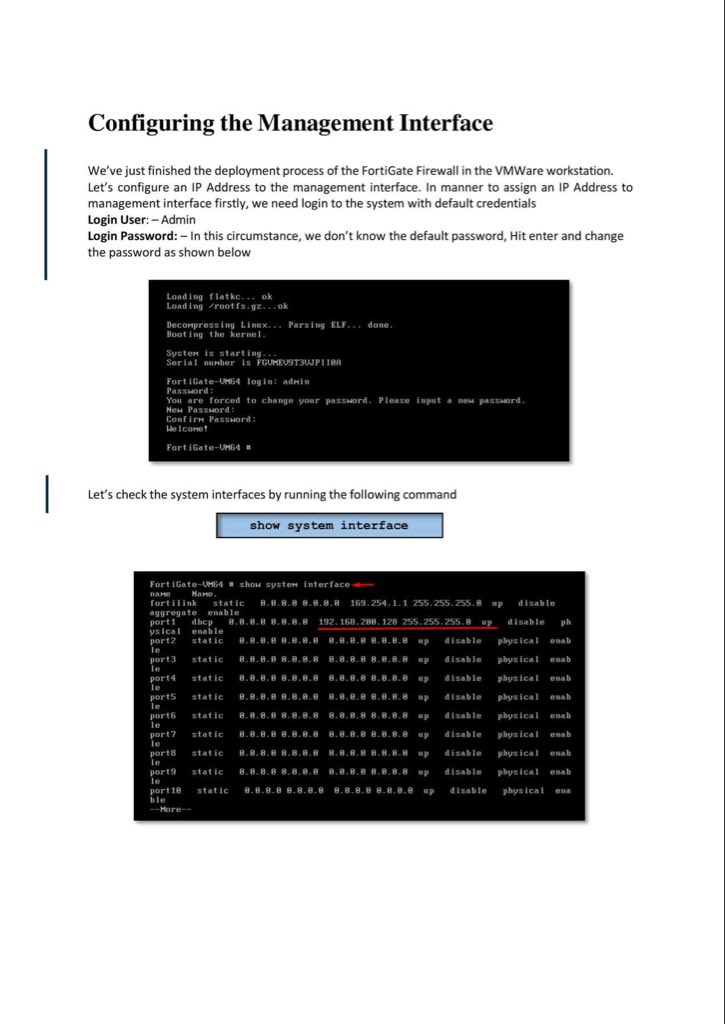
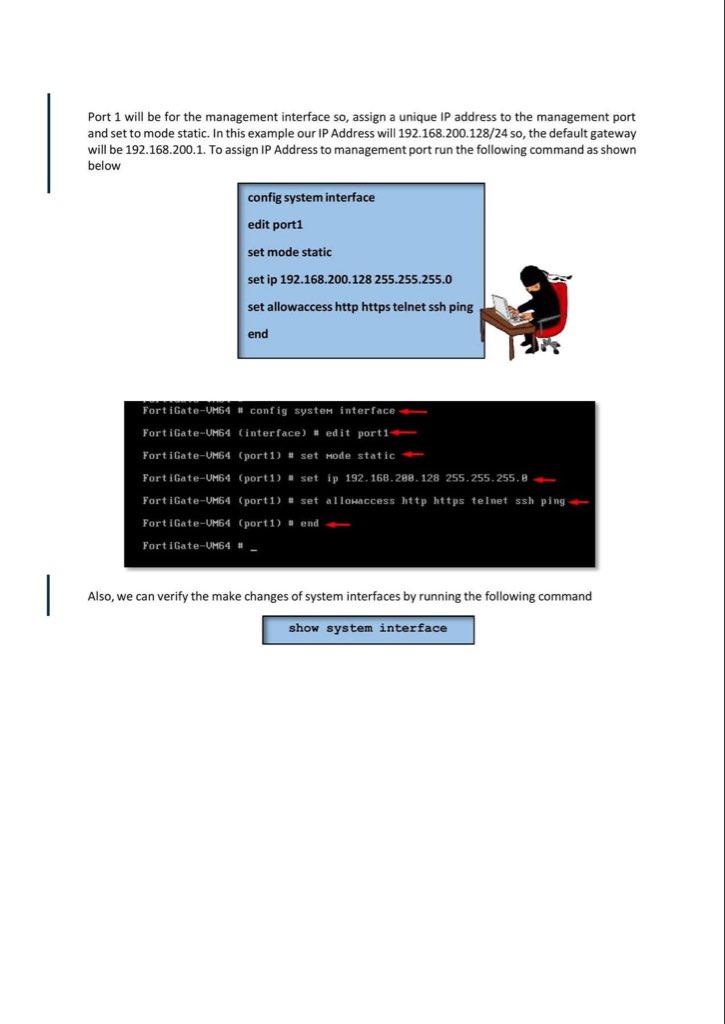
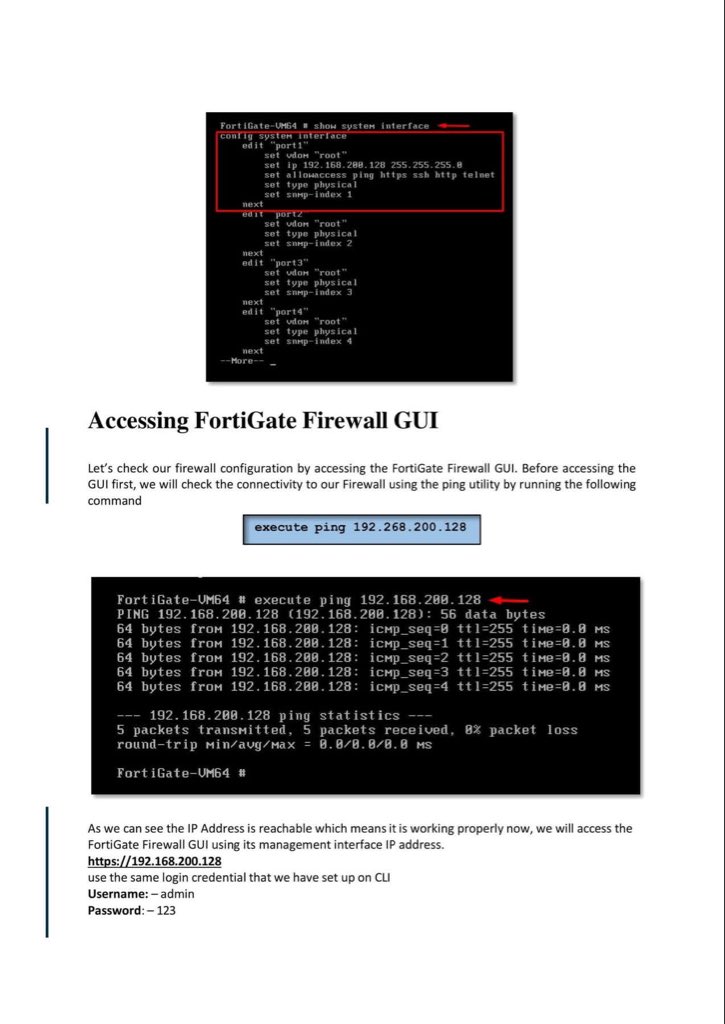
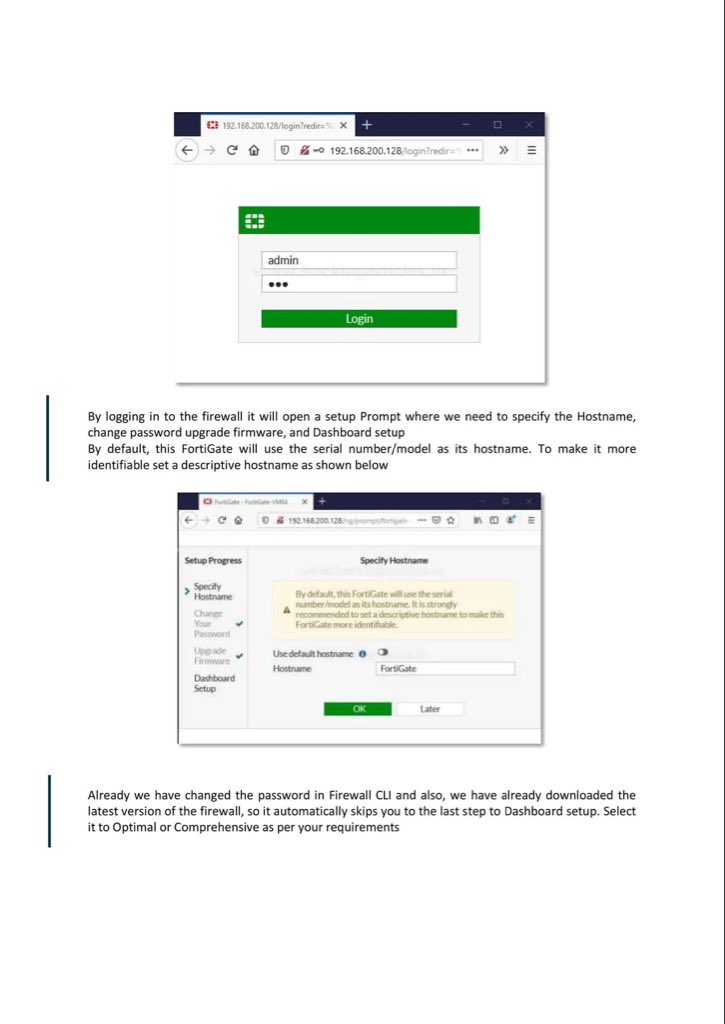
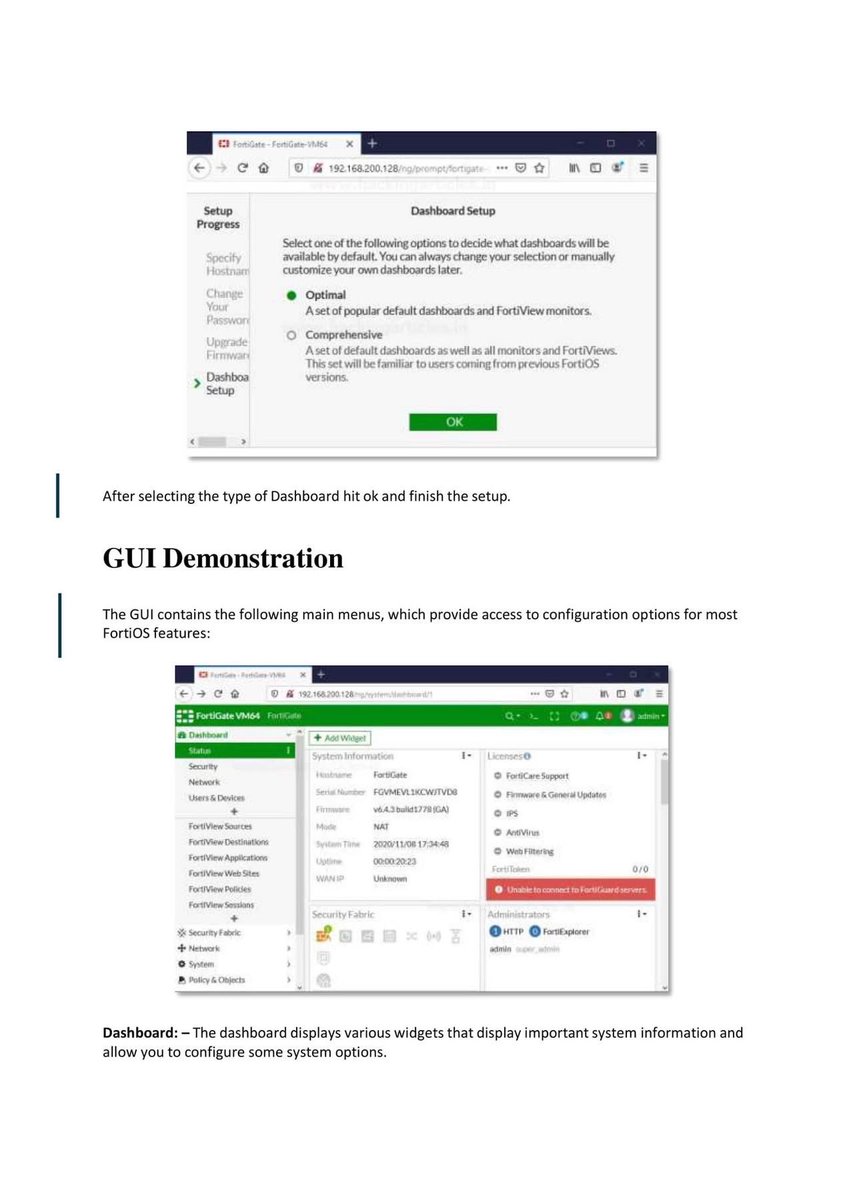
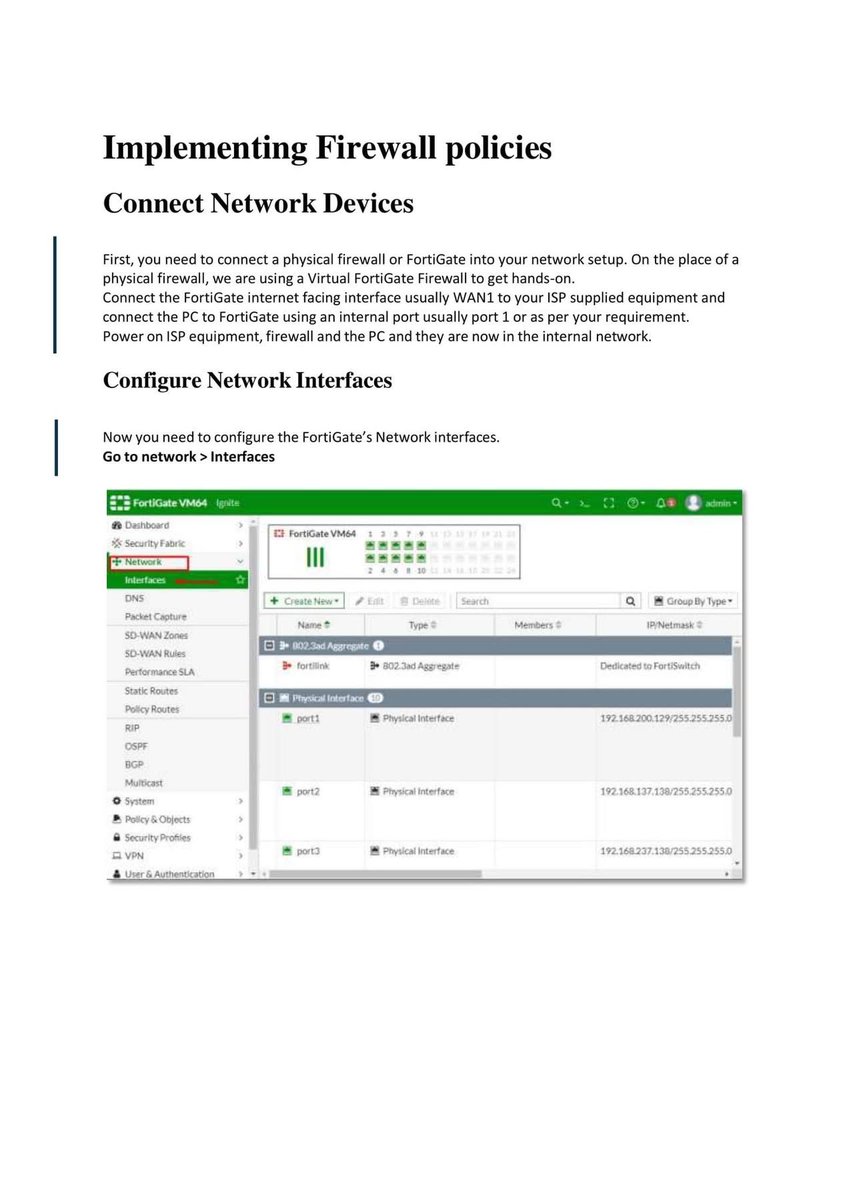
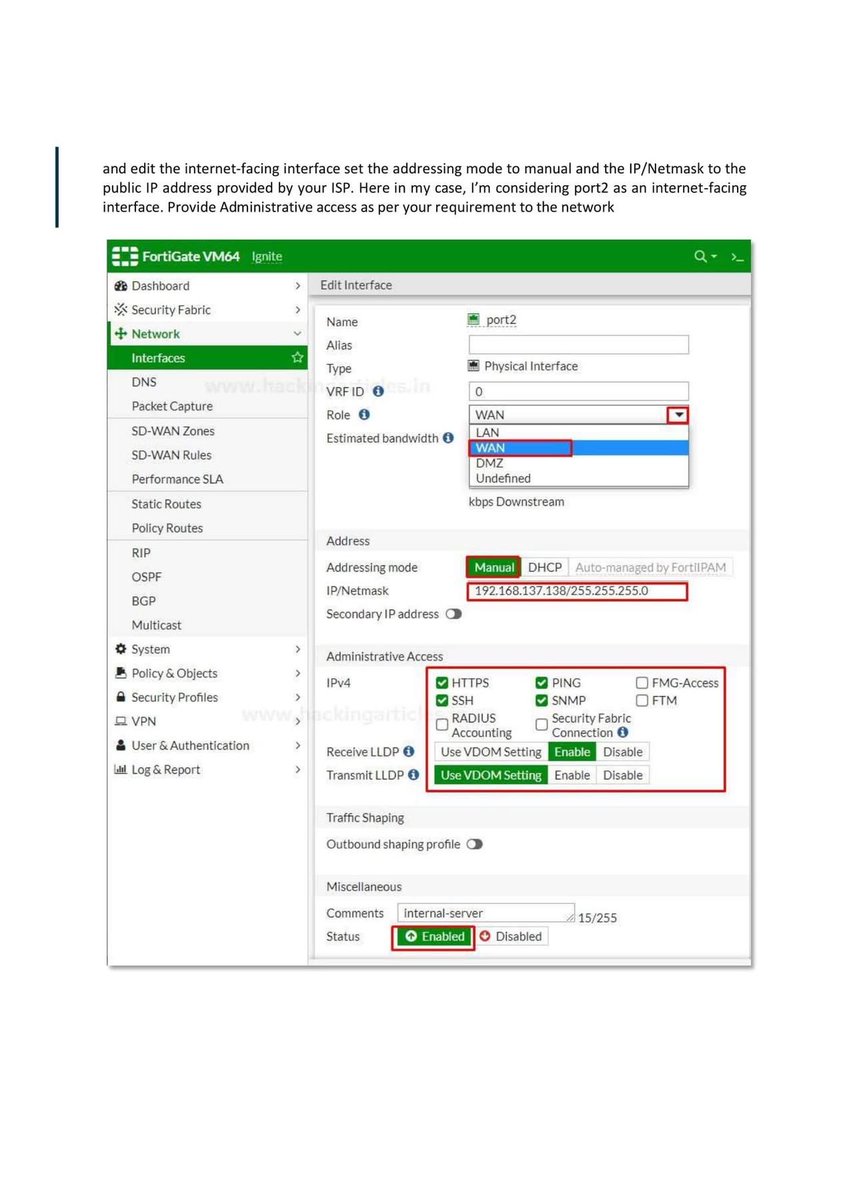
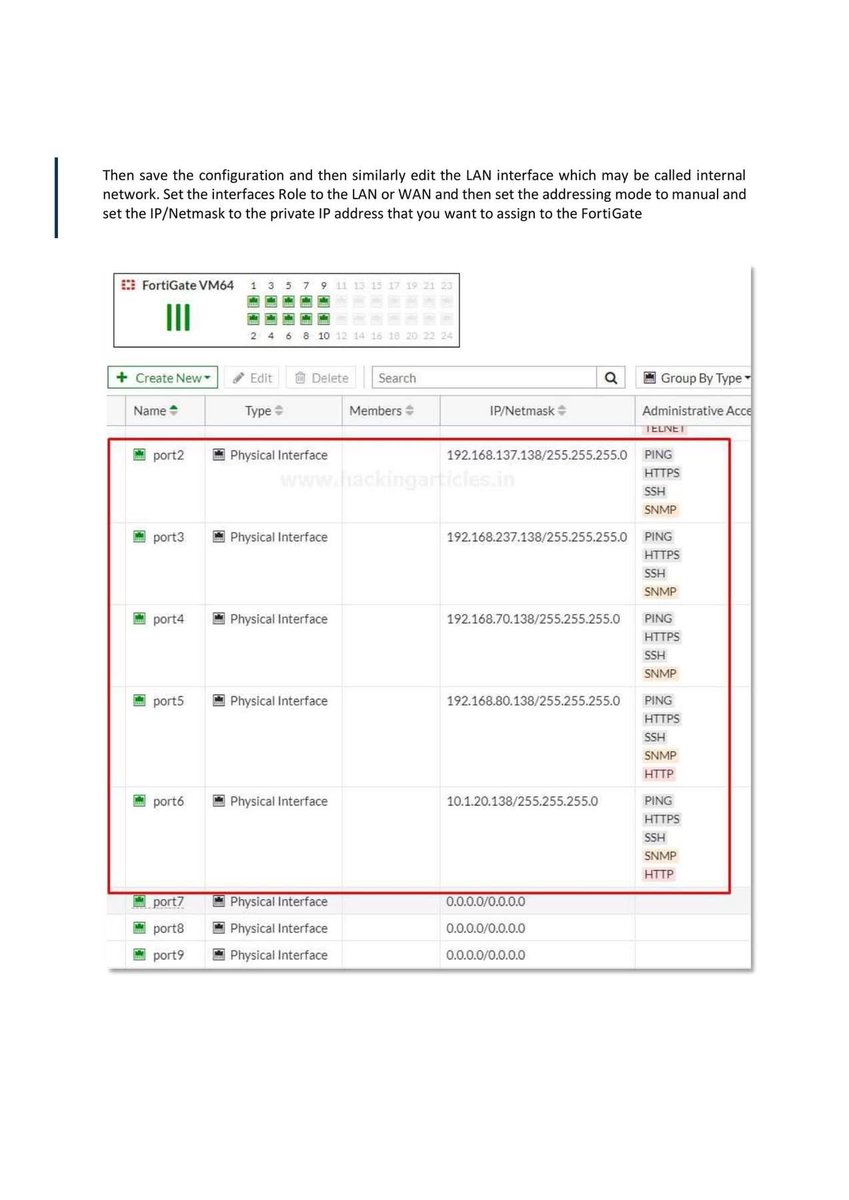
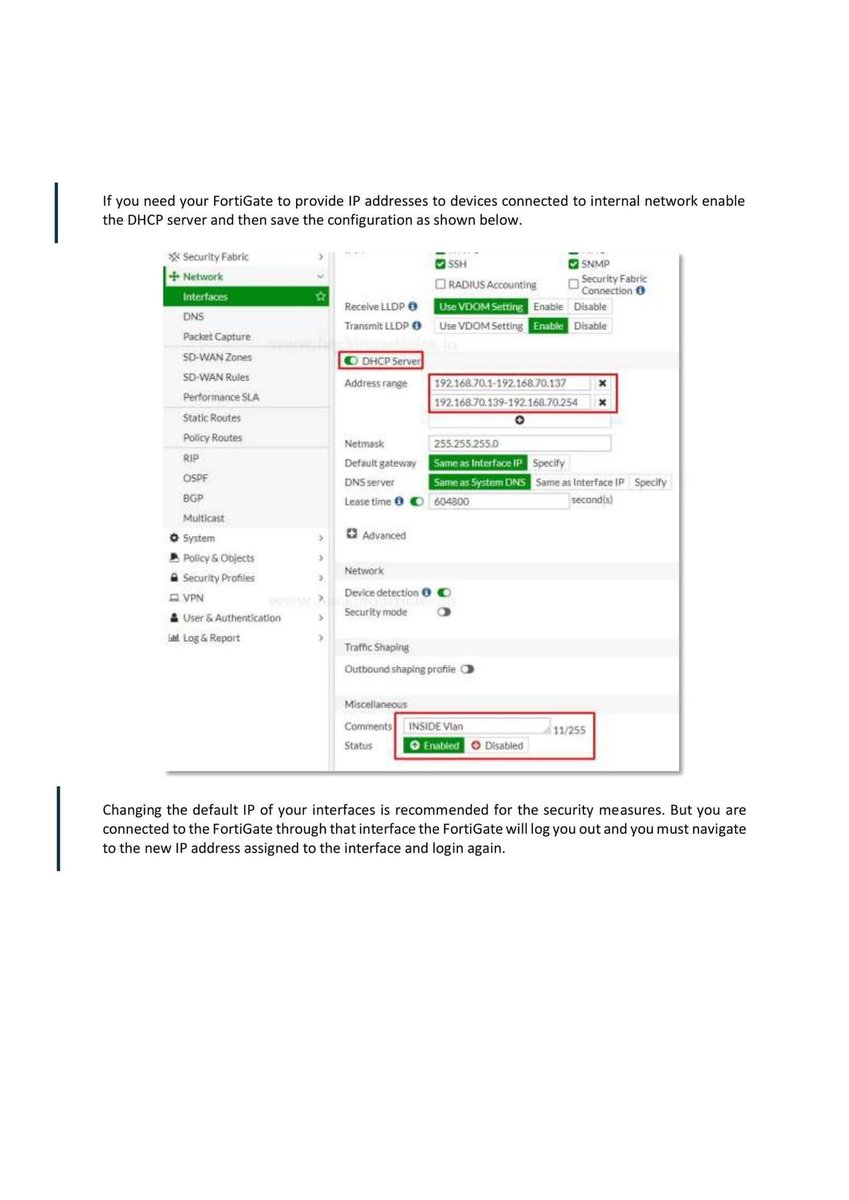
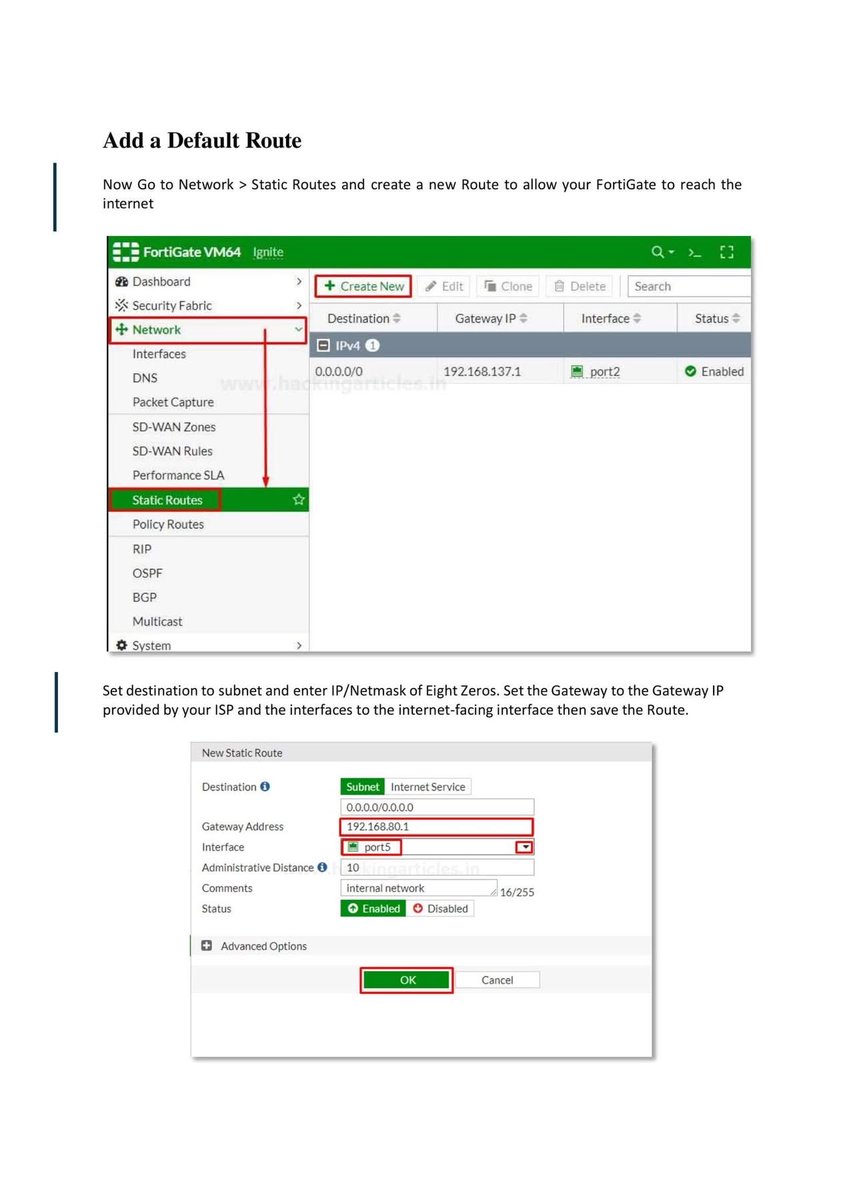
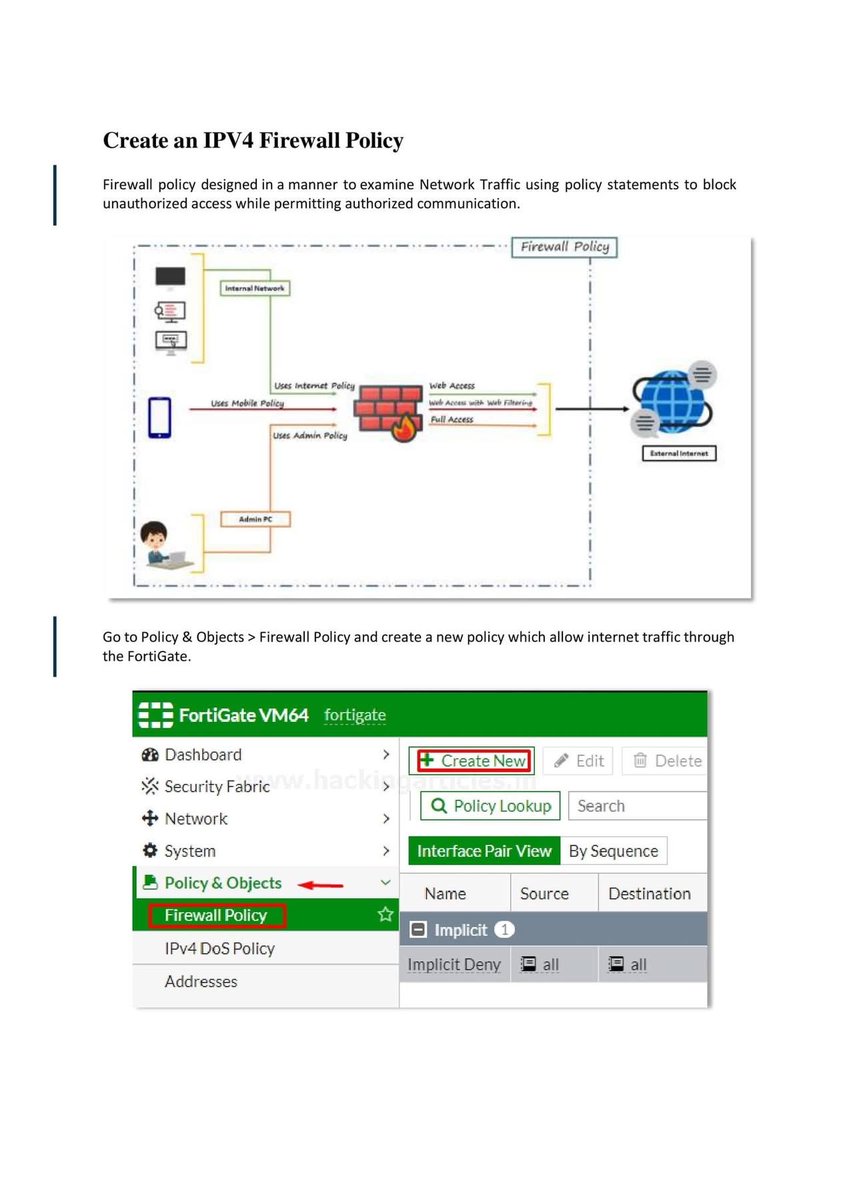
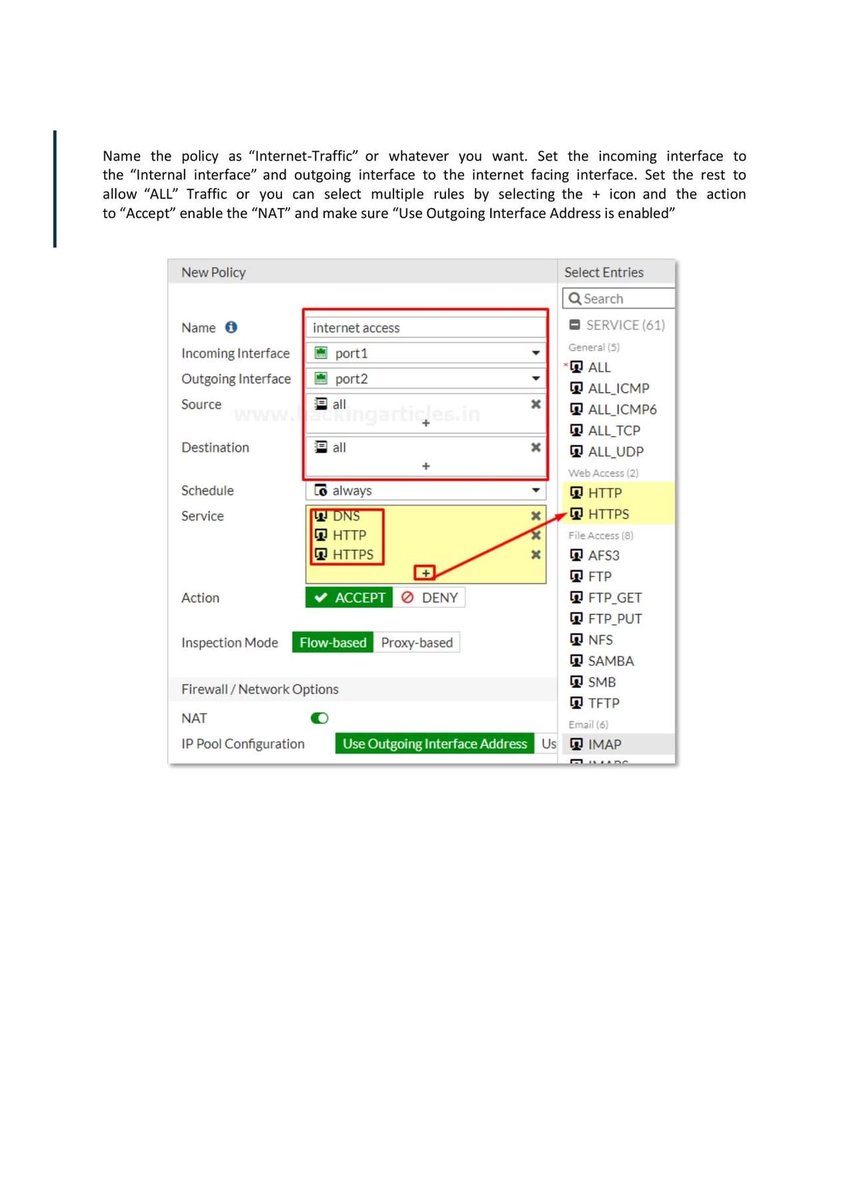
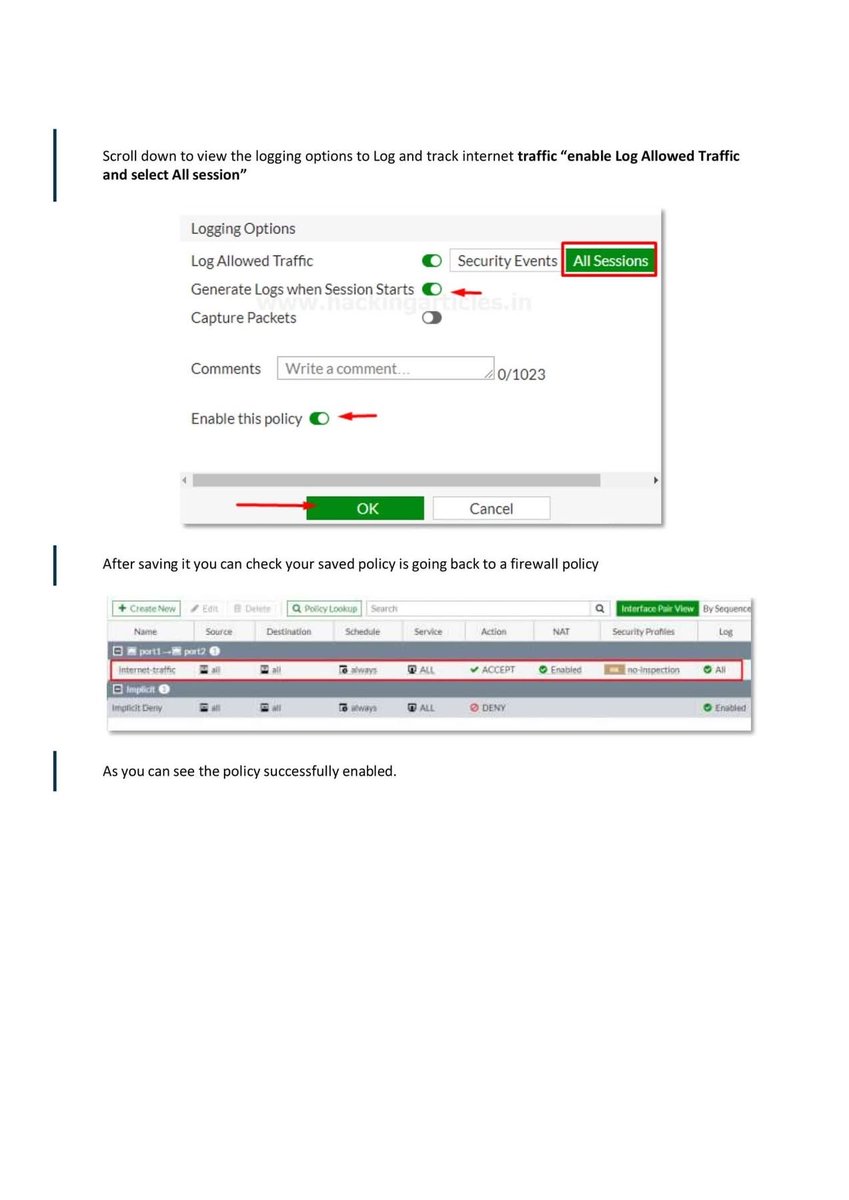
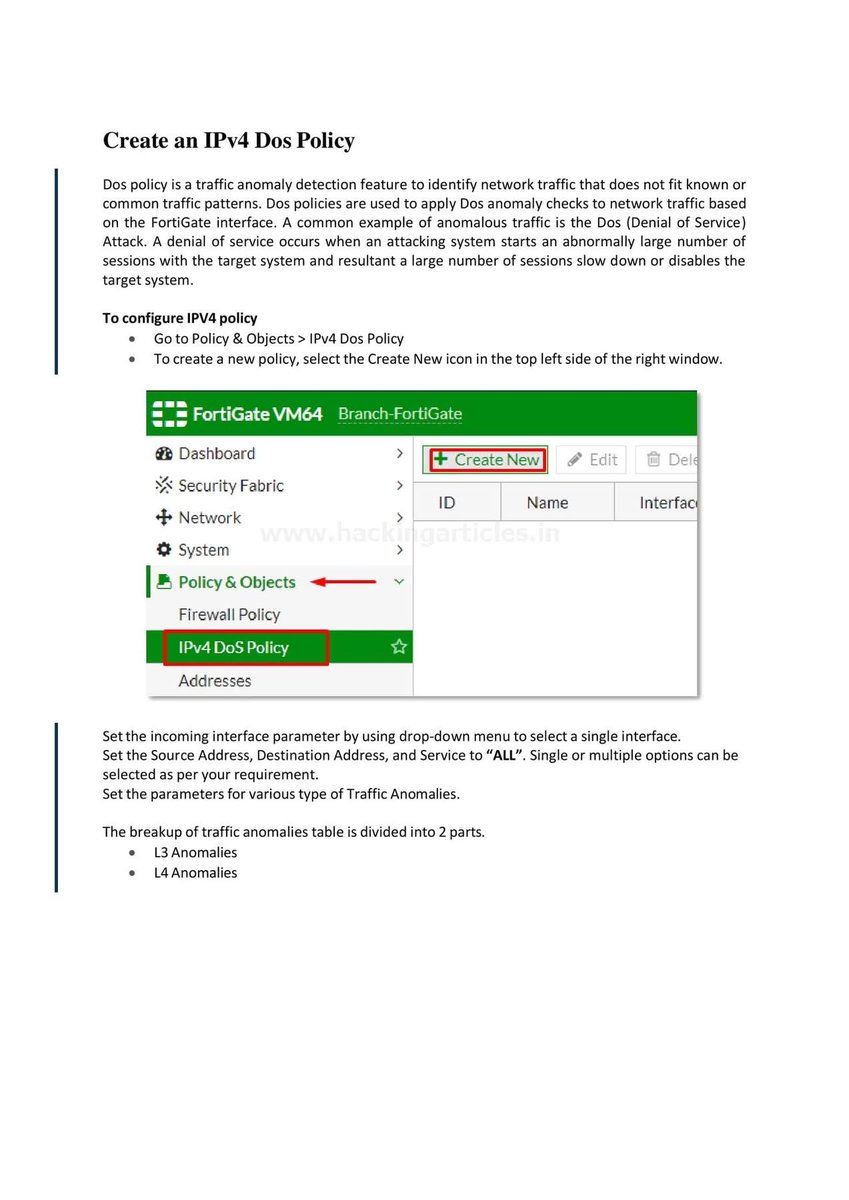
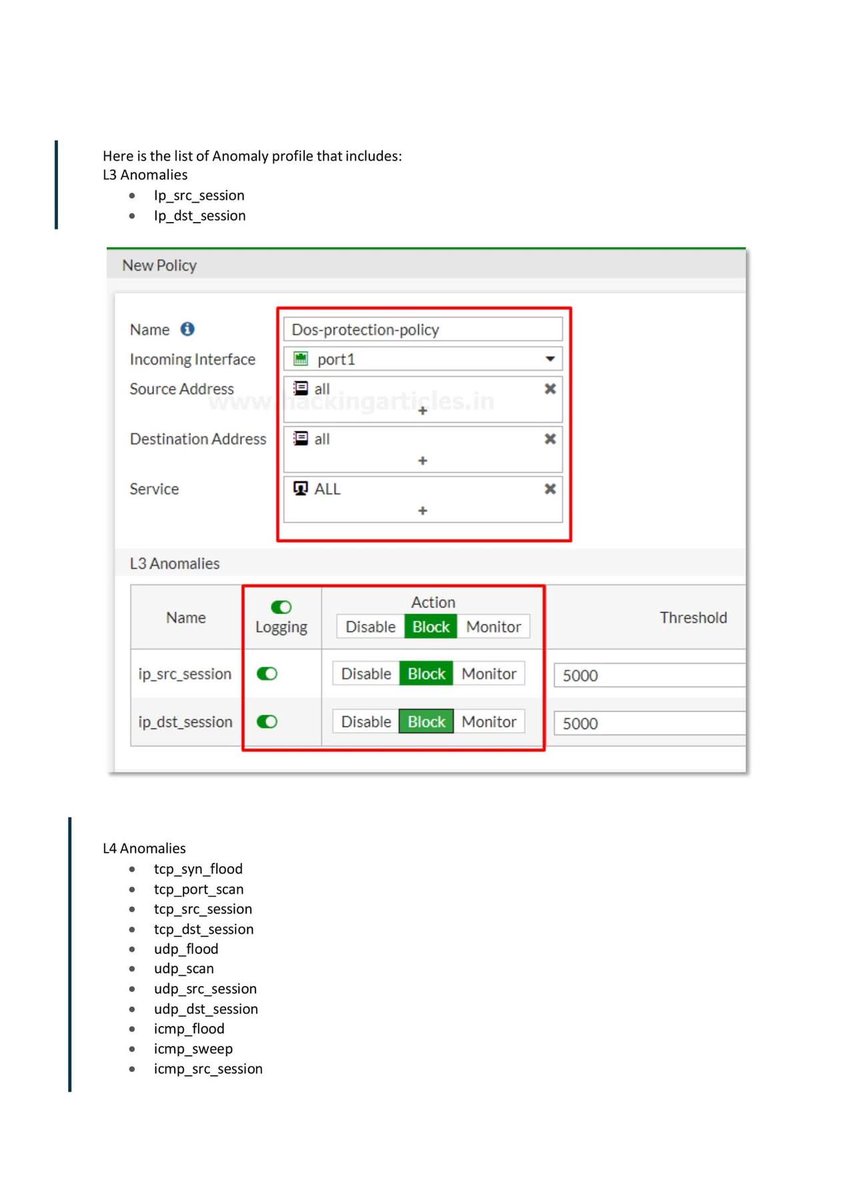
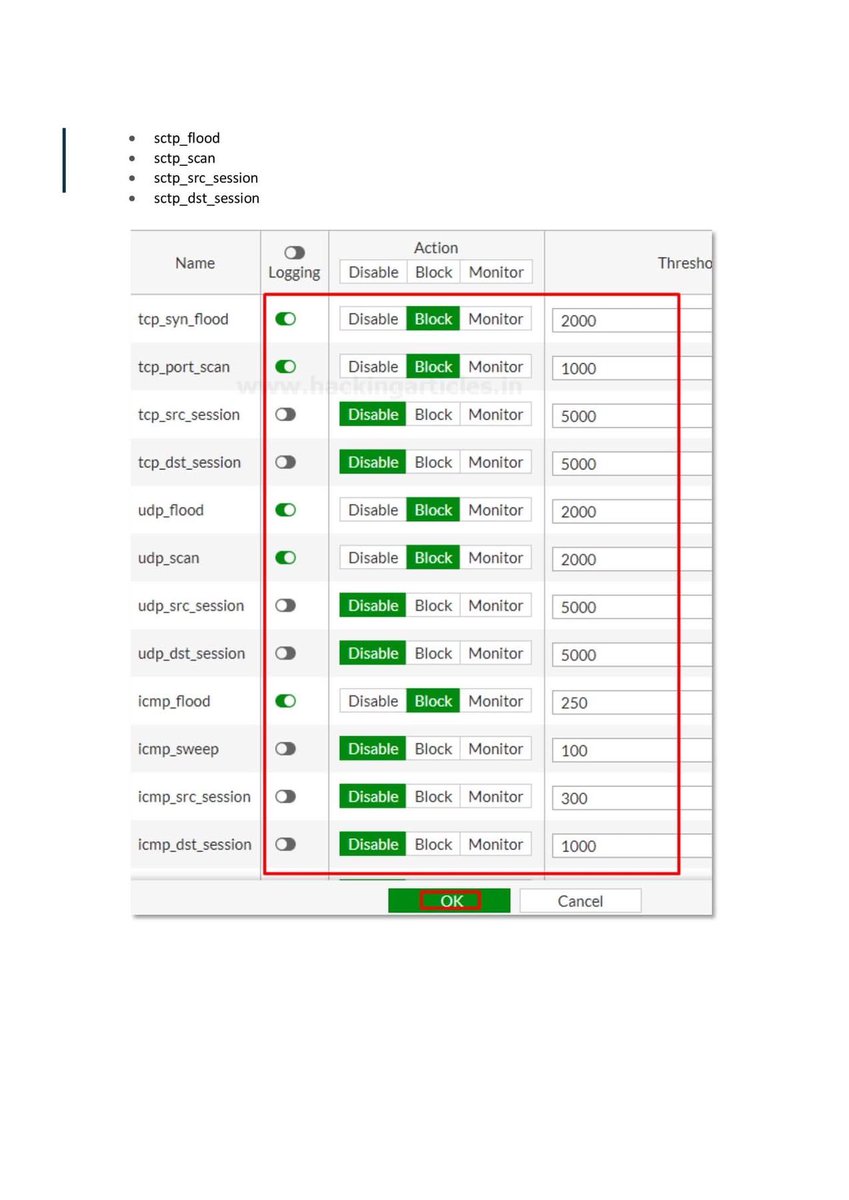
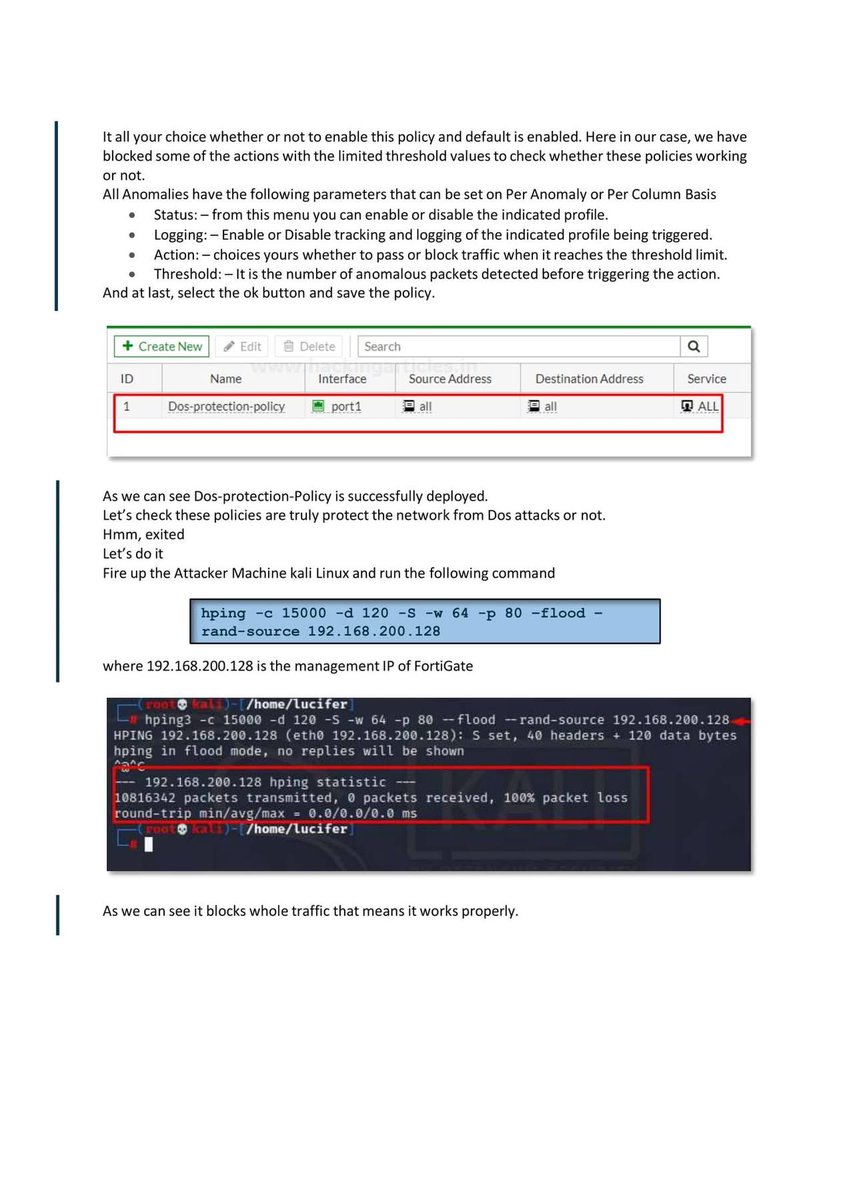
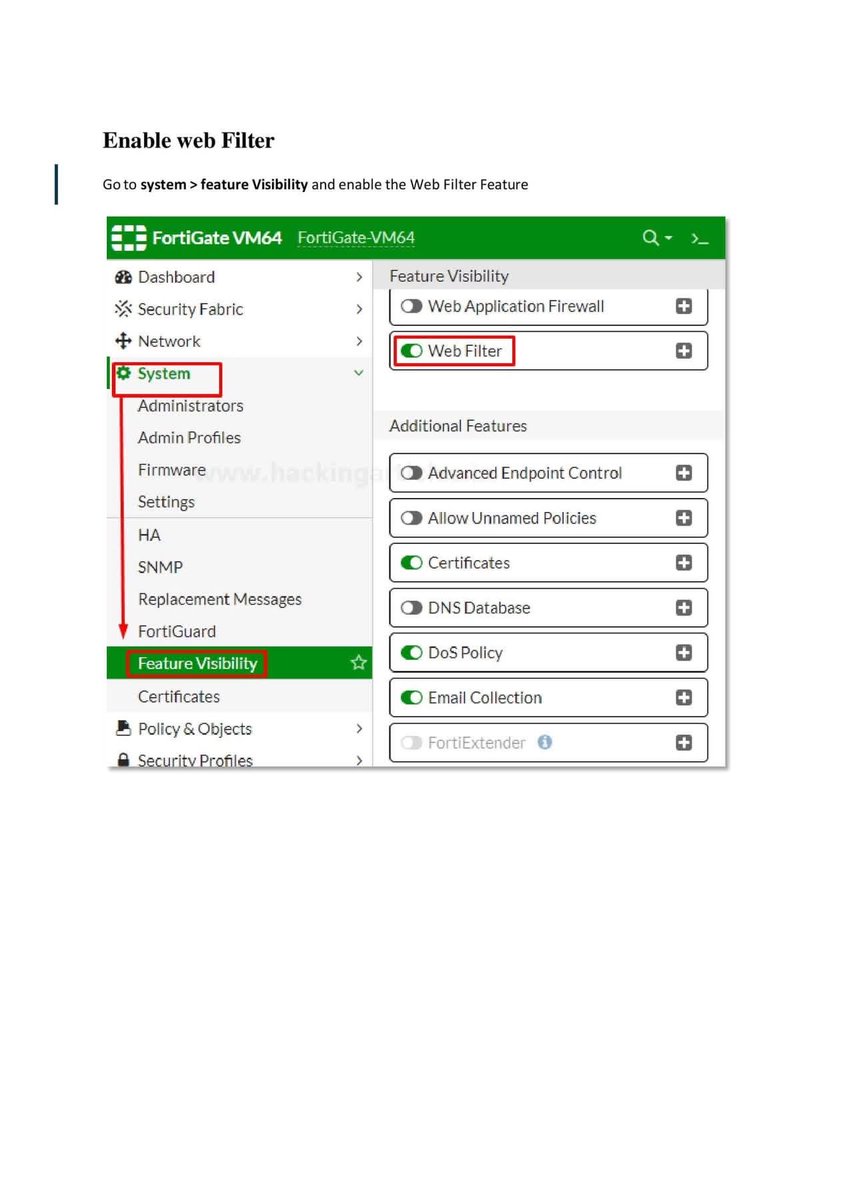
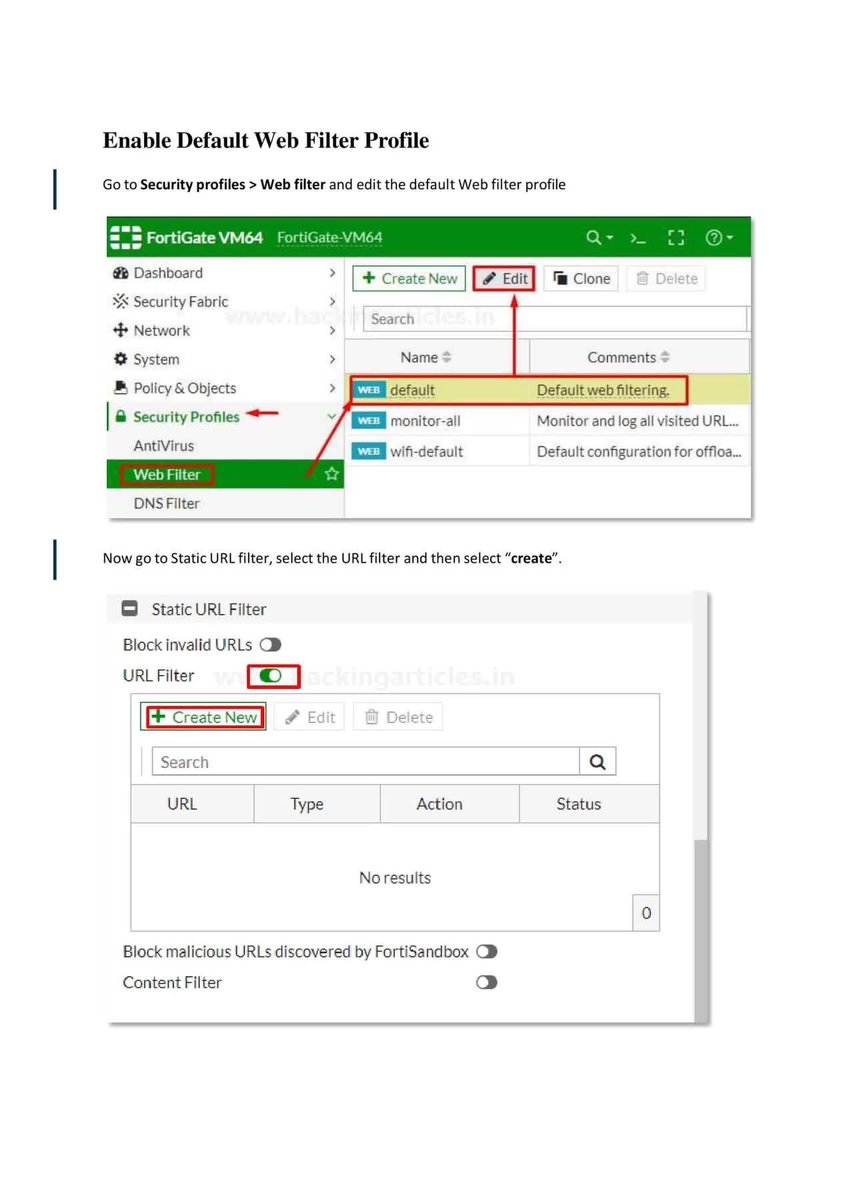
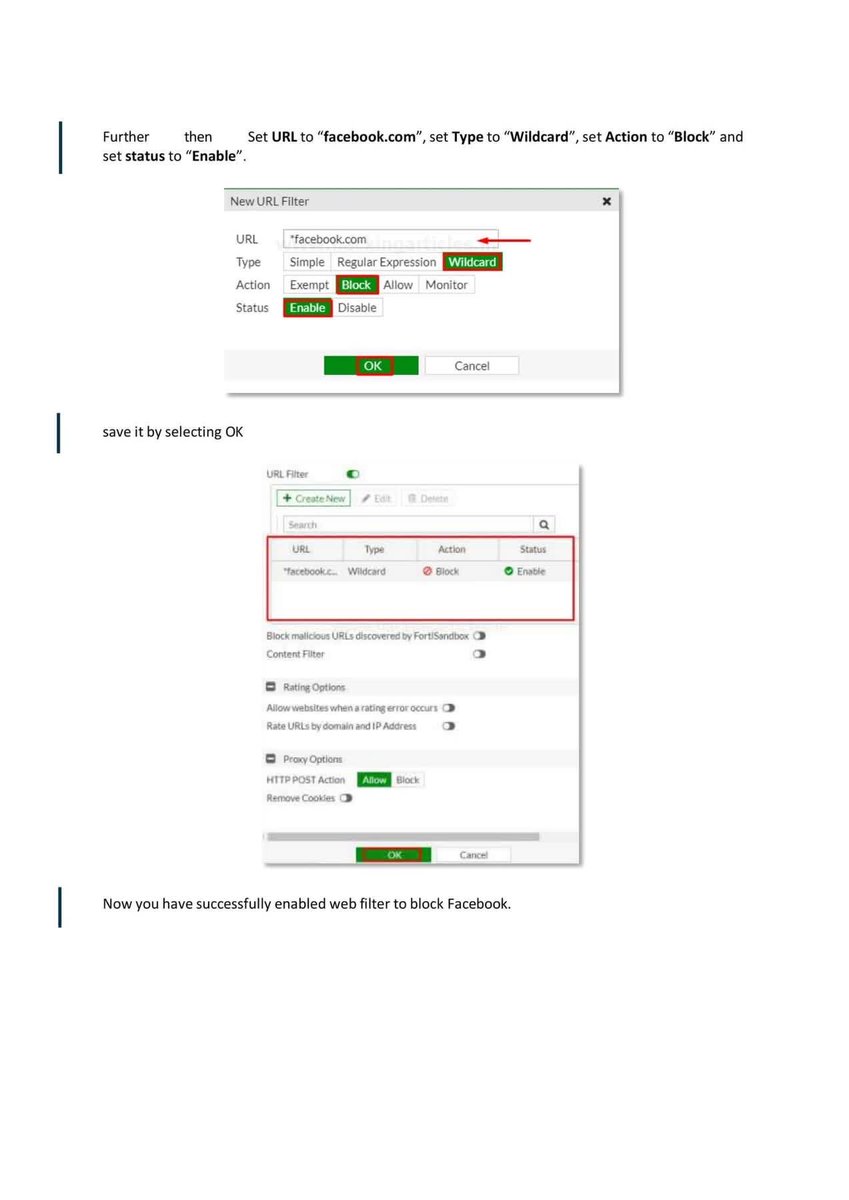
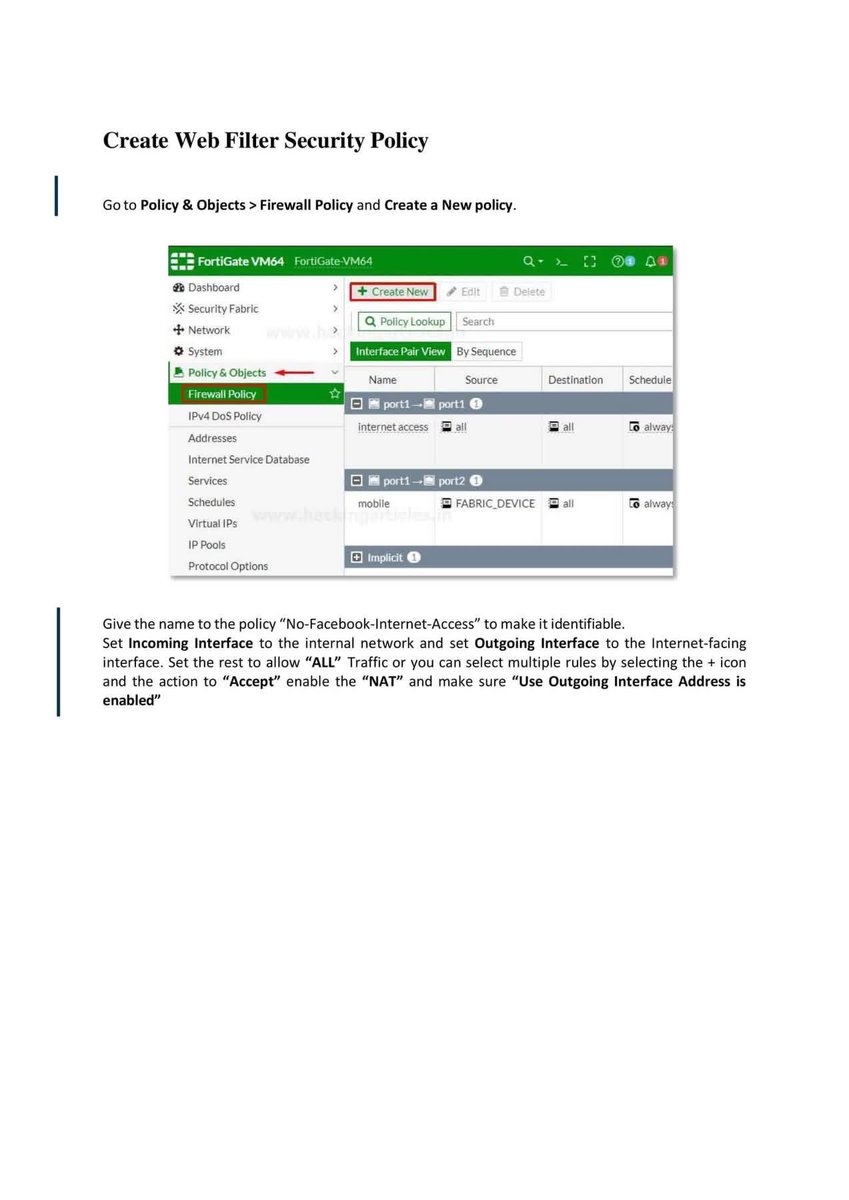
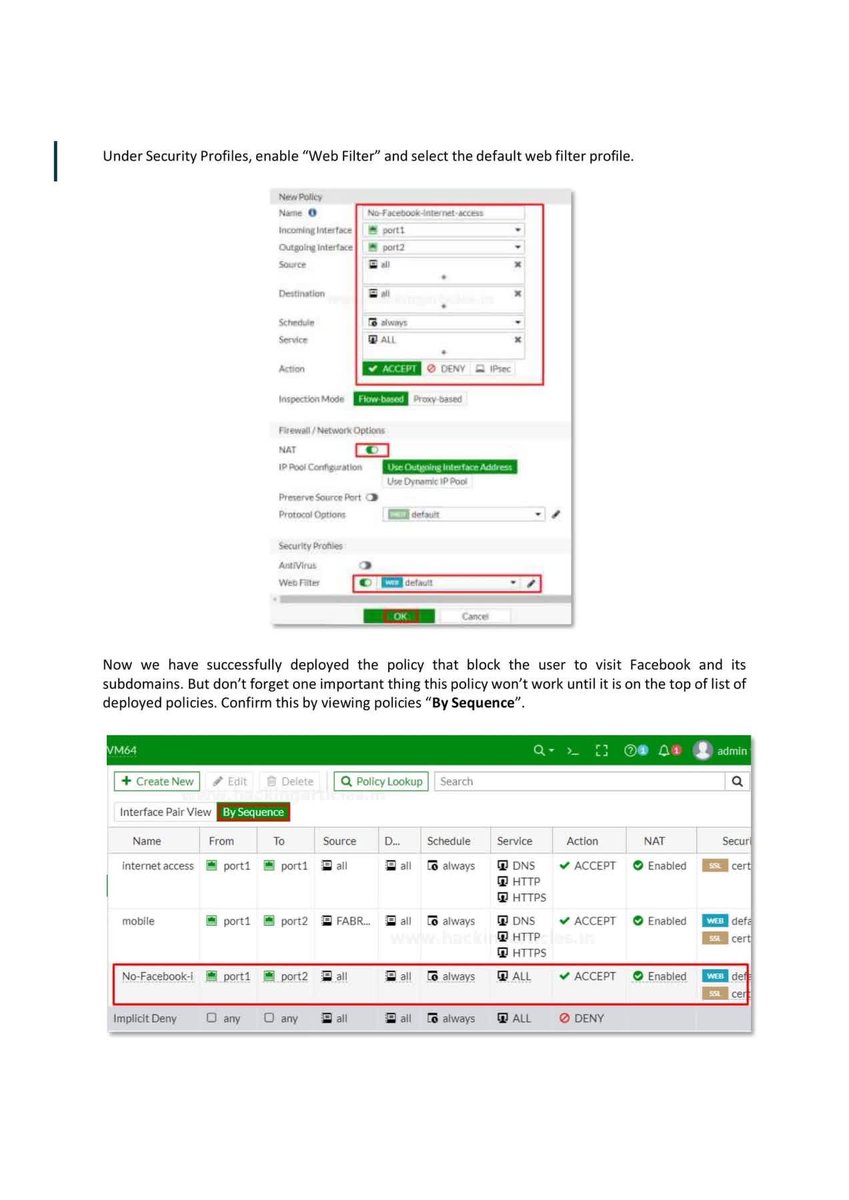
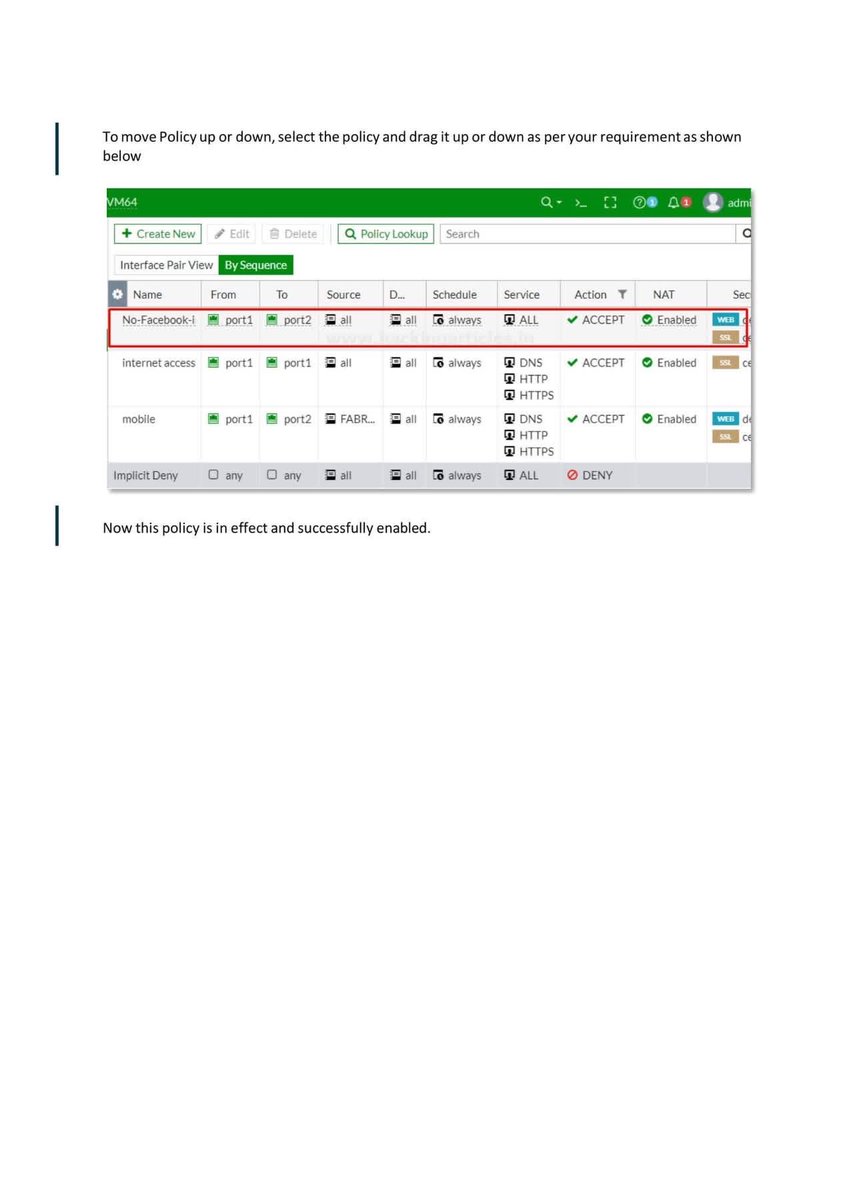
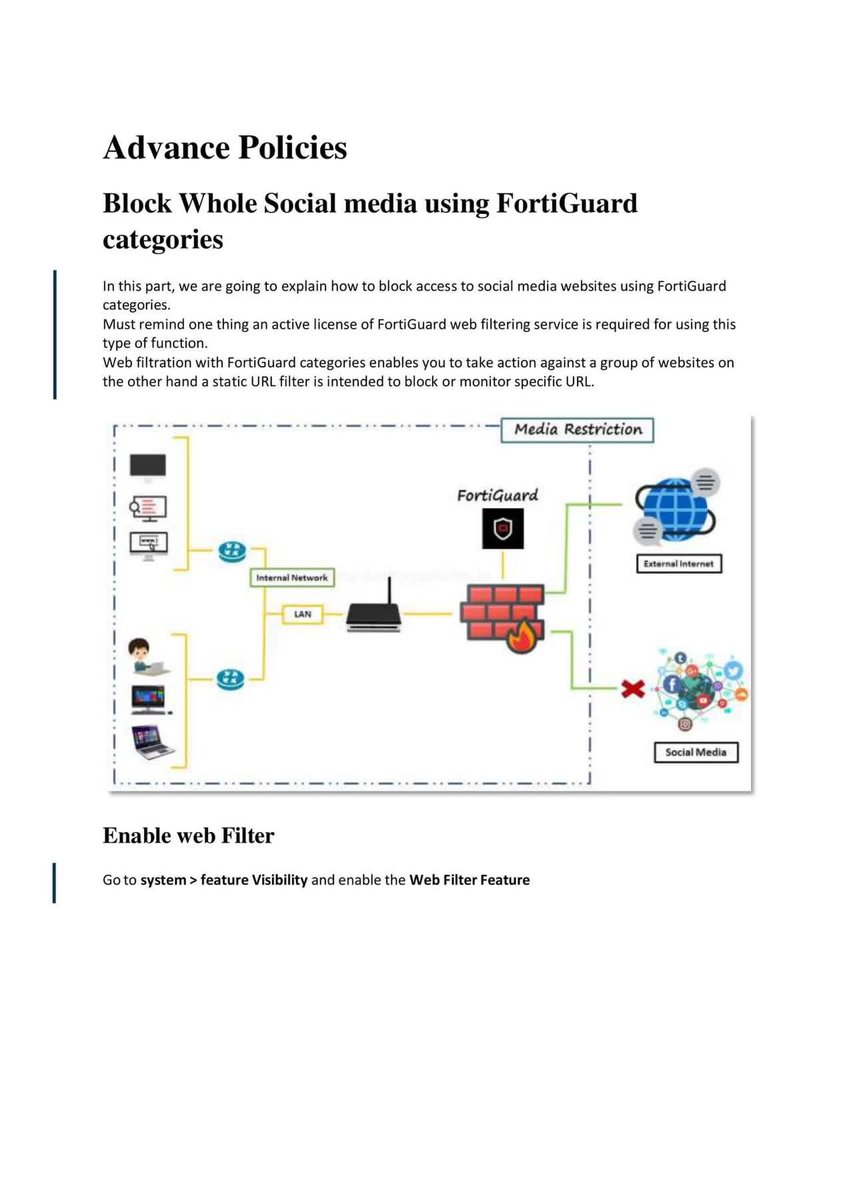
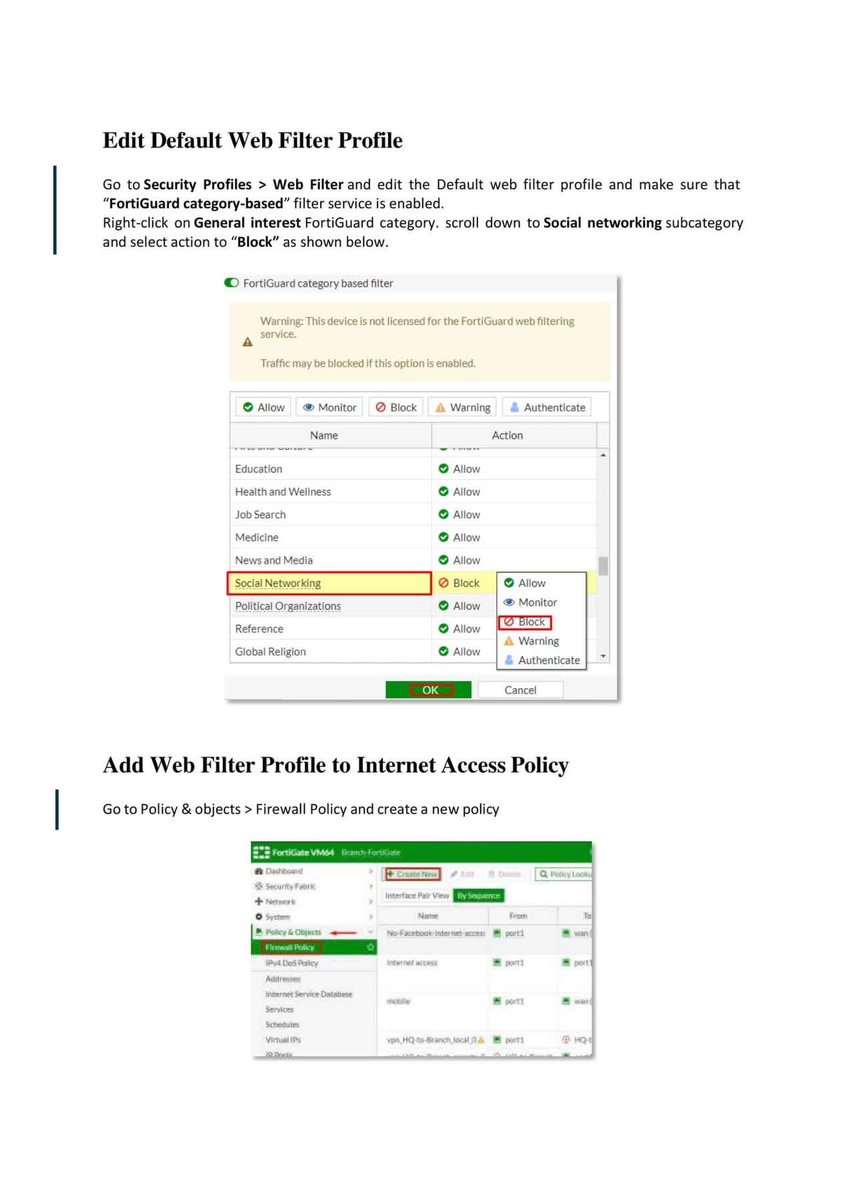
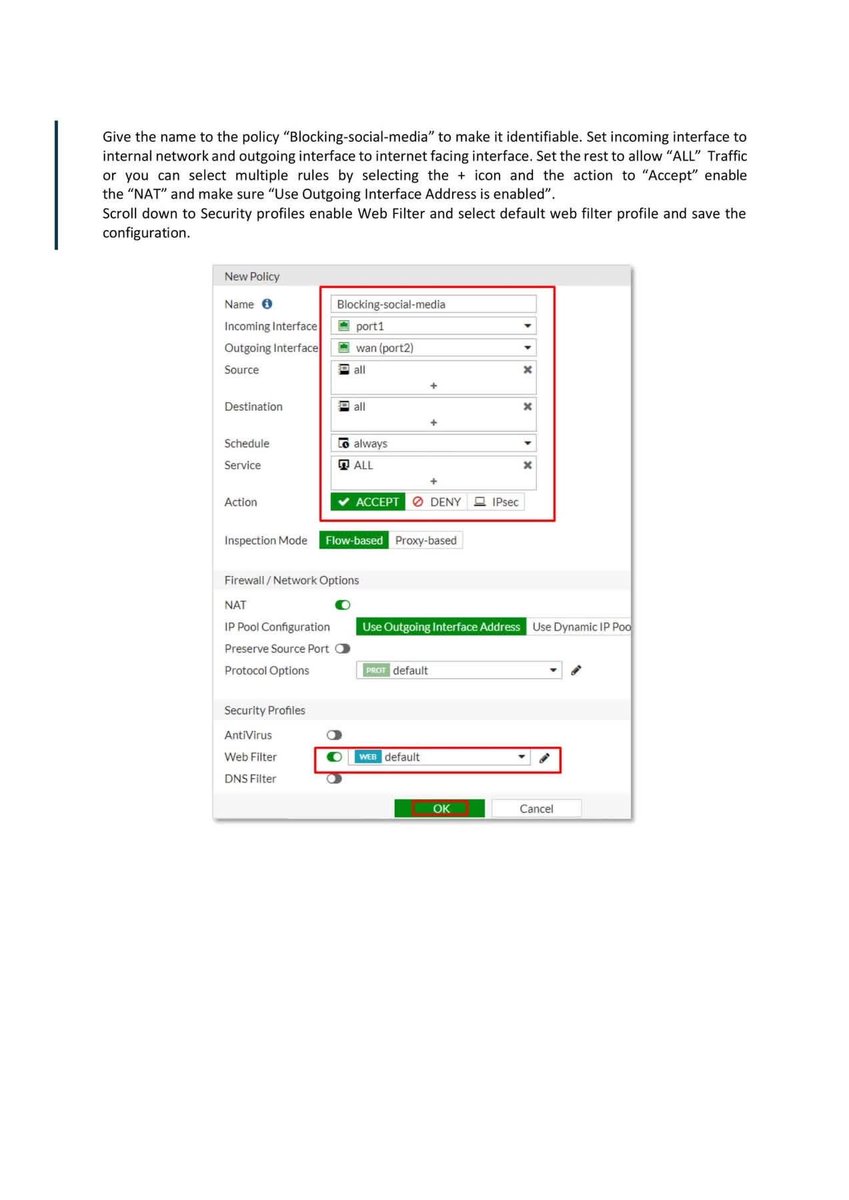
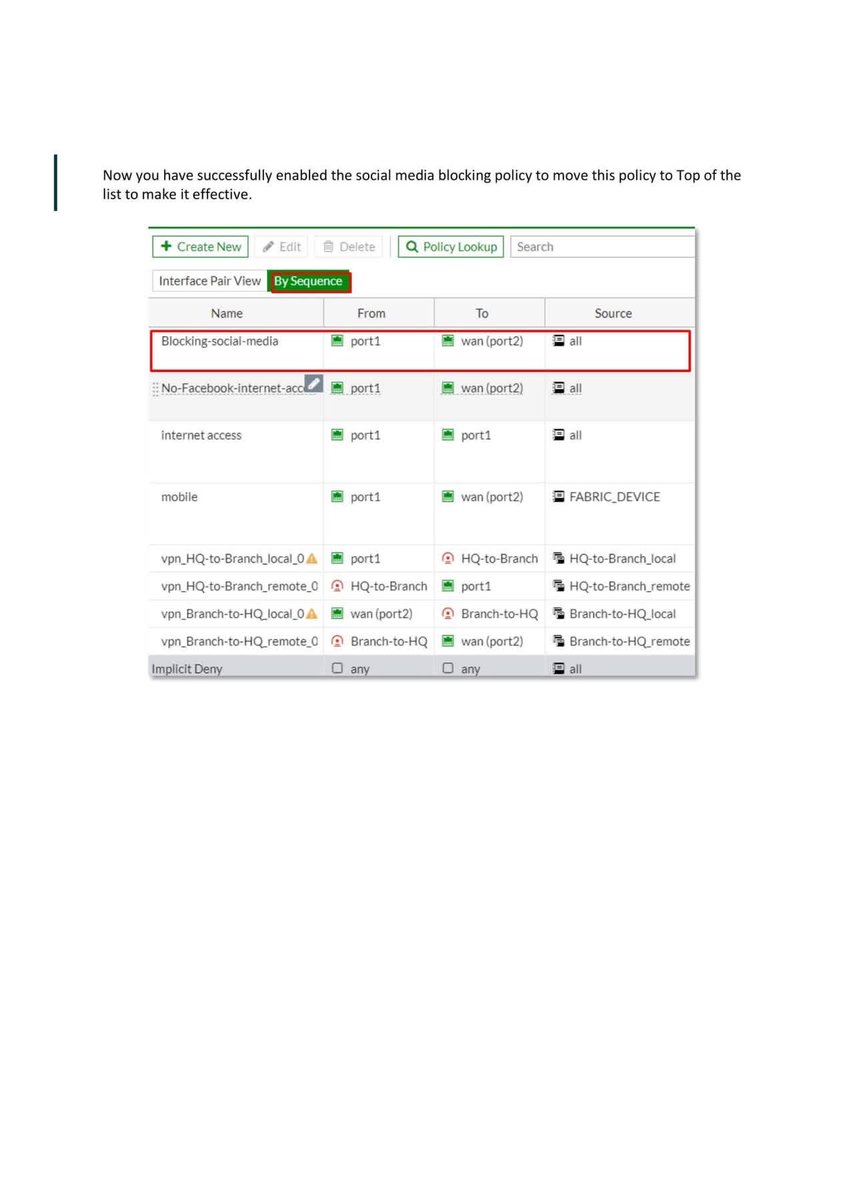
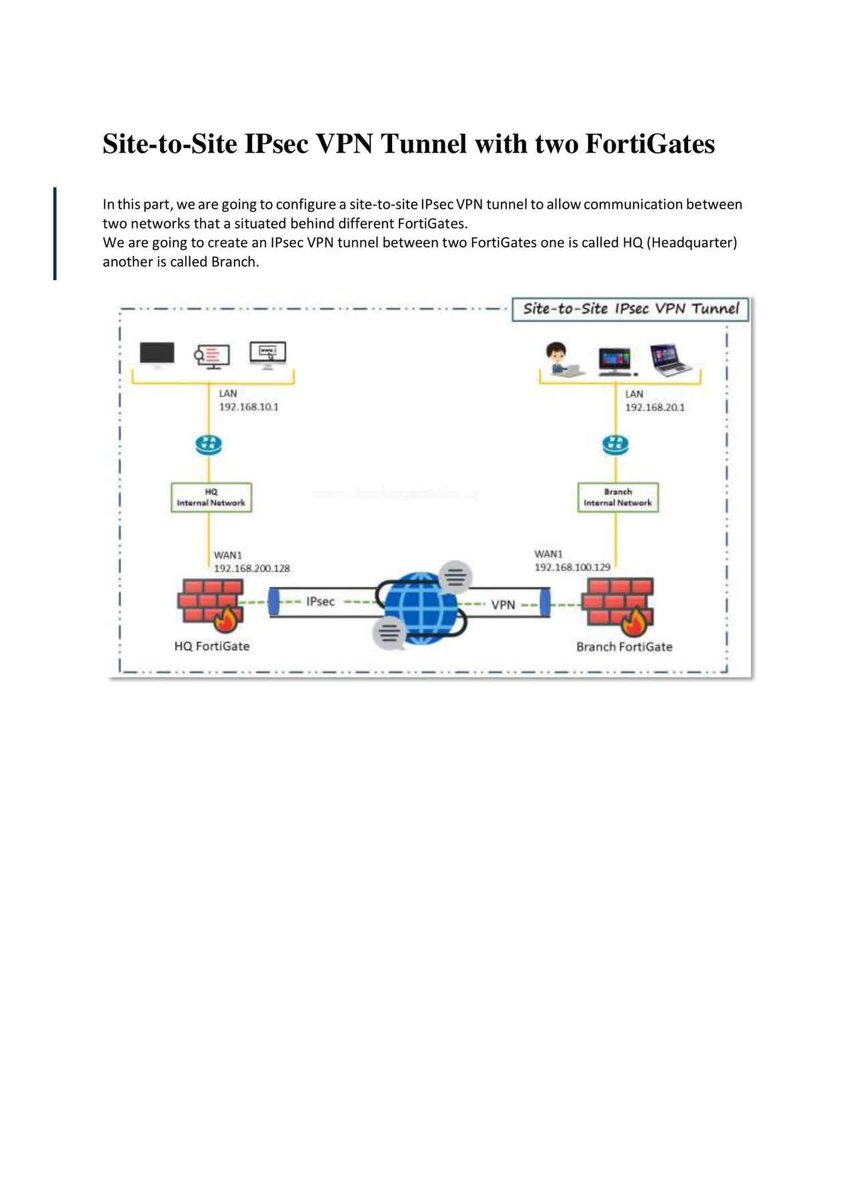
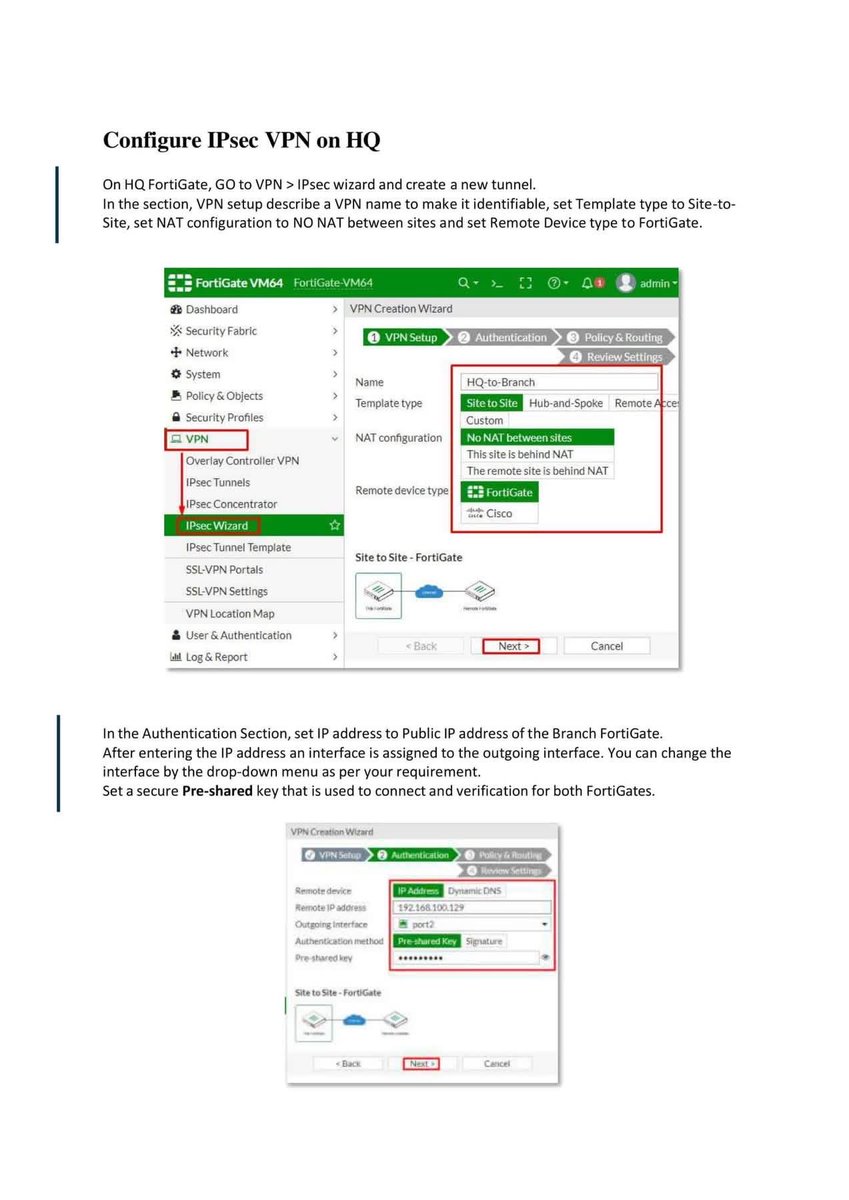
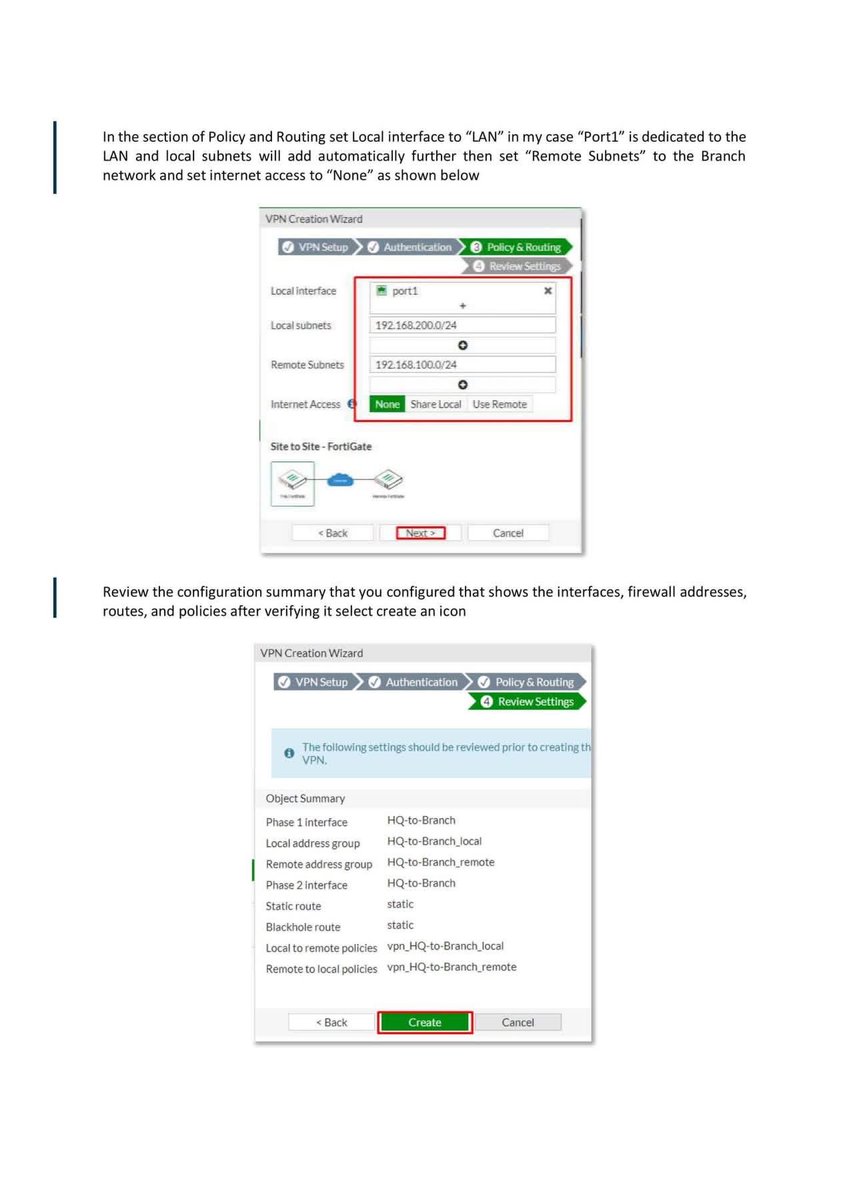
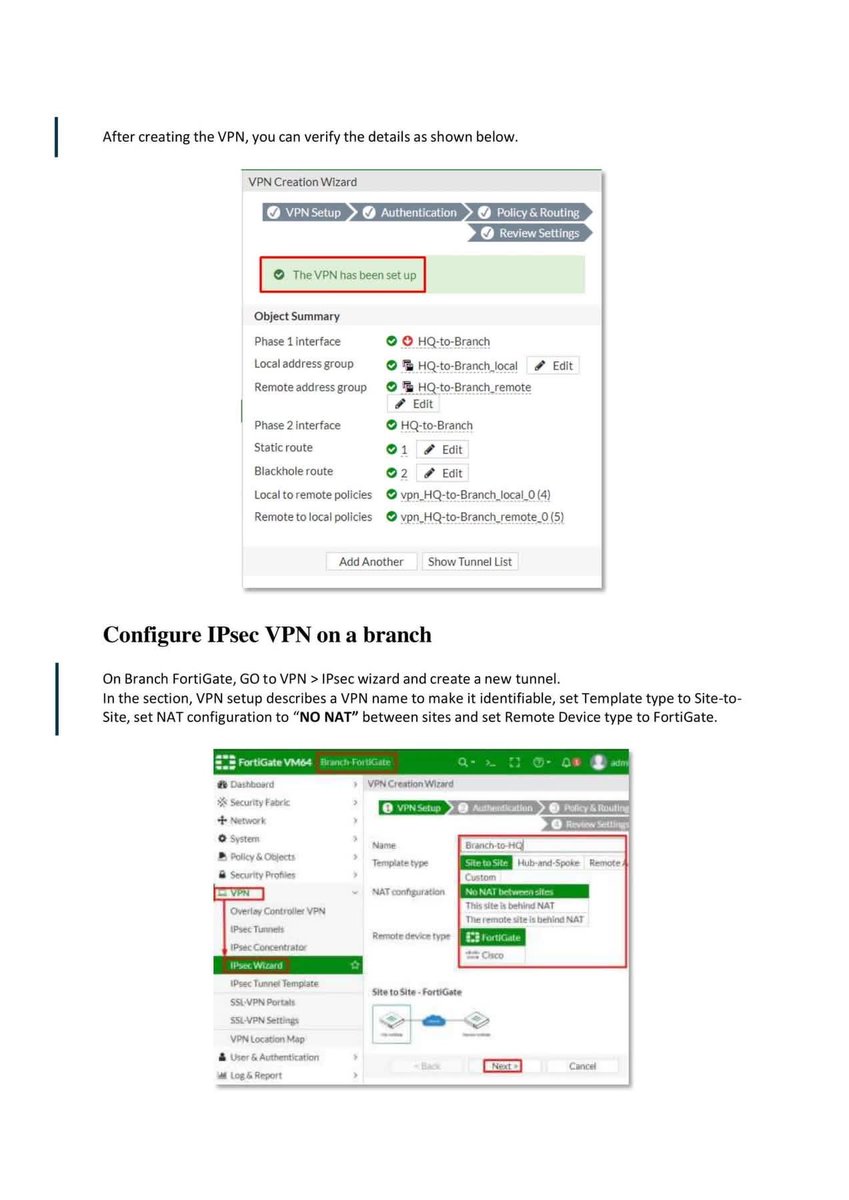
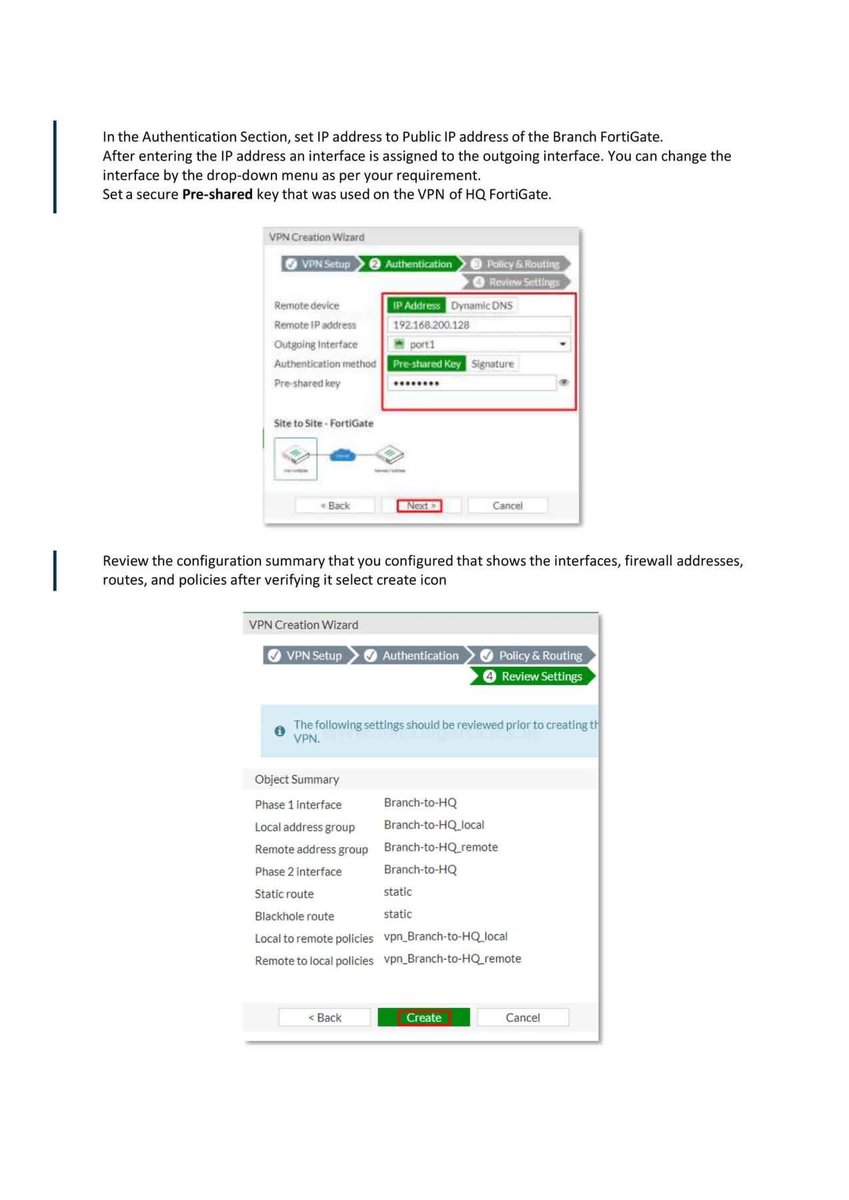
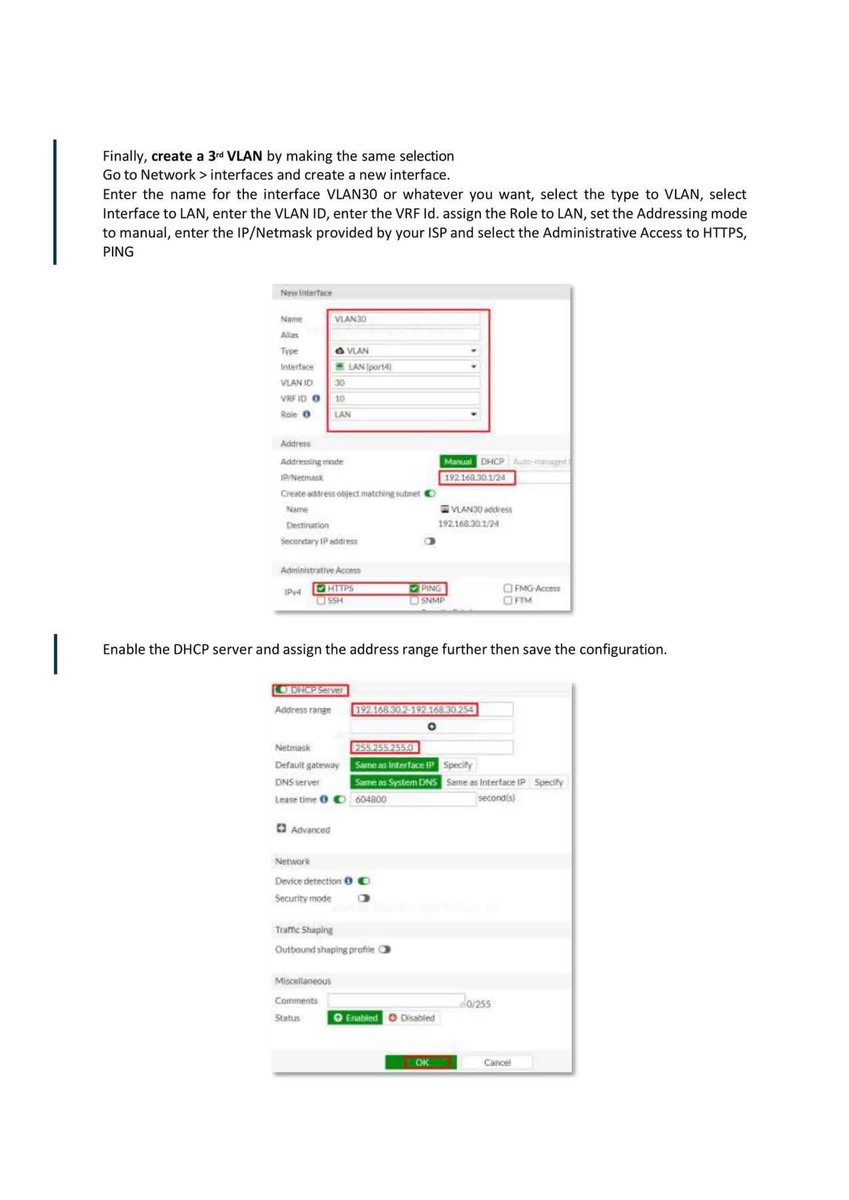
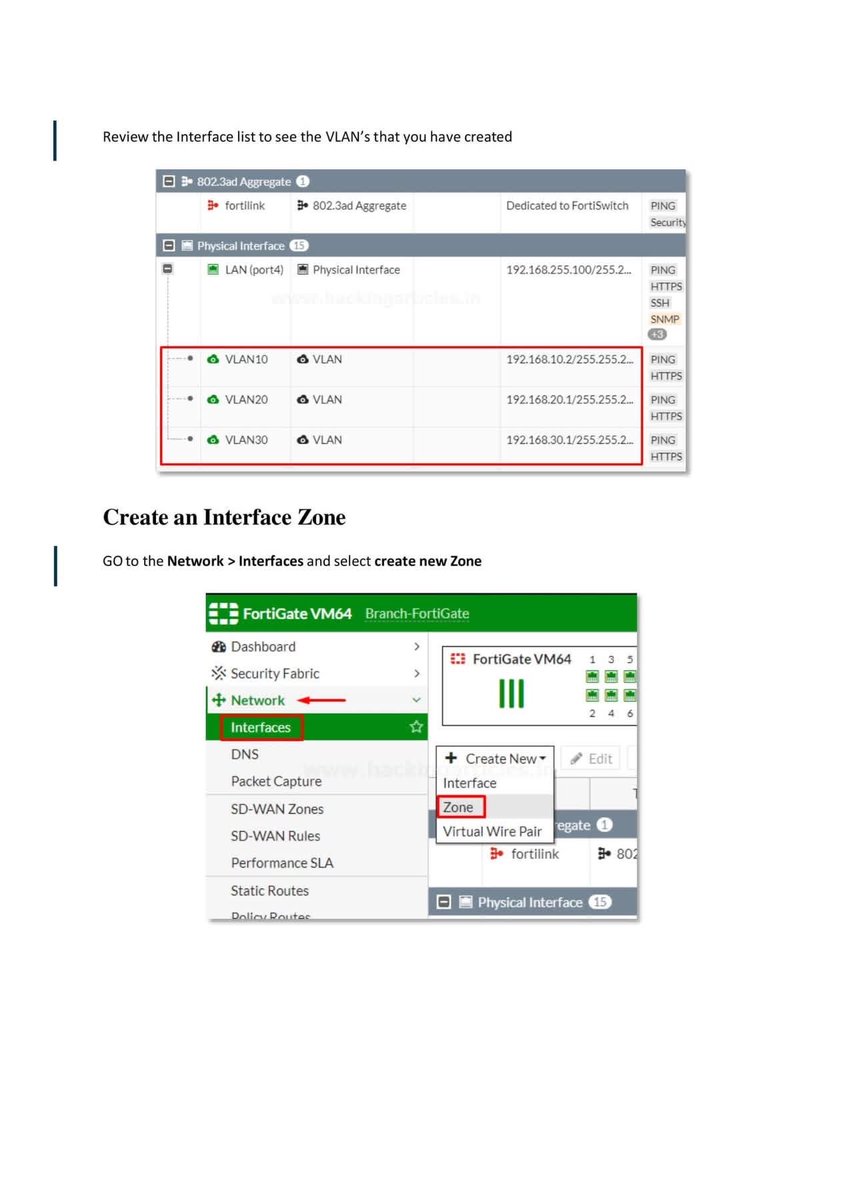
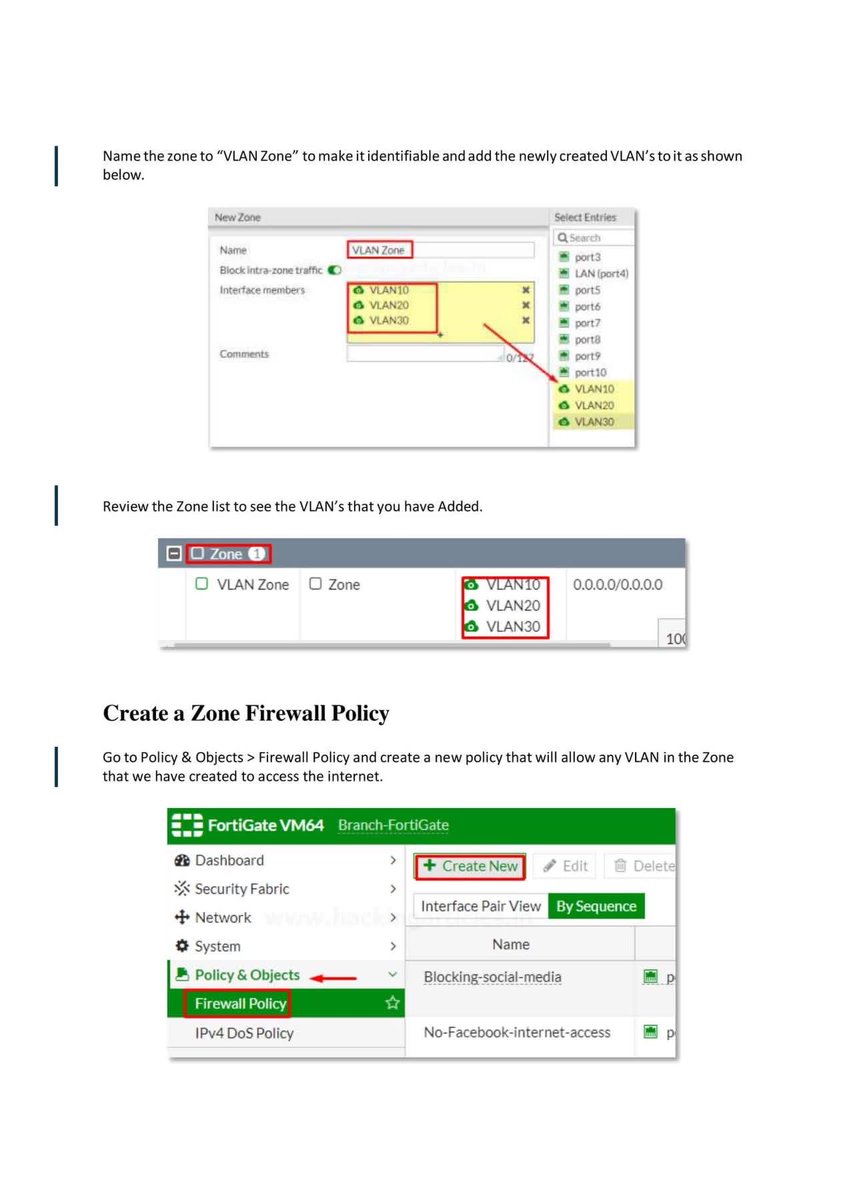
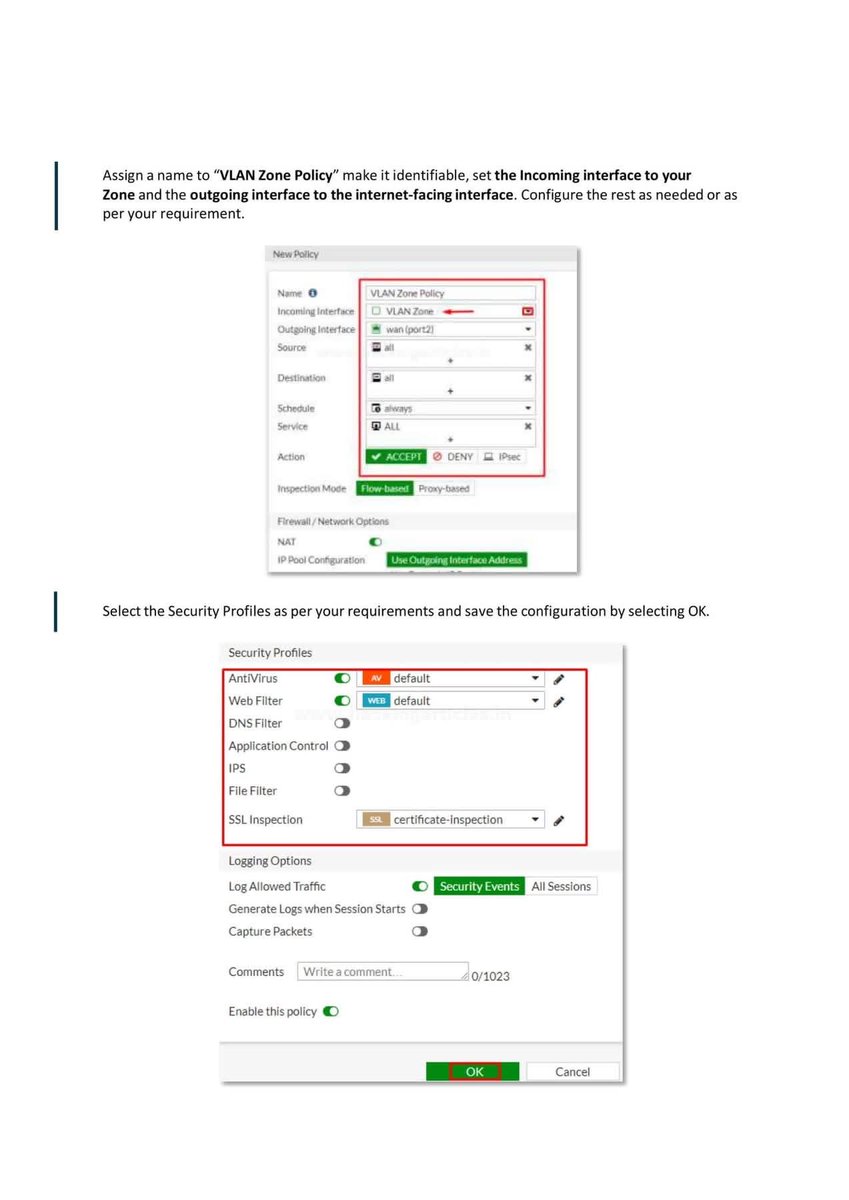
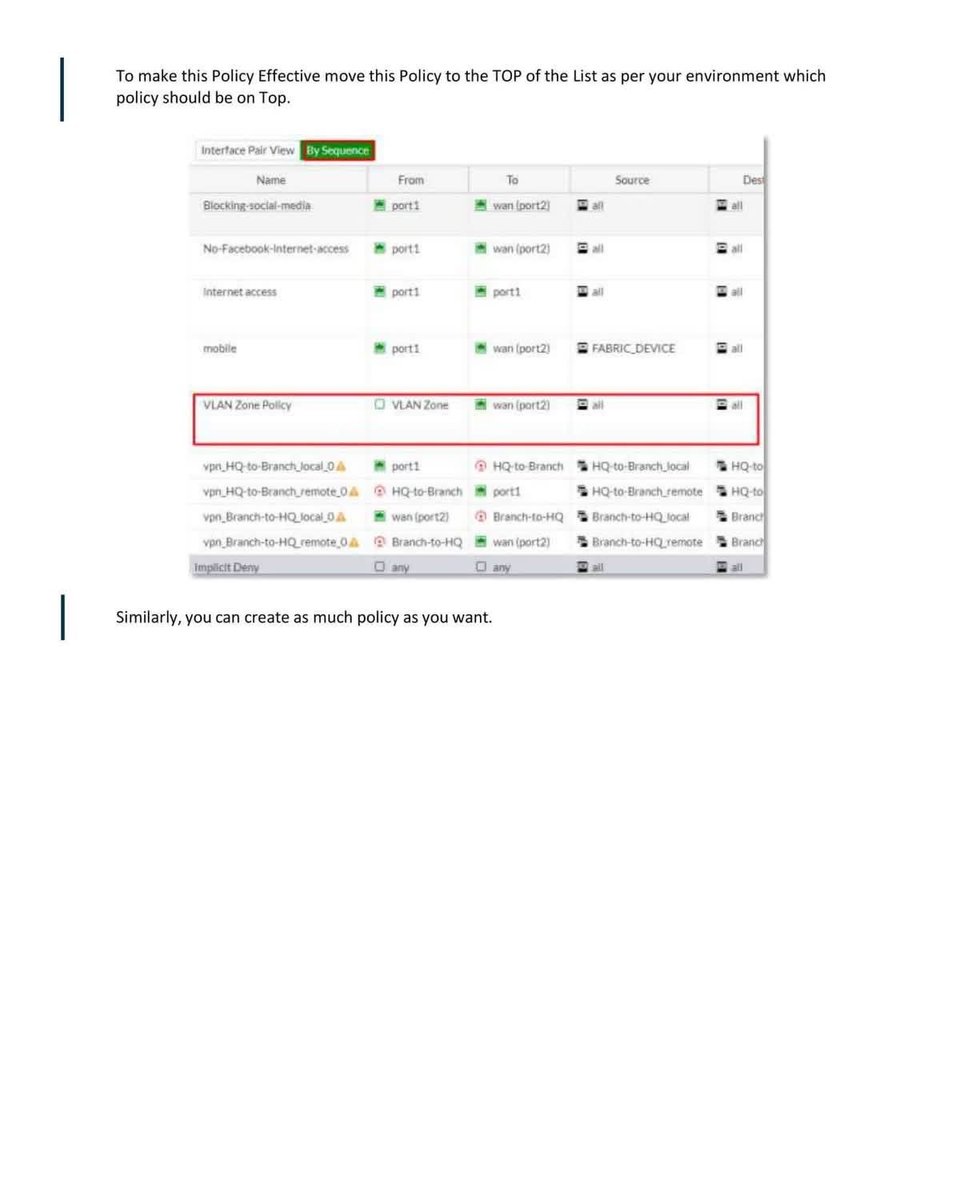
Introduction to Firewall
A firewall is a network security device or software designed to monitor, filter, and control incoming and outgoing network traffic according to predefined security rules.
💡 Comment PDF for full guide
A firewall is a network security device or software designed to monitor, filter, and control incoming and outgoing network traffic according to predefined security rules.
💡 Comment PDF for full guide

Its main goal is to create a protective barrier between a trusted internal network and untrusted external networks, such as the internet, safeguarding systems from unauthorized access and cyber threats
🔹 Purpose of a Firewall
•Protects computers and networks from malware, hackers, and unauthorized intrusions.
•Ensures that only legitimate and safe data traffic passes through.
•Serves as the first line of defense in any network security architecture
•Protects computers and networks from malware, hackers, and unauthorized intrusions.
•Ensures that only legitimate and safe data traffic passes through.
•Serves as the first line of defense in any network security architecture
🔹 Types of Firewalls
Packet-Filtering Firewall
•Operates at the network layer and inspects packets based on IP addresses, ports, and protocols.
Stateful Inspection Firewall
•Monitors the state of active connections and filters traffic using both rules and context
Packet-Filtering Firewall
•Operates at the network layer and inspects packets based on IP addresses, ports, and protocols.
Stateful Inspection Firewall
•Monitors the state of active connections and filters traffic using both rules and context
Proxy Firewall (Application-Level Gateway)
•Works at the application layer, inspecting requests before forwarding them to their destination.
•Works at the application layer, inspecting requests before forwarding them to their destination.
Next-Generation Firewall (NGFW)
•Integrates traditional firewall features with intrusion prevention, deep packet inspection, and application-level awareness.
•Integrates traditional firewall features with intrusion prevention, deep packet inspection, and application-level awareness.
Cloud Firewall / Virtual Firewall
•Deployed in cloud environments to protect virtual networks, workloads, and cloud-based services.
•Deployed in cloud environments to protect virtual networks, workloads, and cloud-based services.
#Firewall #NetworkSecurity #CyberSecurity #ITInfrastructure #NetworkProtection #NextGenFirewall #CloudSecurity #InformationSecurity #NetworkDefense #NetworkEngineer #ITSecurity
• • •
Missing some Tweet in this thread? You can try to
force a refresh