Blog on Chinese cyber operations, online surveillance, always on the hunt for leaked documents : https://t.co/AwtprnaSoG | https://t.co/eVXinXn7NL
How to get URL link on X (Twitter) App



 Starting with the institution: the Xinjiang Police Academy is the main undergraduate training and education facility for the Ministry of Public Security
Starting with the institution: the Xinjiang Police Academy is the main undergraduate training and education facility for the Ministry of Public Security

 Let's start with I-Soon: Gaining fame during a rather juicy leak of internal chats in 2024, that presented proof of their involvement in cyber attacks and information theft on behalf of regional Public Security Bureaus. After the story broke, the company got closed down and they abandoned their office. 2/10
Let's start with I-Soon: Gaining fame during a rather juicy leak of internal chats in 2024, that presented proof of their involvement in cyber attacks and information theft on behalf of regional Public Security Bureaus. After the story broke, the company got closed down and they abandoned their office. 2/10

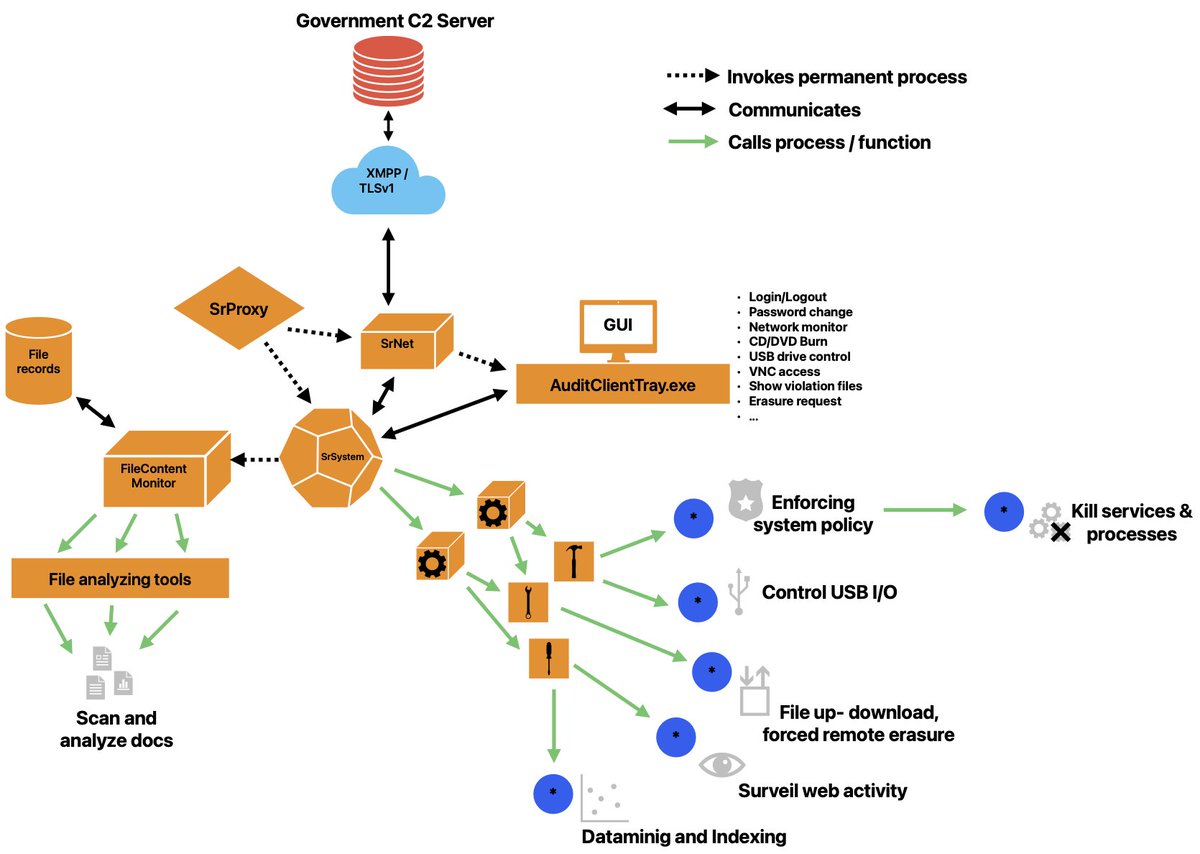
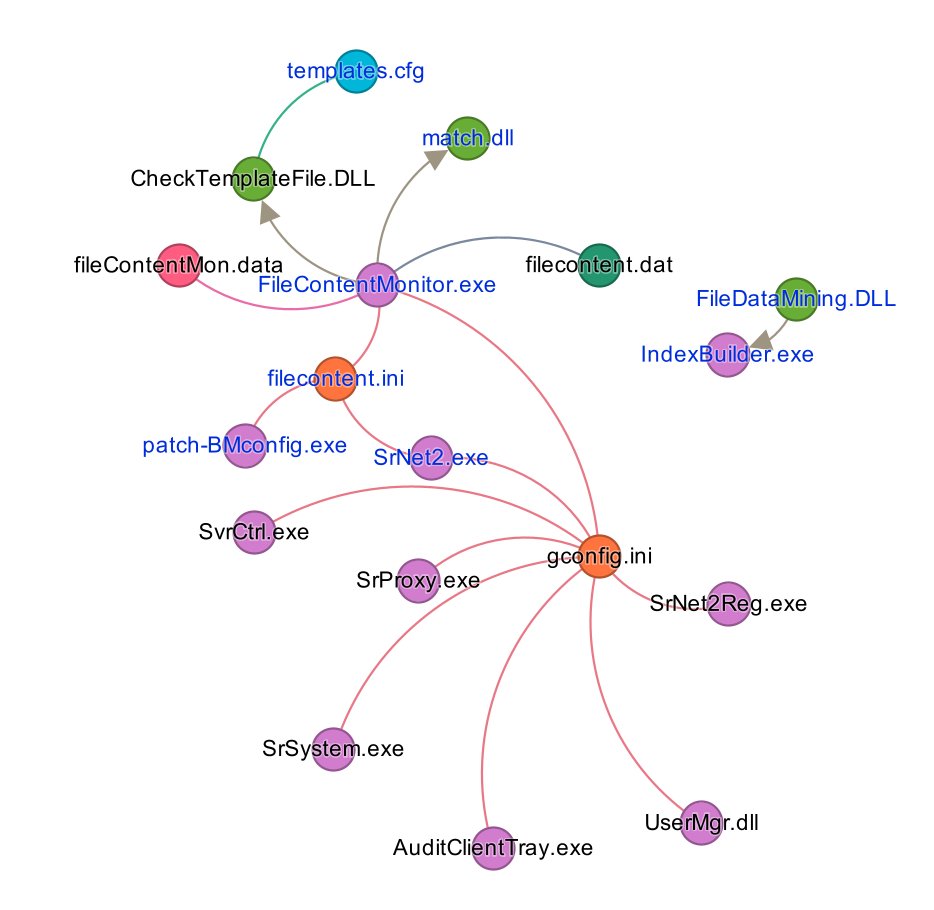
 Designed mainly for WinXP and Win7, it lodges itself rather deep inside the system to have full file system access, controls hardware/USB devices, dynamic content analysis and enumeration, provides network traffic proxies and enables remote control and granular file behavior. 2/9
Designed mainly for WinXP and Win7, it lodges itself rather deep inside the system to have full file system access, controls hardware/USB devices, dynamic content analysis and enumeration, provides network traffic proxies and enables remote control and granular file behavior. 2/9