‼️ China's largest cybersecurity firm, Knownsec, was breached, exposing details of China's state cyber operations.
The data includes cyberweapon documentation, internal hacking tool source code, and global target lists covering over 20 countries, including Japan, Vietnam, and India.
A spreadsheet lists 80 hacked foreign organizations, plus evidence of 95 GB of stolen Indian immigration data and 3 TB of call records from South Korean mobile operator LG U Plus.
One of the documents mention a malicious power bank, disguised as a charging device.
Knownsec is key to China's cybersecurity, providing advanced defense and offensive capabilities, including espionage tools.
A thread with their tools 🧵
The data includes cyberweapon documentation, internal hacking tool source code, and global target lists covering over 20 countries, including Japan, Vietnam, and India.
A spreadsheet lists 80 hacked foreign organizations, plus evidence of 95 GB of stolen Indian immigration data and 3 TB of call records from South Korean mobile operator LG U Plus.
One of the documents mention a malicious power bank, disguised as a charging device.
Knownsec is key to China's cybersecurity, providing advanced defense and offensive capabilities, including espionage tools.
A thread with their tools 🧵

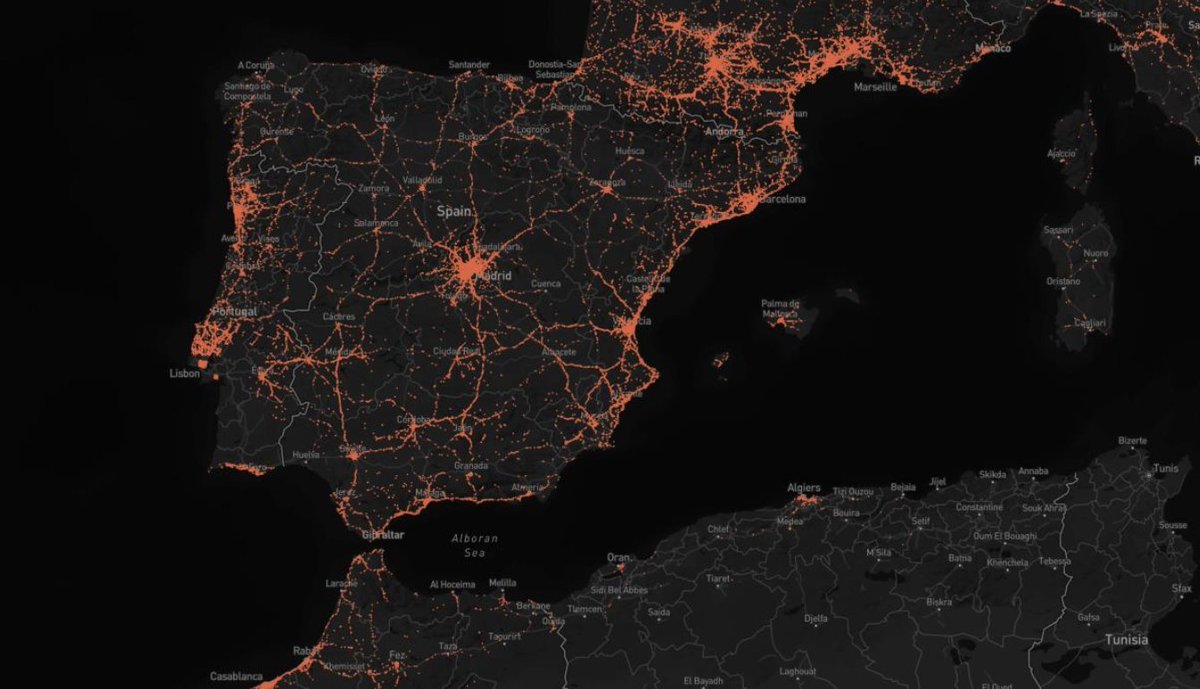
ZoomEye
A global search engine similar to Shodan or Censys, lists vulnerabilities for each host. It claims to scan the entire IPv4 address range in 7-10 days.
A global search engine similar to Shodan or Censys, lists vulnerabilities for each host. It claims to scan the entire IPv4 address range in 7-10 days.

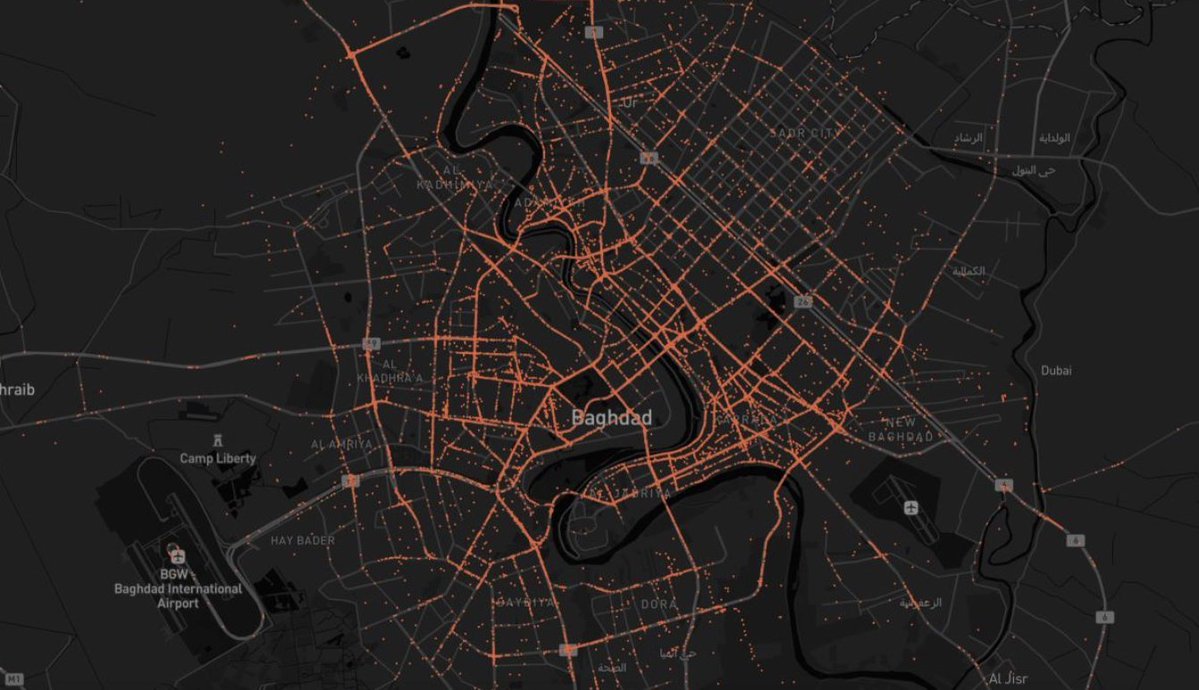
Passive radar
A tool called "Passive Radar," a PCAP analyzer, is used for quick asset mapping tasks, such as those required by military clients.
A tool called "Passive Radar," a PCAP analyzer, is used for quick asset mapping tasks, such as those required by military clients.

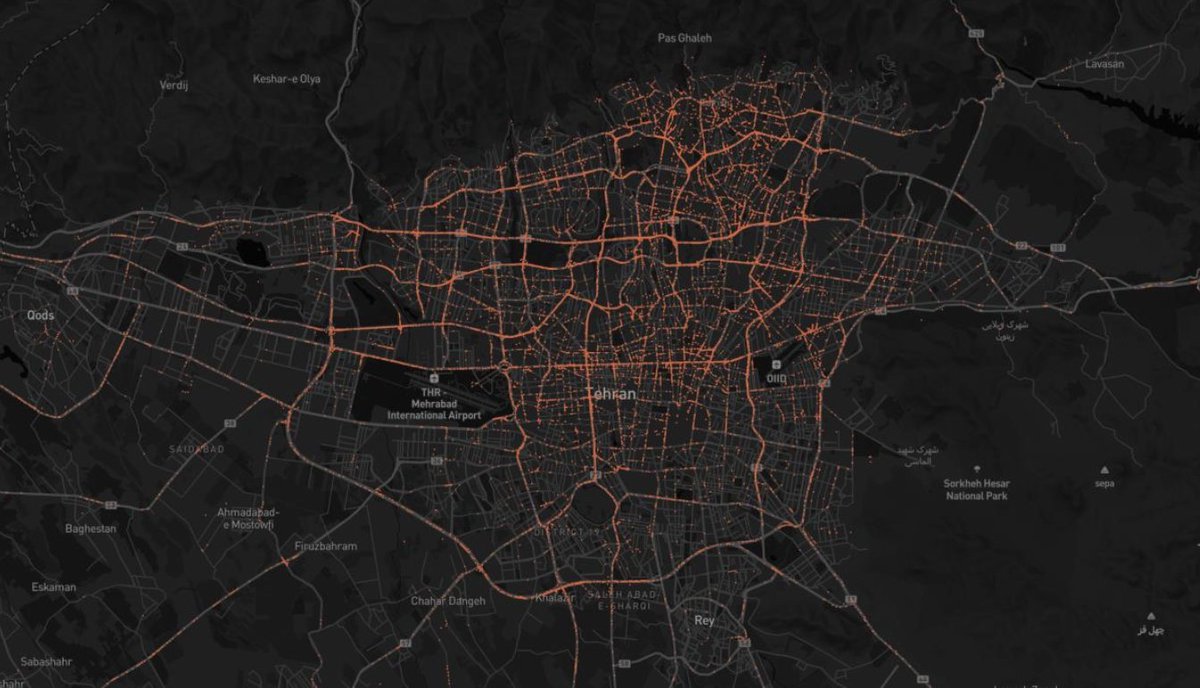
Slides also indicate collecting data and mapping critical digital infrastructure of adversarial nations. 

It's interesting to note the listing of critical Taiwanese edge devices. Reports confirm nation-state actors are attacking these devices. 

This screenshot shows where opportunities exist for a company like KnownSec to add value, including internet surveillance, building command centers, providing big data analysis platforms for various departments, or network construction for specific public security bureaus. 

Building digital command centers for the Ministry of Public Security and how the company supports Public Security in conducting "special investigations" 





Read @NetAskari's report substack.com/home/post/p-17…
Link to the docs: ibb.co/album/5X11nM?p…
Additional sources:
juejin.cn/post/756884162…
chonglangtv.org/t/topic/1485
glav.su/forum/threads/…
Link to the docs: ibb.co/album/5X11nM?p…
Additional sources:
juejin.cn/post/756884162…
chonglangtv.org/t/topic/1485
glav.su/forum/threads/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh