How to get URL link on X (Twitter) App

 🌐 Scope
🌐 Scope
 Core Focus 🎯
Core Focus 🎯
 It focuses on how real-world enterprise networks work not just commands building the mindset needed to troubleshoot, secure and scale networks.
It focuses on how real-world enterprise networks work not just commands building the mindset needed to troubleshoot, secure and scale networks.

 🔑 Key Topics
🔑 Key Topics
 Coverage:
Coverage: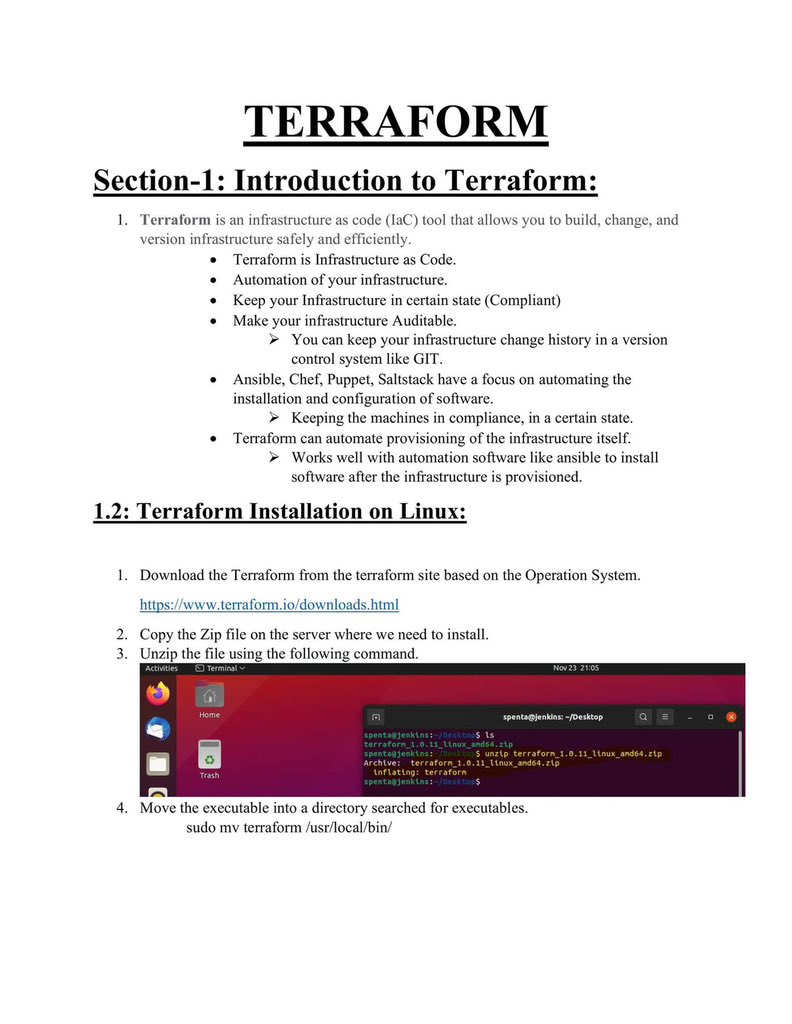
 🔧 What you’ll learn
🔧 What you’ll learn
 Coverage includes:
Coverage includes:
 What it covers:
What it covers:
 Unlike purely technical IR documents, it treats incident response as an organization-wide capability not just a SOC function.
Unlike purely technical IR documents, it treats incident response as an organization-wide capability not just a SOC function.

 Beginner: ML basics & types, core terms, data preprocessing/splitting, evaluation metrics, overfitting vs underfitting.
Beginner: ML basics & types, core terms, data preprocessing/splitting, evaluation metrics, overfitting vs underfitting.
 🔍 What It Covers
🔍 What It Covers
 🔐 What It Covers
🔐 What It Covers
 What it Covers
What it Covers
 ✔ Core Focus Areas
✔ Core Focus Areas
 🔐 Cybersecurity Roadmap Overview
🔐 Cybersecurity Roadmap Overview
 Who uses it?
Who uses it?
 Most beginners want shortcuts.
Most beginners want shortcuts.
 This Fortinet lab guide provides a fully integrated end-to-end FortiGate implementation, walking you through every layer of design, configuration and defense.
This Fortinet lab guide provides a fully integrated end-to-end FortiGate implementation, walking you through every layer of design, configuration and defense.