
Staff Security Researcher @datadoghq | DEF CON/Black Hat main stage speaker | Created https://t.co/QGWMJjuBzE
How to get URL link on X (Twitter) App










https://twitter.com/ThinkstCanary/status/1490749432970850310Please note: I'm not focusing on the CanaryToken product itself. Instead I'll be describing validating regular stolen AWS credentials.




 So it looks like you can steal IAM credentials from a EC2 instance and then you can create your own EC2 but stick it in a private subnet along side a ton of VPC Endpoints (to be clear this is still remarkably painful and annoyting, but at least for now it wont show in GuardDuty
So it looks like you can steal IAM credentials from a EC2 instance and then you can create your own EC2 but stick it in a private subnet along side a ton of VPC Endpoints (to be clear this is still remarkably painful and annoyting, but at least for now it wont show in GuardDuty
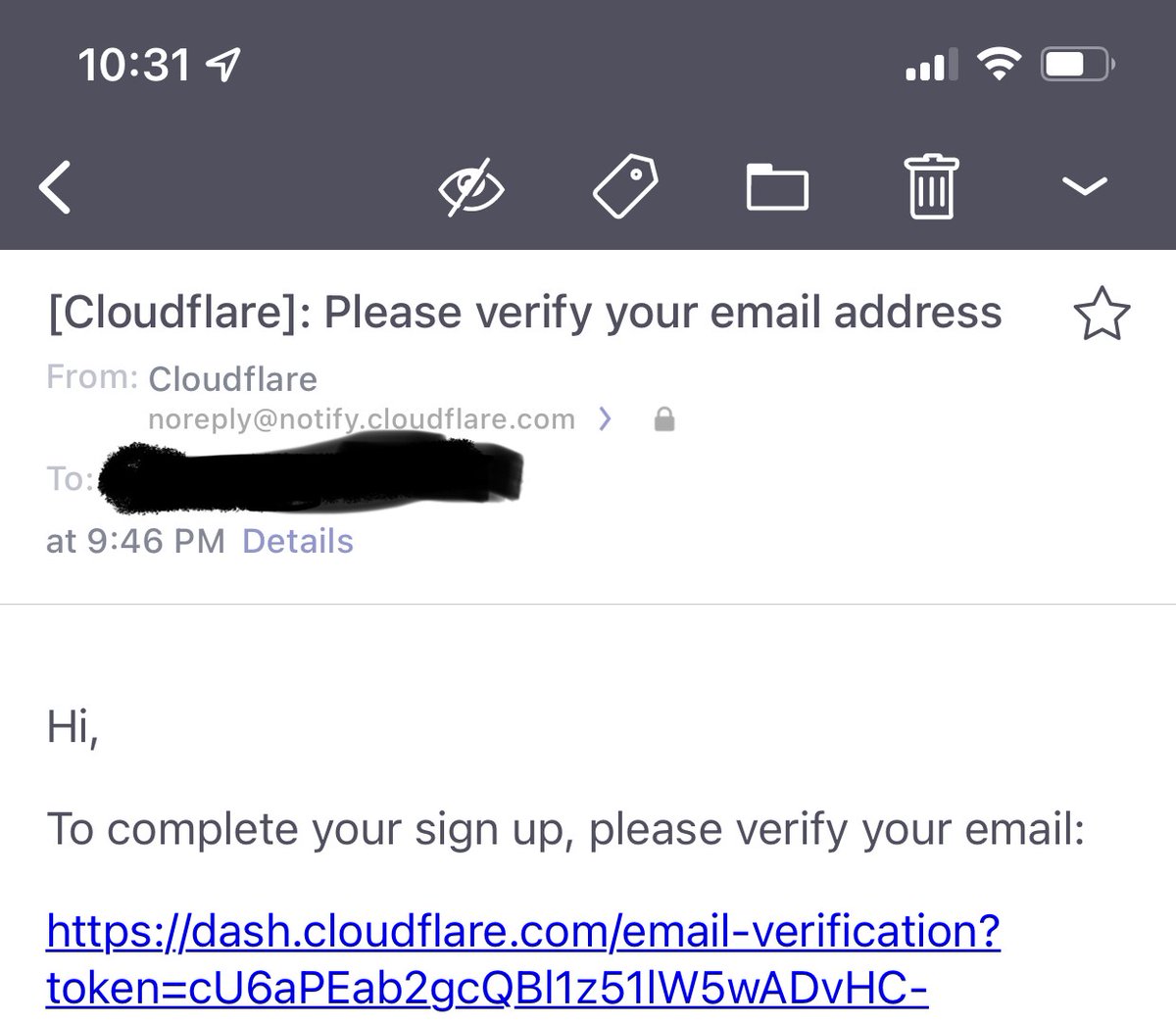
 This had me scrambling. Why would someone register a Cloudflare account in my name? What would someone get out of doing this? Did I accidentally do this? What do I know about Cloudflare? Is this phishing? (Couldn't be phishing, this is a terrible pretext. Domains checked out).
This had me scrambling. Why would someone register a Cloudflare account in my name? What would someone get out of doing this? Did I accidentally do this? What do I know about Cloudflare? Is this phishing? (Couldn't be phishing, this is a terrible pretext. Domains checked out).