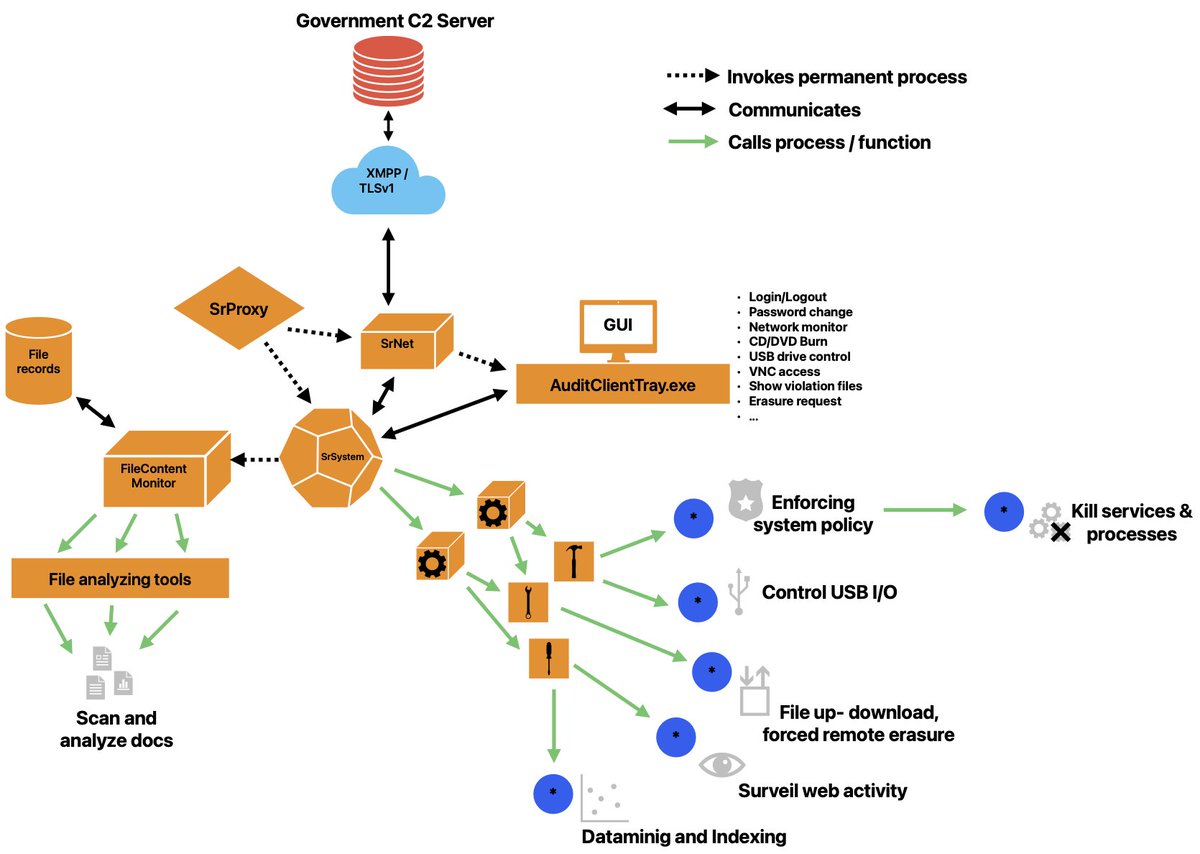
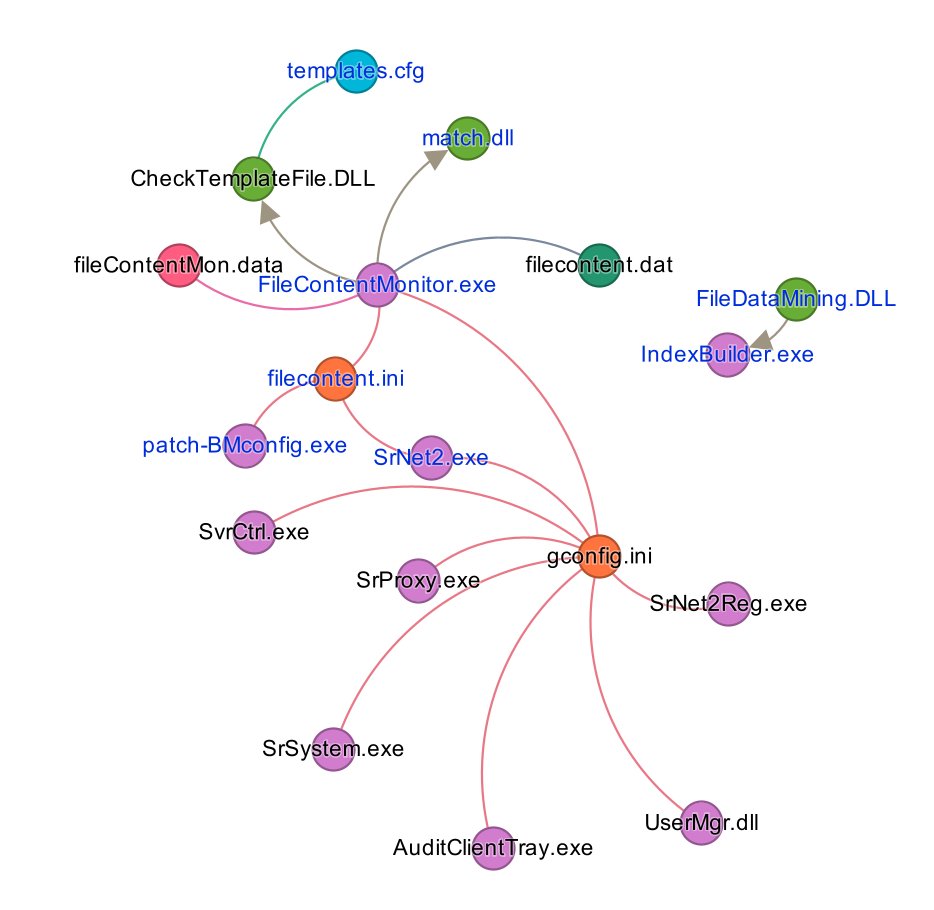
In 2024 we traveled to the Chinese city of Chengdu to find follow the trails of three APT groups: I-Soon, No Sugar Tech, Chengdu404 and Sichuan Silence. In this thread we will do some site visits, getting "thrown out" and talking to a former member of top management, all the while we are trailed by security. 1/10

Let's start with I-Soon: Gaining fame during a rather juicy leak of internal chats in 2024, that presented proof of their involvement in cyber attacks and information theft on behalf of regional Public Security Bureaus. After the story broke, the company got closed down and they abandoned their office. 2/10



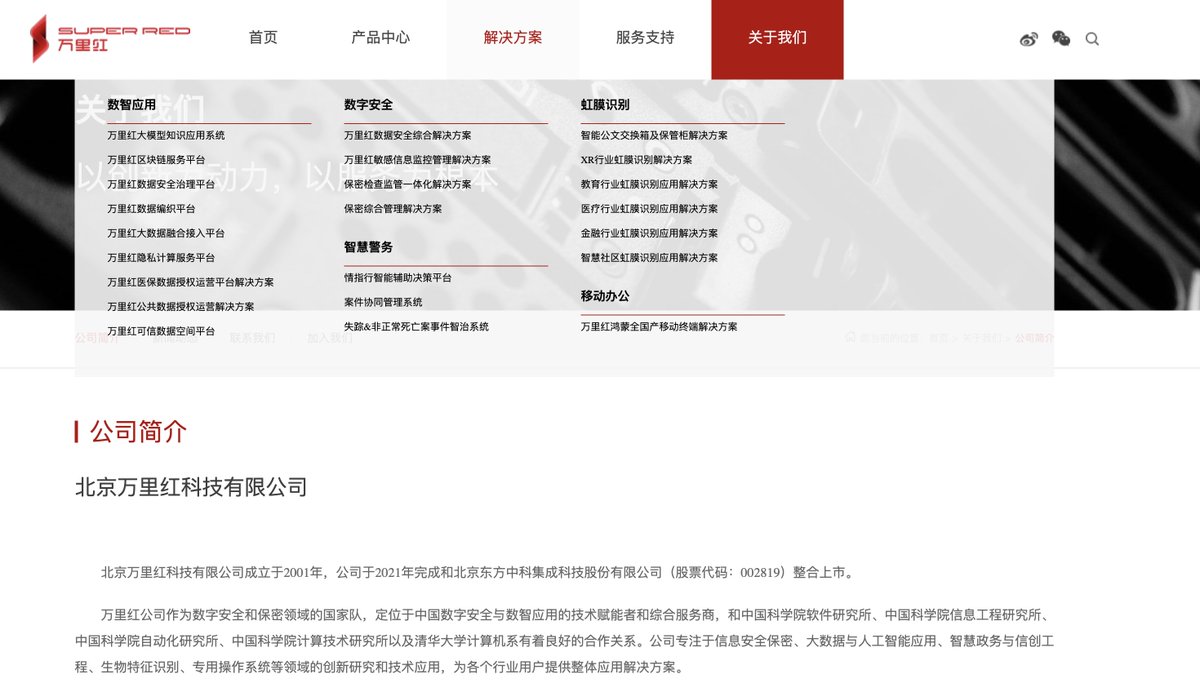
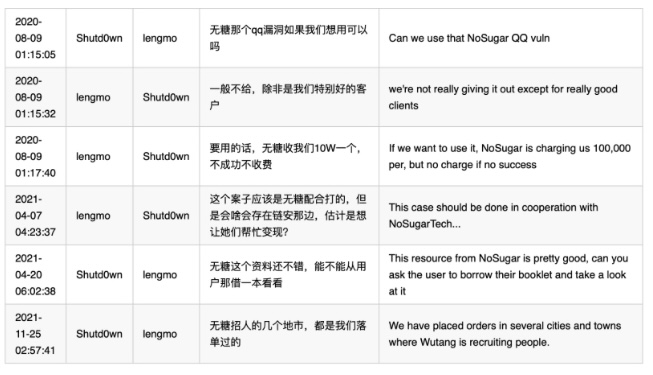
Chengdu was just one of their offices country wide, but by now the company seems defunct. In one chat they mentioned though that they acquired technology from a company named "No Sugar Tech", to get access to QQ accounts. 3/10 
Good for us, they also occupy a modern space in a bigger building at the outskirts of Chengdu. Unfortunately the access is restricted and despite calling up ahead and asking if we could visit and talk to them about the allegations, they refused. 4/10 



Interesting enough, the side of the building they are residing was labeled officially a 成都网络安全大厦. That means companies in that building, are part of a state sponsored initiative to ramp up cyber security capacities. 5/10 cloud.tencent.com/developer/news…

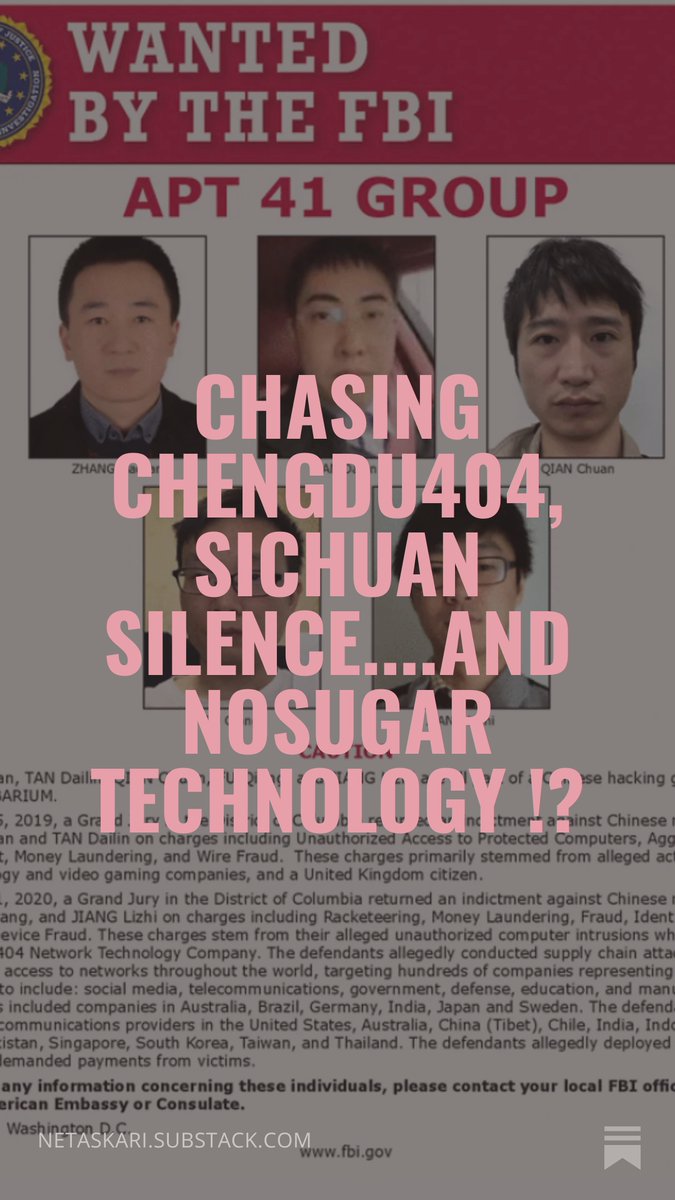
Next up is "Chengdu 404". A group that is, according to the FBI, employed members of the notorious APT41 group. Hidden away in a rather unassuming office building, far less impressive than NoSugarTech. 6/10 

An old picture from an FBI file we can see their old reception, but now the name has changed. Approaching the people in the office, they seemed to know what we were talking about, but did not engage. After a manager politely asked us about our business, he guided us in conversation out of the office, just to close the door seconds after we exited the premise, muttering "no comment". 7/10



Before we got "complemented" out of the door, we could still find remnants of their old relationships scattered on the reception desk. The office was still obviously operational, with some staff sitting behind screens. 8/10 



Last but not least "Sichuan Silence". A company tracked by the British cyber sec vendor Sophos for years and eventually tied down in a cat and mouse game. Under their registered address we can only find a set of banks and financial companies. Though not uncommon for Chinese corporate registers to be out of date, nobody in the office building ever heard of the company, despite having worked there for over 10 years. Maybe give the official number a call ? Its a cellphone after all... 9/10

To our surprise the phone gets picked up by a man who says he is part of the former management team of the company. He even agrees to meet on short notice ( rather unusual under such circumstances ). He meets us. But brings his own camera man with him. An "assistant" to record the conversation, for his own record. He doesn't want to be identified. While talking we are being watched from plain cloths security operatives. They call our interviewees cellphone several times, but he keeps talking. Denying all the claims of course but showing signs of bitterness how he thinks he was not protected by the authorities enough and admitting that after the story came out, his outlet had to close down. 9/10

If you want a more comprehensive read up on our little excursion into the Chengdu-scene, why not come over and check it out here: tinyurl.com/4efbkruj
• • •
Missing some Tweet in this thread? You can try to
force a refresh