
Your weekly go-to cybersecurity newsletter, curated and commented on by our senior analysts.
Got tips? Signal: IntCyberDigest.20
How to get URL link on X (Twitter) App



 His LinkedIn shows his company "Iperlane" was sold to CrowdStrike and that he was also a board member of Black Hat, hence he invited Jeffrey to join him at Black Hat.
His LinkedIn shows his company "Iperlane" was sold to CrowdStrike and that he was also a board member of Black Hat, hence he invited Jeffrey to join him at Black Hat.


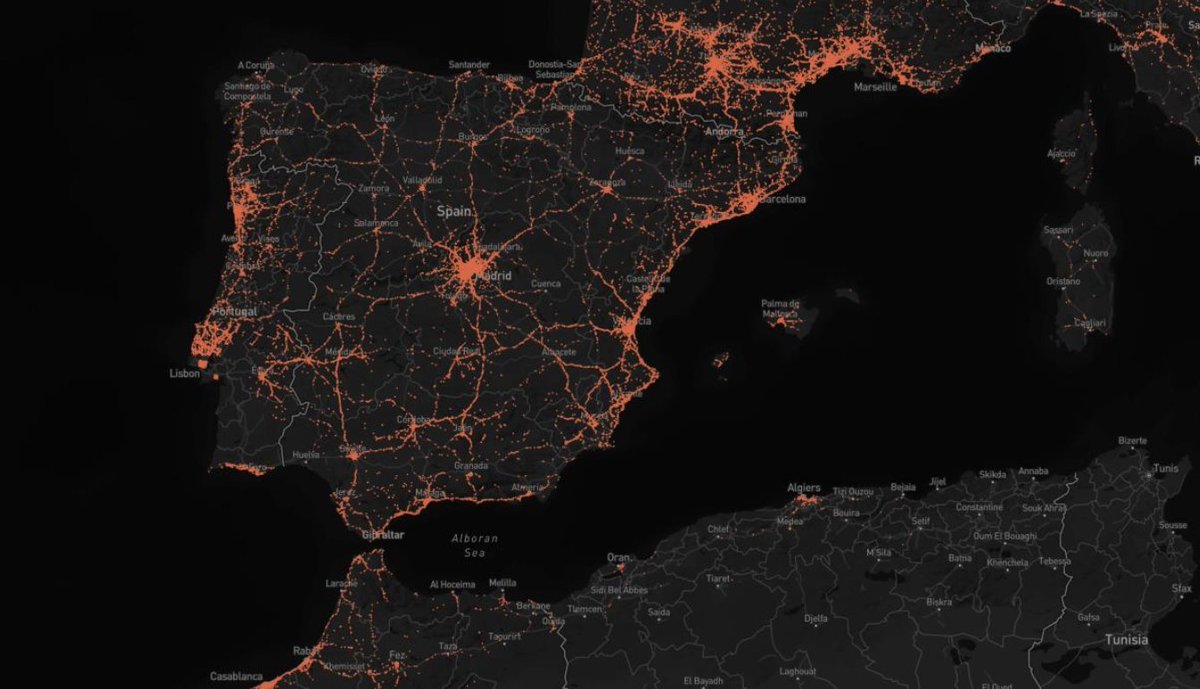
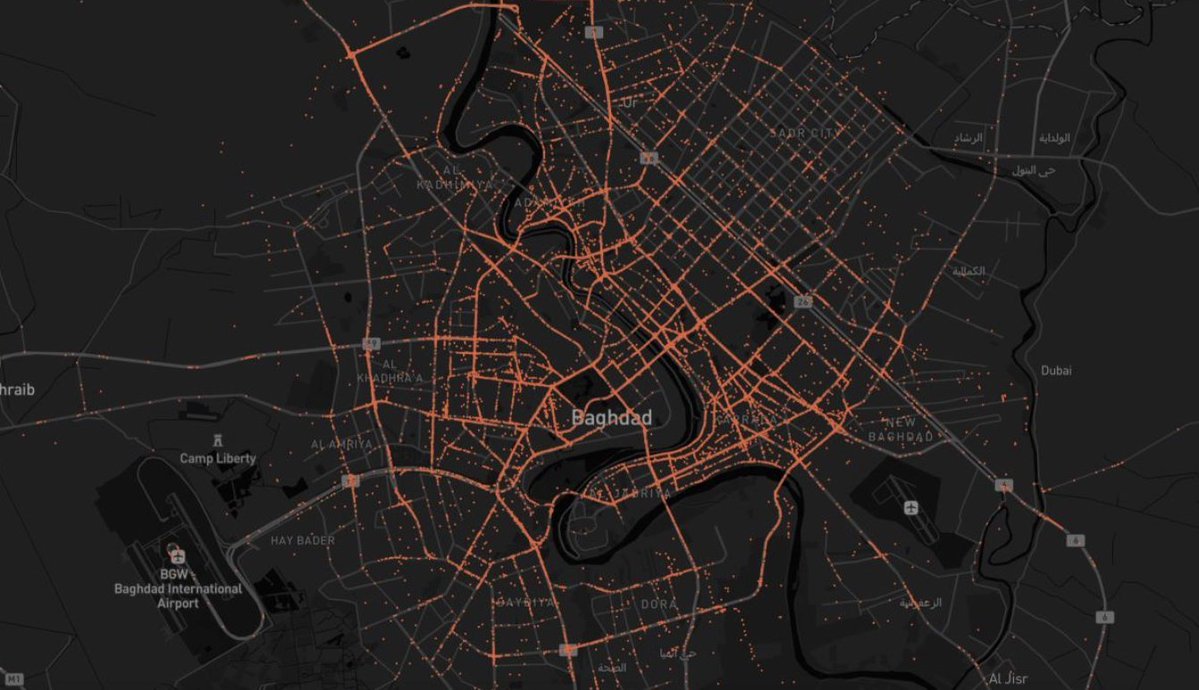
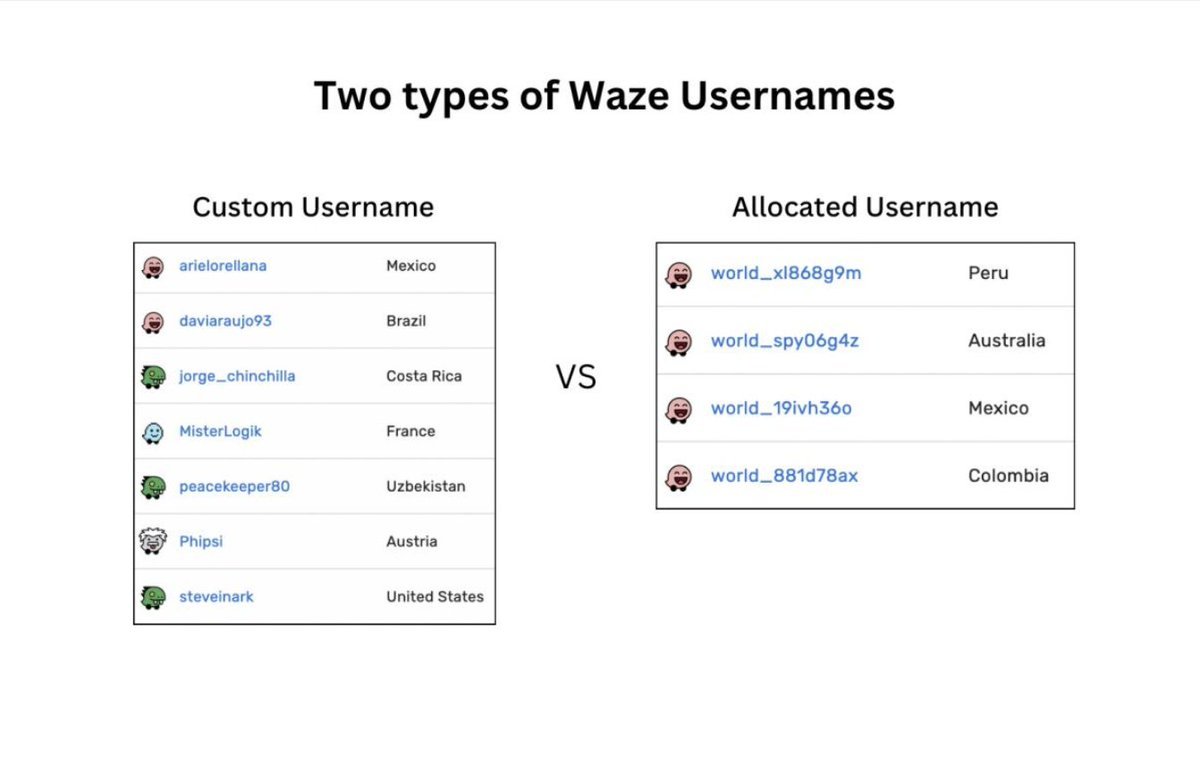
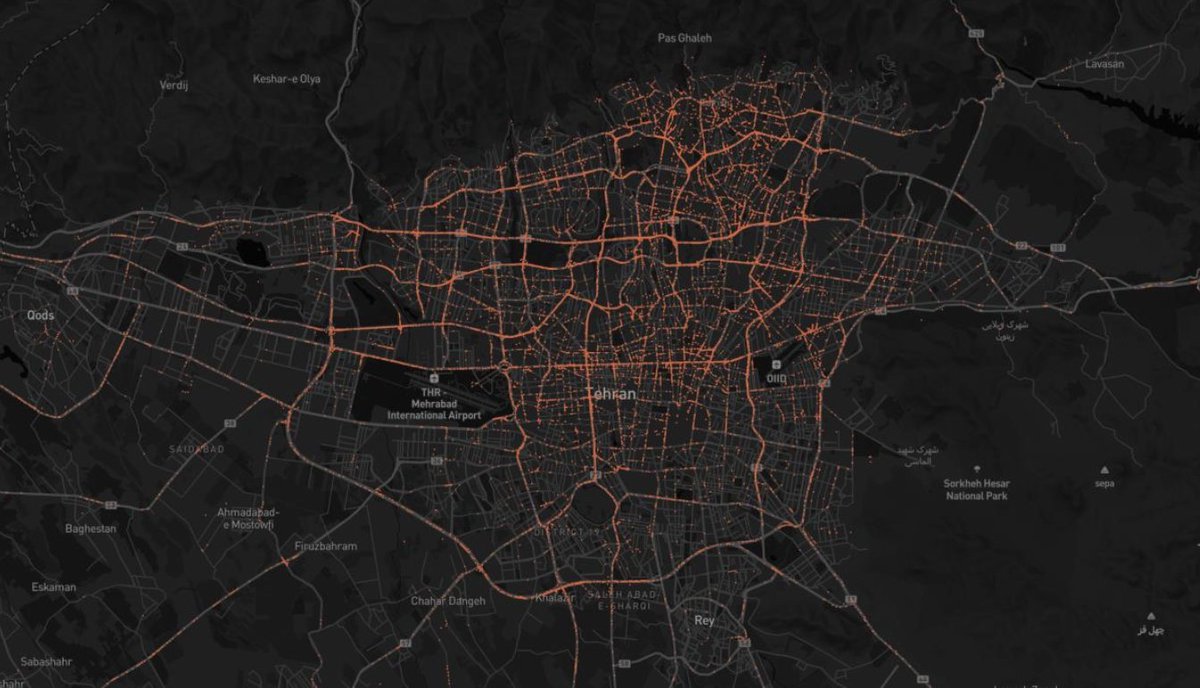 He was able to deanonymize custom usernames by using OSINT tools.
He was able to deanonymize custom usernames by using OSINT tools.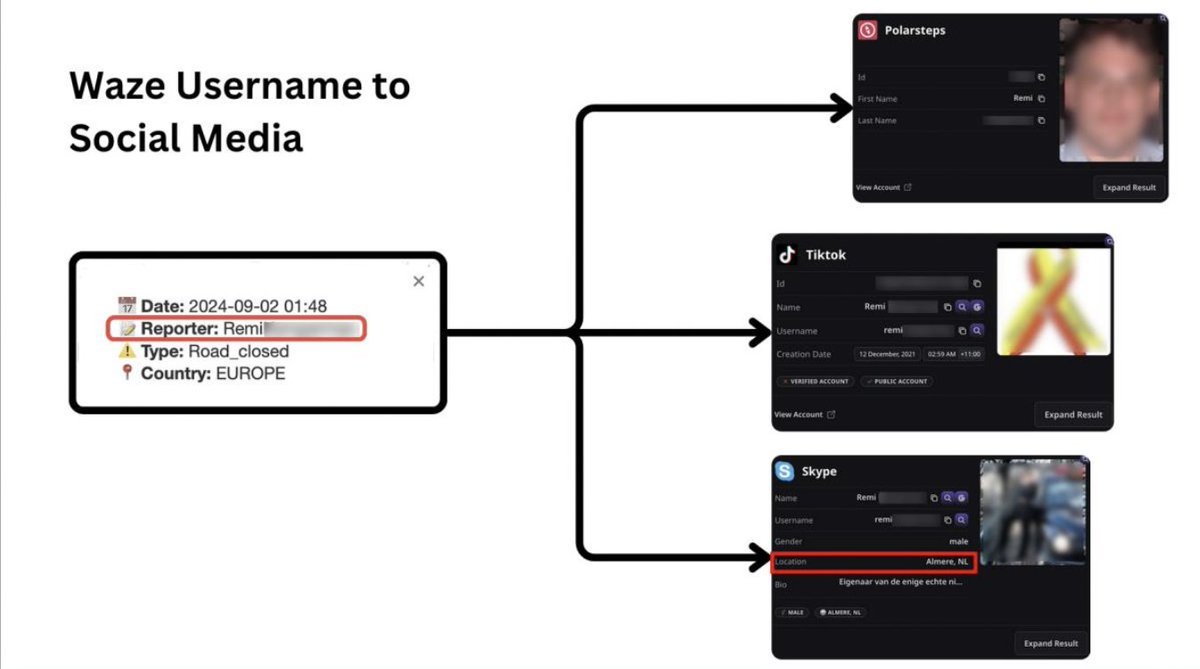

 One year later, the suspect is summoned to appear at the police station in Antwerp, Belgium, on suspicion of premeditated murder.
One year later, the suspect is summoned to appear at the police station in Antwerp, Belgium, on suspicion of premeditated murder. 

 Internal leaked company documents, sales and marketing materials, as well as training videos from the “Intellexa Leaks” investigation provide a never-before-seen glimpse into the internal operations of a mercenary spyware company focused on exploiting vulnerabilities in mobile devices to enable targeted surveillance attacks on human rights defenders, journalists, and members of civil society.
Internal leaked company documents, sales and marketing materials, as well as training videos from the “Intellexa Leaks” investigation provide a never-before-seen glimpse into the internal operations of a mercenary spyware company focused on exploiting vulnerabilities in mobile devices to enable targeted surveillance attacks on human rights defenders, journalists, and members of civil society.


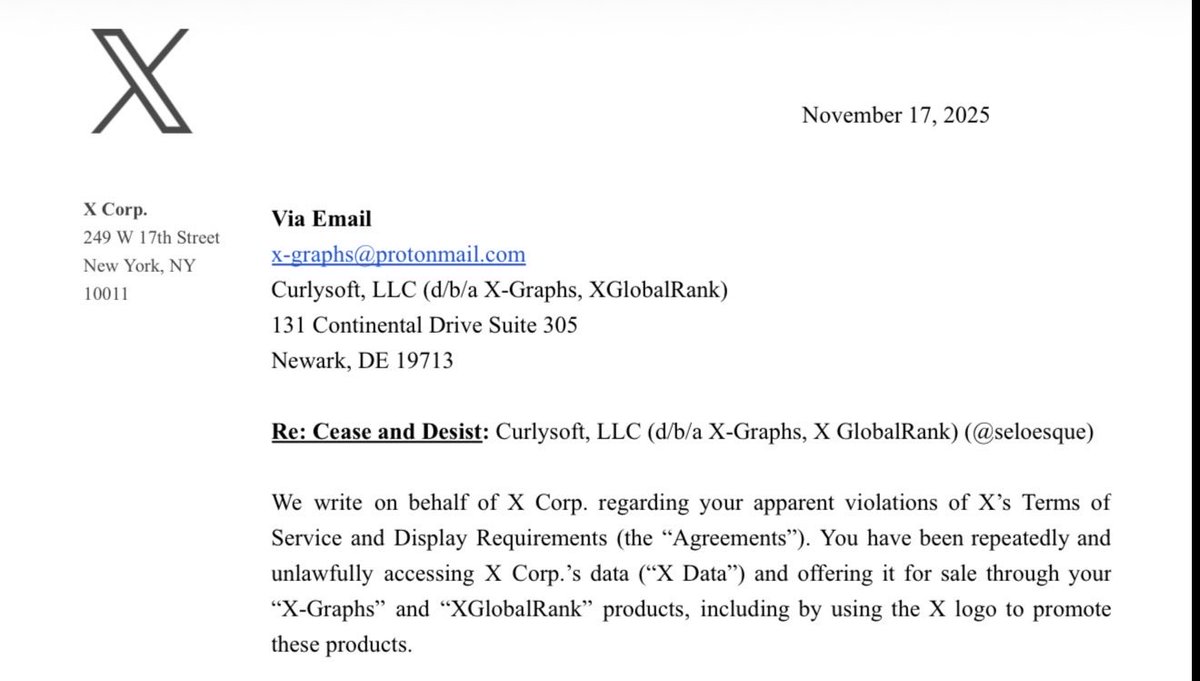
 Despite the developer being open about his project with X employees from the beginning, and getting a job interview and vouch because of it, Nikita Bier mocked him after he was sent a cease and desist.
Despite the developer being open about his project with X employees from the beginning, and getting a job interview and vouch because of it, Nikita Bier mocked him after he was sent a cease and desist.

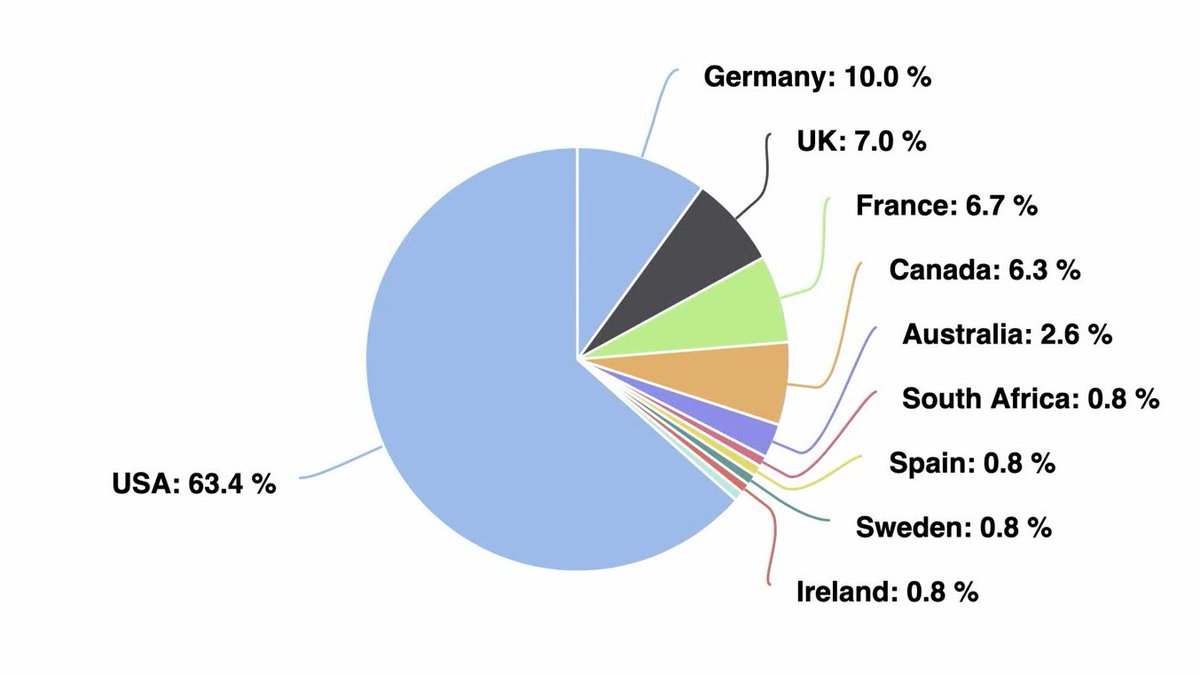
 The documents show a network operations training environment capable of supporting 300 users and 10,000 concurrent connections. It includes DNS gateways, a URL classification database with 100 million entries, and support for 50,000 concurrent connections.
The documents show a network operations training environment capable of supporting 300 users and 10,000 concurrent connections. It includes DNS gateways, a URL classification database with 100 million entries, and support for 50,000 concurrent connections. 

 ZoomEye
ZoomEye
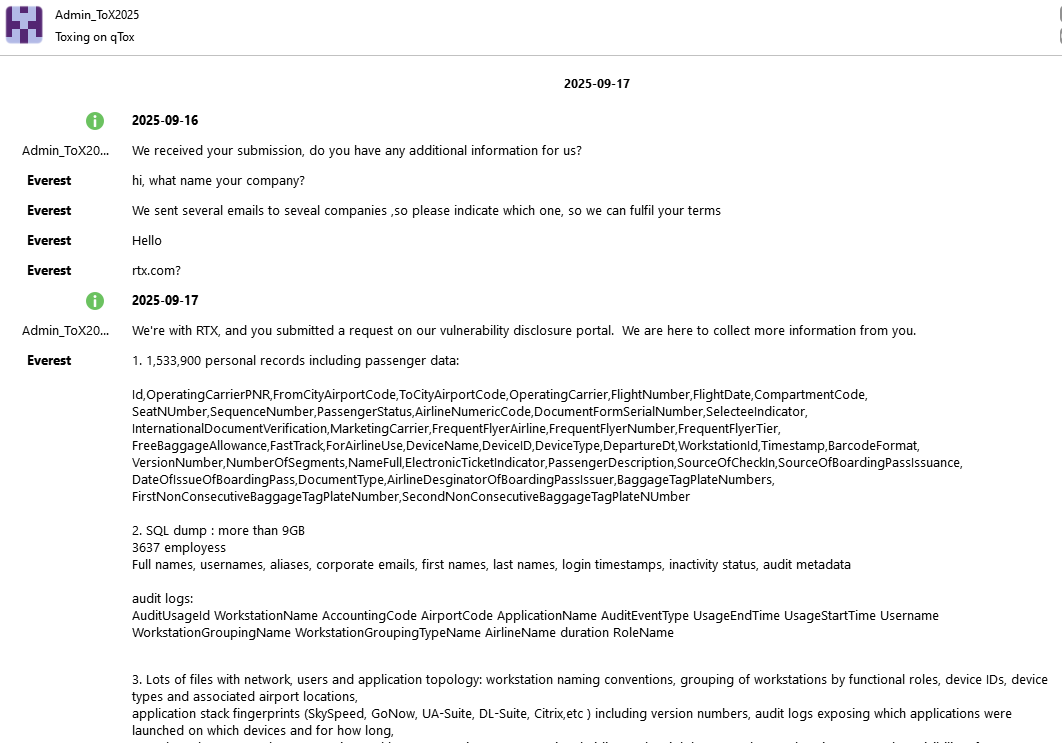


 This is the compromised SFTP server. Username: aiscustomer, password: muse-insecure. Insecure indeed. Why store sensitive files like passenger data, SQL, service documentation, and configurations on a publicly accessible, insecure SFTP server?
This is the compromised SFTP server. Username: aiscustomer, password: muse-insecure. Insecure indeed. Why store sensitive files like passenger data, SQL, service documentation, and configurations on a publicly accessible, insecure SFTP server? 



https://twitter.com/IntCyberDigest/status/1975846997568737666
 Tables:
Tables:

 The file tree includes thousands of repositories referencing major banks, telecoms, airlines, and public-sector organizations, such as Citi, Verizon, Siemens, Bosch, JPMC, HSBC, Merrick Bank, Telstra, Telefonica, and even mentions the U.S. Senate...
The file tree includes thousands of repositories referencing major banks, telecoms, airlines, and public-sector organizations, such as Citi, Verizon, Siemens, Bosch, JPMC, HSBC, Merrick Bank, Telstra, Telefonica, and even mentions the U.S. Senate...

 He sent every order very discreetly packaged, going to great lengths to hide the true contents: counterfeit IDs.
He sent every order very discreetly packaged, going to great lengths to hide the true contents: counterfeit IDs. 




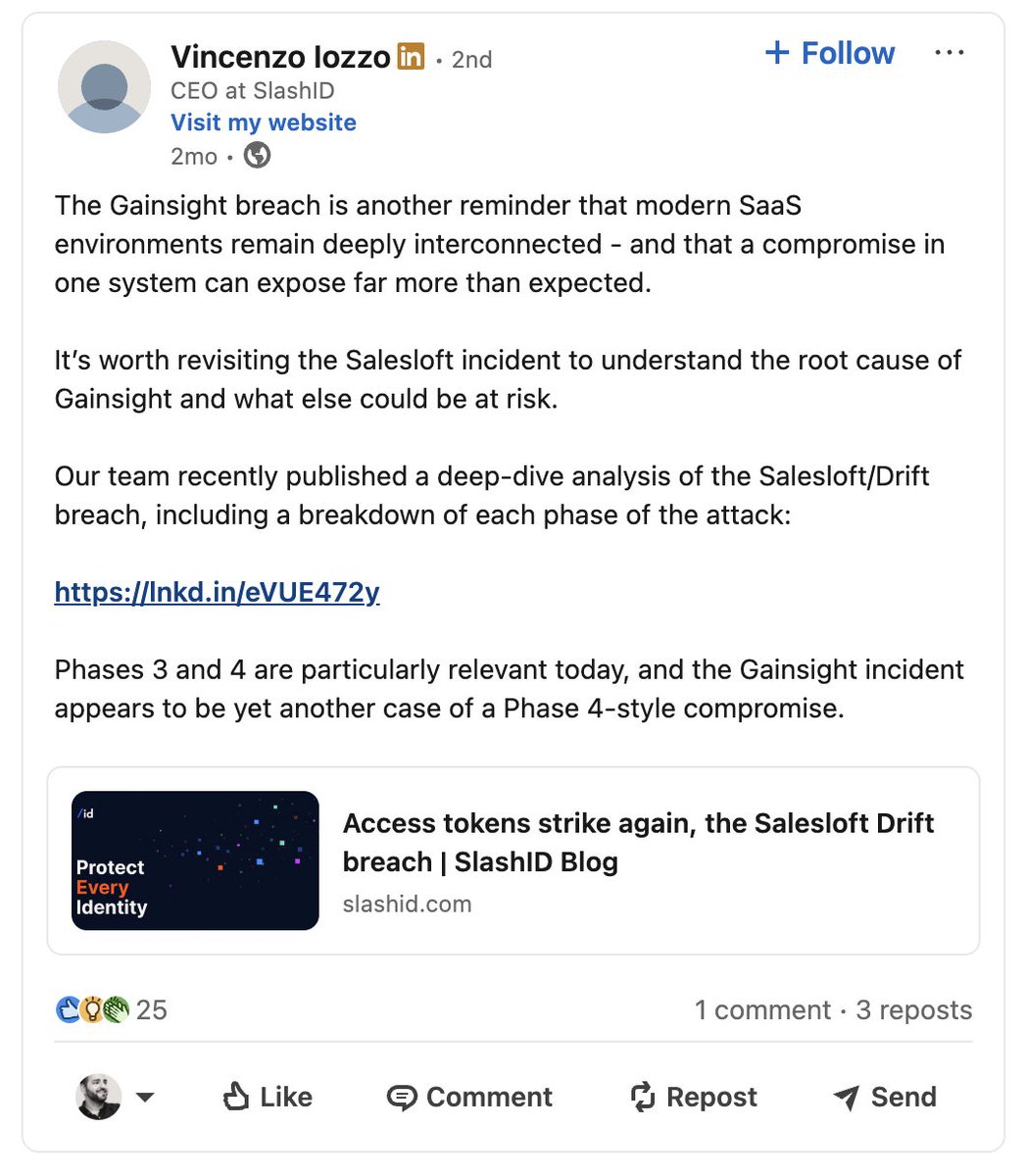
 In March through June 2025, the threat actor accessed the Salesloft GitHub account. With this access, the threat actor was able to download content from multiple repositories, add a guest user and establish workflows.
In March through June 2025, the threat actor accessed the Salesloft GitHub account. With this access, the threat actor was able to download content from multiple repositories, add a guest user and establish workflows.

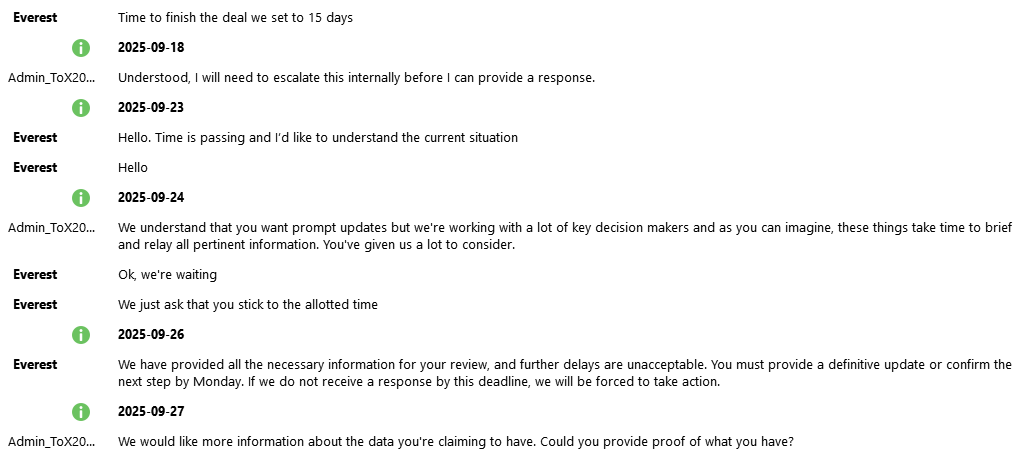
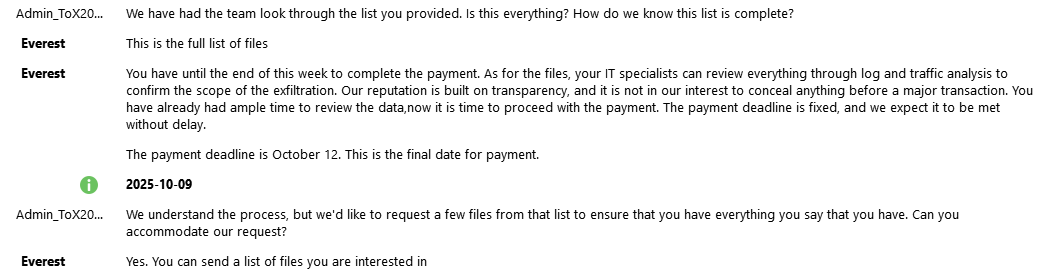
 We're unaccustomed to seeing double or triple extortion from ransomware gangs, as it undermines their business model. Moreover, Nova misrepresented their reasons for demanding more, making them (surprise) an unreliable party.
We're unaccustomed to seeing double or triple extortion from ransomware gangs, as it undermines their business model. Moreover, Nova misrepresented their reasons for demanding more, making them (surprise) an unreliable party.

 1/ Is this really bad for @SchneiderElec? We don't know yet. We've had contact with Hellcat spokesperson @holypryx, he told us 'Today we are leaking everything so samples won't be important anymore right?'
1/ Is this really bad for @SchneiderElec? We don't know yet. We've had contact with Hellcat spokesperson @holypryx, he told us 'Today we are leaking everything so samples won't be important anymore right?'