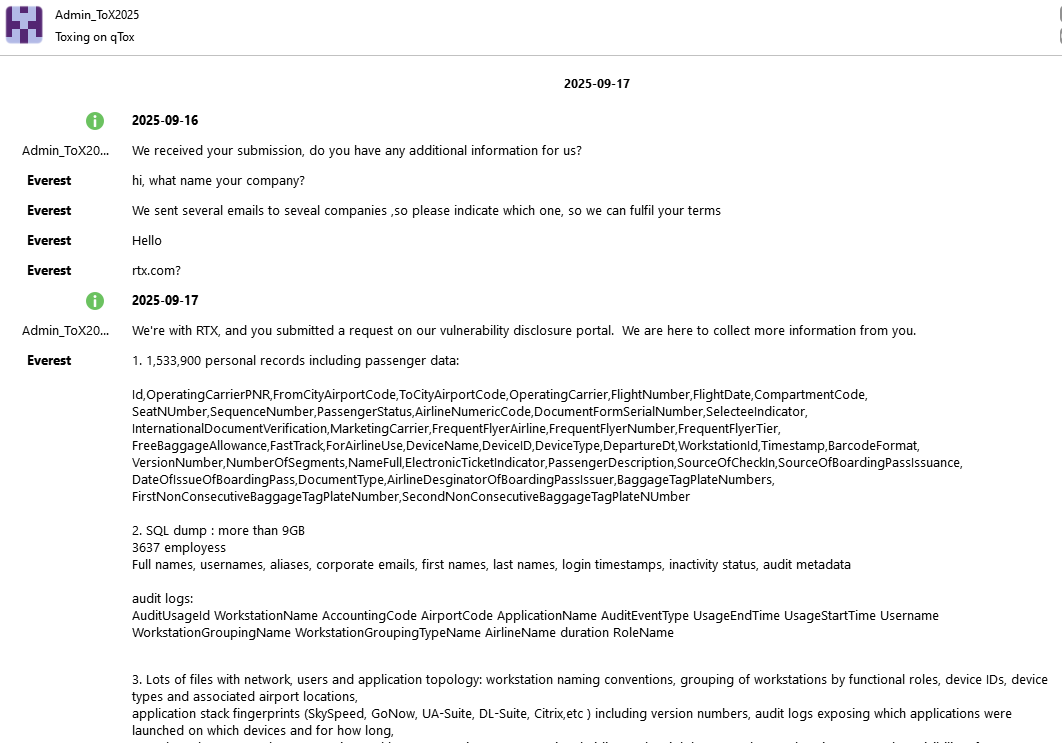
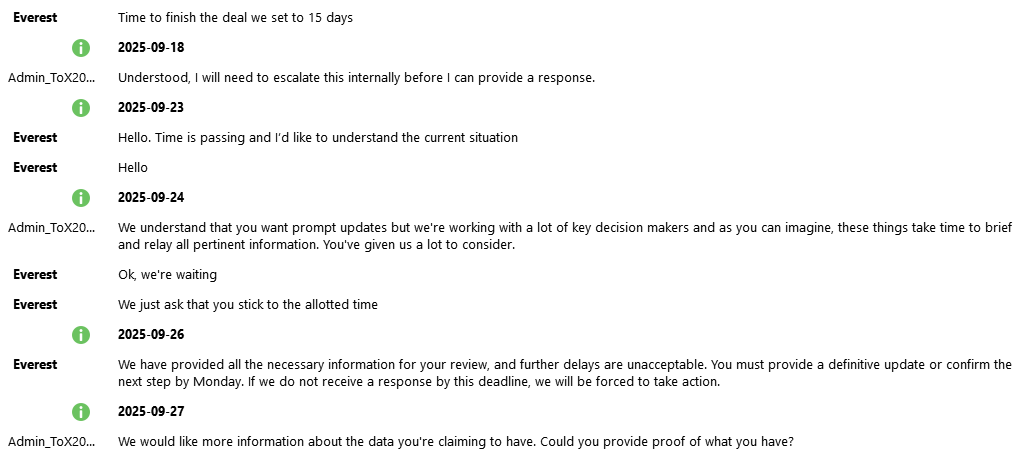
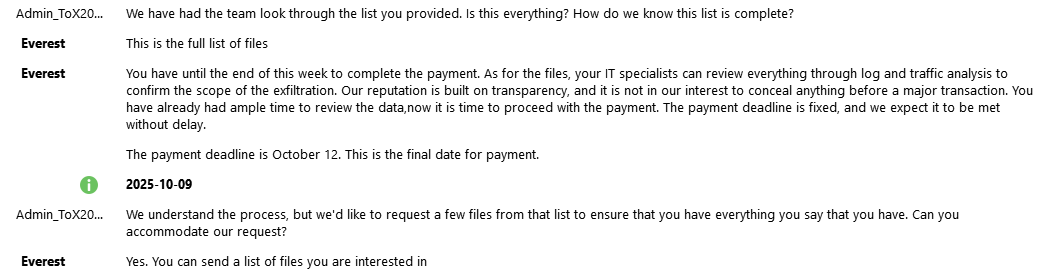
🚨Peter Williams, 39, an Australian, pleaded guilty today in U.S. District Court to selling his employer’s trade secrets to a Russian cyber-tools broker.
The material, stolen over three years from the U.S. defense contractor where he worked, comprised national security-focused software, including at least eight sensitive, protected cyber-exploit components intended for exclusive sale to the U.S. government and select allies. The broker publicly advertises as a reseller of cyber exploits to various customers, including the Russian government.
His employer released the following statement today.
The material, stolen over three years from the U.S. defense contractor where he worked, comprised national security-focused software, including at least eight sensitive, protected cyber-exploit components intended for exclusive sale to the U.S. government and select allies. The broker publicly advertises as a reseller of cyber exploits to various customers, including the Russian government.
His employer released the following statement today.

Correction he pleaded guilty on Wednesday, October 29, 2025.
• • •
Missing some Tweet in this thread? You can try to
force a refresh