
How to get URL link on X (Twitter) App

https://twitter.com/zackkorman/status/1982144413993251302Caveat: If you’re reading this because you want to see what attackers can do +examples, that will come in a later thread. I don’t want that to feel half-assed or rushed. This thread is just to share some info on how it works and problems I see right now.
 Caveats: First, I’m not saying this is the “one true way”, just that it’s my advice because it’s my experience. Ofc, it depends on the type of product you’re building. Second, this is for technical founders, not non-technical founders trying to vibe code or something dumb.
Caveats: First, I’m not saying this is the “one true way”, just that it’s my advice because it’s my experience. Ofc, it depends on the type of product you’re building. Second, this is for technical founders, not non-technical founders trying to vibe code or something dumb.
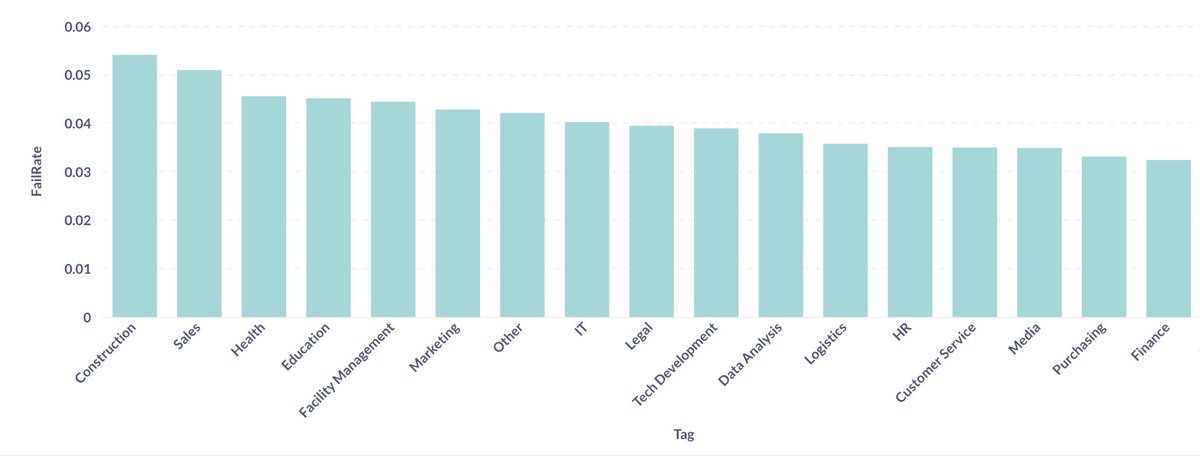
https://twitter.com/zackkorman/status/1977413394048364744One caveat: I’m the CTO at Pistachio, so I’m obviously pretty biased. We have an AI insider threat detection product. But that also means I’ve worked very hands on with these systems. Still, grain of salt and all that.