
How to get URL link on X (Twitter) App


 The attack starts when an attacker, from her controlled machine, triggers a (possibly privileged) Windows host to authenticate to *her*. She does it by requesting EFS-RPC - Encrypted File System service - to open a remote file on her own machine. No domain creds are needed! 2/7
The attack starts when an attacker, from her controlled machine, triggers a (possibly privileged) Windows host to authenticate to *her*. She does it by requesting EFS-RPC - Encrypted File System service - to open a remote file on her own machine. No domain creds are needed! 2/7
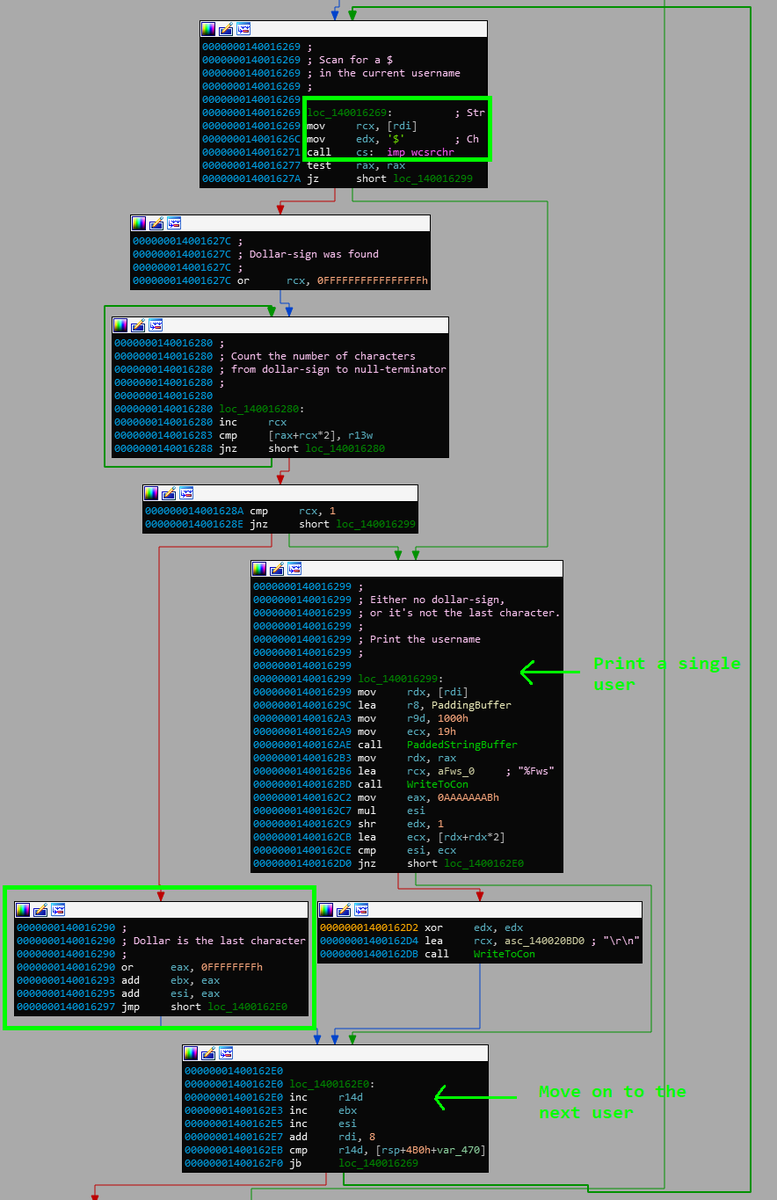
https://twitter.com/Ben0xA/status/1301550957516541952net.exe checks if the username contains a dollar sign. If it does, *and* the dollar sign appears at the end -- the username is not printed but simply skipped. This is probably because ending an account name with "$" may indicate a computer name, and not a human user. [2/5]

 [2/4] Right click and a quick "inspect" on the number, I found out the element's class name is "view_notification_random".
[2/4] Right click and a quick "inspect" on the number, I found out the element's class name is "view_notification_random".
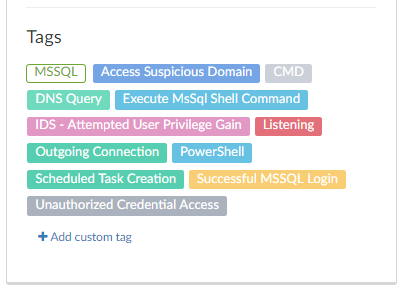
 Before we start: all scripts, binaries and IOCs are available on our github repository. In addition, malicious IPs, attack servers and domains appear on @Guadicore Cyber Threat Intelligence portal. You're welcome to take a look :)
Before we start: all scripts, binaries and IOCs are available on our github repository. In addition, malicious IPs, attack servers and domains appear on @Guadicore Cyber Threat Intelligence portal. You're welcome to take a look :)