🌑 80 Dark Web Facts & Resources You Should Know 🕵️♂️
The Dark Web is often seen as criminal, but it also supports privacy, free speech, and research. Understanding it builds stronger digital safety and awareness.
The Dark Web is often seen as criminal, but it also supports privacy, free speech, and research. Understanding it builds stronger digital safety and awareness.

💡 Key Insights Everyone Should Know:
1️⃣ Definition – The Dark Web is a section of the Deep Web that requires specialized tools (like Tor) to access.
2️⃣ Legality – Not everything on the Dark Web is illegal; it also hosts forums, news sites, and communities focused on privacy.
1️⃣ Definition – The Dark Web is a section of the Deep Web that requires specialized tools (like Tor) to access.
2️⃣ Legality – Not everything on the Dark Web is illegal; it also hosts forums, news sites, and communities focused on privacy.
3️⃣ Privacy Tools – Technologies such as Tor and I2P are designed to enhance anonymity online.
4️⃣ Whistleblowing – Journalists and activists rely on it to protect sources and share sensitive information securely.
4️⃣ Whistleblowing – Journalists and activists rely on it to protect sources and share sensitive information securely.
5️⃣ Risks – Users may encounter scams, malware, and illegal marketplaces ⚠️
6️⃣ Safe Practices – Use VPNs, maintain updated systems, and follow strong OPSEC if researching in controlled environments.
7️⃣ Law Enforcement – Agencies worldwide monitor and shut down illegal operations.
6️⃣ Safe Practices – Use VPNs, maintain updated systems, and follow strong OPSEC if researching in controlled environments.
7️⃣ Law Enforcement – Agencies worldwide monitor and shut down illegal operations.
8️⃣ Educational Value – Cybersecurity professionals study the Dark Web to track emerging threats.
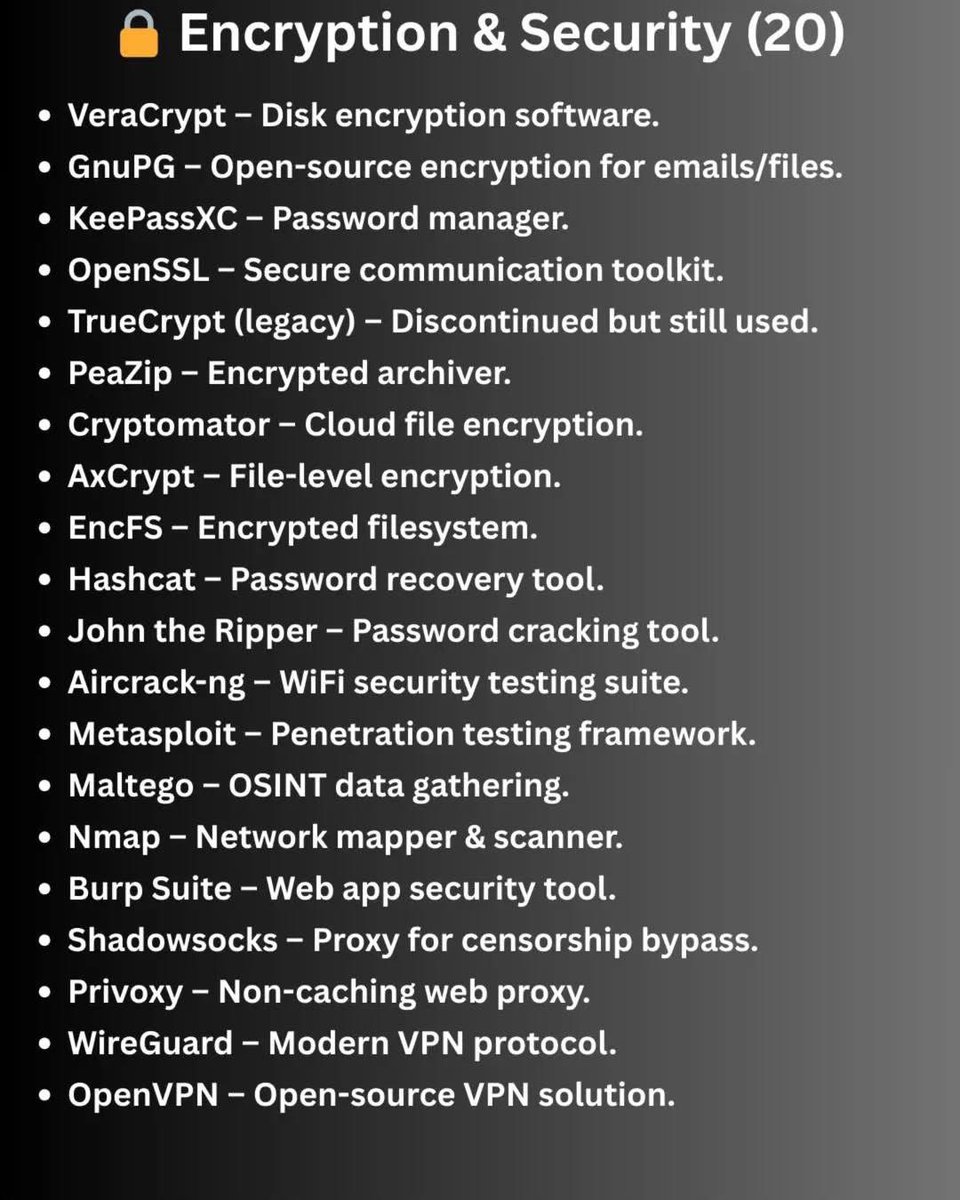
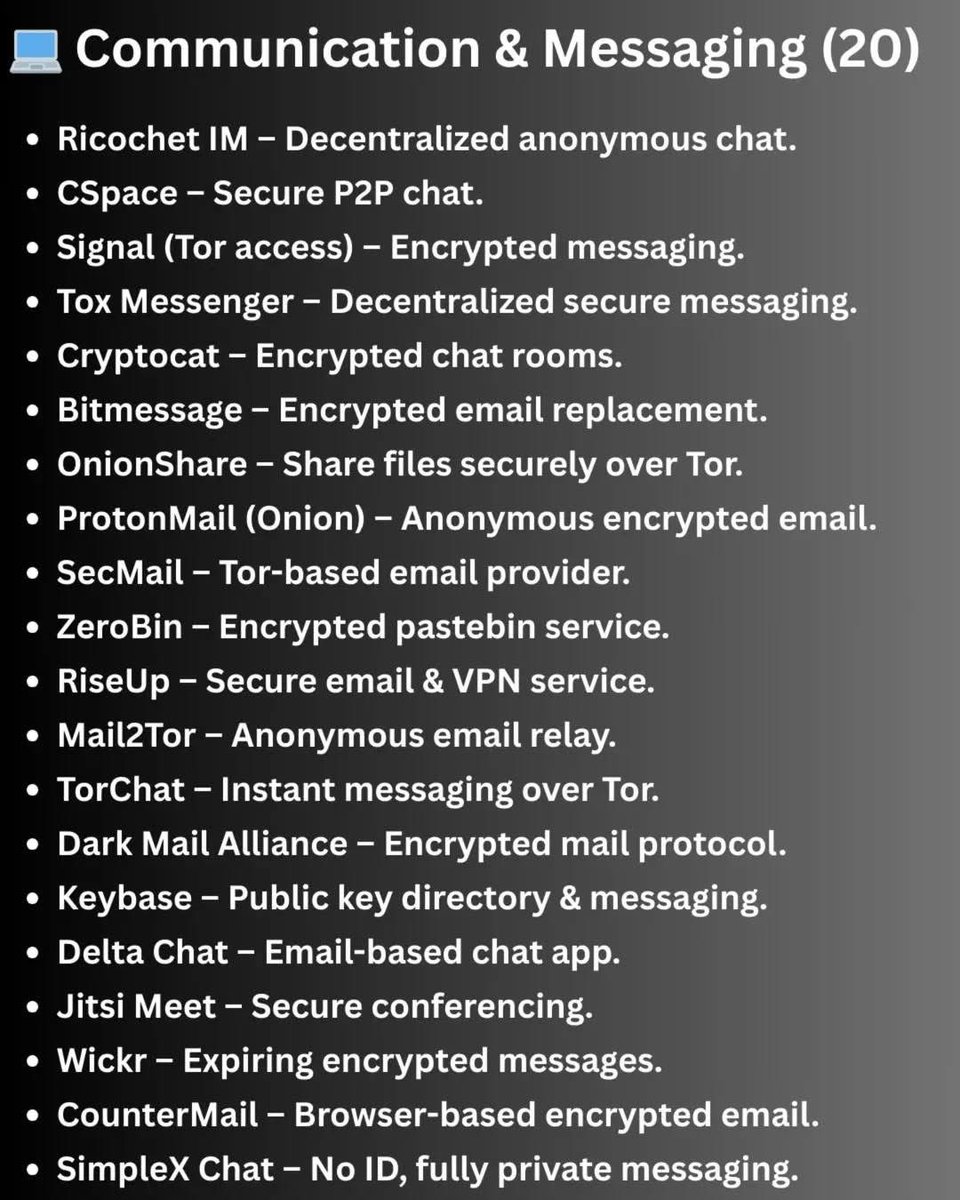
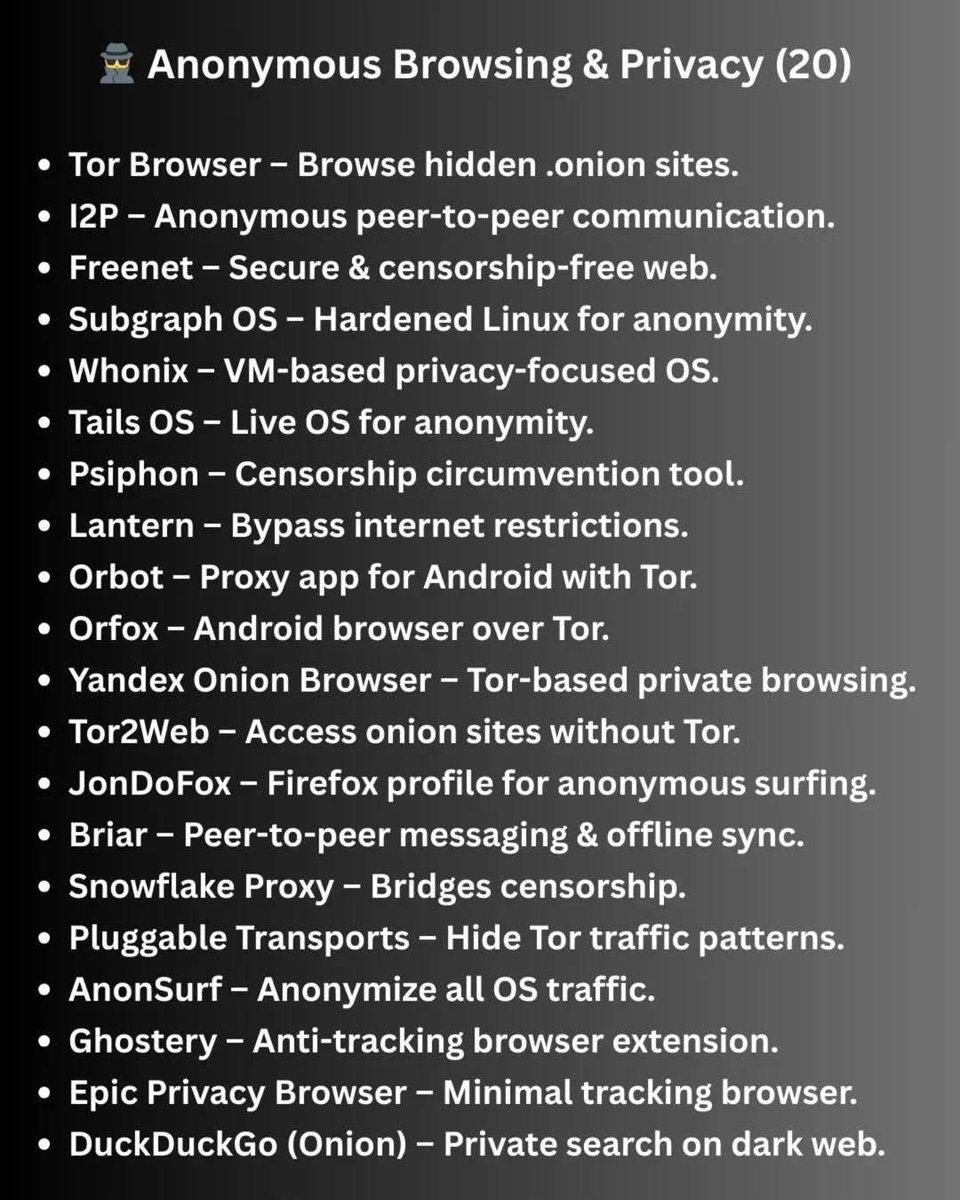
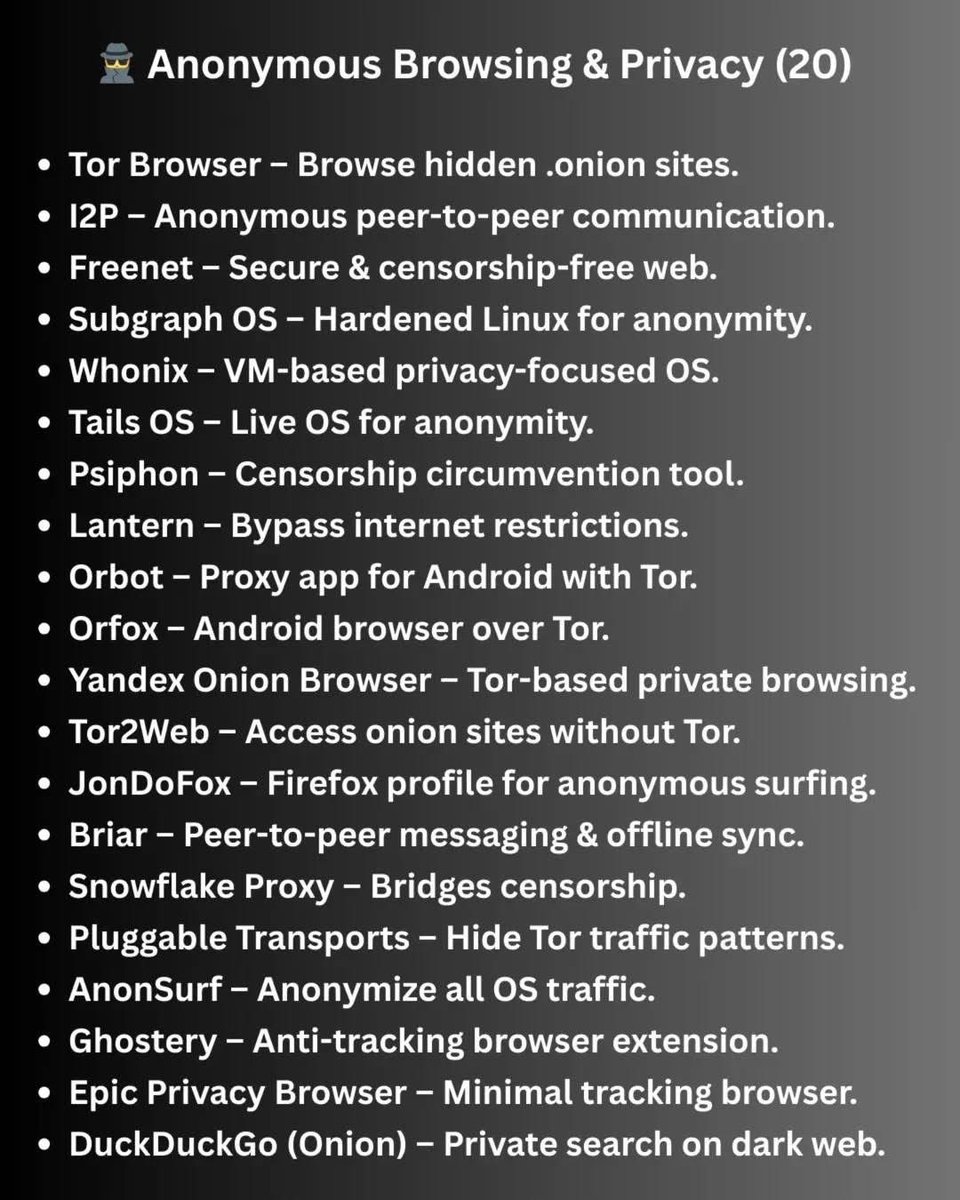
…and the full guide expands into 80+ facts and resources covering tools, history, risks, and safe exploration in research contexts.
…and the full guide expands into 80+ facts and resources covering tools, history, risks, and safe exploration in research contexts.
🌟 Why This Matters:
Understanding the Dark Web helps separate myths from reality, improves online safety, and builds awareness of its impact on cybersecurity, privacy, and digital freedom.
Understanding the Dark Web helps separate myths from reality, improves online safety, and builds awareness of its impact on cybersecurity, privacy, and digital freedom.
⚠️ Disclaimer:
This content is intended only for educational and awareness purposes. Accessing illegal Dark Web material is dangerous, unlawful, and unethical. Always rely on trusted, ethical resources.
#DarkWeb #CyberSecurity #OSINT #CyberAwareness #EthicalTech #Privacy
This content is intended only for educational and awareness purposes. Accessing illegal Dark Web material is dangerous, unlawful, and unethical. Always rely on trusted, ethical resources.
#DarkWeb #CyberSecurity #OSINT #CyberAwareness #EthicalTech #Privacy
• • •
Missing some Tweet in this thread? You can try to
force a refresh