
Cryptogopher / Go crypto maintainer / @kateconger-knower / RC F'13, F2'17 / #BlackLivesMatter / he+him
https://t.co/ZE4RtJ1xqD / https://t.co/qfth7zr00W / https://t.co/j1grpEm8uR
How to get URL link on X (Twitter) App





 I believe Open Source will change one way or another, so I'm putting my (lack of) money where my mouth is, and doing what I think can best catalyze the change I want: becoming a professional, independent Open Source maintainer myself 👨💻💼
I believe Open Source will change one way or another, so I'm putting my (lack of) money where my mouth is, and doing what I think can best catalyze the change I want: becoming a professional, independent Open Source maintainer myself 👨💻💼

 Ah, here's the OpenSSL advisory.
Ah, here's the OpenSSL advisory.https://twitter.com/taviso/status/1503771787733069826



https://twitter.com/FiloSottile/status/1342293403321692162@tqbf Already made it to $250!
https://twitter.com/tqbf/status/1350571461468151813


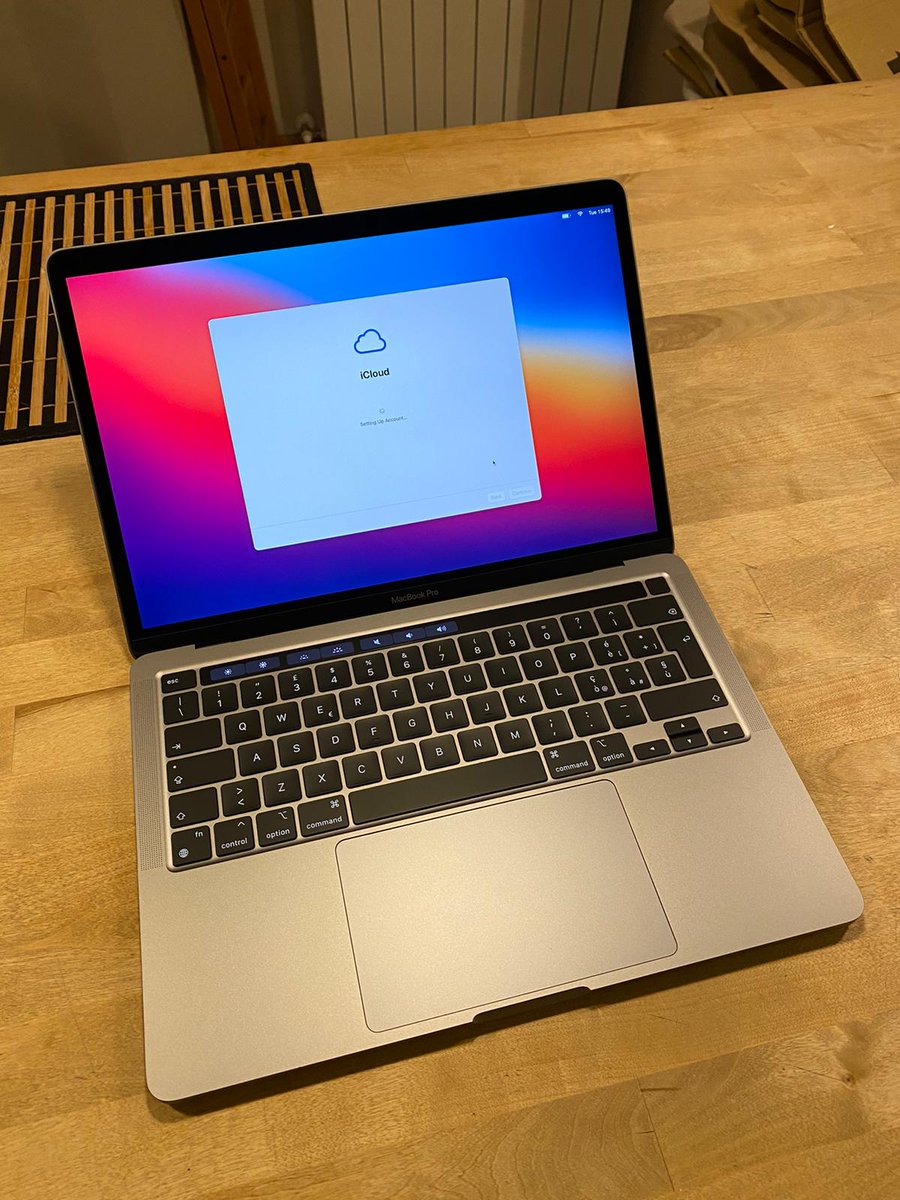
 Well, it couldn't be too easy I suppose.
Well, it couldn't be too easy I suppose.
https://twitter.com/kashhill/status/1291772231991926786


 CLIENT RETENTION BONUSES. For therapists!
CLIENT RETENTION BONUSES. For therapists!https://twitter.com/keithboykin/status/1266933018570219520
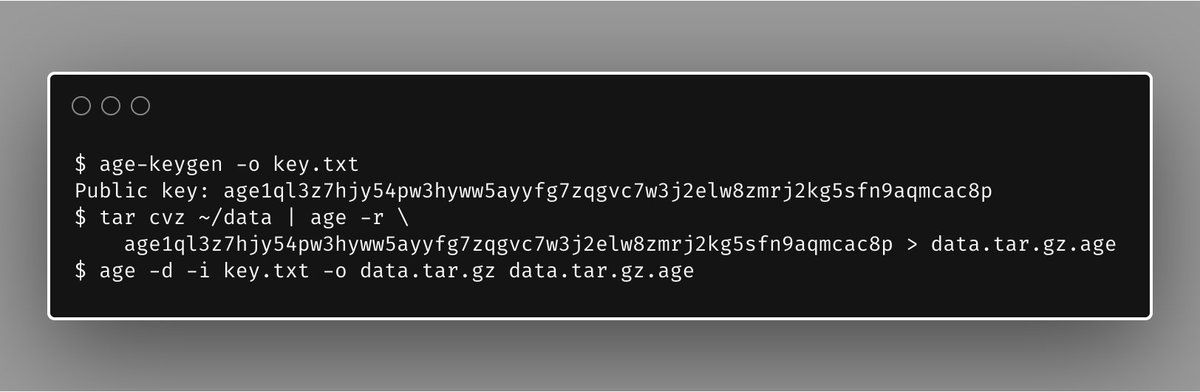
https://twitter.com/agetool/status/1210698705671802881Easy UNIX piping! No config options! Modern crypto! No keyrings! Public keys that fit in a tweet! No more looking up how to encrypt a file on StackOverflow. 💥

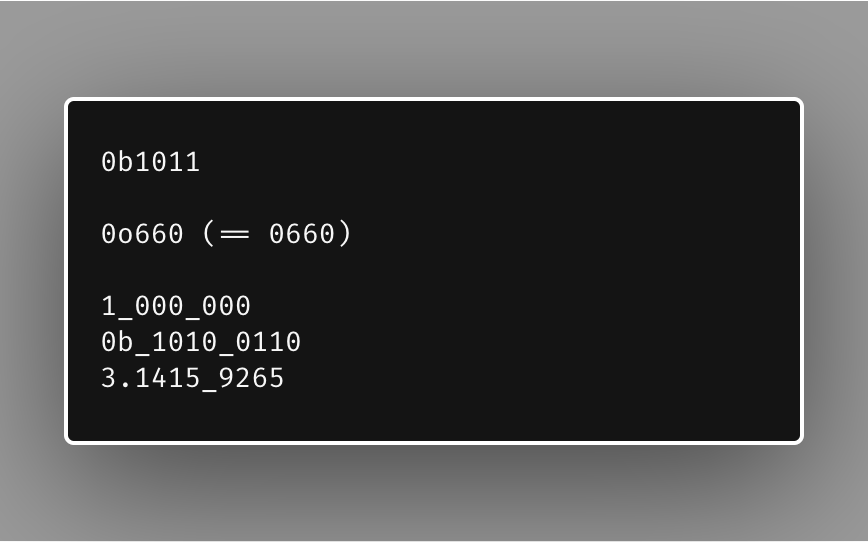
https://twitter.com/bradfitz/status/1168967013001244673There were more than 1750 commits since Go 1.12, so I'm going to miss some awesomeness here. Of course, I can't claim credit for almost any of this.
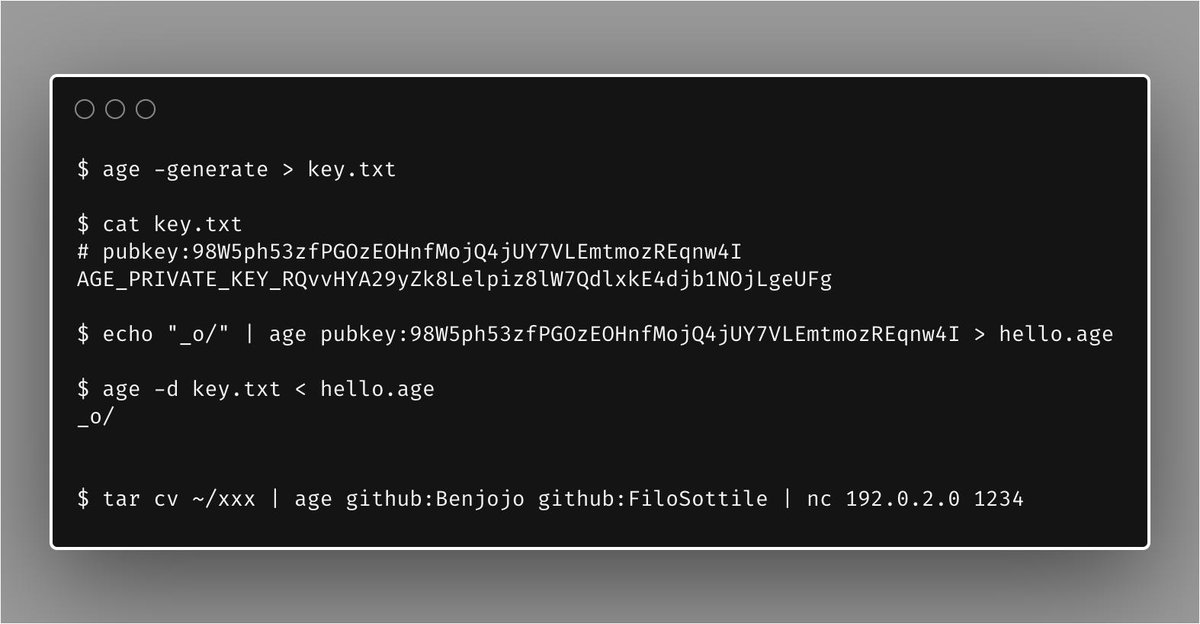



 I'm convinced that while DNS-over-TLS makes more sense as a protocol than DNS-over-HTTPS (DNS requests are small and have unique IDs), the DNS software ecosystem is just unprepared to handle DoT, while there's solid software to reuse for DoH.
I'm convinced that while DNS-over-TLS makes more sense as a protocol than DNS-over-HTTPS (DNS requests are small and have unique IDs), the DNS software ecosystem is just unprepared to handle DoT, while there's solid software to reuse for DoH.