
Christian Family Man, CEO of Patriot Consulting (Microsoft Security Partner) Author of "Securing Microsoft 365" Microsoft MVP (Security) (2020-present)
2 subscribers
How to get URL link on X (Twitter) App


 My use case: remove inactive guests. Clicking on the link in the warning message takes you do this docs page: (TL;DR: "some of what you used to own in P2 now requires an additional purchase 😡 ) How can you remove things I paid for?
My use case: remove inactive guests. Clicking on the link in the warning message takes you do this docs page: (TL;DR: "some of what you used to own in P2 now requires an additional purchase 😡 ) How can you remove things I paid for?

 there are lots of caveats, such as if you use Group-Based licensing to apply the M365 E5 license, then you have to do this weird step where you disable and re-enable the Advanced Audit feature. docs.microsoft.com/en-us/microsof…
there are lots of caveats, such as if you use Group-Based licensing to apply the M365 E5 license, then you have to do this weird step where you disable and re-enable the Advanced Audit feature. docs.microsoft.com/en-us/microsof… 

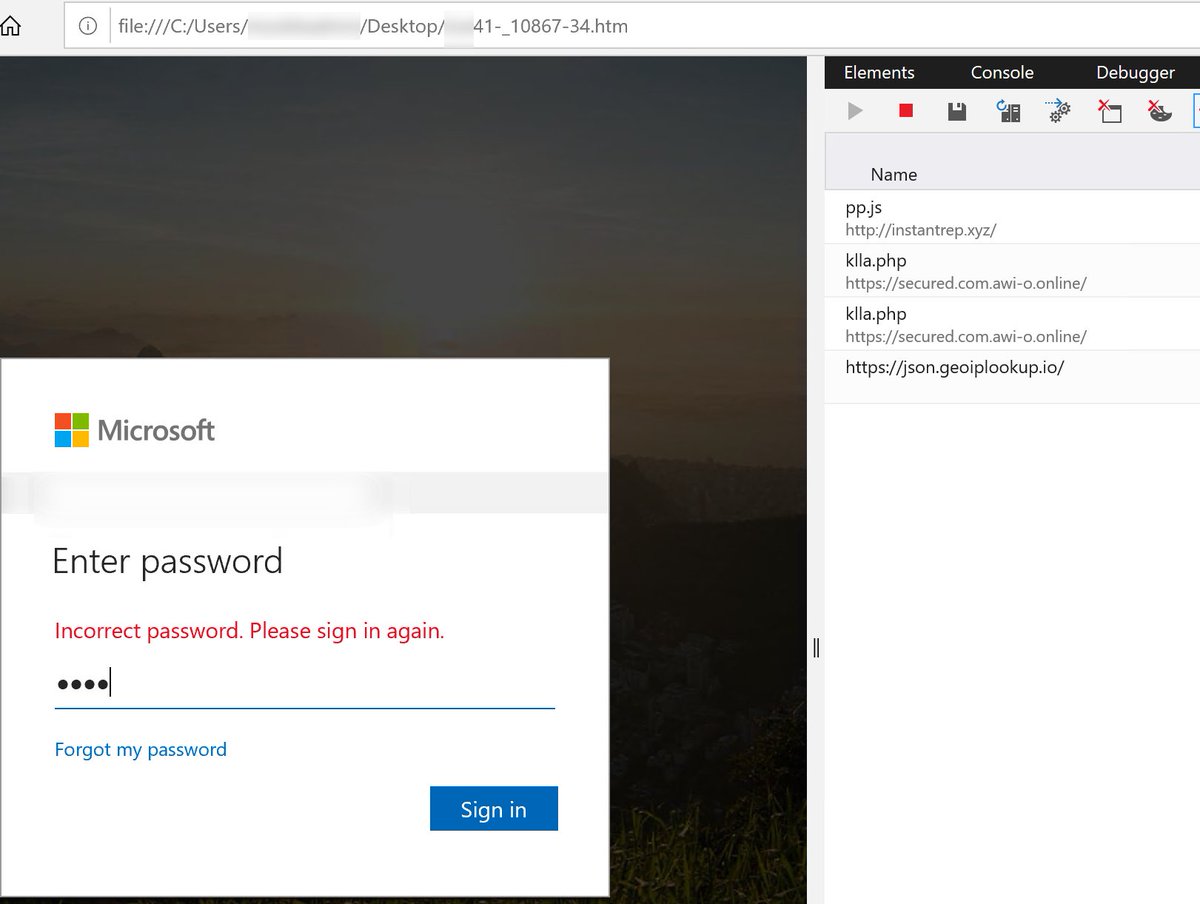
 The reason this attack is so effective at reaching inbox:
The reason this attack is so effective at reaching inbox: