
Agentless Linux security. No endpoint agents and no drama. Linux malware, forensics, intrusion detection, and hacking. Founder @SandflySecurity.
3 subscribers
How to get URL link on X (Twitter) App

https://twitter.com/HackingLZ/status/1970183998875066730Vendors get invited into a bake-off or evaluation by someone. They all immediately spin up the marketing teams to do the "best". By "best" we mean trying to game things to make sure they score the highest. This is not a surprise.
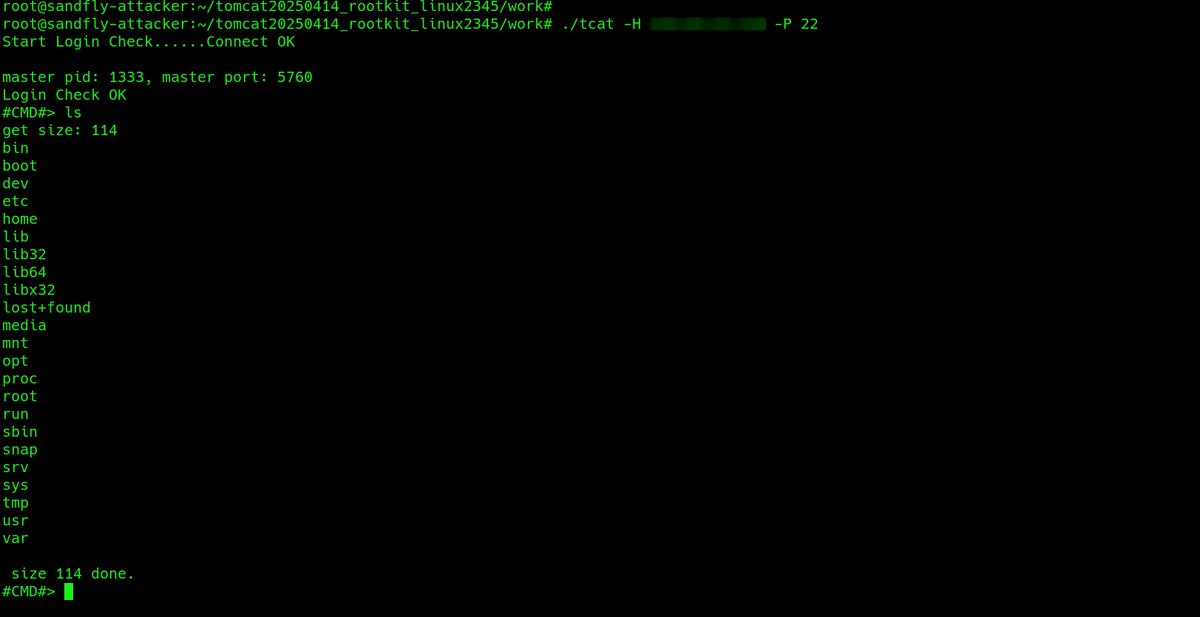

 First, this rootkit is based on the khook library. This is a common rootkit base that allows full stealth for processes, network connections, files, etc. This is what @SandflySecurity sees when the rootkit is active. It's only stealthy if you aren't looking!
First, this rootkit is based on the khook library. This is a common rootkit base that allows full stealth for processes, network connections, files, etc. This is what @SandflySecurity sees when the rootkit is active. It's only stealthy if you aren't looking! 


 Mosler made excellent vaults and safes of superior security and design. The round doors are my favorite as they are the absolute strongest design. The door rotates and locks into lugs when you turn the T handle. The bolts just keep the door from spinning unlocked.
Mosler made excellent vaults and safes of superior security and design. The round doors are my favorite as they are the absolute strongest design. The door rotates and locks into lugs when you turn the T handle. The bolts just keep the door from spinning unlocked. 

https://twitter.com/qualadder/status/1954183677467869408
 ISM Jeweler's safe on display floor of safe company. Attacked with oxyfuel torch. This is Hollywood tier non-sense and would never work on this type of safe.
ISM Jeweler's safe on display floor of safe company. Attacked with oxyfuel torch. This is Hollywood tier non-sense and would never work on this type of safe. 




 SCTP is a protocol mainly used for telcos. It provides reliable transport like TCP, but is not TCP. Be aware that network monitoring may not be paying close attention to SCTP and packet filters can be mis-configured to not block it.
SCTP is a protocol mainly used for telcos. It provides reliable transport like TCP, but is not TCP. Be aware that network monitoring may not be paying close attention to SCTP and packet filters can be mis-configured to not block it.


 The /proc/net directory contains files that shows protocol use on Linux. The /proc/net/packet file shows you all open raw/packet sockets which means the process is sniffing traffic. The file shows you open inodes and who owns them, but doesn't list the process doing the deed.
The /proc/net directory contains files that shows protocol use on Linux. The /proc/net/packet file shows you all open raw/packet sockets which means the process is sniffing traffic. The file shows you open inodes and who owns them, but doesn't list the process doing the deed. 

 First, it only encrypts the binary at rest on disk. It is not encrypting the running process. This will evade legacy file scanning with YARA, etc. that is unreliable on Linux and I don't recommend using. The running process has no encryption so that is our detection target.
First, it only encrypts the binary at rest on disk. It is not encrypting the running process. This will evade legacy file scanning with YARA, etc. that is unreliable on Linux and I don't recommend using. The running process has no encryption so that is our detection target.

 When you run a rootkit like Reptile, they often come with the ability to hide a directory if named a certain way. Any directory with the name "reptile" in it will be hidden with this rootkit as you see below under /lib/udev.
When you run a rootkit like Reptile, they often come with the ability to hide a directory if named a certain way. Any directory with the name "reptile" in it will be hidden with this rootkit as you see below under /lib/udev. 


 When you look at the process listing, you'll see a shell running. But the shell will have the interactive (-i) flag. In general, this isn't terribly common and is a good place to put your attention.
When you look at the process listing, you'll see a shell running. But the shell will have the interactive (-i) flag. In general, this isn't terribly common and is a good place to put your attention. 

 Using SSH with passwords means a trojanized binary will steal any credential of someone logging in. If you are not using public keys with SSH on Ubiquti and other devices (which prevents this), at least use a unique password with *each* device. Do not re-use passwords.
Using SSH with passwords means a trojanized binary will steal any credential of someone logging in. If you are not using public keys with SSH on Ubiquti and other devices (which prevents this), at least use a unique password with *each* device. Do not re-use passwords. 

https://twitter.com/haxrob/status/1762821513680732222

 As disclosed, it runs as [syslogd] after exec. This is easily seen with a ps -auxwf command that it is sitting out all alone and not part of the main [kthreadd] process PID 2.
As disclosed, it runs as [syslogd] after exec. This is easily seen with a ps -auxwf command that it is sitting out all alone and not part of the main [kthreadd] process PID 2.



https://twitter.com/BleepinComputer/status/1713979860404576348
 Backdoor PAM authentication and grab passwords used to login. The stolen passwords are dropped in this file with simple XOR encryption:
Backdoor PAM authentication and grab passwords used to login. The stolen passwords are dropped in this file with simple XOR encryption:



 The "date" command was flagged on a Linux host. I removed the explanation why it was detected so we could see what ChatGPT could make of it as a forensic analyst without any help. The initial observations are an excellent starting point for a Linux investigation:
The "date" command was flagged on a Linux host. I removed the explanation why it was detected so we could see what ChatGPT could make of it as a forensic analyst without any help. The initial observations are an excellent starting point for a Linux investigation: 


 ChatGPT summarizes the data, and even pulls out that the process deleted flag is set to true so it's masquerading and also deleted itself to hide.
ChatGPT summarizes the data, and even pulls out that the process deleted flag is set to true so it's masquerading and also deleted itself to hide. 
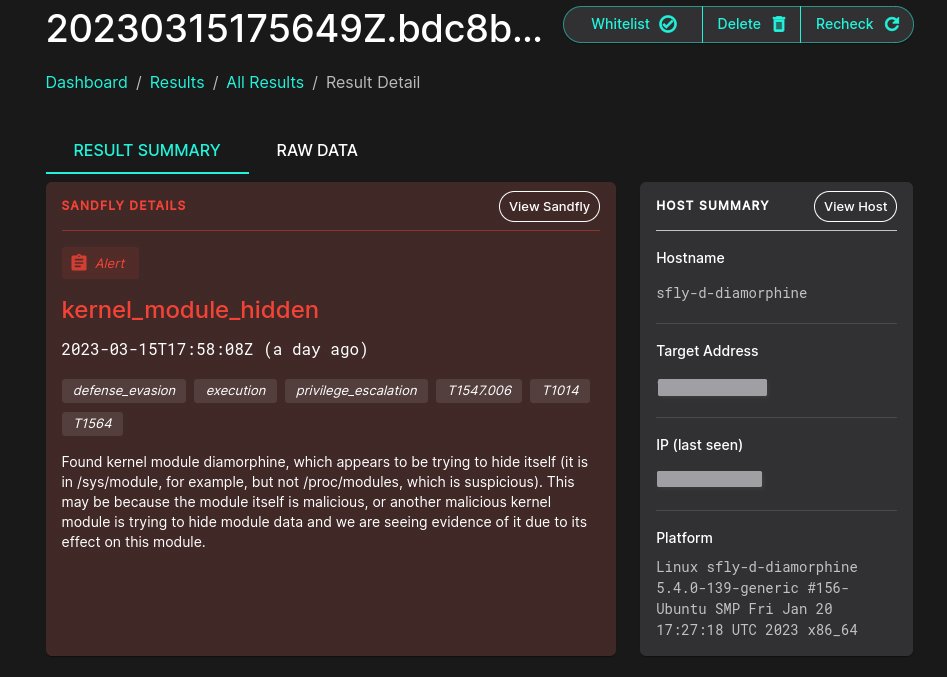

 I ask it whether this kernel module called "Diamorphine" that was found is suspicious. The answer is concise and correct. It's cribbing our explanation a little, but still augmented with other data so we'll let it go.
I ask it whether this kernel module called "Diamorphine" that was found is suspicious. The answer is concise and correct. It's cribbing our explanation a little, but still augmented with other data so we'll let it go. 


 First we'll paste in the raw event JSON and ask it to interpret it. ChatGPT does a great job understanding the fields without any prompting. It knows a security tool generated it and identifies key fields rapidly.
First we'll paste in the raw event JSON and ask it to interpret it. ChatGPT does a great job understanding the fields without any prompting. It knows a security tool generated it and identifies key fields rapidly. 


 We have checks for sniffer activity in the incident response modules. They are not run by default as they can be noisy at times, but we do have a tuned version that is not noisy. Select the hosts you want scanned, then in sandfly selection use the filter to find "sniffer".
We have checks for sniffer activity in the incident response modules. They are not run by default as they can be noisy at times, but we do have a tuned version that is not noisy. Select the hosts you want scanned, then in sandfly selection use the filter to find "sniffer". 

https://twitter.com/GossiTheDog/status/1522964028284411907
 #BPFdoor uses eBPF to sniff traffic. It can bypass firewall rules to see packets. When it starts it writes to /var/run/haldrund.pid which is obfuscated as hex in the code. It also masquerades its name using a number of pre-defined command line values below:
#BPFdoor uses eBPF to sniff traffic. It can bypass firewall rules to see packets. When it starts it writes to /var/run/haldrund.pid which is obfuscated as hex in the code. It also masquerades its name using a number of pre-defined command line values below: 