
Executive Director @OpenPriv. Privacy Researcher
https://t.co/3NovKkkNn3
@cwtch_im icyt7rvdsdci42h6si2ibtwucdmjrlcb2ezkecuagtquiiflbkxf2cqd
5 subscribers
How to get URL link on X (Twitter) App




 There is also a long list of exceptions that allow personal data to be disclosed to a huge number of organizations (including hospitals, schools and libraries) under the ridiculously broad category of "socially beneficial purposes"
There is also a long list of exceptions that allow personal data to be disclosed to a huge number of organizations (including hospitals, schools and libraries) under the ridiculously broad category of "socially beneficial purposes" 


 Thinking back to where it all started, years ago, with just me hacking on a little extension to ricochet it really has come a ridiculously long way thanks to the work and dedication of so many people!
Thinking back to where it all started, years ago, with just me hacking on a little extension to ricochet it really has come a ridiculously long way thanks to the work and dedication of so many people!https://twitter.com/SarahJamieLewis/status/949516067587502081


https://twitter.com/cancivlib/status/1494820569296117762
https://twitter.com/hackerfantastic/status/1485946271877804033It's no secret that I have a hold "professional organizations" and "registries" as a whole in pretty low regard. One of the reasons I got into hacking in the first place was because it was one of the few paths where progress was not gate-kept by useless bureaucratic bullshit.

https://twitter.com/SarahJamieLewis/status/1132728009289396224Failed Approach #1: Custom Wiki
https://twitter.com/SarahJamieLewis/status/1194087392505946113
https://twitter.com/valkenburgh/status/1465366443613200388Seriously please wipe off the layer of rentier capitalism, it is what Adam Smith would have wanted.
https://twitter.com/SarahJamieLewis/status/1287870948398383104
https://twitter.com/SarahJamieLewis/status/1459296130387177472I started programming simple real mode operating systems in my teens and it's fluctuated as a hobby for me over the course of the last 2 decades.
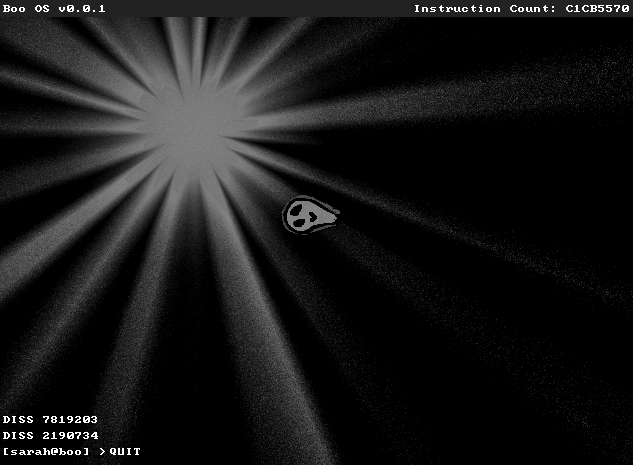
 It is completely useless. All that work, and you can only run a few commands, and one of them is QUIT.
It is completely useless. All that work, and you can only run a few commands, and one of them is QUIT.https://twitter.com/SarahJamieLewis/status/1451287529269850126
https://twitter.com/OpenPriv/status/1459214054728220676If you read our recent roadmap update carefully you might have surmised that there are two main directions of work taking place @cwtch_im
https://twitter.com/SarahJamieLewis/status/1442549144355106816