
How to get URL link on X (Twitter) App



https://twitter.com/MalwareRE/status/1367521323531046916#GoldMax (aka #SUNSHUTTLE) is a new and capable backdoor written in Go/Golang. It is typically used as a late-stage (e.g. 3+) backdoor brought into an environment using access enabled via #TEARDROP, #RainDrop and other related malware deployed by #NOBELIUM/UNC2452.
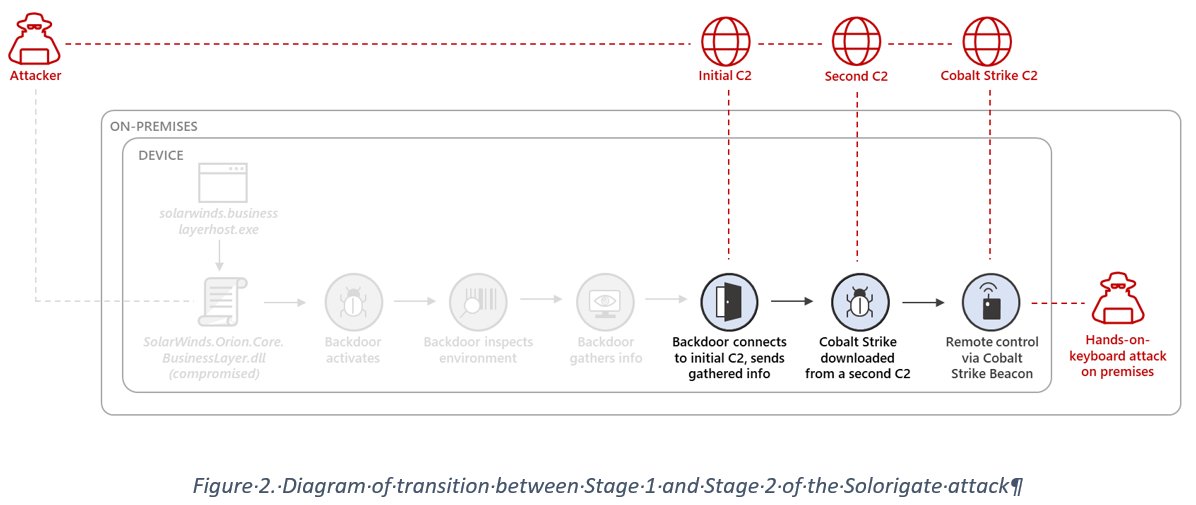
 Here are some highlights:
Here are some highlights: