
add my blog to your RSS reader or something. also @retr0id@retr0.id, at://retr0.id
How to get URL link on X (Twitter) App


https://twitter.com/ProgramMax/status/1638217206180741121
 - Take a screenshot.
- Take a screenshot.
 Step 1:
Step 1: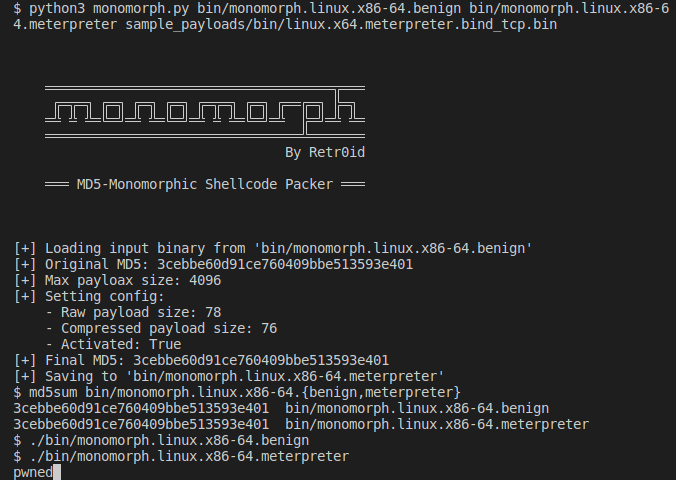
 This tool makes hashquines trivial:
This tool makes hashquines trivial: ![C source code screenshot: static char message[] = "My](https://pbs.twimg.com/media/FdnRWgnXgAAXT_d.jpg)

https://twitter.com/0xabad1dea/status/365863999520251906
 This was particularly tricky to make work because the image data in a PNG needs to have a valid adler32 checksum, *and* a valid crc32 checksum.
This was particularly tricky to make work because the image data in a PNG needs to have a valid adler32 checksum, *and* a valid crc32 checksum.

 There's not a lot going on inside the adapter (I did test it first, and it does support both charging and data)
There's not a lot going on inside the adapter (I did test it first, and it does support both charging and data) 

 This is working code - I might try writing something non-trivial later, to see if it's actually practical.
This is working code - I might try writing something non-trivial later, to see if it's actually practical.
 You can use this script to decode the hidden message in the above tweet: gist.github.com/DavidBuchanan3…
You can use this script to decode the hidden message in the above tweet: gist.github.com/DavidBuchanan3…
https://twitter.com/rqu50/status/1485876188652310534

 I believe this fault pattern is indicative of a successful round 9 fault.
I believe this fault pattern is indicative of a successful round 9 fault. 



 The source is also available on Github, for anyone who can't extract the above image:
The source is also available on Github, for anyone who can't extract the above image: