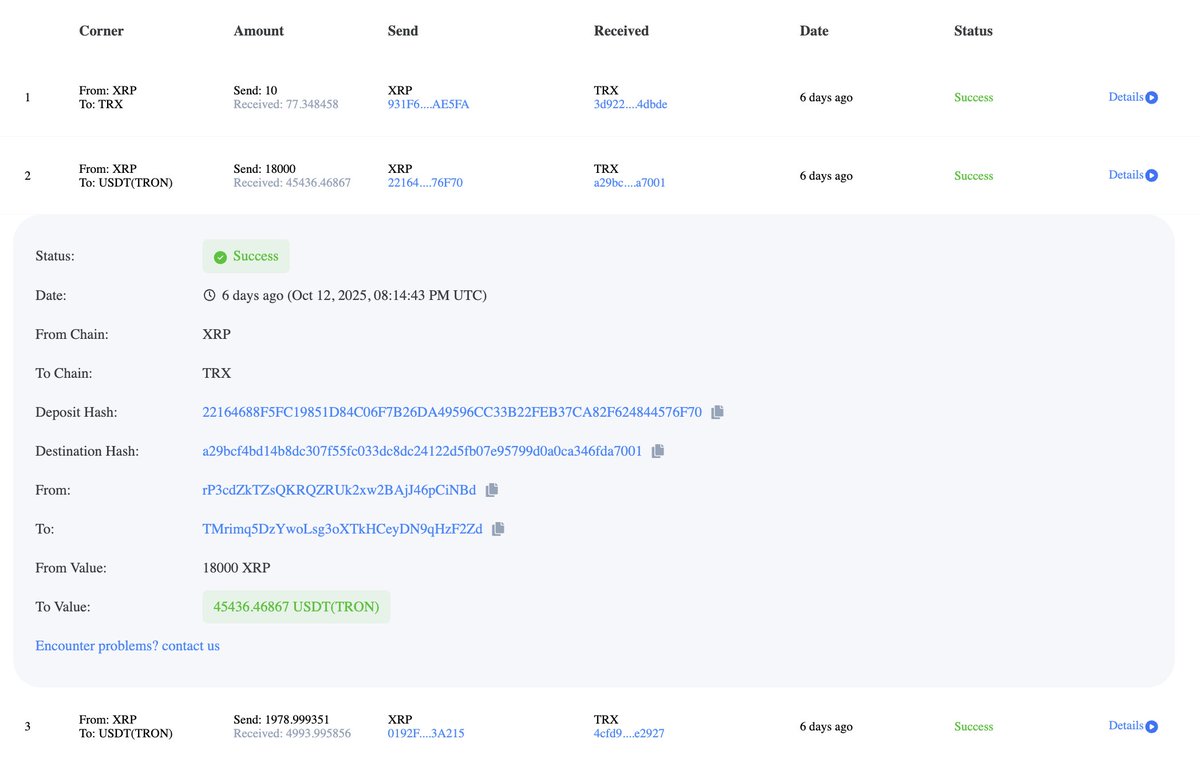
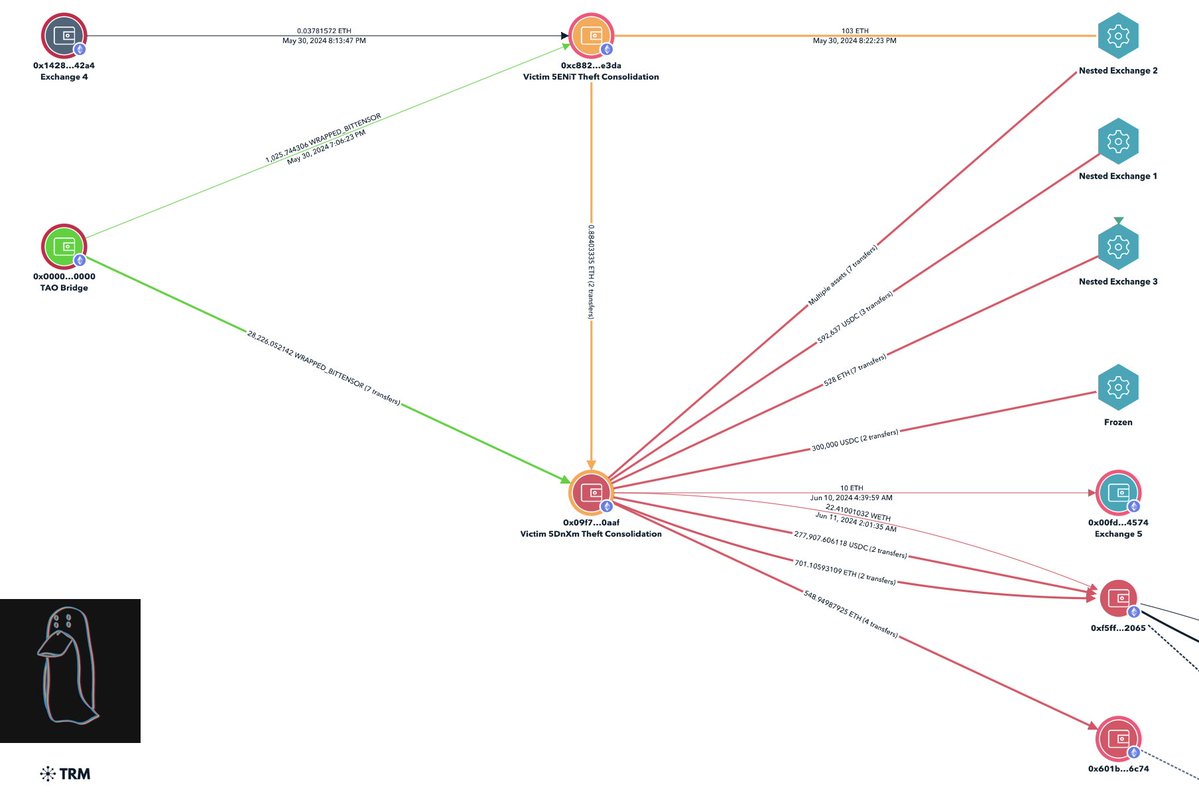
I traced out the payment addresses from the table to two consolidation addresses.
0x58225fed0714e5b9b235642eba7dae3714090a2d
0xa7f9555c34626eb81b64774356a40ca1a6a794ca
I traced out the payment addresses from the table to two consolidation addresses.
0x58225fed0714e5b9b235642eba7dae3714090a2d
0xa7f9555c34626eb81b64774356a40ca1a6a794ca

3/ Sandy Nguyen (@bullishgopher) a DPRK ITW from this cluster was spotted via OSINT next to the North Korea flag at an event in Russia.
A small group of people still believe North Korean devs are just a conspiracy despite all of the IOCs, research, etc widely available.


A small group of people still believe North Korean devs are just a conspiracy despite all of the IOCs, research, etc widely available.



4/ Other indicators from this cluster after speaking with teams displayed immediate red flags.
>ITW refused to meet up irl with team member but claimed to live in same city
>Three ITWs referred each another for role at the same project
>Russian IPs for ITW supposedly from California
>Changing Github usernames / deleted LinkedIn
>payments for multiple ITWs flow to same address
>failed routine KYC check
>ITW refused to meet up irl with team member but claimed to live in same city
>Three ITWs referred each another for role at the same project
>Russian IPs for ITW supposedly from California
>Changing Github usernames / deleted LinkedIn
>payments for multiple ITWs flow to same address
>failed routine KYC check
5/ USDC was sent directly from Circle accounts to three addresses in this cluster.
It’s 1 hop from an address blacklisted by Tether in April 2023 tied to Hyon Sop Sim.
Other DPRK ITW clusters currently have decent sized quantities of USDC sitting.
I think it’s misleading Circle markets themselves as the most compliant stablecoin that puts security first when they do not have proper channels to report illicit activity and do not engage in incident response during major exploits.

It’s 1 hop from an address blacklisted by Tether in April 2023 tied to Hyon Sop Sim.
Other DPRK ITW clusters currently have decent sized quantities of USDC sitting.
I think it’s misleading Circle markets themselves as the most compliant stablecoin that puts security first when they do not have proper channels to report illicit activity and do not engage in incident response during major exploits.


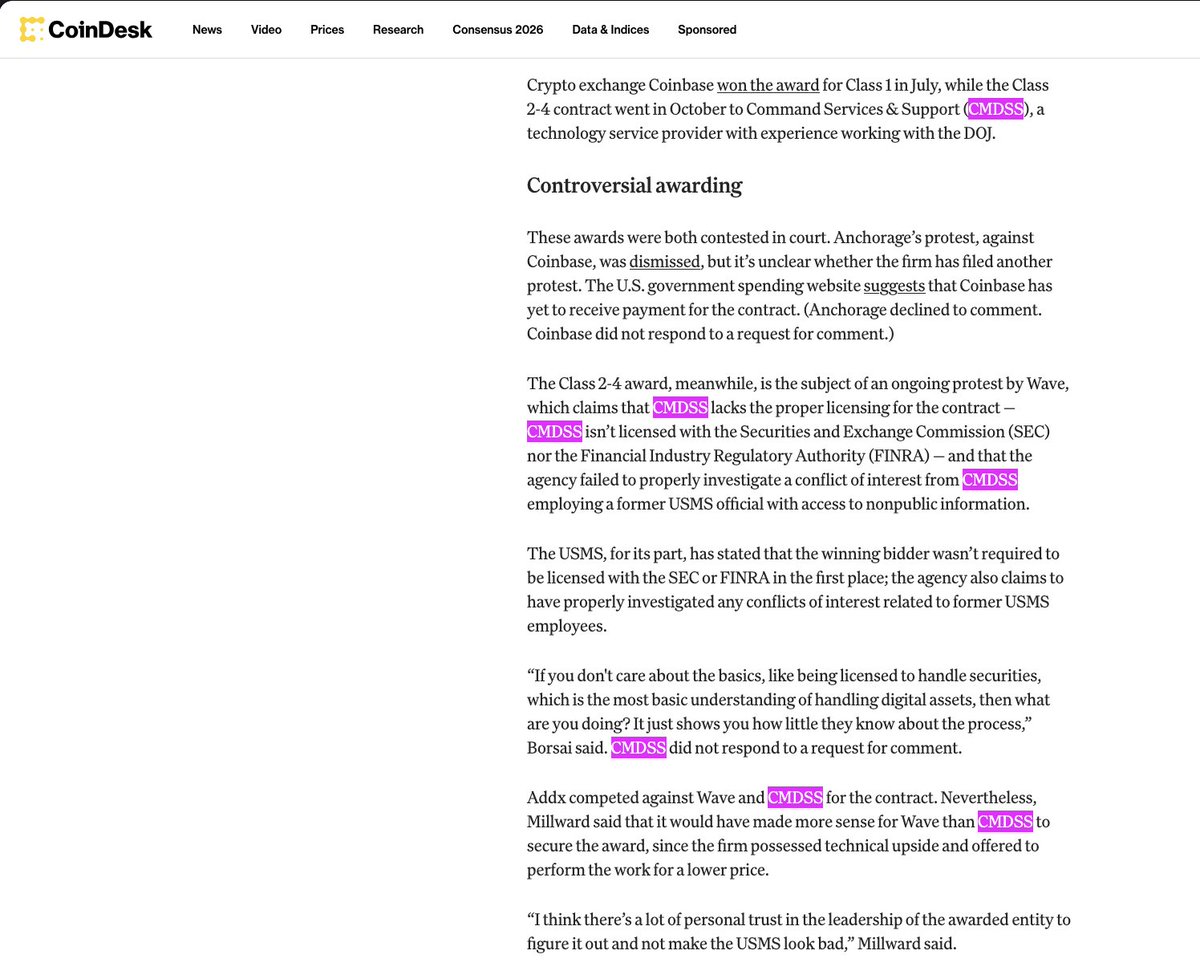
6/ I am closely monitoring five other larger clusters of DPRK ITWs but will not share those addresses publicly since they are active.
One thing to note is the number does not include exploits conducted by them on projects (LND, ChainSaw, Favrr, Munchables, Dream, etc)
They typically take on multiple roles at once and frequently get fired due to under performance so turnover is high.
Once they infiltrate a team and take ownership of contracts your project becomes at risk of an incident.


One thing to note is the number does not include exploits conducted by them on projects (LND, ChainSaw, Favrr, Munchables, Dream, etc)
They typically take on multiple roles at once and frequently get fired due to under performance so turnover is high.
Once they infiltrate a team and take ownership of contracts your project becomes at risk of an incident.



7/ A few key trends I have observed:
A common misconception is that US exchanges have more rigorous KYC/AML requirements than offshore competitors.
DPRK ITWs have an increasing number of accounts tied to US exchanges like Coinbase or Robinhood
MEXC remains a popular choice by ITWs for laundering funds onchain.
A few years ago Binance was widely used by ITWs but now it is rare due to improvements in detection and private industry collaboration that lead to seizures.
A common misconception is that US exchanges have more rigorous KYC/AML requirements than offshore competitors.
DPRK ITWs have an increasing number of accounts tied to US exchanges like Coinbase or Robinhood
MEXC remains a popular choice by ITWs for laundering funds onchain.
A few years ago Binance was widely used by ITWs but now it is rare due to improvements in detection and private industry collaboration that lead to seizures.
8/ Another misconception is crypto projects have the most DPRK ITWs when in reality the issue is just as bad if not worse at traditional tech companies.
The downside of fiat is you cannot trace funds back to the company to alert them whereas when ITWs are paid with crypto it makes all activity onchain traceable.
The rise of neobanks/fintech with stablecoin integrations has allowed DPRK ITWs to easily on-ramp fiat -> crypto.
The downside of fiat is you cannot trace funds back to the company to alert them whereas when ITWs are paid with crypto it makes all activity onchain traceable.
The rise of neobanks/fintech with stablecoin integrations has allowed DPRK ITWs to easily on-ramp fiat -> crypto.
9/ I believe that when a team hires multiple DPRK ITWs it is a decent indicator for determining that startup will be a failure.
Unlike other threats to the industry DPRK ITWs have little sophistication so it’s mainly the result of a team’s own negligence.
I think the prevalence of them is due to being cheap and the lack of available talent as well as high valuations that resulted in incompetent founders who received funding.
Unlike other threats to the industry DPRK ITWs have little sophistication so it’s mainly the result of a team’s own negligence.
I think the prevalence of them is due to being cheap and the lack of available talent as well as high valuations that resulted in incompetent founders who received funding.

Update: Sandy Nguyen changed his X username after my post from ‘bullishgopher’ to ‘dddxxxssseaeff’
X user ID: 1532495241038778387

X user ID: 1532495241038778387


• • •
Missing some Tweet in this thread? You can try to
force a refresh