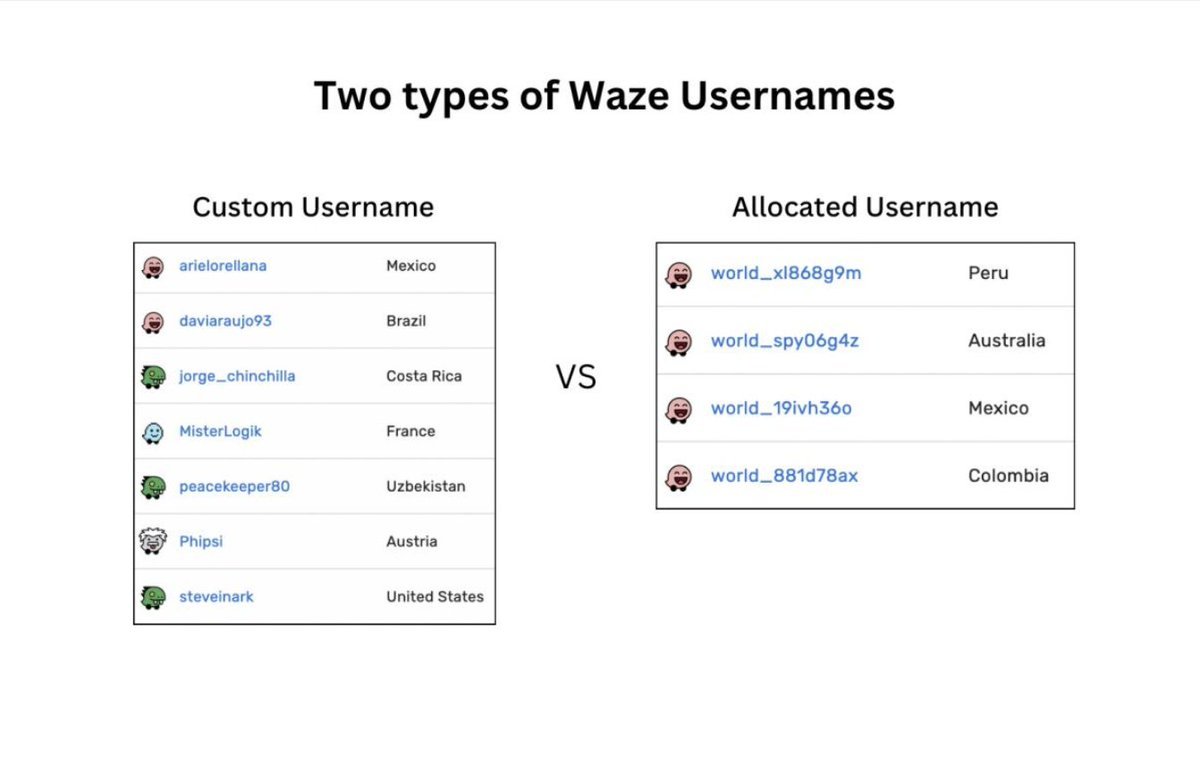
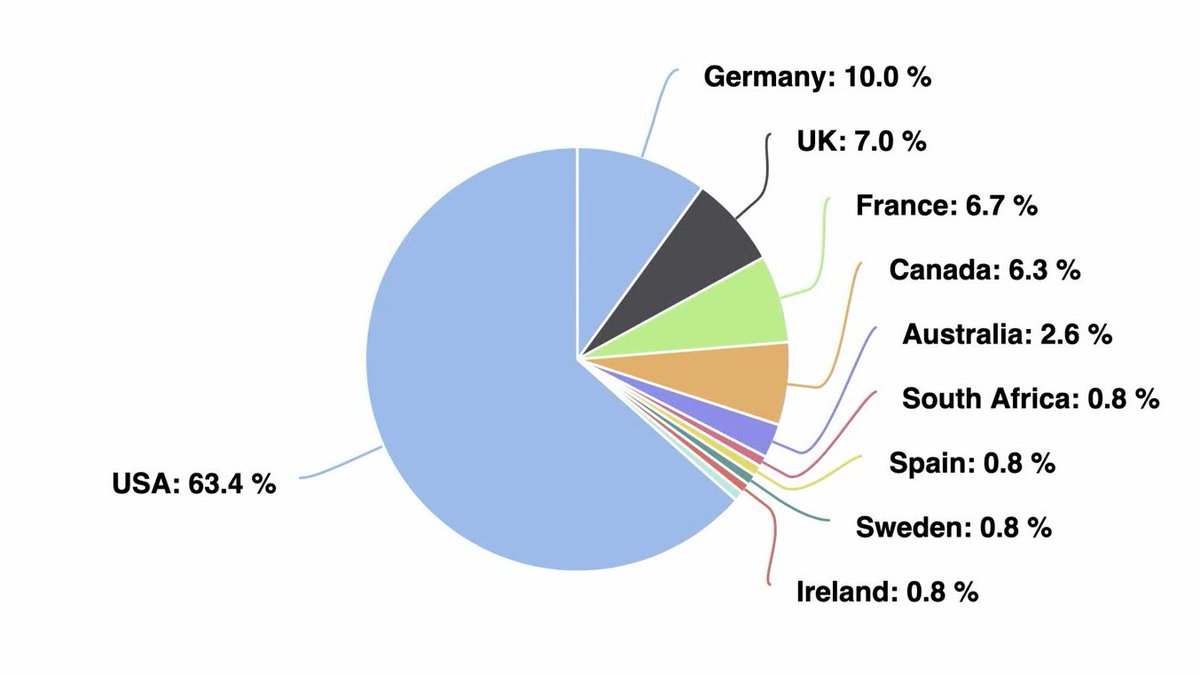
‼️ BREAKING: Researchers have uncovered secret AI surveillance projects linked to KYC provider Persona and OpenAI, sending user data to the US government.
Code references include intelligence program codenames "Project SHADOW" and "Project LEGION."
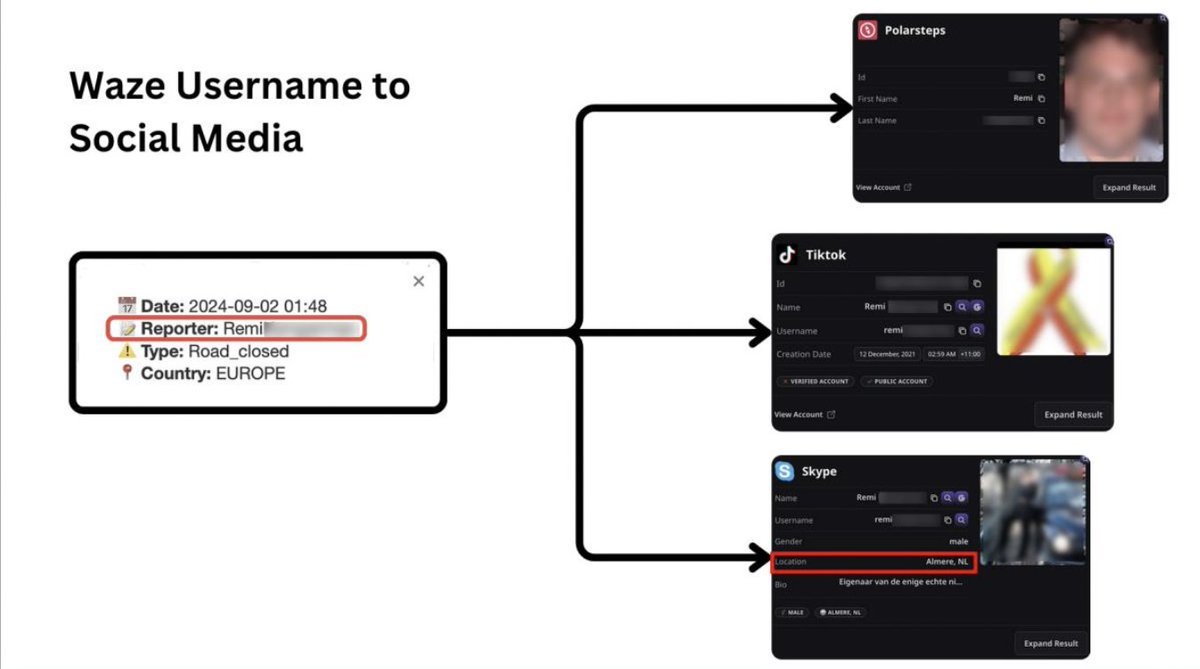
Analysis of source code revealed OpenAI's user verification systems includes biometric tracking, facial scanning, political screening, and intelligence reporting.
Researchers also discovered ONYX on Persona's government server — matching ICE's $4.2M AI surveillance tool — which scrapes social media and the dark web, builds digital footprints, tracks emotional sentiment, assigns risk scores across 300+ platforms and 28B+ data points, and flags individuals for "violent tendencies."
None of it was hidden. It was all internet-facing.

Code references include intelligence program codenames "Project SHADOW" and "Project LEGION."
Analysis of source code revealed OpenAI's user verification systems includes biometric tracking, facial scanning, political screening, and intelligence reporting.
Researchers also discovered ONYX on Persona's government server — matching ICE's $4.2M AI surveillance tool — which scrapes social media and the dark web, builds digital footprints, tracks emotional sentiment, assigns risk scores across 300+ platforms and 28B+ data points, and flags individuals for "violent tendencies."
None of it was hidden. It was all internet-facing.
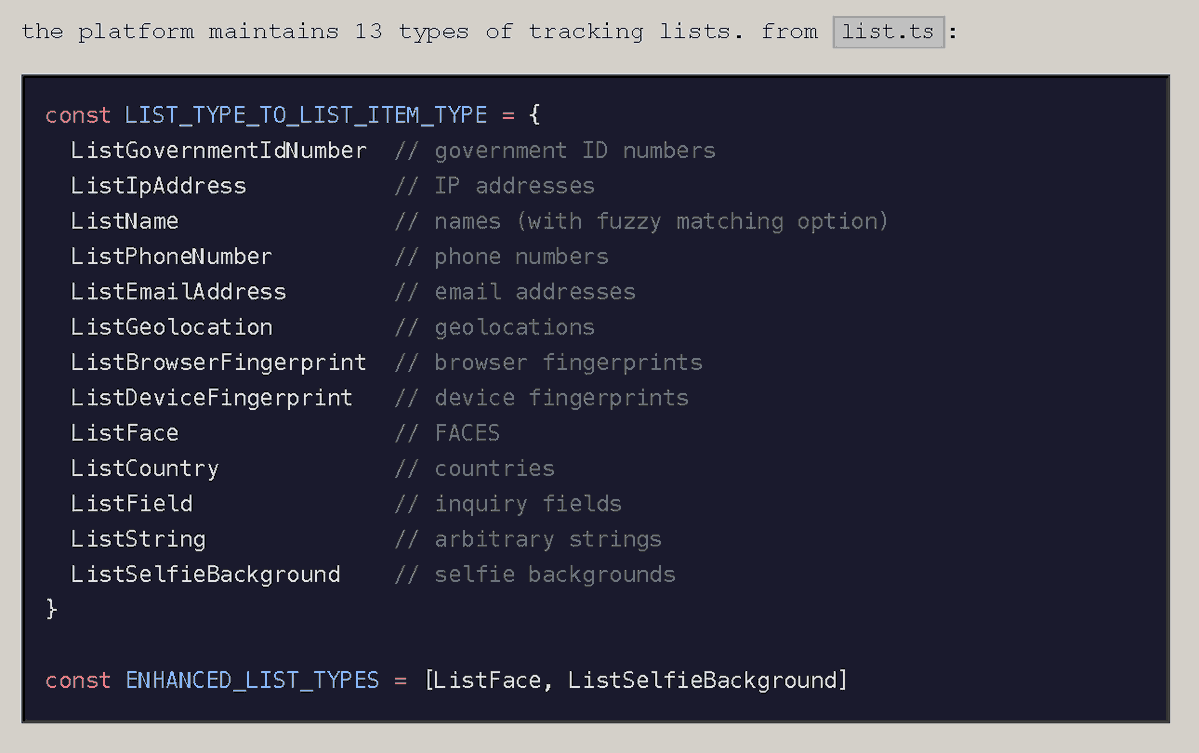
Here is a list of some of Persona's customers:
- OpenAI (ChatGPT)
- Discord
- LinkedIn
- DoorDash
- Etsy
- Brex
- Coursera
- Carahsoft
- Swan Bitcoin
- Mercury
- Wealthsimple
- Branch
- WeTravel
- Grailed
- Eaze
- Stifel Financial Corp
- First Republic
- Fire & Flower Holdings
- Serviap Global
- OpenAI (ChatGPT)
- Discord
- DoorDash
- Etsy
- Brex
- Coursera
- Carahsoft
- Swan Bitcoin
- Mercury
- Wealthsimple
- Branch
- WeTravel
- Grailed
- Eaze
- Stifel Financial Corp
- First Republic
- Fire & Flower Holdings
- Serviap Global
The researchers writeup can be found here: vmfunc.re/blog/persona
• • •
Missing some Tweet in this thread? You can try to
force a refresh