
How to get URL link on X (Twitter) App





https://twitter.com/vxunderground/status/1423336151860002816



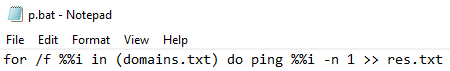
 1. NTDS dumping
1. NTDS dumping


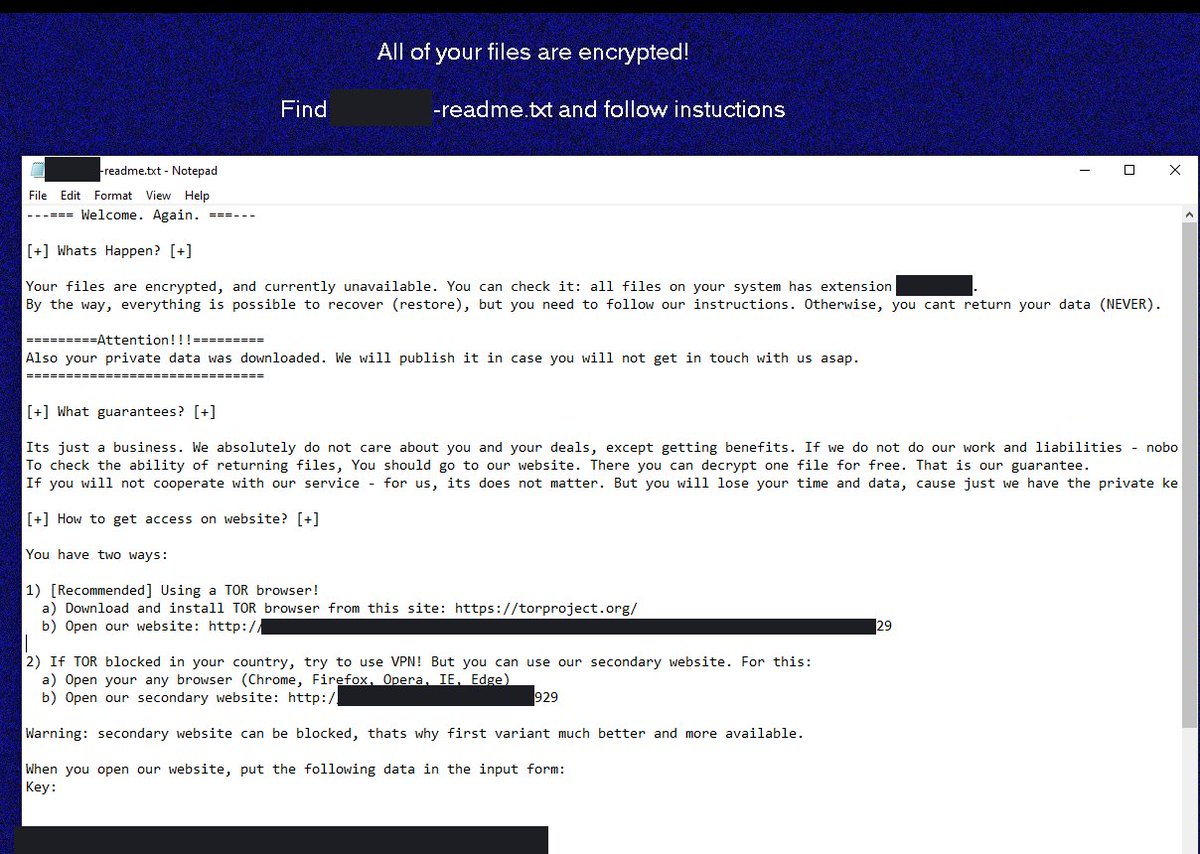



 Shout-out to @hatching_io, @lazyactivist192, @malwrhunterteam, and @R3MRUM. Thanks for doing what you do!
Shout-out to @hatching_io, @lazyactivist192, @malwrhunterteam, and @R3MRUM. Thanks for doing what you do!