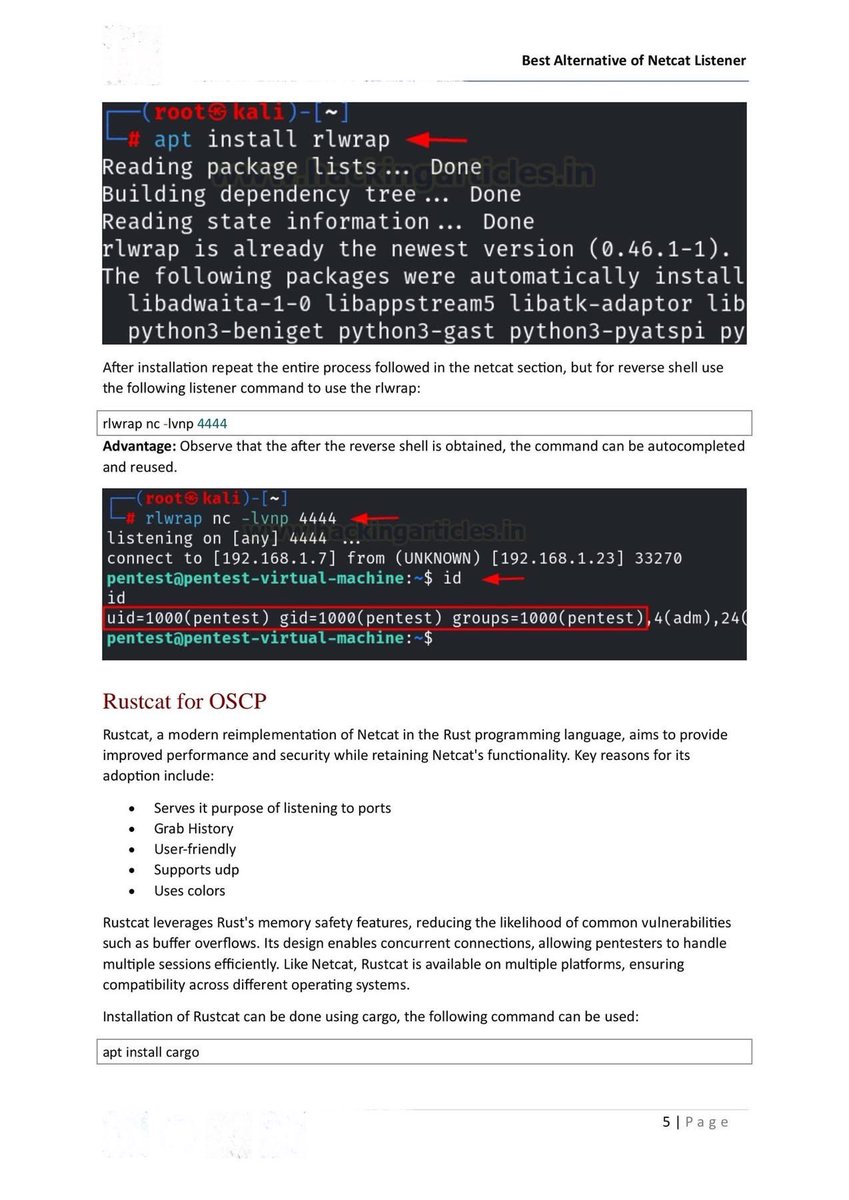
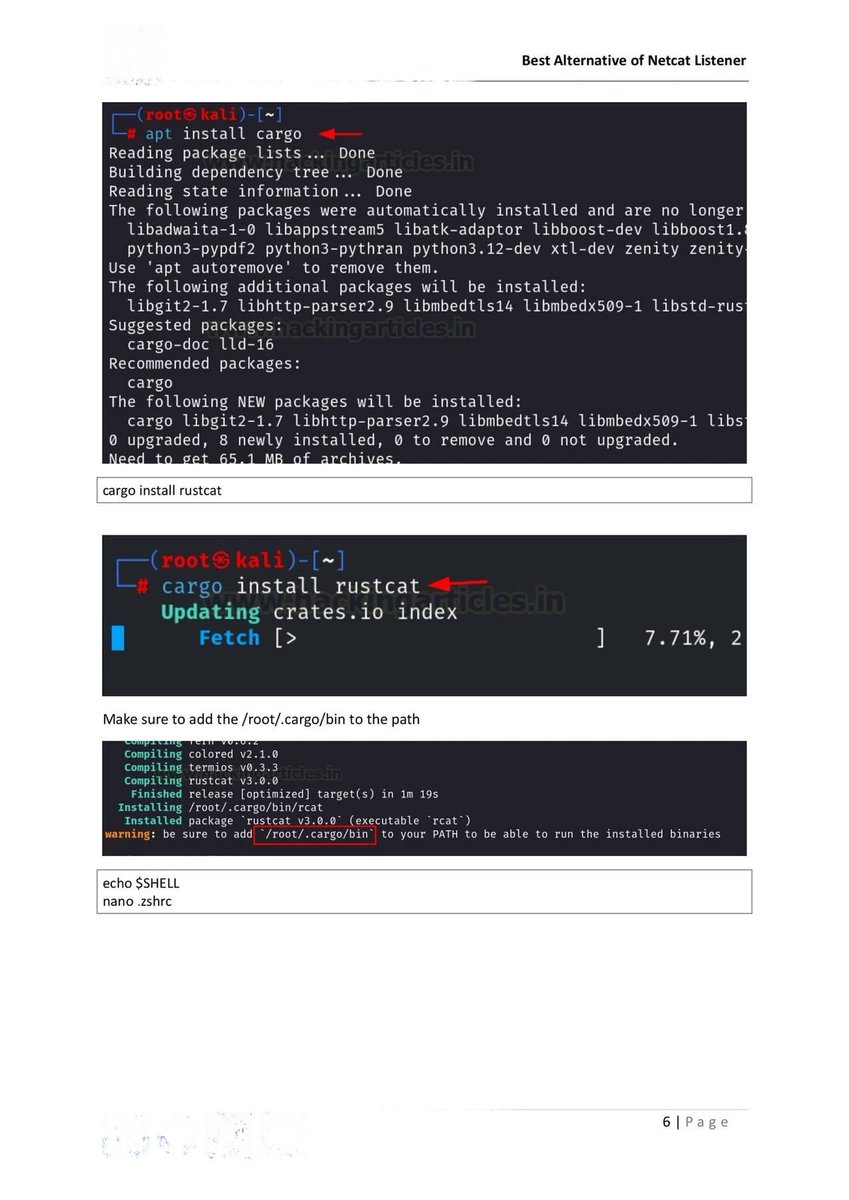
✅ 60 Search Engines for Hackers, OSINT Analysts & Cybersecurity Pros
Explore, analyze, uncover legally and ethically.
Well Categorized ⤵️💯
Explore, analyze, uncover legally and ethically.
Well Categorized ⤵️💯

Whether you’re digging for vulnerabilities, tracing digital footprints, or conducting threat intel, these search engines unlock layers of the internet you can’t reach through Google alone.
🔬 Recon & Vulnerability Discovery
1.🔎 Google — google.com
2.🛰️ Shodan — shodan.io
3.🌐 Censys — censys.io
4.🔭 ZoomEye — zoomeye.org
5.🧱 GreyNoise — greynoise.io
6.🚀 FOFA — fofa.info
.
1.🔎 Google — google.com
2.🛰️ Shodan — shodan.io
3.🌐 Censys — censys.io
4.🔭 ZoomEye — zoomeye.org
5.🧱 GreyNoise — greynoise.io
6.🚀 FOFA — fofa.info
.
7.🧿 Onyphe — onyphe.io
8.🗂️ NIST NVD — nvd.nist.gov
9.🧬 osv.dev — osv.dev
10.📊 VulnIQ — vulniq.com
11.⚙️ VulDB — vuldb.com
12.🧨 0day.today — 0day.today
8.🗂️ NIST NVD — nvd.nist.gov
9.🧬 osv.dev — osv.dev
10.📊 VulnIQ — vulniq.com
11.⚙️ VulDB — vuldb.com
12.🧨 0day.today — 0day.today
13.📘 OpenCVE — opencve.io
14.💣 ExploitDB — exploit-db.com
15.🧩 Rapid7 DB — rapid7.com/db
16.🔔 Vulmon — vulmon.com
.
14.💣 ExploitDB — exploit-db.com
15.🧩 Rapid7 DB — rapid7.com/db
16.🔔 Vulmon — vulmon.com
.
17.🌪️ Chaos (ProjectDiscovery) — chaos.projectdiscovery.io
18.🕹️ FullHunt — fullhunt.io
19.🧪 Tria.ge — tria.ge
20.🧫 malapi.io — malapi.io
18.🕹️ FullHunt — fullhunt.io
19.🧪 Tria.ge — tria.ge
20.🧫 malapi.io — malapi.io
🧭 Certificates, DNS & Infrastructure
21.📜 crt.sh — crt.sh
22.🏗️ BuiltWith — builtwith.com
23.📡 RobTex — robtex.com
24.🧭 DNSdb — dnsdb.io
21.📜 crt.sh — crt.sh
22.🏗️ BuiltWith — builtwith.com
23.📡 RobTex — robtex.com
24.🧭 DNSdb — dnsdb.io
📶 Wireless & Geolocation Intelligence
29.🗺️ Wigle — wigle.net
30.📍 WiFiMap — wifimap.io
31.🛰️ WiFiSPC — wifispc.com
29.🗺️ Wigle — wigle.net
30.📍 WiFiMap — wifimap.io
31.🛰️ WiFiSPC — wifispc.com
🧠 Static Code, File, and Tech Stack Discovery
32.🔠 SearchCode — searchcode.com
33.🔍 grep.app — grep.app
34.🧱 LOLBAS — lolbas-project.github.io
32.🔠 SearchCode — searchcode.com
33.🔍 grep.app — grep.app
34.🧱 LOLBAS — lolbas-project.github.io
👥 People & Personal Data Search
38.🧑💼 Hunter.io — hunter.io
39.🧠 Skymem — skymem.info
40.🧾 ThatsThem — thatsthem.com
38.🧑💼 Hunter.io — hunter.io
39.🧠 Skymem — skymem.info
40.🧾 ThatsThem — thatsthem.com
41.🔐 Snusbase — snusbase.com
42.🕳️ Dehashed — dehashed.com
43.📞 Tellows — tellows.com
44.🧬 SpyDialer — spydialer.com
42.🕳️ Dehashed — dehashed.com
43.📞 Tellows — tellows.com
44.🧬 SpyDialer — spydialer.com
💧 Leak & Exposure Monitoring
48.🌊 LeakIX — leakix.net
49.🧰 Omnisint — omnisint.io
50.🕶️ SynapsInt — synapsint.com
51.🌀 Riddler — riddler.io.
48.🌊 LeakIX — leakix.net
49.🧰 Omnisint — omnisint.io
50.🕶️ SynapsInt — synapsint.com
51.🌀 Riddler — riddler.io.
🌐 Alternative Web Search Tools
55.🔍 Bing — bing.com
56.🦆 DuckDuckGo — duckduckgo.com (suggested)
57.🕵️♂️ Startpage — startpage.com (suggested)
58.🌱 Mojeek — mojeek.com (suggested)
55.🔍 Bing — bing.com
56.🦆 DuckDuckGo — duckduckgo.com (suggested)
57.🕵️♂️ Startpage — startpage.com (suggested)
58.🌱 Mojeek — mojeek.com (suggested)
📚 Bonus Intelligence Resources
59.🧭 OSINT Framework — osintframework.com (structured reference)
60.🔗 Maltego Community — maltego.com (optional visual link mapper)
59.🧭 OSINT Framework — osintframework.com (structured reference)
60.🔗 Maltego Community — maltego.com (optional visual link mapper)
💡 Whether you’re in bug bounty recon, corporate investigations, or digital forensics having the right search tools can supercharge your workflow.
⚠️ Disclaimer: These tools are intended strictly for educational use and ethical security research. Always operate within legal scopes such as bug bounty programs, authorized assessments, or public datasets.
#OSINT #EthicalHacking #RandomRedGuy #RedTeam
#OSINT #EthicalHacking #RandomRedGuy #RedTeam
• • •
Missing some Tweet in this thread? You can try to
force a refresh