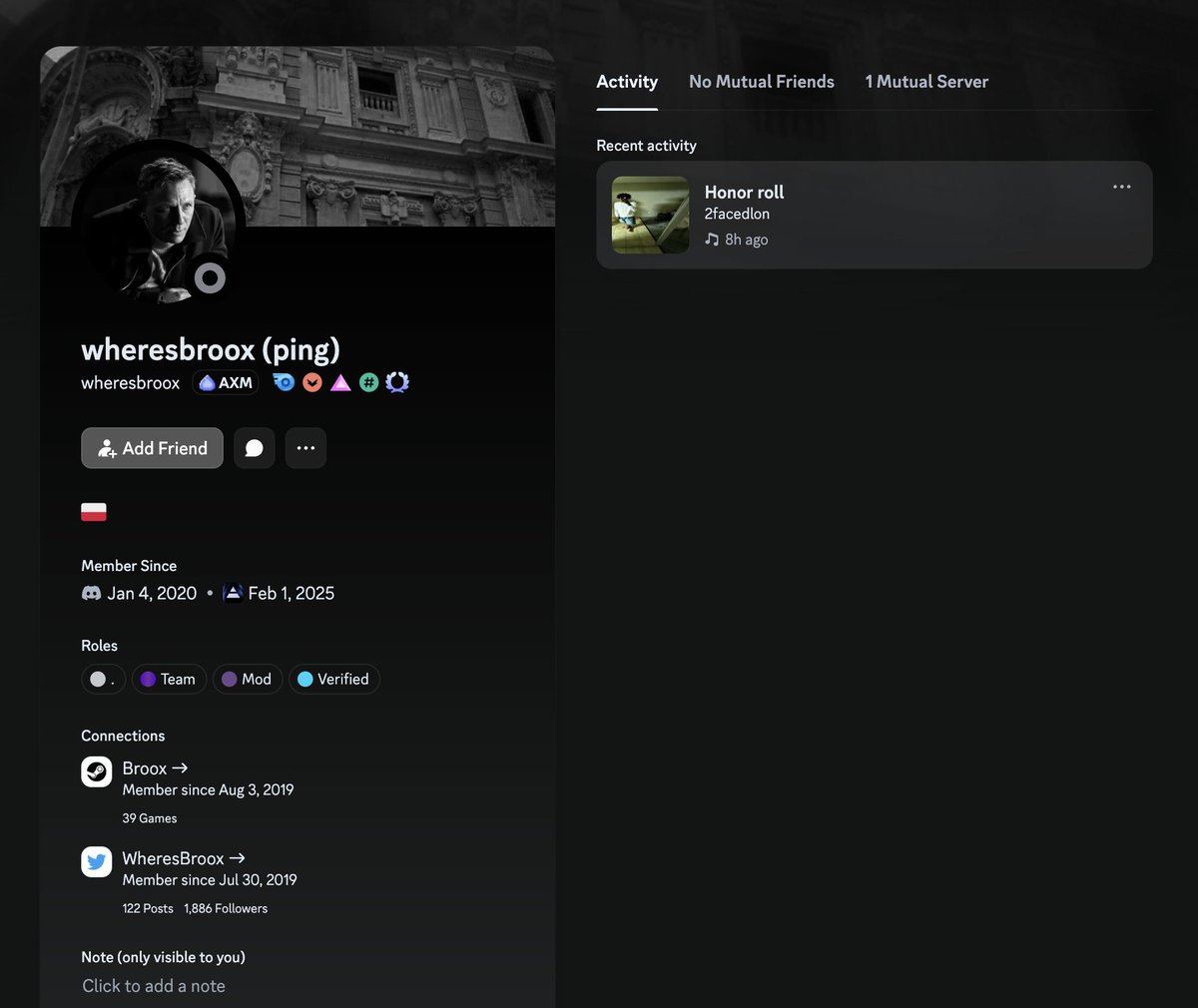
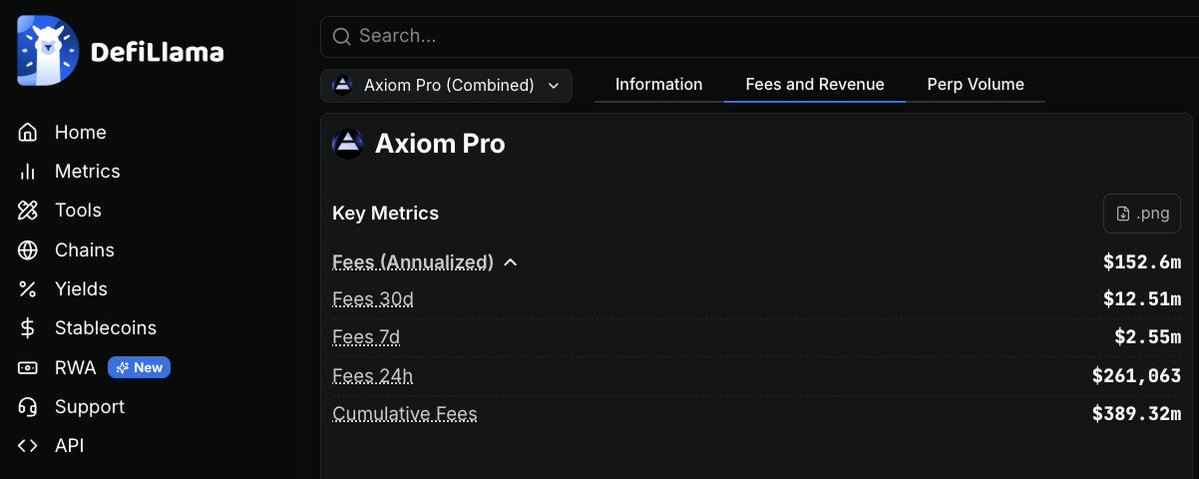
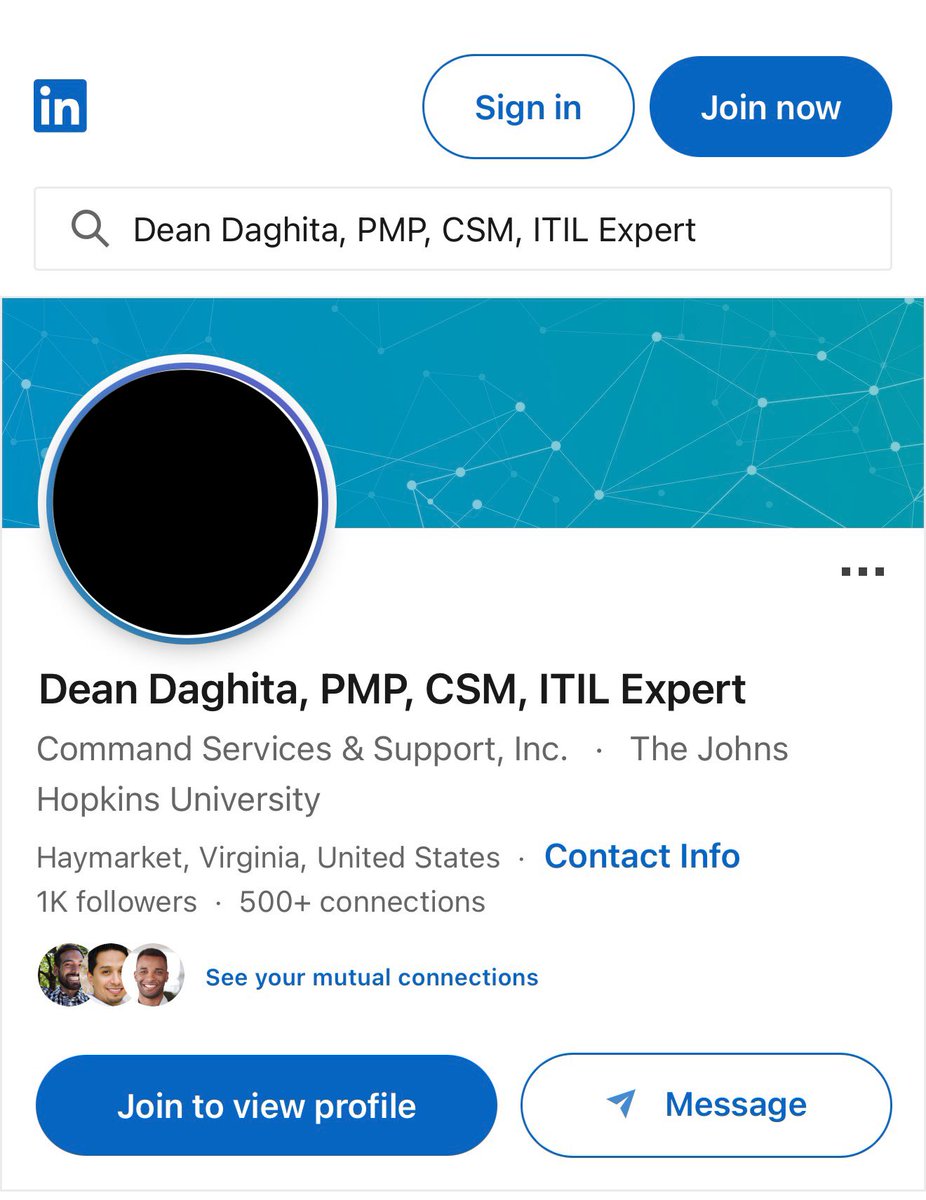
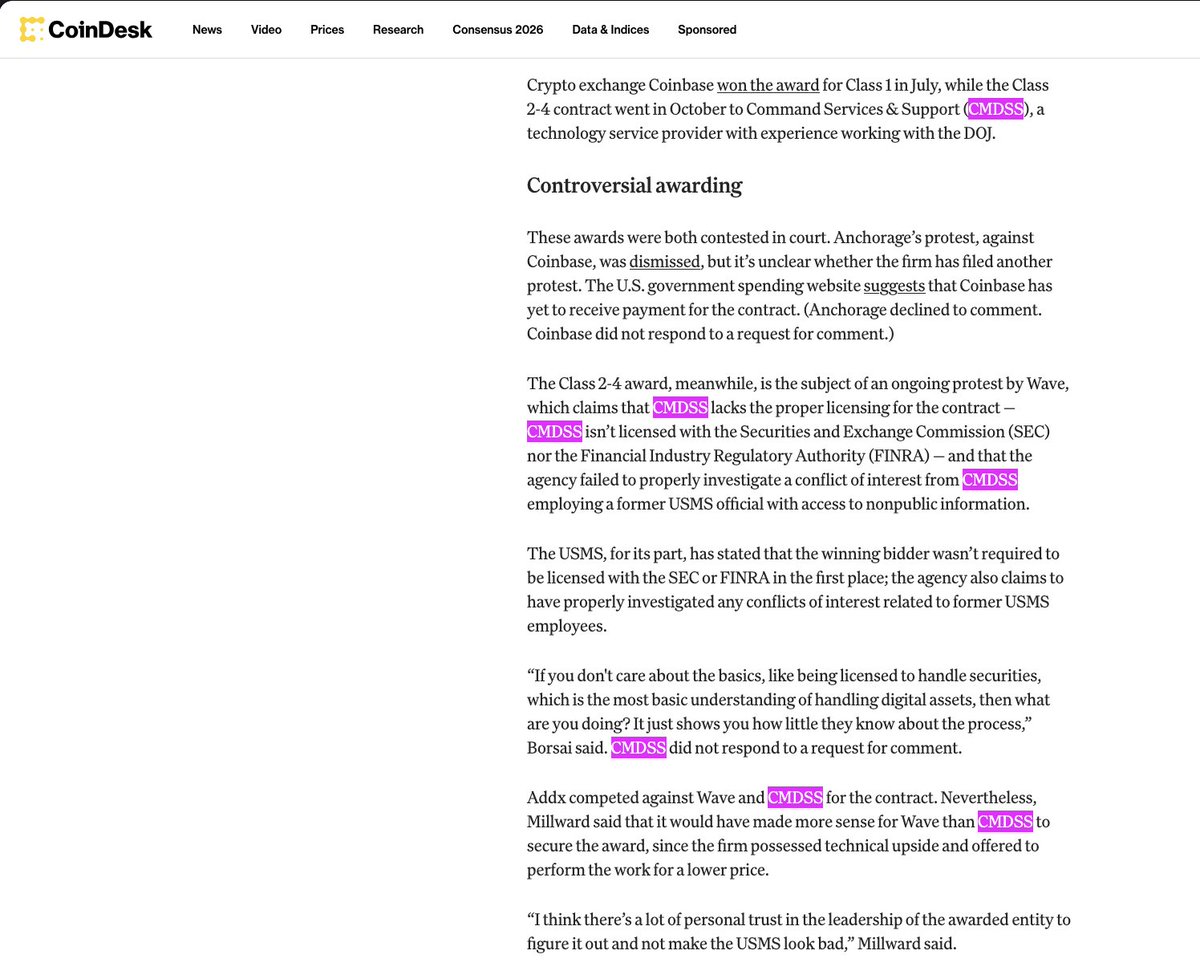
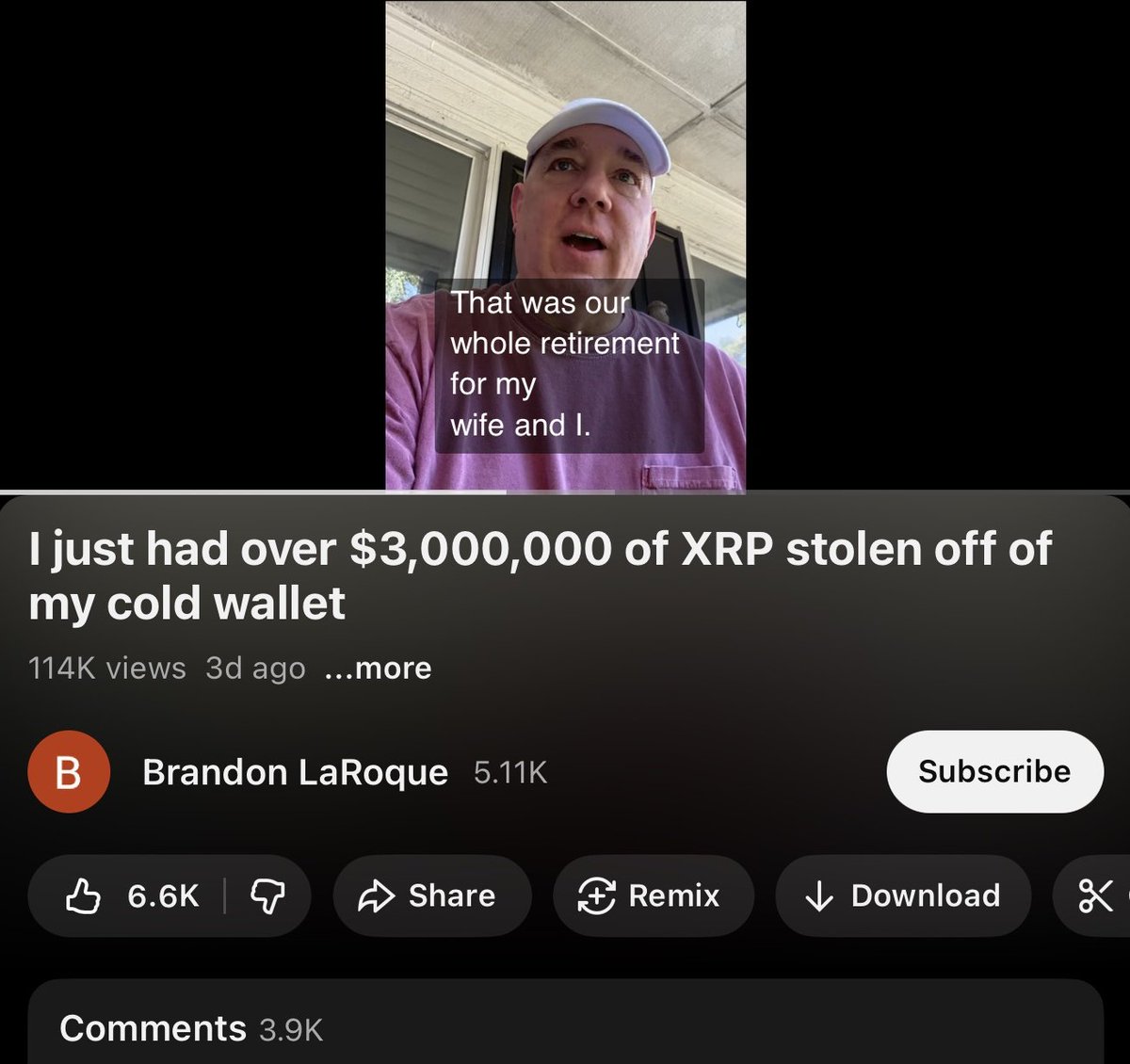
1/ Meet the threat actor John (Lick), who was caught flexing $23M in a wallet address directly tied to $90M+ in suspected thefts from the US Government in 2024 and multiple other unidentified victims from Nov 2025 to Dec 2025. 


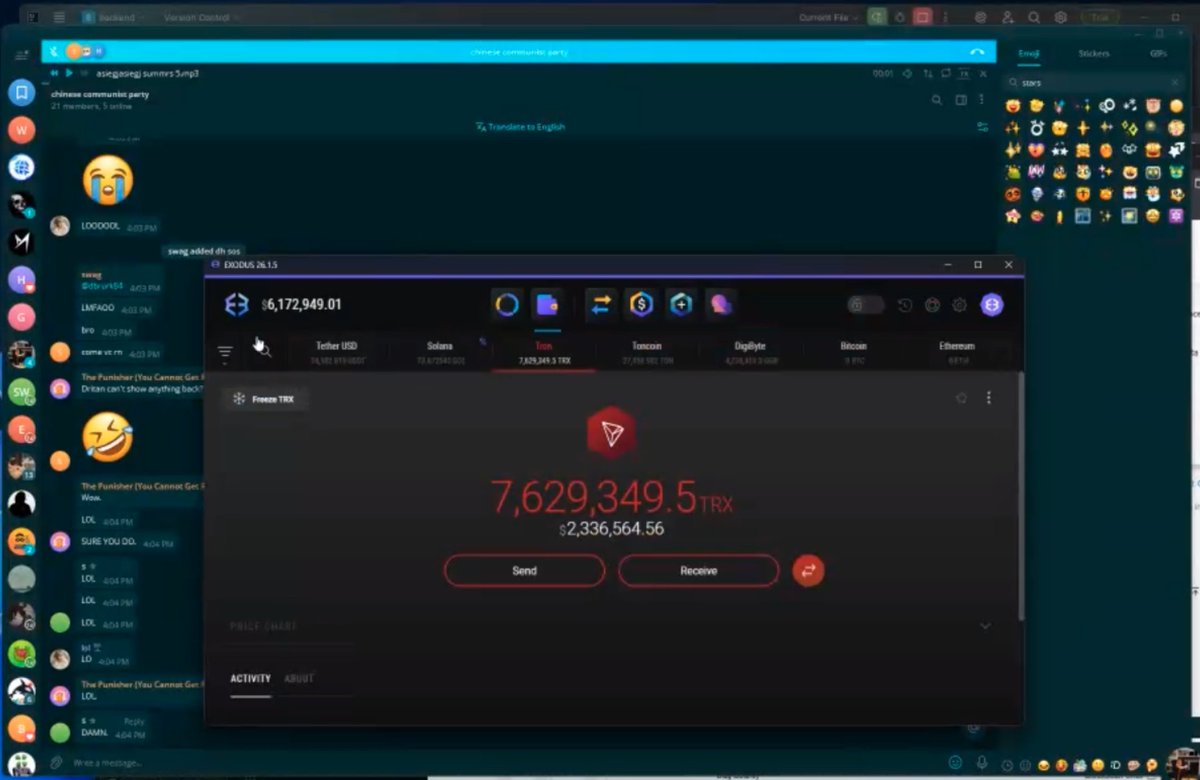
2/ Earlier today John got into a heated argument with another threat actor known as Dritan Kapplani Jr. in a group chat to see who had more funds in crypto wallets.
In 'The Com' this is known as a band for band (b4b).
However the entire interaction was fully recorded.

In 'The Com' this is known as a band for band (b4b).
However the entire interaction was fully recorded.
https://x.com/zachxbt/status/1931216174903398723
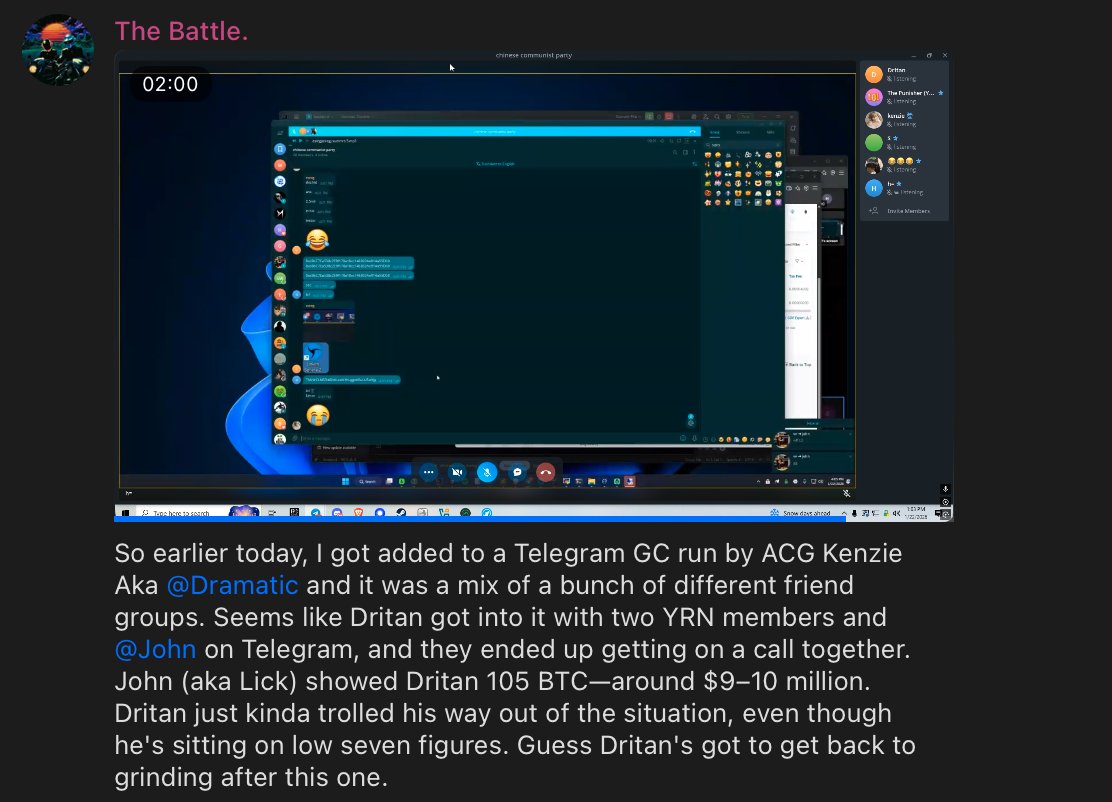
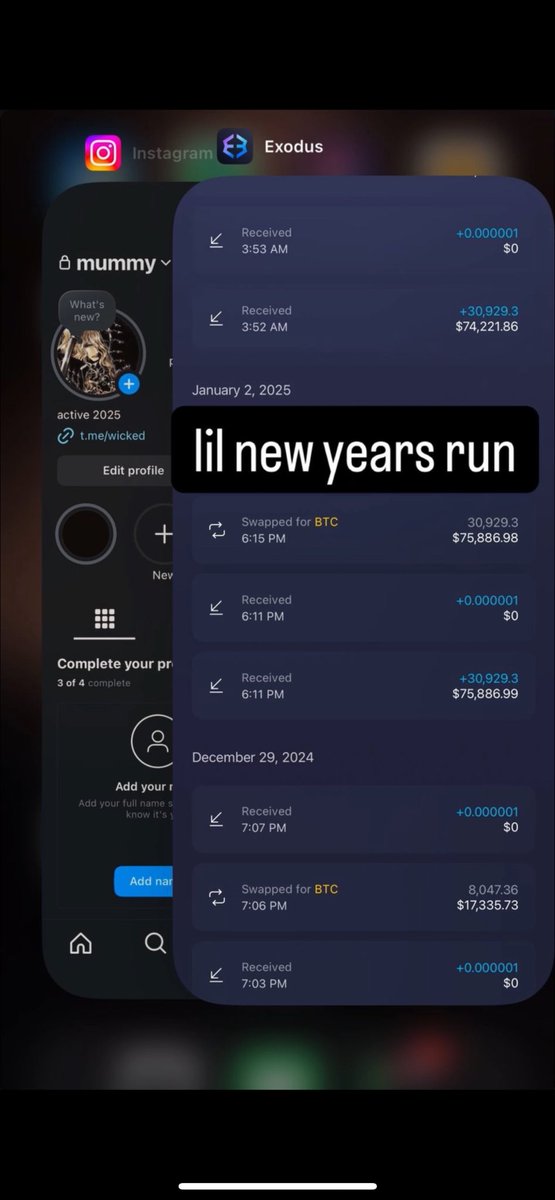
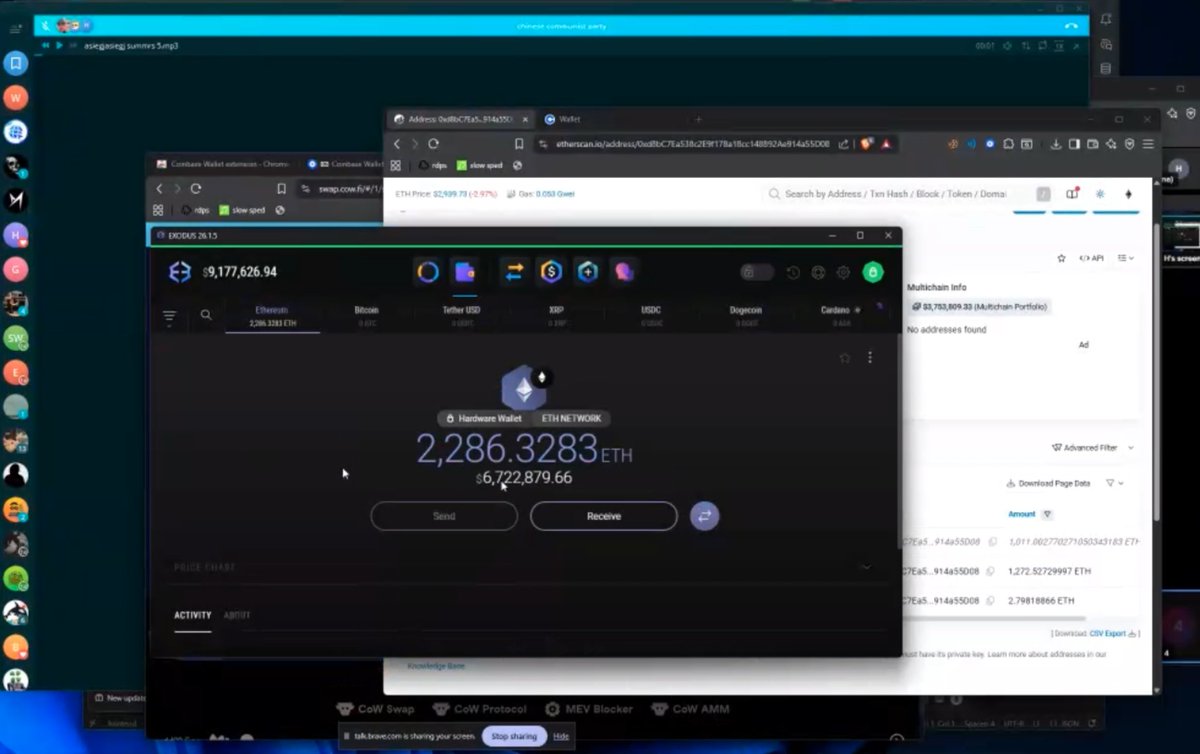
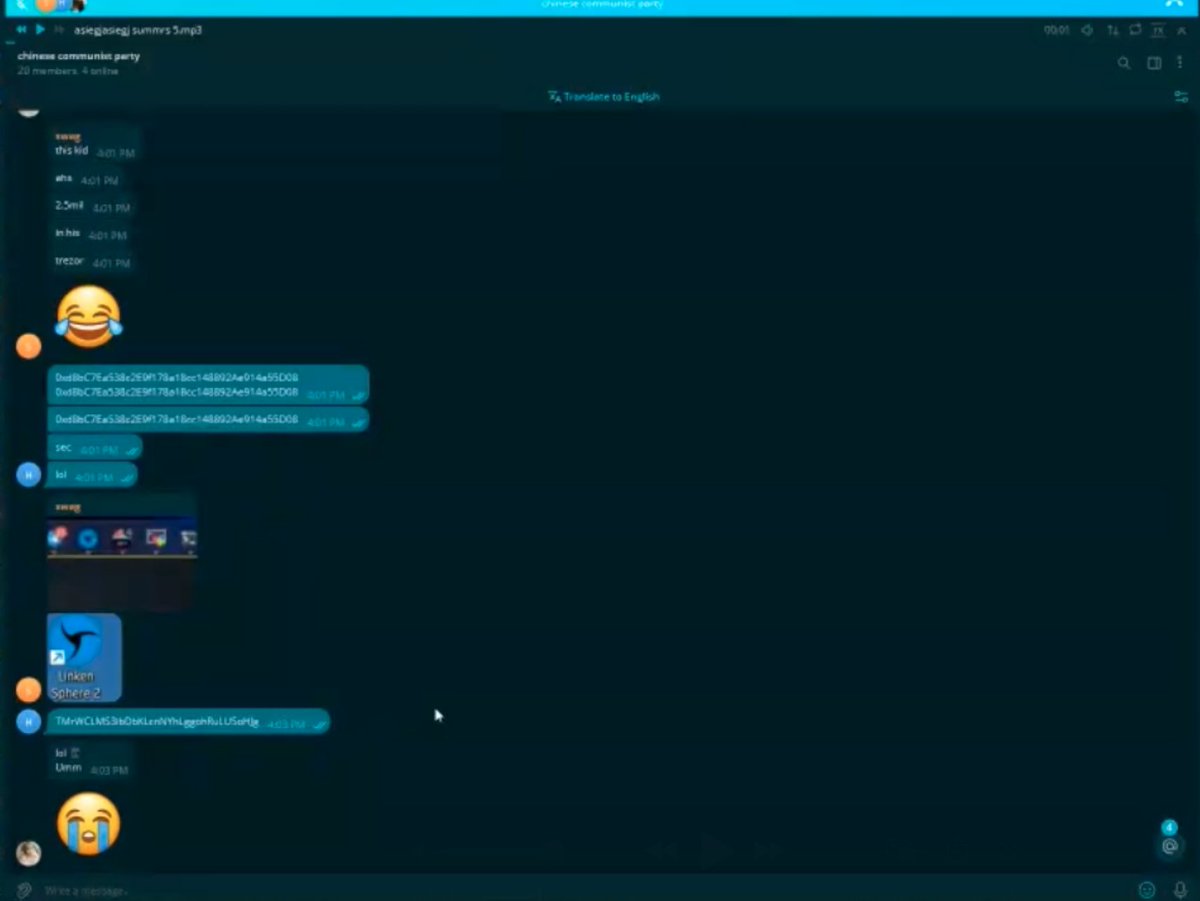
3/ In part 1 of the recording Dritan mocks John however John screenshares Exodus Wallet which shows the Tron address below with $2.3M:
TMrWCLMS3ibDbKLcnNYhLggohRuLUSoHJg
TMrWCLMS3ibDbKLcnNYhLggohRuLUSoHJg
4/ In part 2 of the recording Dritan continues to mock John while another $6.7M worth of ETH is moved into the wallet address below:
0xd8bc7ea538c2e9f178a18cc148892ae914a55d08
0xd8bc7ea538c2e9f178a18cc148892ae914a55d08
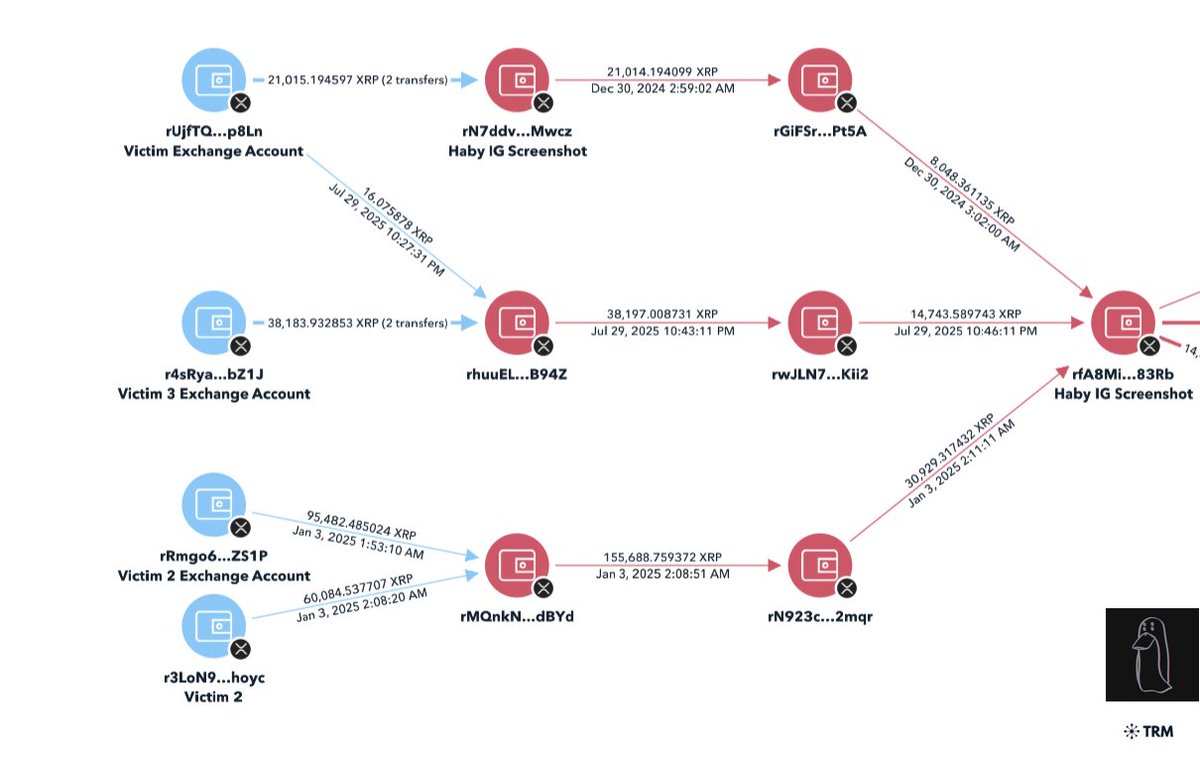
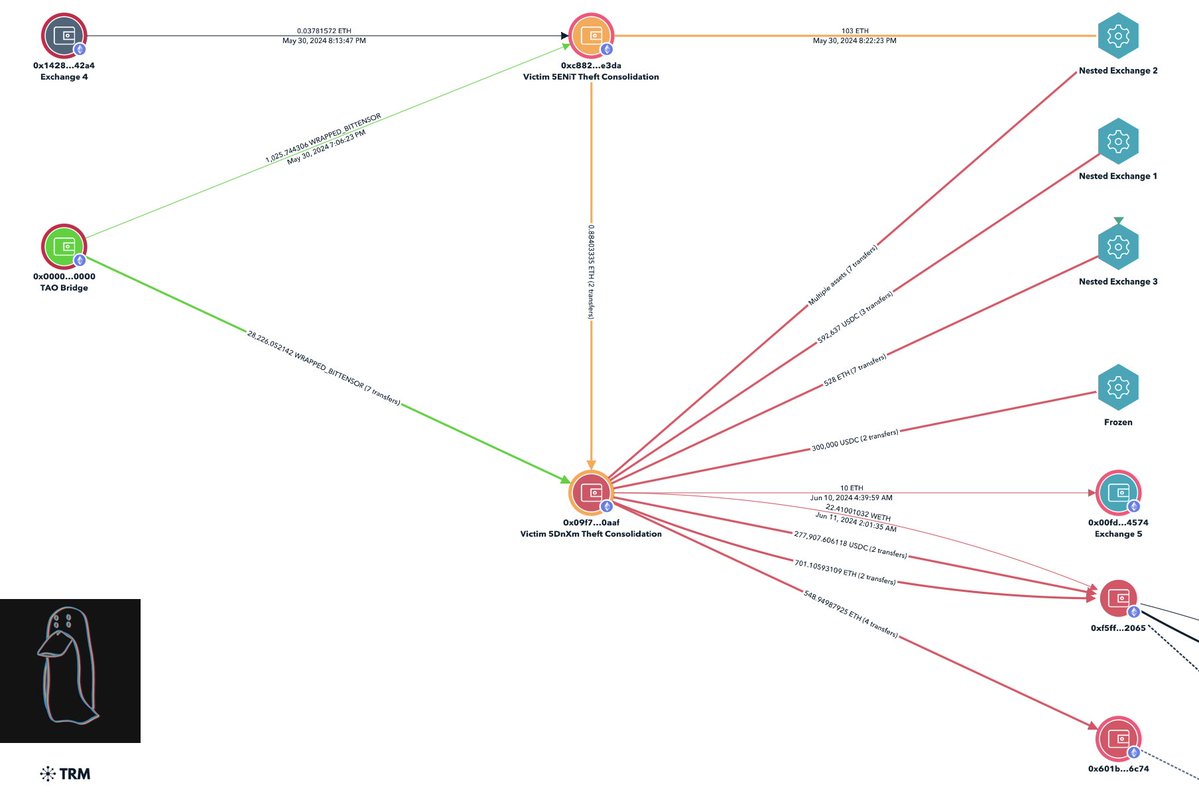
5/ After the B4B was done John had moved ~$23M total to 0xd8bc.
The recording captures that John clearly controls both addresses.
Additional addresses can likely be found in the recordings.
I then began tracing backwards to verify the source of funds.


The recording captures that John clearly controls both addresses.
Additional addresses can likely be found in the recordings.
I then began tracing backwards to verify the source of funds.
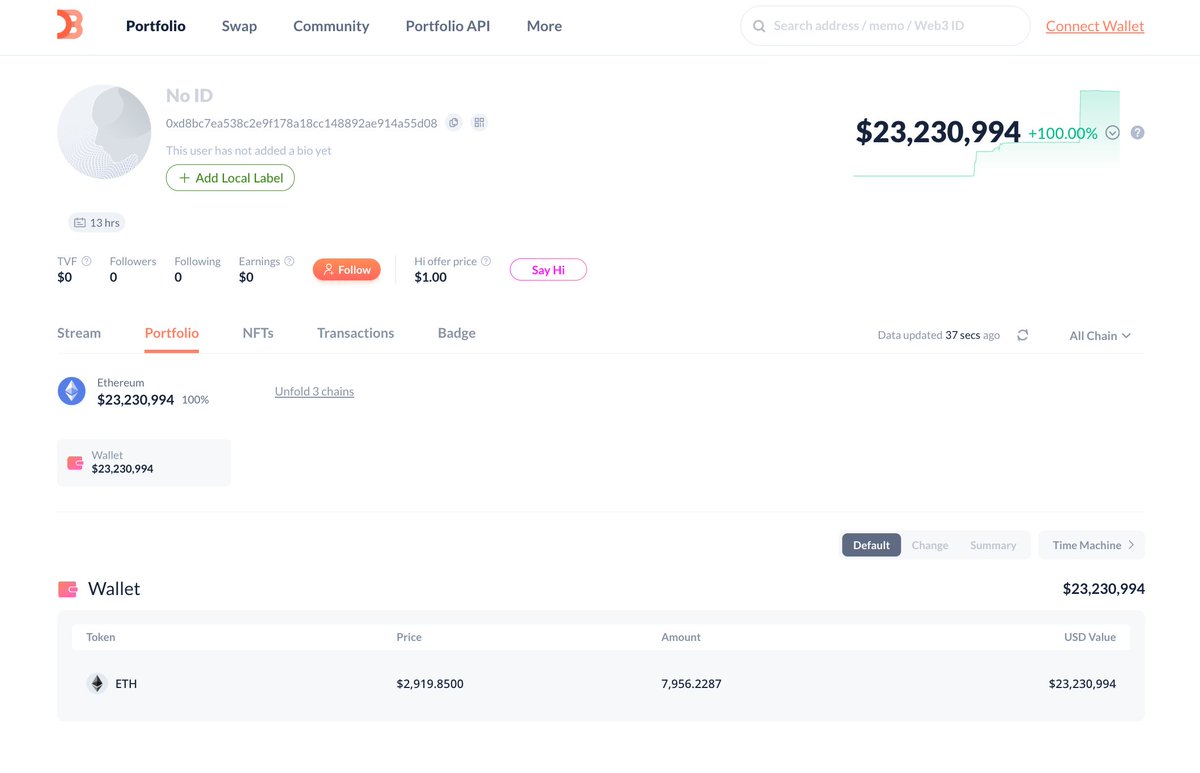
6/ 0xd8bc receives from 0x8924 which in the recording John confirms owning.
0x8924 received 1066 WETH from 0xc7a2 on Nov 20, 2025 in the following txn.
0x76c6e92c4cefda209263a214241f1b47b9cff0123e9d292d613aea3447466dd0
0x8924 received 1066 WETH from 0xc7a2 on Nov 20, 2025 in the following txn.
0x76c6e92c4cefda209263a214241f1b47b9cff0123e9d292d613aea3447466dd0
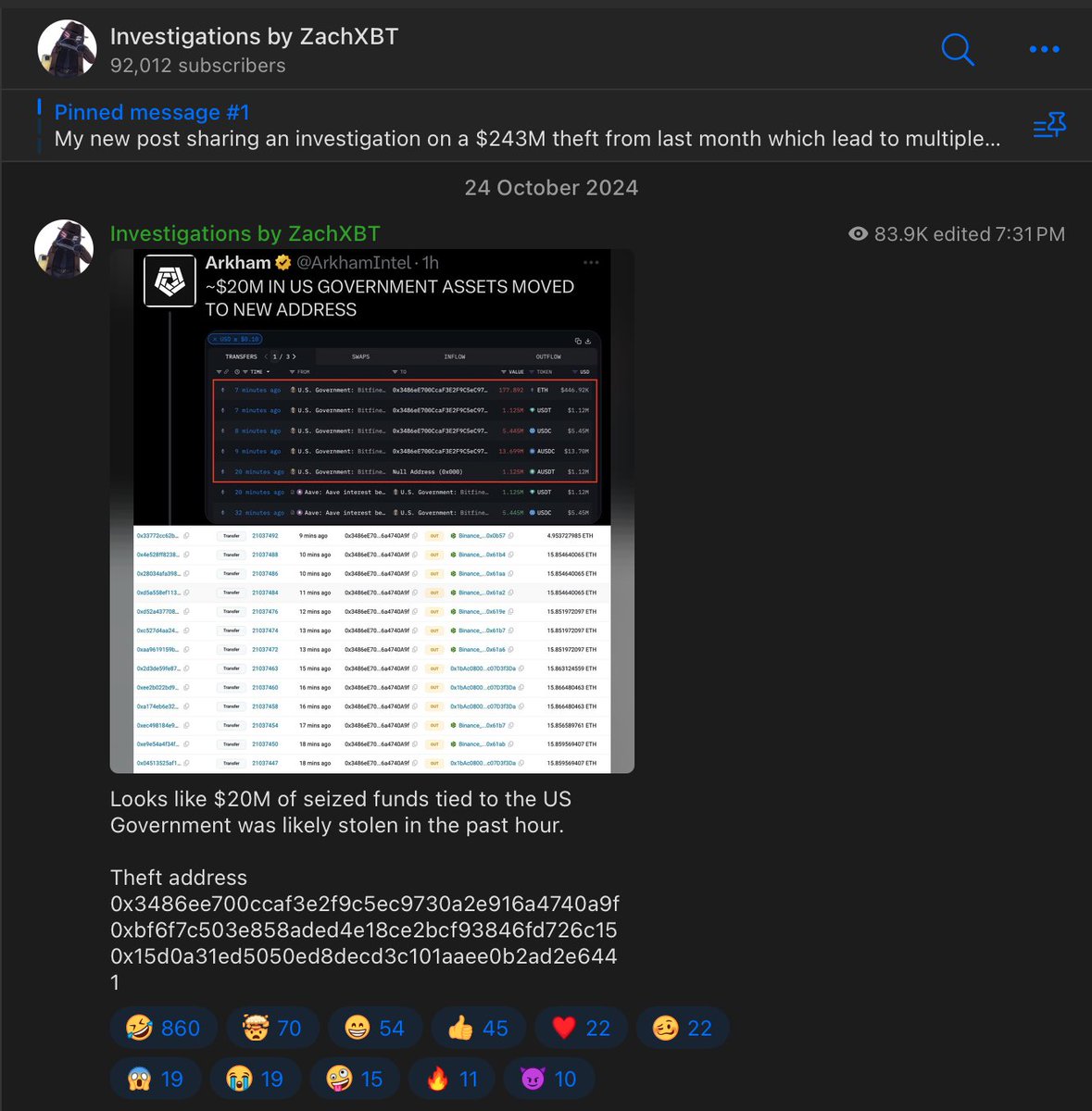
7/ 0xc7a2 received $24.9M from a US Government address in March 2024 related to the Bitfinex hack seizure which is a theft from the USG I previously reported about in Oct 2024.
$18.5M currently sits at
0xc7A253fD3C61CF69d043e6184c107dF4E29475B5
$18.5M currently sits at
0xc7A253fD3C61CF69d043e6184c107dF4E29475B5
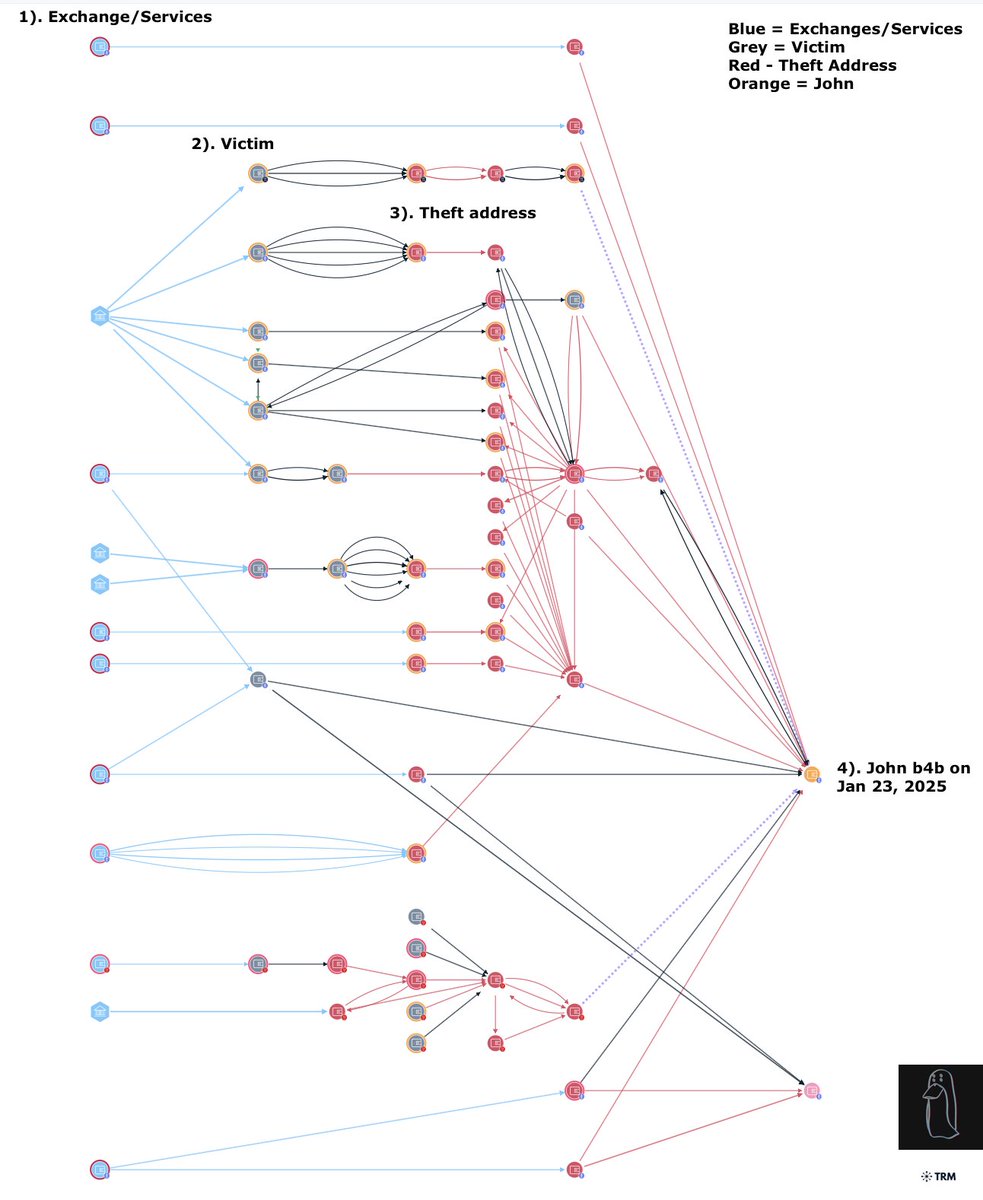
8/ 0xd8bc is tied to $63M+ inflows from suspected victims and government seizure addresses in Q4 2025.
Dec 2025
$13.5M
0x77a722bf33787c3512d0f4fc36412140057f4223
$15.4M
0xf51b044f998277b17467cd713d72b403e16fad48
Nov 2025
$3M
TACZPnbg2Fi2ppC3cGxQxZb95SqwAZVAw9
$1M
6tMdWb3w3UaVq4JRSm1qa2s8mVwj2MYFAveJEL6S93Ua
Dec 2025
$13.5M
0x77a722bf33787c3512d0f4fc36412140057f4223
$15.4M
0xf51b044f998277b17467cd713d72b403e16fad48
Nov 2025
$3M
TACZPnbg2Fi2ppC3cGxQxZb95SqwAZVAw9
$1M
6tMdWb3w3UaVq4JRSm1qa2s8mVwj2MYFAveJEL6S93Ua
9/ Another 4.17K ETH ($12.4M) was received from MEXC earlier today flowing to 0xd8bc
0xe0f7a45a491d53f9361d35b4ef9908986d3b37b7
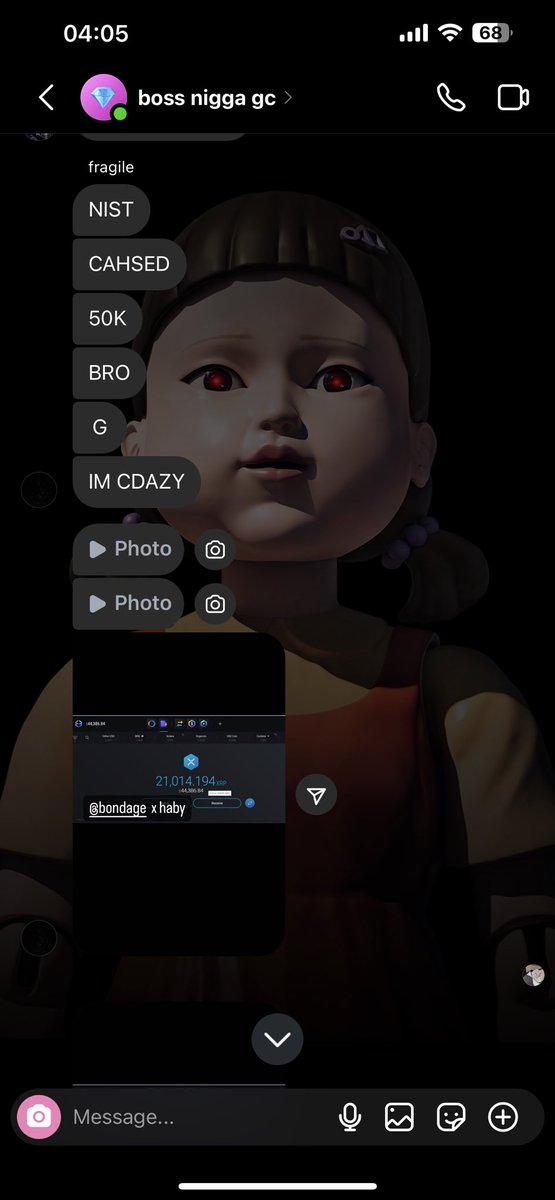
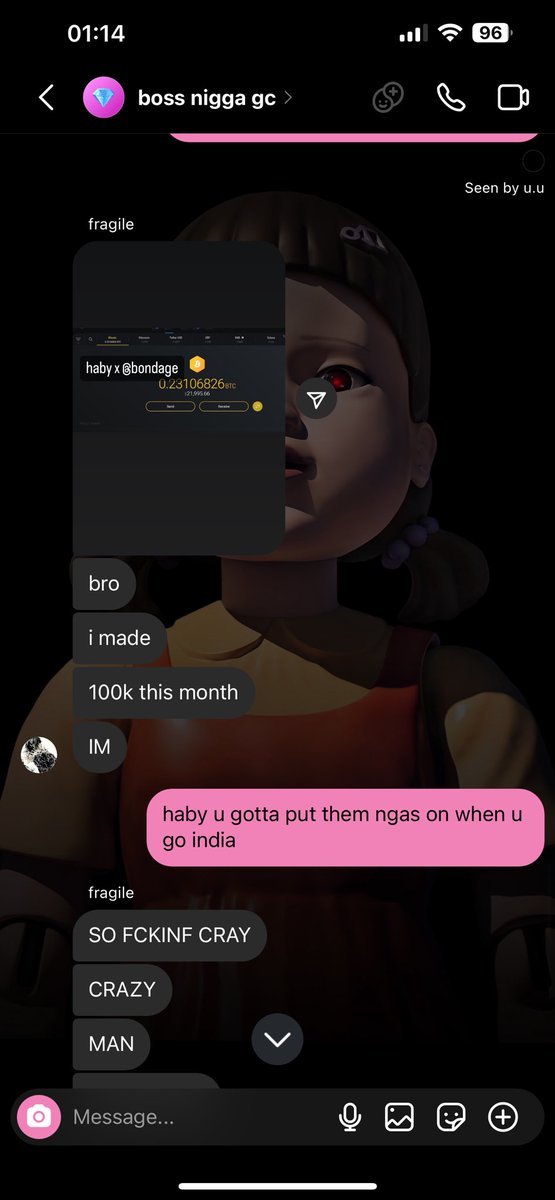
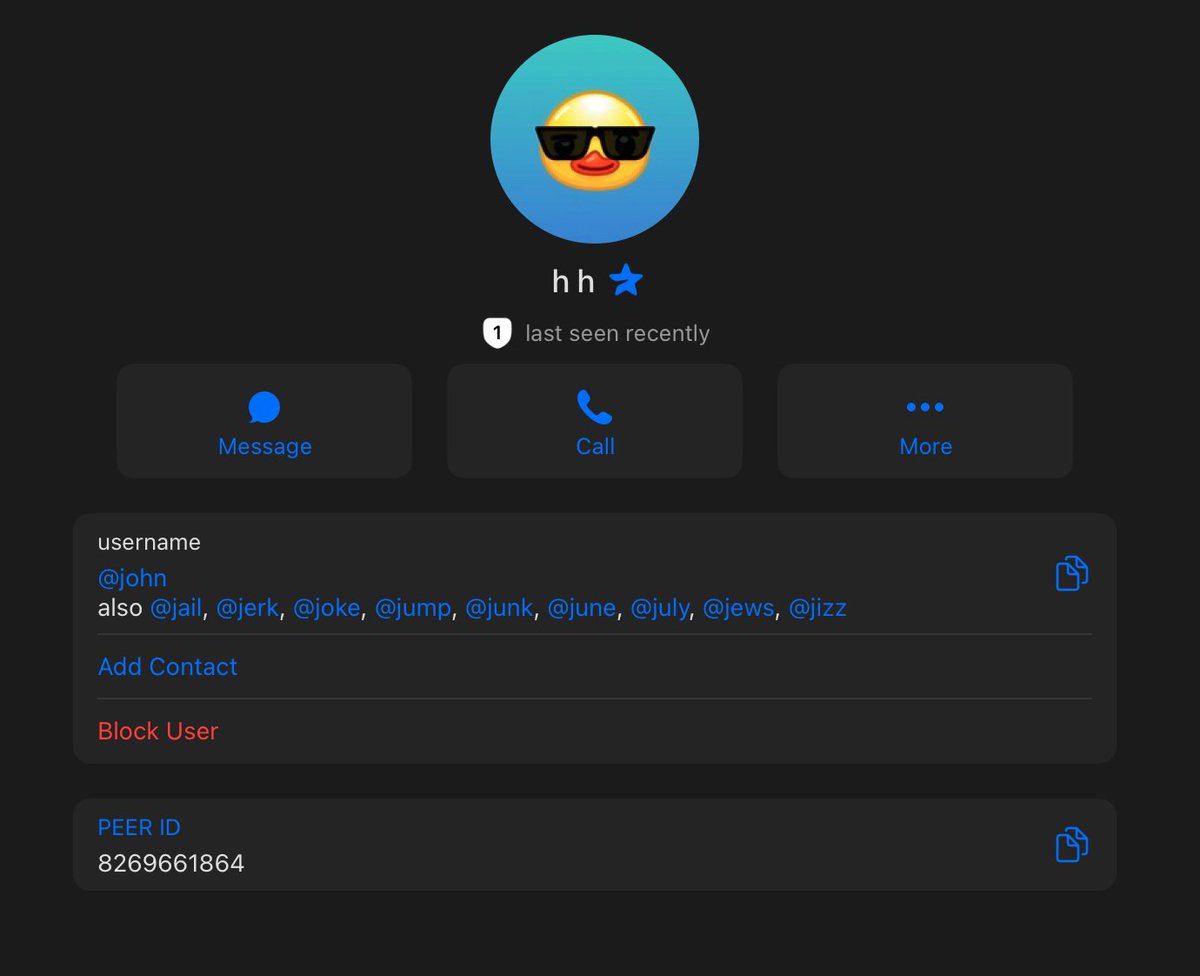
John has an extensive message history on Telegram flaunting his networth and calling others broke.
TG ID: 8269661864


0xe0f7a45a491d53f9361d35b4ef9908986d3b37b7
John has an extensive message history on Telegram flaunting his networth and calling others broke.
TG ID: 8269661864

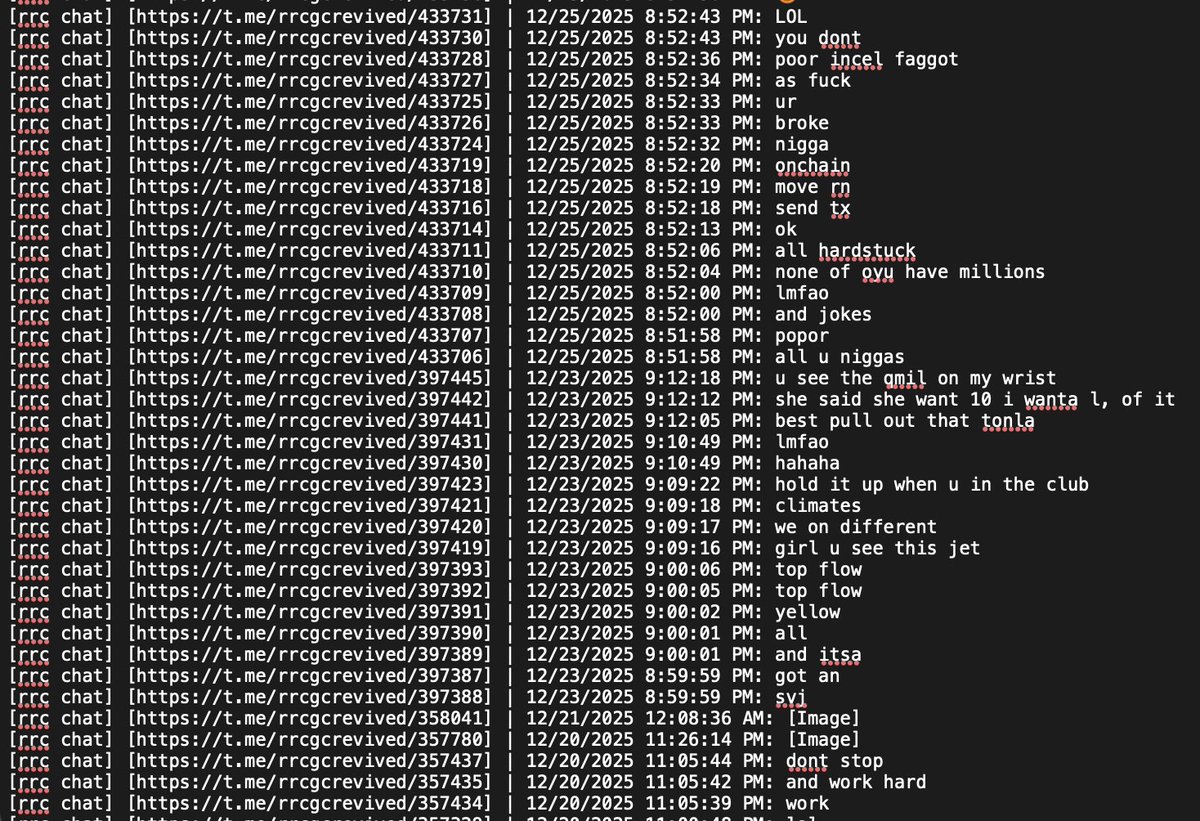
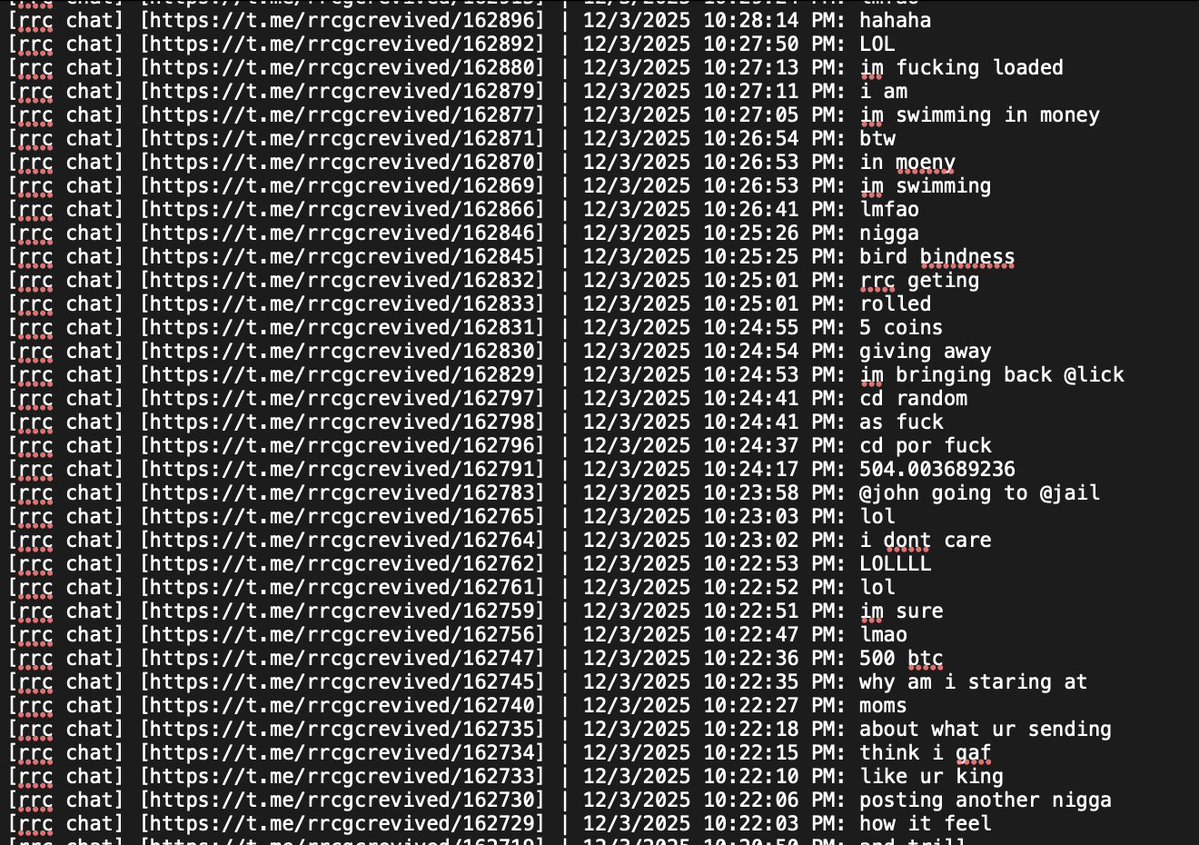
10/ Rumors circulating from cybercrime Telegram channels indicate John could be John Daghitia who was previously arrested in Sep 2025.
Though more research is needed to fully confirm.

Though more research is needed to fully confirm.


11/ Threat actors only continue to showing off stolen funds in leaked recordings rather than simply just staying quiet after an alleged theft from the US Government.
In this case John was ragebaited by Dritan into going band for band and the proof of ownership for these wallets makes it an easy future case for law enforcement.
In this case John was ragebaited by Dritan into going band for band and the proof of ownership for these wallets makes it an easy future case for law enforcement.
Update: John quickly removed all of the NFT usernames from his Telegram account and change his screenname after my post. 
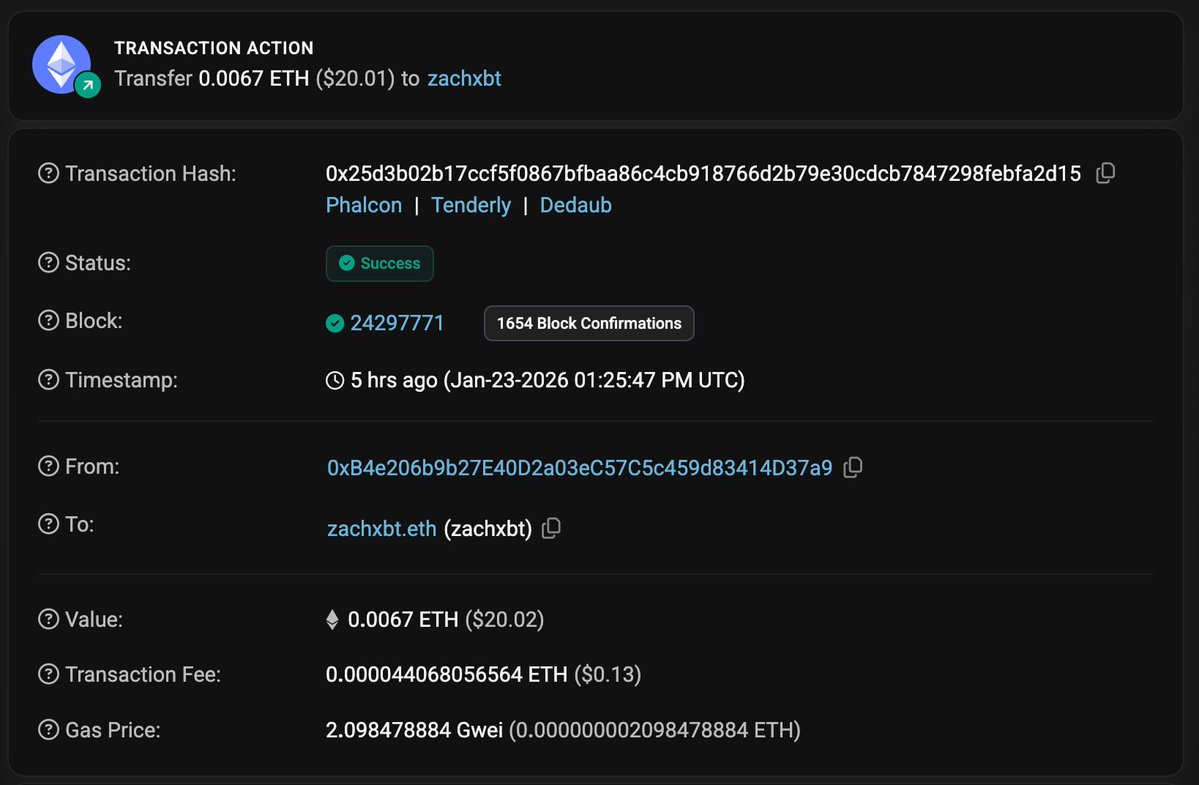
Update: John dusted my public address zachxbt.eth from one of the theft addresses.
Transaction hash
0x25d3b02b17ccf5f0867bfbaa86c4cb918766d2b79e30cdcb7847298febfa2d15
Transaction hash
0x25d3b02b17ccf5f0867bfbaa86c4cb918766d2b79e30cdcb7847298febfa2d15
• • •
Missing some Tweet in this thread? You can try to
force a refresh