senior red team engineer @snowflake |
former grocery store bagger
He/him
:wq!
How to get URL link on X (Twitter) App

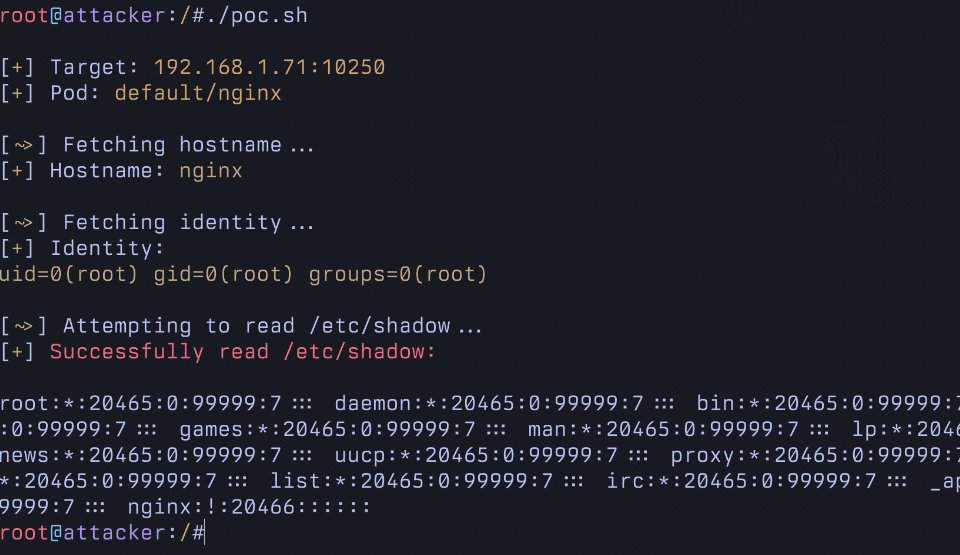
 I initially disclosed this in November of 2025 to the Kubernetes bug bounty program.
I initially disclosed this in November of 2025 to the Kubernetes bug bounty program. 

 NixOS (not to be confused with *nix or the Nix package manger) is a Linux distro that aims to be reproducible, declarative, and reliable. It has a few different ways of accomplishing this:
NixOS (not to be confused with *nix or the Nix package manger) is a Linux distro that aims to be reproducible, declarative, and reliable. It has a few different ways of accomplishing this:

 2. Flameshot: Without a doubt the best screenshot utility. (Yes, even better than greenshot)
2. Flameshot: Without a doubt the best screenshot utility. (Yes, even better than greenshot)