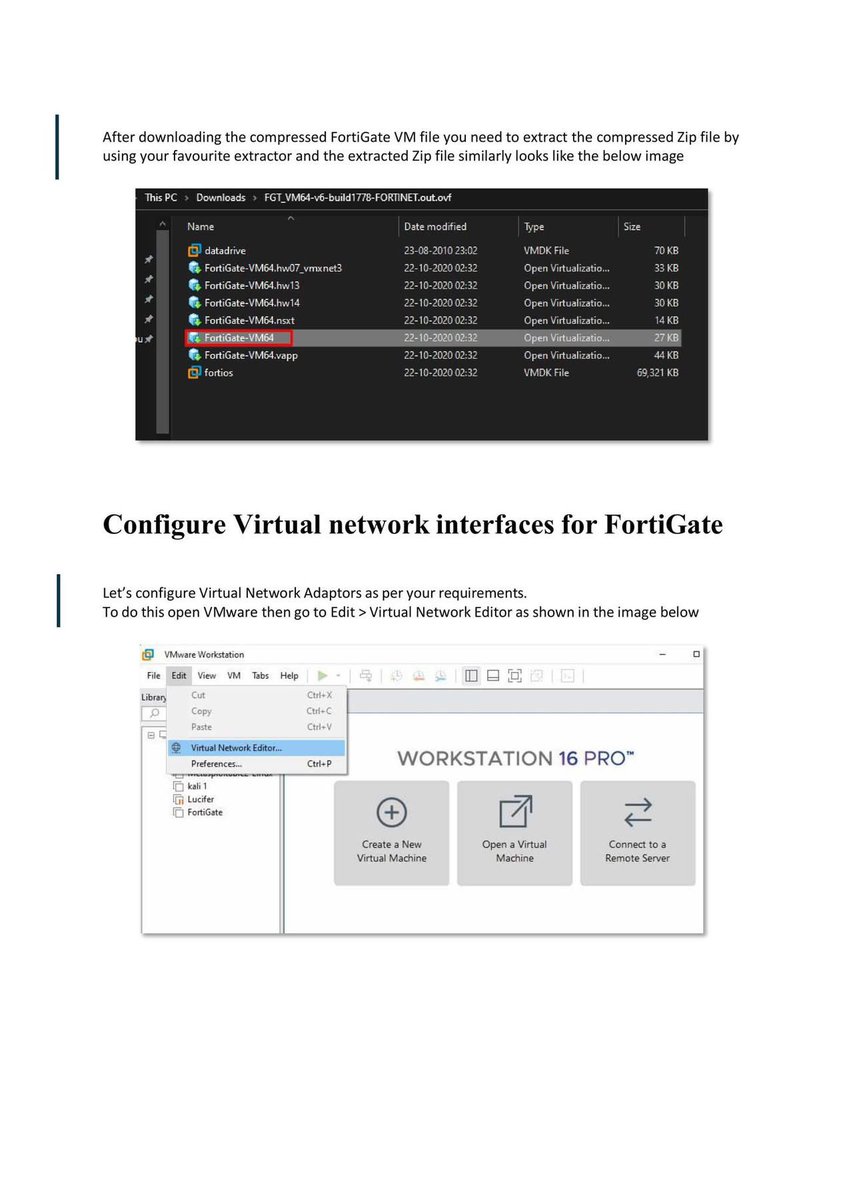
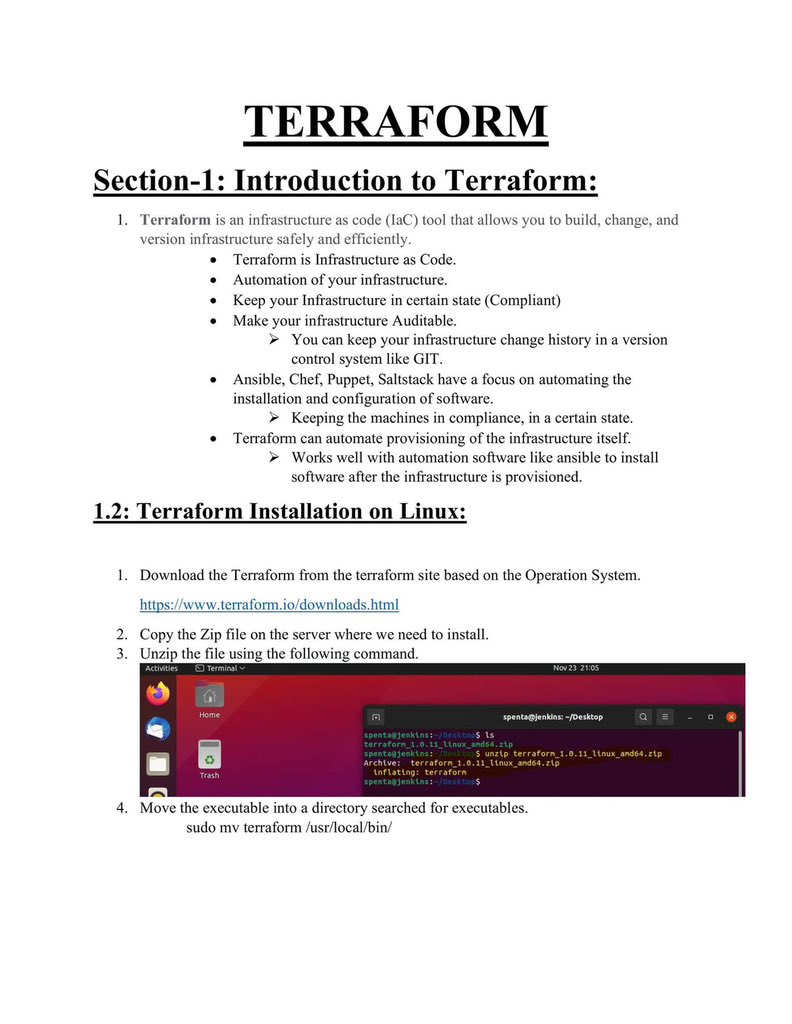
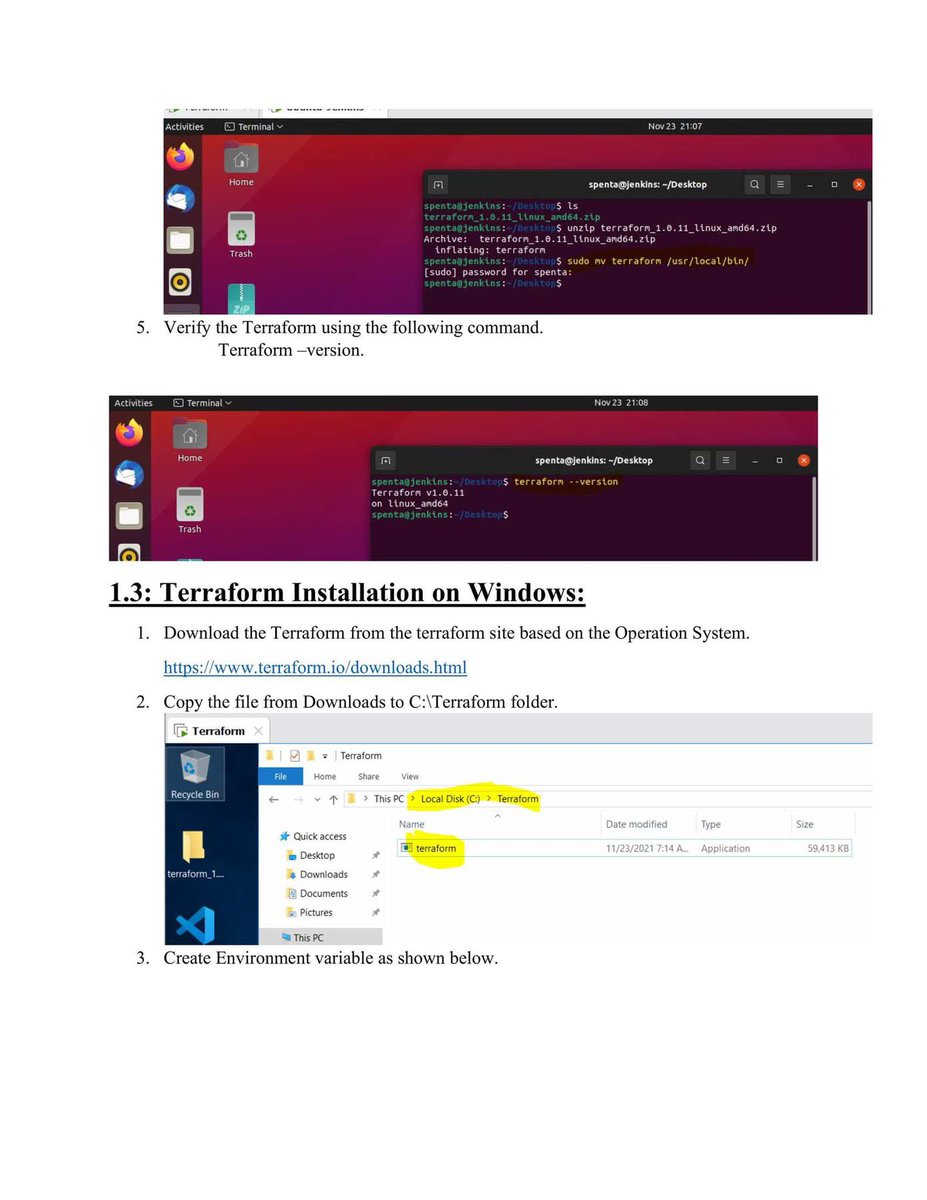
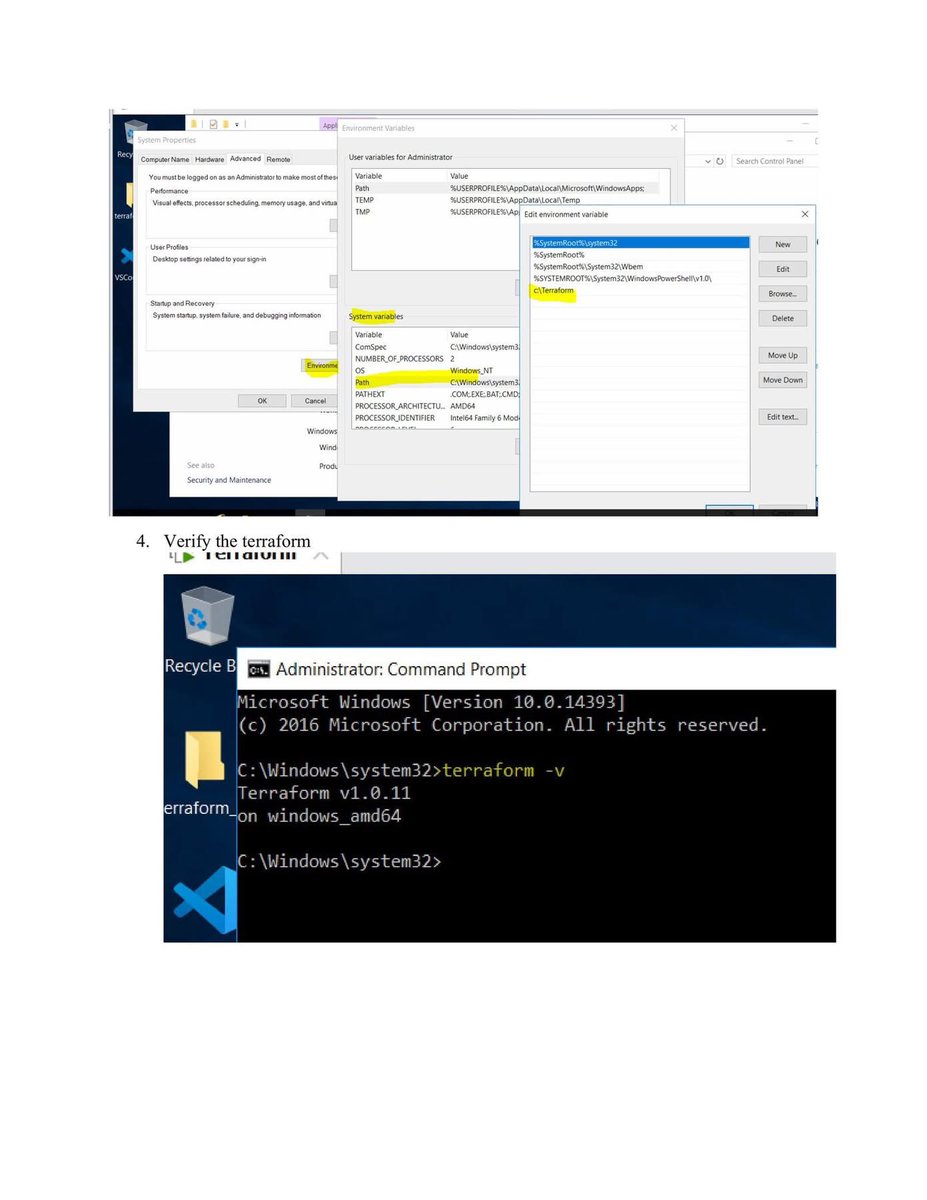
💡 My Cybersecurity Home Lab Mini SOC Environment
Over the past few months, I built a fully virtualized home lab designed to mimic a real SOC environment combining offensive testing, defensive monitoring, and layered security.
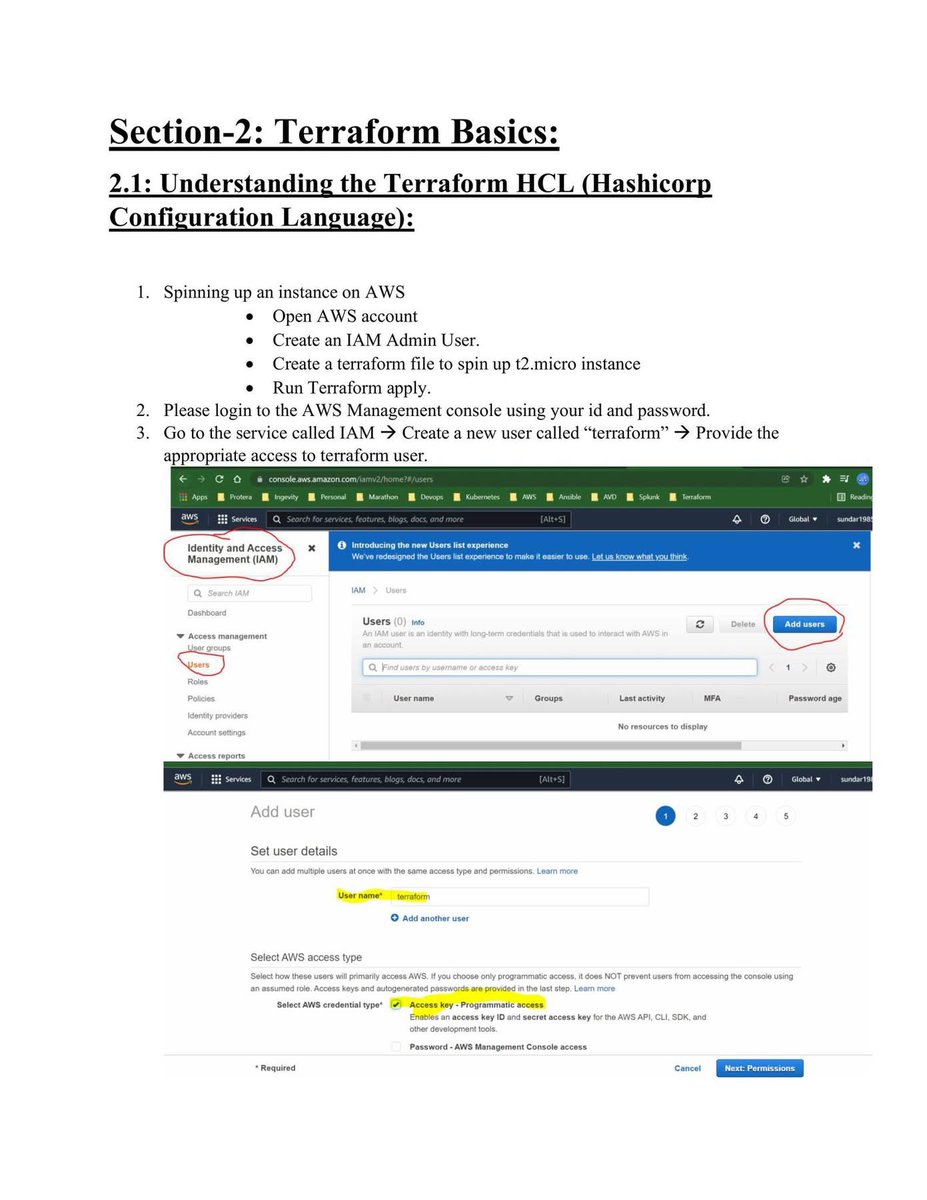
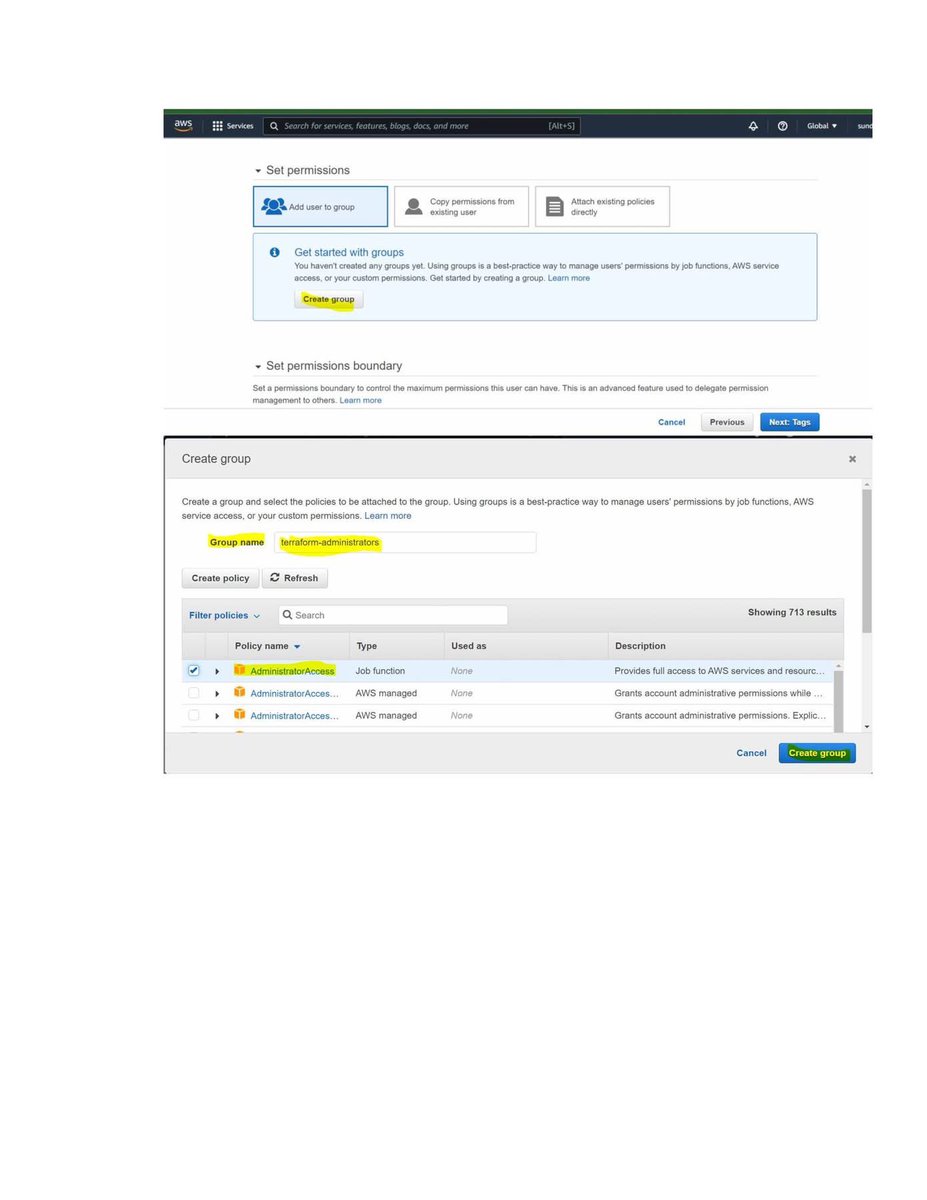
Over the past few months, I built a fully virtualized home lab designed to mimic a real SOC environment combining offensive testing, defensive monitoring, and layered security.

It gives me hands-on experience in threat hunting, network defense, alert correlation, and overall SOC workflows
🔧 Lab Setup Includes:
•🐉 Kali Linux – Recon & exploitation
•🐧 Ubuntu (Wazuh) – SIEM for monitoring & correlation
•🛡 pfSense – Firewall + segmentation
🔧 Lab Setup Includes:
•🐉 Kali Linux – Recon & exploitation
•🐧 Ubuntu (Wazuh) – SIEM for monitoring & correlation
•🛡 pfSense – Firewall + segmentation
•🧪 Suricata IDS/IPS – Threat detection & active blocking
•🪟 Windows Server AD – Domain & user management
•🎯 Metasploitable – Vulnerable target for testing
•🪟 Windows Server AD – Domain & user management
•🎯 Metasploitable – Vulnerable target for testing
🎯 Key Achievements:
•🚨 Detected Nmap stealth scans with custom Suricata rules
•🚫 Blocked malicious traffic using IPS mode
•🔐 Identified brute-force attempts via Wazuh alerts
•🚨 Detected Nmap stealth scans with custom Suricata rules
•🚫 Blocked malicious traffic using IPS mode
•🔐 Identified brute-force attempts via Wazuh alerts
•🕵️♂️ Flagged Mimikatz credential dumping (MITRE T1003.001)
•🔄 Correlated pfSense → Suricata → Wazuh logs for validation
•🛡 Set up FIM, vulnerability scans, and log-based detections
•📊 Built a practical layered defense similar to real SOC environments
•🔄 Correlated pfSense → Suricata → Wazuh logs for validation
•🛡 Set up FIM, vulnerability scans, and log-based detections
•📊 Built a practical layered defense similar to real SOC environments
🔗 Open to connecting with SOC analysts, cybersecurity pros, and recruiters let’s collaborate and grow together
#CyberSecurity #SOC #SIEM #ThreatHunting #Wazuh #Suricata #pfSense #ActiveDirectory #MITREATTACK
#CyberSecurity #SOC #SIEM #ThreatHunting #Wazuh #Suricata #pfSense #ActiveDirectory #MITREATTACK
• • •
Missing some Tweet in this thread? You can try to
force a refresh