indie dev • building in public • travelling the world
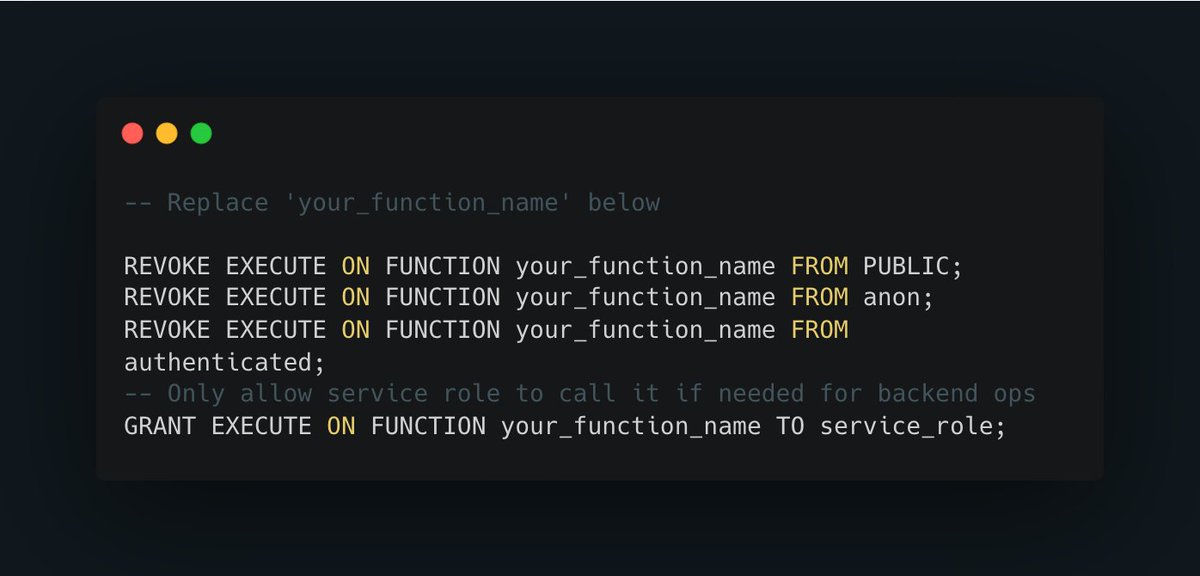
☠️ https://t.co/FDsz1A1dwW - secure your vibecoded app
💎 https://t.co/Lzh71PmHdb
👨💻 https://t.co/jZsVBIJZc1
🎮 https://t.co/edFPZ7ncwI
How to get URL link on X (Twitter) App