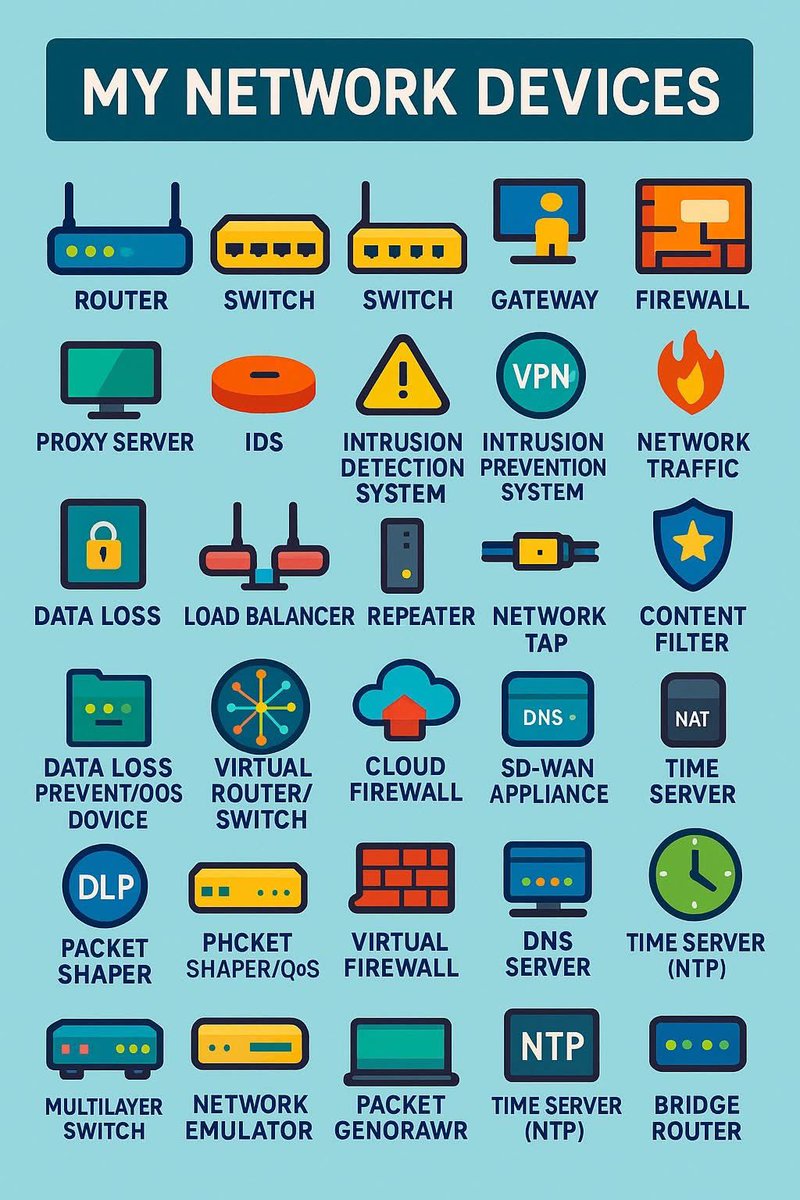
If you’re getting into cybersecurity, IT, or just like knowing how things work, understanding key network devices is a must. These tools run everything behind the scenes from your online games to enterprise systems. Here’s a quick breakdown every tech-savvy man should know.
🧩 Router – The Traffic Director
A router is your network’s commander-in-chief. It connects different networks together, like your home LAN to the internet. Its main job is to route data packets to the right destination, making sure what you send or receive goes exactly where
A router is your network’s commander-in-chief. It connects different networks together, like your home LAN to the internet. Its main job is to route data packets to the right destination, making sure what you send or receive goes exactly where
it should. Most routers also come equipped with NAT (Network Address Translation) and firewall features to keep outside threats at bay.
🔁 Switch – The Local Connector
Think of a switch as the internal network manager. It connects multiple devices computers, printers, servers within the same local network (LAN). Working at Layer 2 of the OSI model, it uses MAC addresses to direct traffic.
Think of a switch as the internal network manager. It connects multiple devices computers, printers, servers within the same local network (LAN). Working at Layer 2 of the OSI model, it uses MAC addresses to direct traffic.
Advanced (or “smart”) switches allow you to configure VLANs, prioritize traffic with QoS, and even monitor network performance.
📶 Access Point (AP) – The Wi-Fi Enabler
If you want wireless access, this is the tool An access point extends your network’s reach by providing Wi-Fi connectivity. It plugs into a switch or router via Ethernet and broadcasts a wireless signal for laptops, phones, and IoT devices
If you want wireless access, this is the tool An access point extends your network’s reach by providing Wi-Fi connectivity. It plugs into a switch or router via Ethernet and broadcasts a wireless signal for laptops, phones, and IoT devices
. Essential for solid coverage in large homes, offices, or any public space.
🛡️ Firewall – The Security Gatekeeper
Every serious setup needs a firewall. Whether hardware or software-based, it filters incoming and outgoing traffic based on predefined security rules. Firewalls block unauthorized access, monitor threats, and keep your network locked down.
Every serious setup needs a firewall. Whether hardware or software-based, it filters incoming and outgoing traffic based on predefined security rules. Firewalls block unauthorized access, monitor threats, and keep your network locked down.
🌍 Modem – The Signal Translator
The modem is the bridge between your local setup and your Internet Service Provider (ISP). It converts analog signals from DSL, cable, or fiber lines into digital data your network can understand and vice versa. Without it, you’re not getting
The modem is the bridge between your local setup and your Internet Service Provider (ISP). It converts analog signals from DSL, cable, or fiber lines into digital data your network can understand and vice versa. Without it, you’re not getting
⚖️ Load Balancer – The Power Distributor
In high-performance or enterprise networks, a load balancer is key. It distributes incoming traffic across multiple servers to prevent overload, ensuring uptime, stability, and smooth performance. If you’re working with cloud services.
In high-performance or enterprise networks, a load balancer is key. It distributes incoming traffic across multiple servers to prevent overload, ensuring uptime, stability, and smooth performance. If you’re working with cloud services.
🛠️ Network Interface Card (NIC) – The Access Point for Devices
A NIC allows any device desktop, laptop, or server to join a network. It can be wired (Ethernet) or wireless (Wi-Fi), internal (PCIe card) or external (USB). Without it, your device has no way to talk to the rest
A NIC allows any device desktop, laptop, or server to join a network. It can be wired (Ethernet) or wireless (Wi-Fi), internal (PCIe card) or external (USB). Without it, your device has no way to talk to the rest
• • •
Missing some Tweet in this thread? You can try to
force a refresh