
Christian | Full-time Bug Bounty Hunter | Host of @ctbbpodcast | Advisor @CaidoIO | 4x LHE MVH | 🗣️ English, 日本語 | ♥️ @mariahchan_ ♥️
8 subscribers
How to get URL link on X (Twitter) App


 *HTTP
*HTTP
 * Predictable/flawed password reset token
* Predictable/flawed password reset token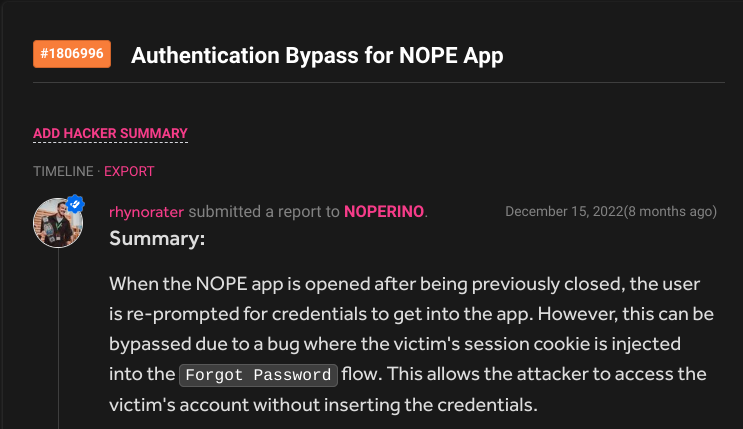
 Banking apps often have extra security measures in place and sometimes those security measures backfire. In this scenario, the app had implemented a re-auth mechanism after the app was closed. However, for whatever reason, the session was still alive in the background.
Banking apps often have extra security measures in place and sometimes those security measures backfire. In this scenario, the app had implemented a re-auth mechanism after the app was closed. However, for whatever reason, the session was still alive in the background.
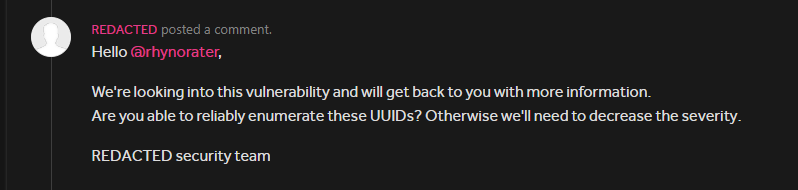
 1. Application-level ID Leakage
1. Application-level ID Leakage
 * Check all schemes (http, https, file, ftp, gopher, etc)
* Check all schemes (http, https, file, ftp, gopher, etc)