Hacker, researcher, builder of things. Founded @securityheaders/@reporturi, Pluralsight author, Microsoft MVP, award winning entrepreneur. Likes cars.
How to get URL link on X (Twitter) App


 The ECA itself is installed on the main feed from the Low Pressure Fuel Pump on top of the fuel tank. It’s an inline sensor that reads the fuel as it passes through.
The ECA itself is installed on the main feed from the Low Pressure Fuel Pump on top of the fuel tank. It’s an inline sensor that reads the fuel as it passes through. 



 Driving out of the city with @stebets, this place is mega!! ❄️🔥🇮🇸
Driving out of the city with @stebets, this place is mega!! ❄️🔥🇮🇸 




https://twitter.com/JohnONolan/status/1277934977754132480I also recall @zeeg once talking about customers on a $50/mo sub wanting custom legal terms / NDAs / security reviews etc... but I can't find the tweet. It'd take us years to recoup the cost of onboarding them.

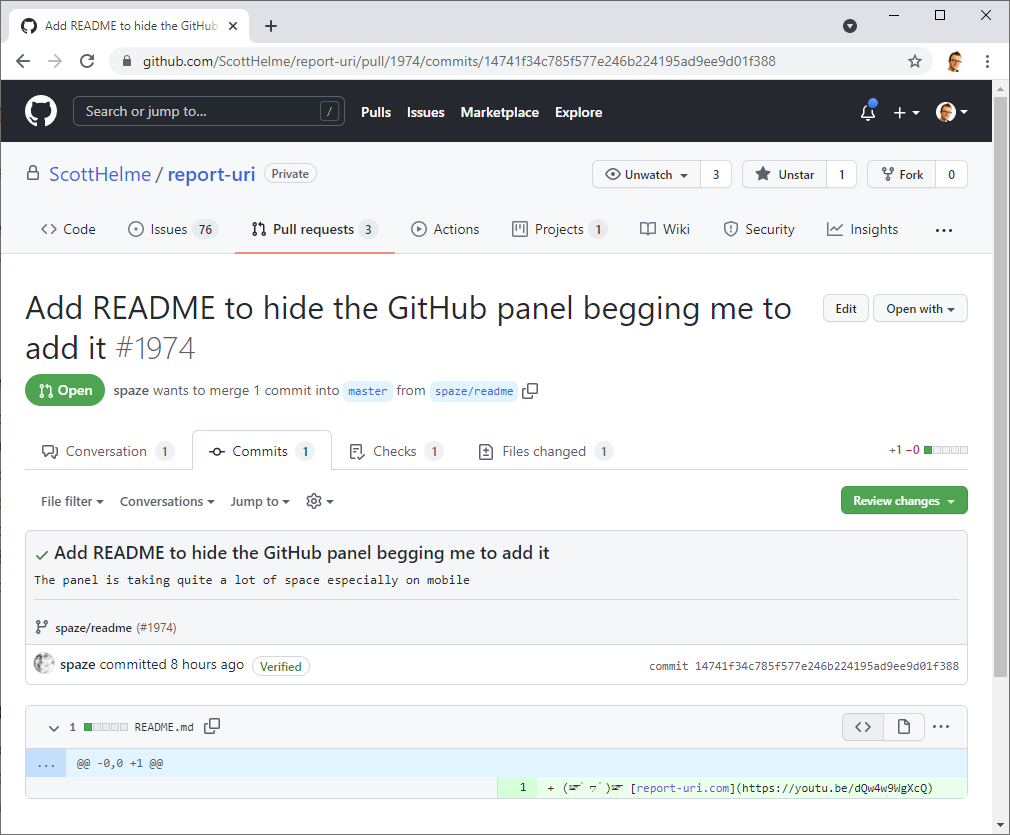
 Sadly, this change did not pass our stringent review process.
Sadly, this change did not pass our stringent review process. 


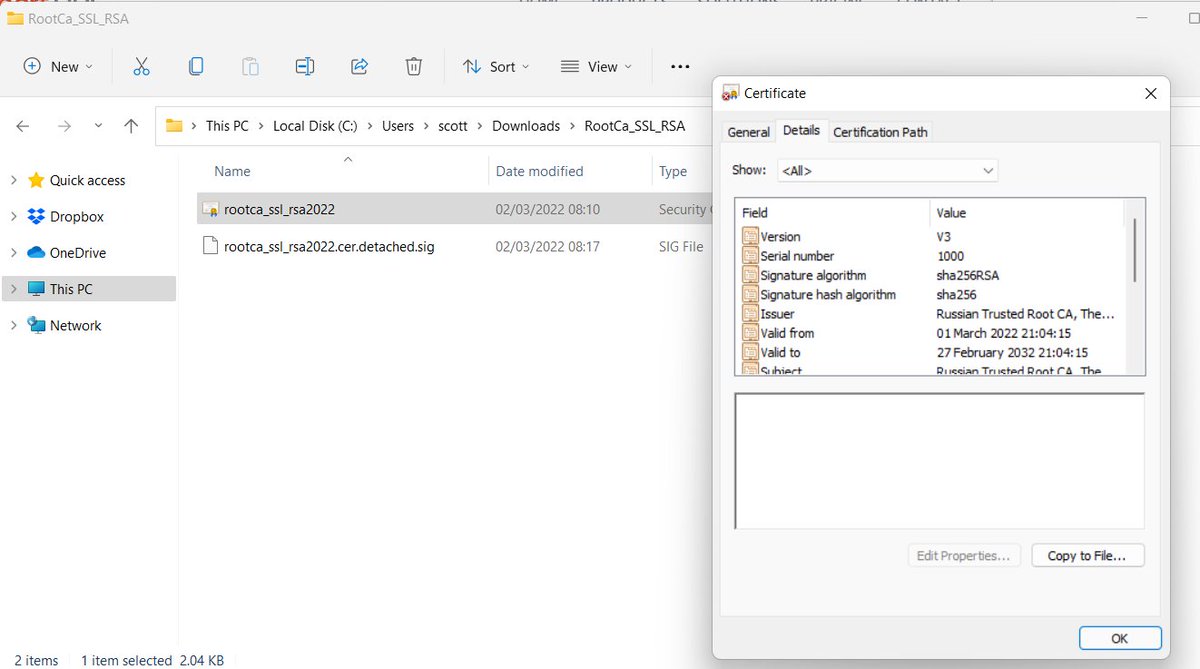
https://twitter.com/Scott_Helme/status/1300813526030839808Imagine buying a new certificate that looks like this!


 So here we go with the build! First up was the rack, I wanted one with wheels because of where it’s going (space restricted and can’t go on the wall). Couldn’t see one I like with wheels so I gave mine wheels!
So here we go with the build! First up was the rack, I wanted one with wheels because of where it’s going (space restricted and can’t go on the wall). Couldn’t see one I like with wheels so I gave mine wheels!